The IT administrators are responsible for managing users' accesses to web applications and sensitive business data without inhibiting business agility, user experience and compliance— in a cost-effective way.
However, as business challenges keep continuously evolving, enterprises are compelled to adopt different solutions to tackle them. As a result, network boundaries are not traditional anymore.
With the advent of cloud adoption, BYOD, and remote working, IT administrators now have to manage the user identities and accesses across multiple platforms and beyond the traditional network perimeters. This had hugely strained the IT team's efficiency.
Adopting automation for IAM can greatly improve the IT team's functioning by eliminating redundant work. Automating identity management can also enhance security, simplify compliance audits, and improve the agility of your business model.
When employees are hired, their account must be set up— this includes configuring user attributes, mailboxes, home folders, and more. Likewise, when employees leave the organization, all their access to IT resources must be revoked without fail.
Provisioning and de-provisioning users across different platforms especially across physical, virtual, and cloud environment, is complex. As a result, provisioning and de-provisioning users across these siloed cloud services in bulk becomes more complex, error-prone, and manually exhaustive.
The complexity increases if a company's HR payroll changes frequently
For instance, if an organization has 5,000 employees and experiences 10% employee growth and turnover rate, the total number of provisioning tickets would be 1500 (new users added: 10% x 5000 = 500, users leaving the organization: 10% x 5000 = 500, users added to fill existing positions: 10% x 5000 = 500).
The average time required to provision a user account in Active Directory can typically range from 5 to 30 minutes depending on the number of attributes associated with that account.
Check out the below table on how such changes incur cost to the company.
| In an organization with 5,000 employees | For 1 ticket | For 1500 tickets |
|---|---|---|
| Average time required to provision an AD account and other cloud identities | 15 mins | 375 hours |
| The average hourly wage of a help desk technician | $22 | $22 |
| Total cost incurred in using native tools | $5.50 | $8,250 |
What if this cost can be reduced to more than 70%. Introducing AD360, integrated identity and access management (IAM) solution for managing user identities, governing access to resources, ensuring compliance, enforcing security across on-premises Active Directory, Exchange Servers, and cloud applications from a centralized console.
How AD360 helps drastically cut down Active Directory user provisioning and de-provisioning costs:
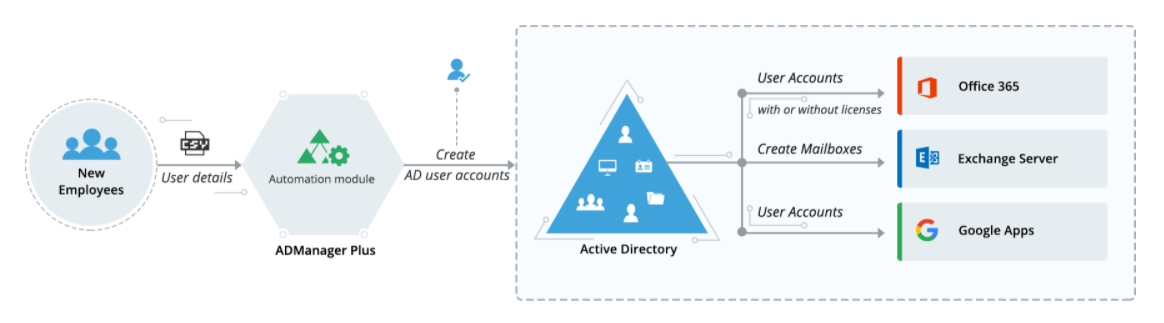
AD360 lets you automatically provision multiple users across on-premises Active Directory, Exchange Servers, and cloud applications. Using built-in User Creation Templates and CSV update features, object creation, modification, and management can be done in just a few minutes. These templates can also be customized as per organizational policies.
| In an organization with 5,000 employees | |
|---|---|
| The time required by the administrator to create multiple user templates [This is mostly a one time activity] | 1 - 2 hours |
| The time required by the help desk to import a list of users into an existing template | 1 minute |
| The number of tickets raised by HR (Approx). Let us assume each ticket includes 10 new user details | 150 tickets |
Total time required for provisioning the entire list of users sent by HR in a year = 2 hours of admin time + 30 minutes of help desk time for a total of 2.5 hours.
