- HOME
- More
- Security Analytics
- Cybersecurity in the age of AI
Cybersecurity in the age of AI
- Last Updated: November 14, 2024
- 921 Views
- 6 Min Read

Today's threat landscape is more complicated than ever, making it challenging for organizations to maintain a foothold. Billions of users and devices are connecting to enterprise networks and cloud applications and processing data at a scale unlike anything we have seen before.
Cisco's cybersecurity readiness index points to a rapidly evolving global threat landscape. In particular, the meteoric rise of artificial intelligence (AI) continues to create both opportunities and potential risks for organizations, and cybersecurity solutions are no exception.
AI vs. AI—the double-edged sword
AI has revolutionized the cybersecurity landscape by enhancing threat detection, response times, and overall defenses. With predictive capabilities, AI can even forecast threats before they materialize, empowering security teams to act preemptively. But here’s the catch—what happens when the very same technology is leveraged by malicious actors?
The rise of tools like generative AI enables attackers to execute more sophisticated and targeted attacks, creating threats so personalized that even the most vigilant users can fall prey. The World Economic Forum identifies AI-driven cyberthreats as one of the top 10 global risks for the next decade, making it crucial for organizations to strengthen their cybersecurity measures.
We are clearly entering a new era of cyber warfare defined by its complexity—a constant game of cat and mouse where one wrong move can compromise an entire network. To navigate this high-stakes environment, organizations must remain vigilant and wield varied weapons to ensure cybersecurity resilience.
Common cybersecurity challenges
Let's explore a few ways attackers can use AI to outmaneuver enterprise security defenses and execute notorious attacks.
1. Spear phishing attacks
Phishing has long been a favored tool for cybercriminals, but generative AI tools like WormGPT have escalated this threat. These AI programs generate convincing, personalized phishing emails that mimic real individuals or organizations, deceiving unsuspecting individuals into revealing sensitive data. With AI-driven automation, attacks are more frequent and sophisticated, making scams harder to spot.
2. Weaponized malware
AI is significantly impacting the development of weaponized malware, allowing cybercriminals to create intelligent malware that adapts to target systems. This AI-powered malware learns from its environment, evading traditional security measures for greater impact. For example, the BlackEnergy attack on Ukraine’s power grid caused a massive blackout by using adversarial AI to bypass security, remain hidden, and gather data before striking.
3. Automated bot attacks
AI-driven bots pose another critical cybersecurity threat, enabling large-scale attacks like distributed denial-of-service (DDoS) attacks with unprecedented speed and scale. By overwhelming online services with traffic, they disrupt operations, cause organizations to incur financial losses, and harm reputations. The complexity and multivector nature of these attacks require organizations to maintain heightened vigilance, as traditional security measures may struggle to keep pace.
4. Deepfake attacks
Deepfake technology uses AI to create hyper-realistic audio, video, or images that mimic real individuals. Cybercriminals increasingly exploit deepfakes in social engineering attacks, targeting executives and government officials. For example, a United Kingdom energy firm lost £200,000 (about $243,000) when attackers impersonated the CEO's voice, causing significant financial and reputational damage. This incident underscores the need for robust cybersecurity measures and employee training to recognize social engineering tactics.
5. Automated vulnerability exploitation
AI has revolutionized how cybercriminals identify and exploit vulnerabilities. Unlike traditional manual scanning, AI-powered tools automate the process, quickly detecting weak points in digital infrastructure and launching large-scale attacks at unprecedented speeds. For instance, AI can scan multiple websites for vulnerabilities, such as unpatched software or weak passwords, and exploit them before organizations can respond.
How to level up your defense strategy to address the risk of AI
The advancement of AI has provided attackers with sophisticated tools to launch severe attacks on enterprise networks. It's crucial for security professionals to stay ahead of these emerging threats with multifaceted tools and strategies. Here are some powerful analytics-powered strategies to combat the risks imposed by AI:
1. Enhanced threat detection with advanced analytics
One of the key challenges in cybersecurity is detecting threats early enough to minimize damage. Leverage advanced analytics and AI-driven insights to monitor network activities, identify suspicious behaviors, and flag potential threats. By having a unified single pane view of various data sources, such as network logs, access control information, and user activity, it's easier to quickly spot unusual activity that may indicate an attack in progress.
For example, insider threats—whether malicious or accidental—are one of the most challenging aspects of cybersecurity. Employees and trusted individuals often have legitimate access to critical systems, making it difficult to detect when these rights are abused or compromised. Unusual login attempts, suspicious data transfers, or access patterns that deviate from established baselines can all be quickly detected through an analysis similar to the one below. Security teams can stay abreast of sudden outliers through automated alerting capabilities.
