Zero Trust is a security standard that functions on the principle of “never trust, always verify” and ensures that no user or device is trusted, irrespective of whether they are within or outside the organization’s network. Simply put, the Zero Trust model eliminates the concept of trusting anything within an organization’s security perimeter and instead advocates stringent identity verification policies to grant access to users both within and outside the security perimeter. The Zero Trust standard was first proposed by John Kindervag of Forrester Research in 2009 to compensate for the drawbacks encountered by traditional perimeter-based security models.
In the traditional security approach, also dubbed the castle-and-moat model, all the users, devices, and applications within a network are trusted by default. The network perimeter is protected with the help of firewalls and other on-premises solutions. The problem with this approach is that once an attacker gets past the security perimeter, they can move laterally within the network and gain easy access to network resources. With increases in mobility, cloud adoption, remote work, bring your own device (BYOD) policies, and sophisticated cyberattacks, the traditional security model is no longer sufficient to protect organizational assets and resources.
The M&M candy analogy has often been used to describe the traditional perimeter-based security model: hard and crunchy on the exterior, soft and chewy in the center. The fundamental goal of Zero Trust is to eliminate this soft interior and establish stringent security measures throughout the network. This is done primarily by shifting the focus towards protecting the network resources rather than the network perimeter.
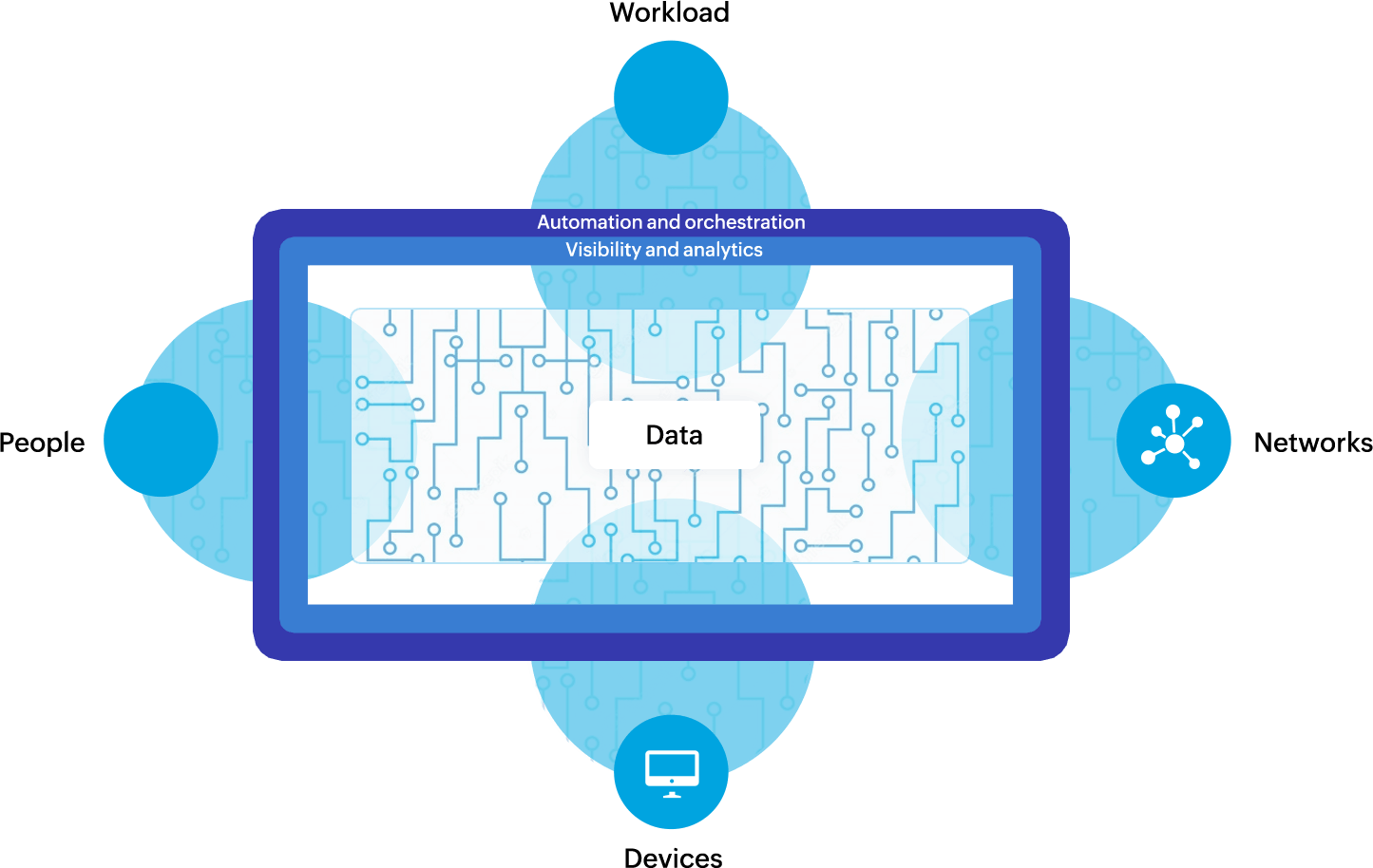
With the recent exponential increase in the number of remote workers, perimeter-based security is no longer adequate. Organizations' network perimeters are actively being redefined as data and users are located outside the boundary, and the rapid increase in mobility and cloud adoption causes data and resources to spread beyond the network perimeter. This also applies to employees, vendors, and other service providers. Consequently, this increases the attack surface and paves the way for attackers to gain entry into the network using novel and sophisticated methods, and a single security control cannot be applied to the entire network.
As previously mentioned, protecting the perimeter using firewalls, VPNs, and network access control is inadequate. While this may keep out external attackers and threats, the issue of insider attacks still looms large because everything within the network perimeter is inherently trusted. Additionally, cybercriminals are constantly finding ways to get into the network through either trusted user credentials or malicious links and attachments. Once the attacker makes it past the security perimeter, they can move laterally through the network and usually have free reign over the network resources, leading to data leaks.