This means the total annual cost = [2 x hourly wage of an IT administrator] + [0.5 x hourly wage of a help desk technician] + annual subscription cost of AD360's AD management module that supports automation, or [2 x $32] + [0.5 x $22] + [$1,795] = $1870.
| For an organization with 1000 employees | Cost incurred annually | Percentage of savings | |
|---|---|---|---|
| Before automation | After automation | ||
| User provisioning and de-provisioning | $8,250 | $1,870 | 77.33% |
Provisioning user accounts in bulk using native Active Directory (AD) tools or Windows PowerShell scripts have always been irksome and time consuming, as it requires in-depth scripting knowledge. Further, as IT administrators have to often toggle between multiple consoles while provisioning access rights to new employees across Active Directory, Office 365, Exchange, Skype for Business, and G Suite, there is plenty of room for error.
With the help of CSV-based user provisioning techniques, AD360 simplifies bulk user provisioning for IT administrators.
For instance, if a group of employees who share the same set of permissions has to onboarded, AD360 makes this user provisioning simple by allowing the admin to create a template for the permissions, specify the employee names and other details in a CSV file and import it, and finally, apply the template to all the employees specified in the CSV file.
From the moment employees are onboarded until they leave the organization, the IT administrator manages the user account. Often, the administrator has to create an AD user account, modify its properties when the employee is assigned a different role, grant appropriate access rights, and delete the user account when the employee is off boarded.
Each of these modification tasks is highly error-prone and time-consuming when performed using native AD tools or PowerShell.
Such errors can be avoided if repetitive AD management tasks are standardized automated with AD360's User Modification Templates. These templates simplify and automate the process of modifying attributes of existing accounts at once.
Using the CSV import feature, IT administrators can perform AD account modification tasks in just a few clicks. Say an IT administrator has to modify 100 user accounts, all they have to do is apply the appropriate template to the list of users, and the desired attributes of the user accounts will be modified automatically. These templates can also be customized based on different organizational policies.
