Since 1960, passwords have been the de facto method for proving that a person is who they claim to be. This is a testament to the reliability and popularity of passwords. However, passwords have their shortcomings. If passwords are the only way to gain access to a user account, whoever knows the password can access the account. There is always a risk that somebody could guess the password, and this isn't helped by many users who practice multiple poor password behaviors.
The two major shortcomings of passwords are:
In both cases, the attacker can obtain the user's password. But what if there's another authentication process that the attacker can't get hold of, like your fingerprints? Adding a second layer of authentication that only the true user can genuinely provide ensures that even if the first layer is compromised, the attacker can't get through the second layer.
Enter multi-factor authentication (MFA), a simple idea that can reduce the risk of identity theft issues.
MFA is an additional layer of authentication that sits on top of a pre-existing authentication layer (most commonly passwords). For example, a user would have to enter their password, and then prove their identity by using their fingerprint, entering a one-time password (OTP) sent to their trusted device, or by other means to gain access. Most organizations use two layers of authentication to prove user identities, and this is called two-factor authentication (TFA).
Why can't we use just one strong authentication method, and make things easier? After all, it is extremely difficult to obtain someone's fingerprints, right? To answer this question, let's examine the three types of authentication factors.
Passwords fall under what are called knowledge-based factors, as you use something that only you know (hopefully) to confirm your identity. PINs and secret questions also fall under this category.
Then, you have inheritance factors. These are factors such as your fingerprints, eye retinas, DNA, which are things that you "inherit" and are part of your human body.
Lastly, there are possession factors. These are things authentication obtained from something you have with you, such as a key cards, a trusted smartphone, etc.
Each of these factors have their own set of shortcomings when used individually. For example, knowledge factors are compromised when someone else gains the knowledge. Possession factors are compromised when the trusted devices are stolen. Inheritance factors such as fingerprints, although extremely challenging to compromise, cannot possibly be changed once they are not secure anymore. However, when two or more of these factors are used together, one of the factors covers the other's shortcomings and vice versa, giving you a much stronger authentication system. For example, you can combine a knowledge-based factor, such as a password, with a possession factor, such as a code obtained from your smartphone. This way, if the smartphone is stolen, or if the password is obtained through phishing, one can't be used without the other to gain access to an account. Using MFA is an efficient way to prevent a data breach, or fall victim to attackers and their grand schemes.
Deciding on what combination you need to use is completely dependent on your organization's needs. Here are some of the most common MFA combinations:
All of these combinations use passwords as one of the authentication factors, which shows that passwords continue to remain popular. Why are passwords still used? The simple reason is that passwords are the easiest, simplest, and the cheapest authentication method to implement that requires no additional hardware. Passwords are still a secure authentication factor if they are set strong, and they have an additional authentication factor to back them up. This is why password management tools are still being used, and are a necessity.
In Active Directory (AD), there are native tools for password management, but they are neither as robust as third-party tools, nor as convenient to use. Third-party password management solutions sit on top of native tools, and give more granular control and more security options. Let's take the example of ManageEngine AD360's password management module and it's functionalities.
Users still often set passwords that are weak, or have been compromised already, or both, in many cases. An organization's security is only as strong as its weakest password, so strict password policies should be enforced. Natively, you can set the password length, complexity, and its expiration period. AD360's password management module lets you do all that, and more. With AD360, you can:
Users can easily update the user attributes in their AD profile through a secure web-based portal. This keeps their profiles up to date, and avoids discrepancies due to little, wrong, or no information. Implementing AD self-service greatly reduces the IT help desk workload and its operational costs.
A problem that can arise when users update their own information is that certain user attributes need to change. For example, when a user changes their working mode from office to work-from-home, their VPN permissions should be updated accordingly. This problem can be alleviated by setting modification rules. An IT admin can set certain conditions, and create rules that dictate what permissions or attributes must be modified if those conditions are met. So, in this case, when the user changes their information to work-from-home, the necessary VPN permissions will be automatically updated.
User updates their AD information ---> IT admin approves information update ---> Information falls under Condition 2 ---> Rules for Condition 2 are automatically applied
Adding a second layer of authentication on top of existing passwords enhances your organization's security multifold. IT admins can implement MFA directly on the users' logon screens on Mac, Windows, and Linux PCs. Some of the authentication methods supported are:
Apart from this, administrators can also enable single sign-on (SSO) for all SAML based applications. SSO allows users to use just one password and logon to access all their commonly used applications. It uses the same MFA methods listed above to identify the user securely. Users don't have to remember numerous passwords.
Password synchronization is also managed by AD360. When a user updates or resets their AD or Azure passwords, AD360 ensures the passwords meet the set password policy requirements, and then synchronizes them across all used on-premises applications.
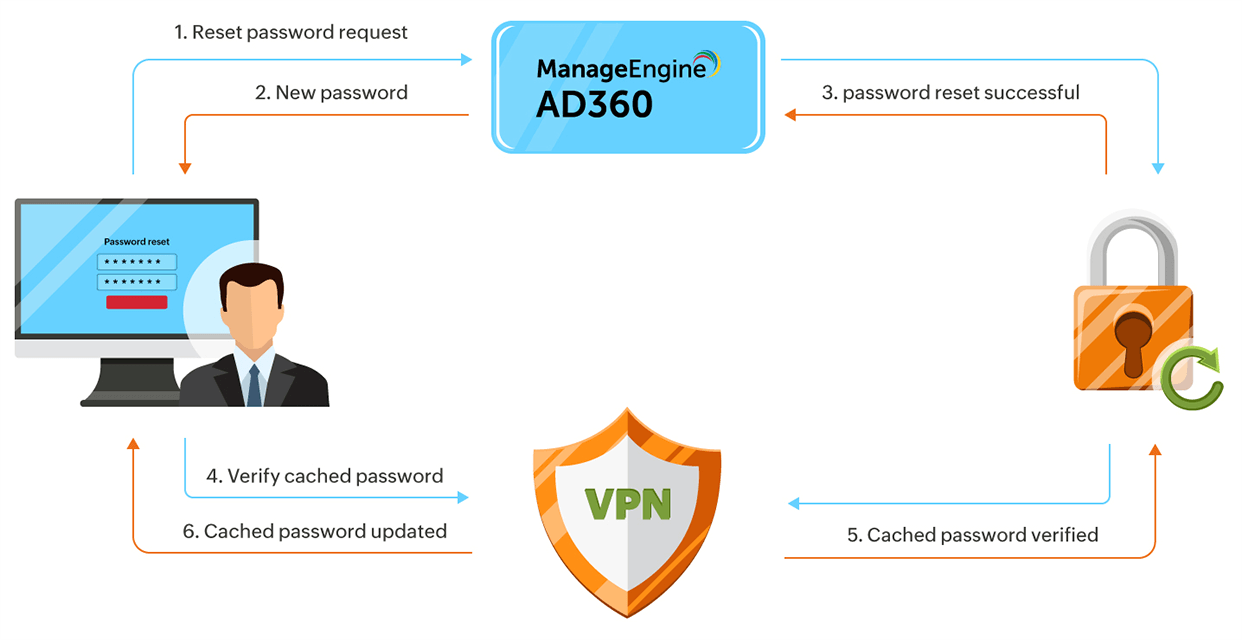
As you can see, AD360 provides many advantages over native tools. Ultimately, you receive better password management, stronger password security, and easier workflow overall. AD360 is also a solution that does more than just password management. It is an entire suite of tools that can take care of all your IAM needs.