The traditional perimeter-based security model was not developed with such dynamic shifts in the security landscape in mind, nor was it designed to support remote workers or cloud-hosted applications. But given that enterprises are accelerating towards such changes, a hybrid approach to cybersecurity has become necessary. A central point of management and control is now required, calling for a new approach to network security with the Zero Trust model.
The Zero Trust approach calls for eliminating the idea that trust is binary and that attackers cannot be present both within and outside the network perimeter. Every user, device, application, and the network itself is assumed to be hostile and meant to be authenticated before establishing trust. Thus, identity and access management forms the core of the Zero Trust model. However, Zero Trust is not a one-size-fits-all approach; organizations need to analyze and develop a holistic approach that builds on existing strategies and technologies to suit their requirements. Some of these strategies are as follows:
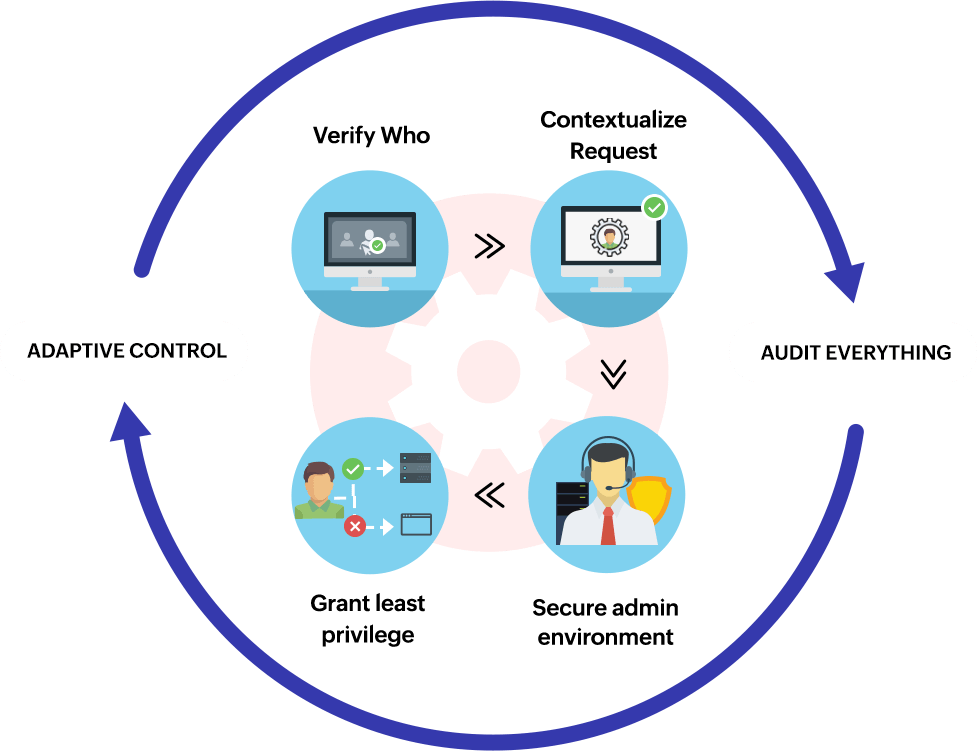
The Zero Trust approach involves identifying a protect surface, which is composed of the most important data, assets, applications, and services of the network. This protect surface is typically smaller than the attack surface. Once the protect surface is identified, the traffic flow across the organization’s network with respect to the protect surface can be monitored and analyzed. A microperimeter is then established around the protect surface.
Microsegmentation is the process of dividing the security perimeter into smaller and manageable zones, enabling granular access and control. Each zone maintains independent access, ensuring increased security. Microsegmentation reduces the attack surface to a minimum and restricts unauthorized lateral movement within the network.
Least privilege access is one of the most important aspects of Zero Trust. By employing the principle of least privilege, each user is given access only to the data and resources essential for performing a specific task. Since users are given access to resources on a need-to-know basis, their exposure to the sensitive and critical parts of the network is significantly minimized. Consequently, even if a user’s credentials or device are compromised by a malicious attack, the attacker gains access only to resources for which the user is granted access. There are many ways to implement least privilege access, the most common of which is role-based access control (RBAC). With RBAC, each user is granted or denied access to data and applications on the basis of their role within the organization.