These templates also simplify the process of access provisioning to employees who change their department within the organization.
Every organization has multiple departments; and employees in each of these departments require access to different resources based on their roles and responsibilities.
With AD360, an IT administrator can create a template for each of these departments. When an employee changes their department, the IT administrator only has to apply the appropriate template to the user account and all the new access privileges required will be automatically assigned while earlier ones automatically revoked.
By using these templates that save the standard values and formats of all the attributes that are common to a group of employees sharing the same role, AD360 helps drastically reduce the human errors during privilege and access assignment assignment operations.
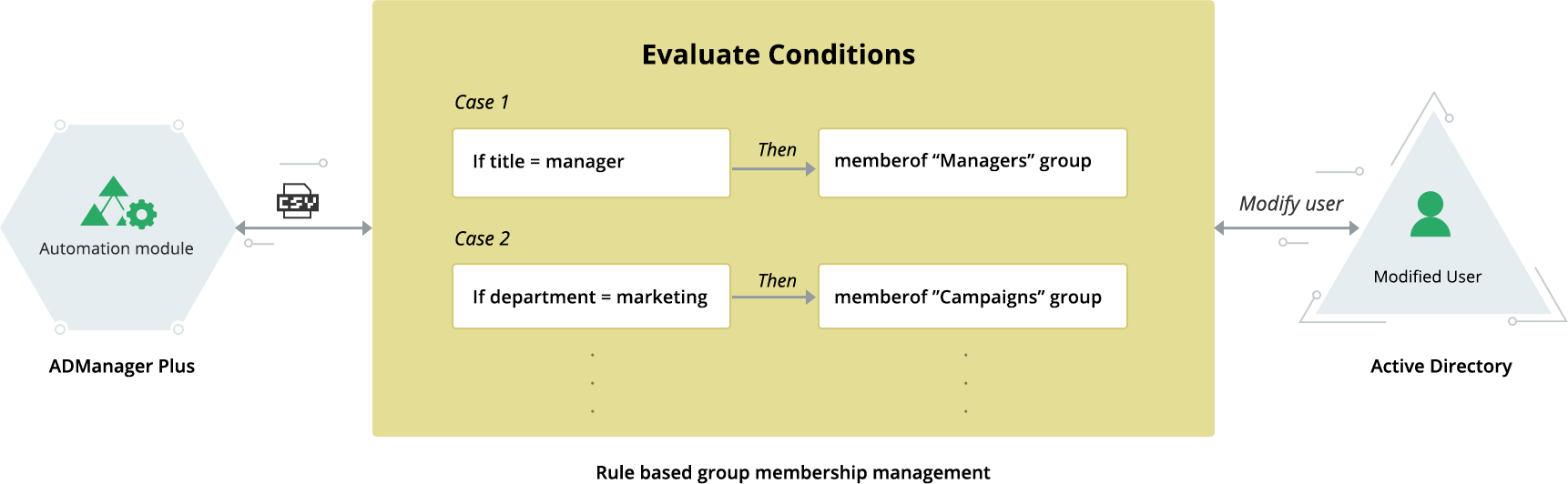
Using user modification templates, updating group memberships of employees becomes a whole lot easier. These templates help automate the process of updating employees' group memberships according to the set of rules set by the IT administrator.
For example, you can create a rule to add the user to the 'Designers' group if the user's title is 'Graphic Designer'. You can also update or manage the group membership for users in bulk, by importing a CSV file containing the list of user accounts to be modified.
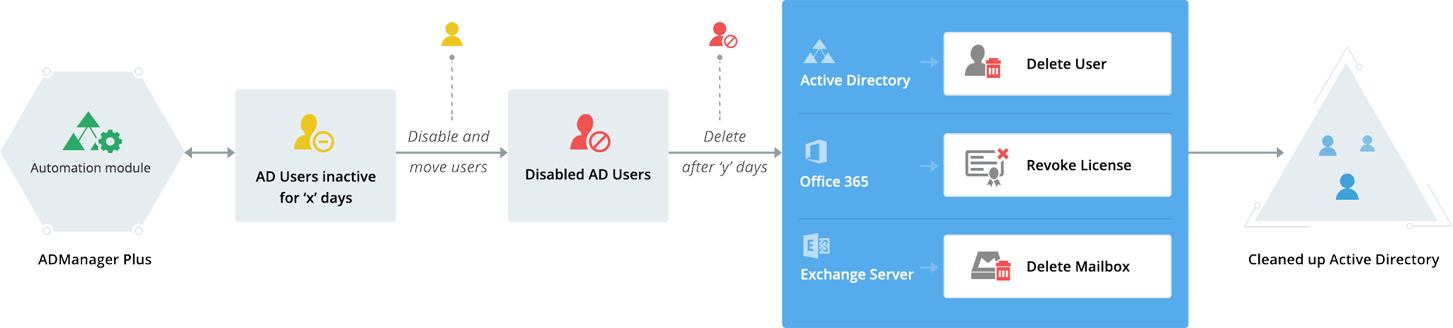
When employees leave your organization, their user accounts often remain in Active Directory (AD) unnoticed. The passwords of these accounts remain unchanged, which can lead to potential account compromises.
It gets worse if privileged user's account is residued.
This is why it's crucial to identify inactive accounts and immediately purge them. However, the only way to ensure that all inactive accounts are removed immediately is by automating the process. While native AD has provisions to track down and eliminate inactive user accounts, it cannot remove them in bulk or automate the process.
AD360 lets you effortlessly generate a list of all the inactive user accounts, disabled user accounts, and the expired user accounts in the form of reports. Right from these reports, you can delete or disable these accounts in bulk instantly. If required, you can also move them to a separate organizational unit, quarantine them for a desired period, and then delete them eventually. Best of all, you can automate these tasks and specify how often you want this automation to run.