Single sign-on (SSO) enables users to log in to a wide range of applications and services using a single set of credentials. SSO is a step in the right direction to implement passwordless authentication as it greatly reduces the number of passwords required for each user. In addition to this, SSO plays an important role in minimizing the number of credential-based attacks. SSO also helps in resolving security gaps due to fragmented identities caused by using both on-premises and cloud solutions.
Multi-factor authentication (MFA) is another core component of Zero Trust security. With multi-factor authentication, users are required to verify themselves using more than one authentication factor. This is typically employed by combining multiple credentials or factors such as something the user knows, something the user has, and something the user is.
For example, using a two-factor authentication (2FA) method, the user may be required to provide a password and a biometric such as a fingerprint. Another example is a one-time password (OTP) or code sent to the user’s device. By increasing the number of credentials required to gain access to the network, the number of credential-based attacks is greatly reduced. Multi-factor authentication can be combined with single sign-on to provide an additional layer of security.
Zero Trust requires all user activities to be continuously monitored and audited. Threat detection and user behavior analytics are employed to proactively look out for and shut down malicious attacks. Attackers are now employing technologies such as AI and machine learning to perform sophisticated attacks, so organizations must stay up to date by leveraging the same strategies and technologies to stay one step ahead of their perpetrators.
Identity and access management (IAM) is at the core of Zero Trust security. Users need to be authenticated and authorized before they can be provided access to network resources. Gartner recommends 15 critical capabilities that every IAM solution should have. It specifies identity automation features, which majorly reduce the risk of human-induced errors in the process of identity management.
The main role of network security is to prevent malicious attacks from reaching the endpoints in the network; as the conventional network perimeter begins to fade, enforcing tight endpoint security is crucial to protect the network against threats and attacks. Zero Trust advocates the integration of network and endpoint security to develop a holistic security model.
The network can be secured by performing microsegmentation and applying threat protection to help prevent security threats and attacks. Traditional network boundaries are rapidly vanishing with the increase in cloud adoption, BYOD policies, and remote working. To secure network resources against constantly evolving threats, the network has to be monitored using new age behavioral analytic tools.
Simplify complex tasks such as bulk user management and bulk mailbox management with AD360. Administrators can continuously monitor Office 365, receive real-time email notifications on service outages, and view the availability of endpoints. Admins can also view the granular details of a particular incident and gain access to the performance and health status of their Office 365 features and endpoints. AD360 also provides detailed reports which aid in compliance management and other tasks that keep Office 365 secure.
Automate routine management tasks such as user provisioning, modification, deprovisioning, and Active Directory (AD) administration with the identity life cycle management solution offered by AD360. Performing identity management tasks for thousands of users, including temporary employees and contractors, imposes a heavy workload on IT administrators. AD360 eliminates the manual processing of these tasks and helps rule out redundancies and errors often caused by humans. The competent and streamlined identity management solution ensures that stringent access policies are followed to provide the right level of access to users based on their roles and requirements. This is a crucial step towards employing Zero Trust.
AD360 allows easy provisioning, modification, and deprovisioning of multiple user accounts and mailboxes across AD, Exchange Server, Office 365, and G-Suite from a single console. Customizable user creation templates can be used to import data from CSV files to bulk provision user accounts. By integrating AD, Office 365, Exchange, G-Suite, and HR management system applications, AD360 simplifies critical IT management tasks for admins who would otherwise have to manage multiple applications and tools. This helps organizations save valuable manpower and resources while maintaining security and productivity.
With AD360, administrators can monitor AD, Office 365, Windows Server, and Exchange Server to keep themselves updated and obtain reports on changes. Compliance management is also made easy with built-in compliance reports and advanced auditing features, which minimize the workload of IT admins. Real-time audit reports on critical changes help detect insider threats by continuously monitoring user logon activities and other changes in the AD, Office 365, and Exchange Server environments. By ensuring compliance to standards such as HIPAA, the GDPR, SOX, and PCI DSS using prepackaged reports, AD360 helps prevent regulatory risks.
Admins can use AD360 to perform adaptive authentication and enforce tighter security with the identity analytics tool. By utilizing technologies such as big data, machine learning (ML), and AI, identity analytics tools provide contextual risk-based authentication. This, in turn, helps track unusual user behavior and restrict access privileges while enhancing the security and monitoring of privileged accounts. Users are provided access to applications and resources based on the principle of least privilege, which is one of the core tenets of Zero Trust.
AD360 provides MFA and SSO features to mitigate identity theft and password attacks. MFA combined with SSO provides an additional layer of security and a seamless user experience, reducing the time spent on managing passwords while increasing overall productivity. Passwords are on the verge of becoming obsolete due to their inefficiency at providing immunity against sophisticated password attacks. The password management module in AD360 allows administrators to enforce strict password policies by specifying the password length, complexity, expiration period, and granular password settings. Users can reset their passwords and update user attributes in their AD profiles.
AD360 employs user behavior analytics (UBA) to actively detect anomalies in user behavior and provide intelligent threat alerts. UBA offers enhanced accuracy and efficiency while reducing the rate of false positive alerts. User behavior is analyzed over an extended period and a baseline of normal user activities is developed with the help of data analytics and machine learning. Whenever there is a deviation from normal user behavior, the UBA solution considers it to be abnormal and the administrator is notified immediately. This is particularly useful for detecting insider threats and privilege abuse. Traditional security solutions typically employ rule-based threat detection techniques, which can inadvertently lead to false alarms. This creates difficulties in recognizing actual threats, which affects the organization's security. Similarly, traditional solutions do not employ ML and are incapable of detecting anomalies with precision. By taking advantage of the ML-based UBA capabilities offered by AD360, organizations can build a Zero Trust model to ensure maximum security.