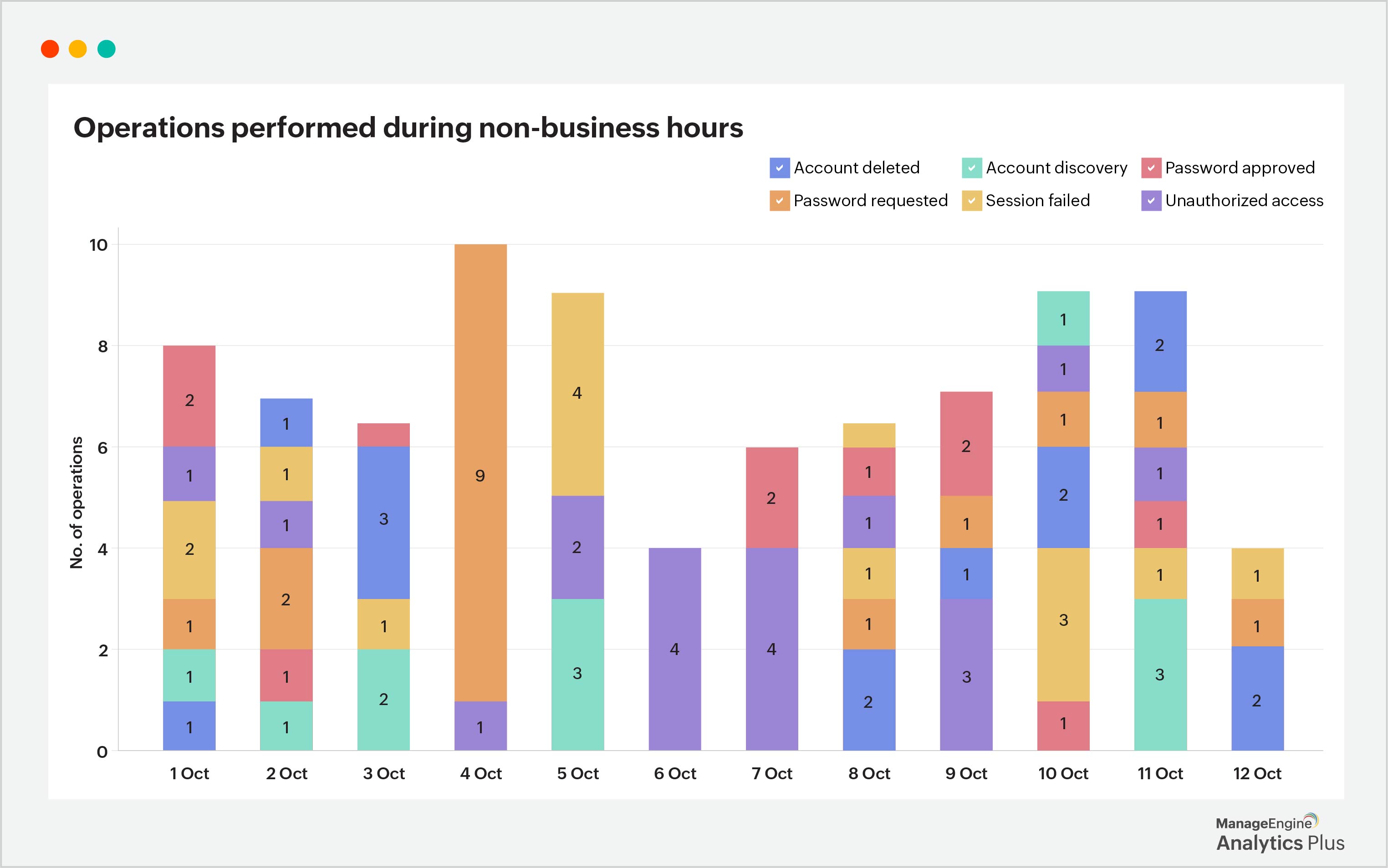
2. Preemptive measures to prevent security breaches
By leveraging predictive analytics, IT teams can build a proactive defense strategy that involves addressing vulnerabilities, refining security policies based on attack patterns, and strengthening the overall security posture to stay ahead of emerging threats. This approach minimizes downtime, prevents breaches, and ensures continuous network protection.
The visualization below highlights vulnerabilities over time, enabling organizations to identify periods of increased risk and take action before threats escalate. For instance, the spikes in September and October indicate the need to prioritize patches and updates for affected systems.
Additionally, this analysis provides insights into endpoint-specific vulnerabilities, allowing IT teams to focus on devices or systems with consistently high CVE scores. In addition to tracking vulnerabilities by endpoint type or operating system, predictive analytics can also foresee high-risk areas, enabling teams to allocate resources, apply updates, and enhance monitoring before vulnerabilities are exploited.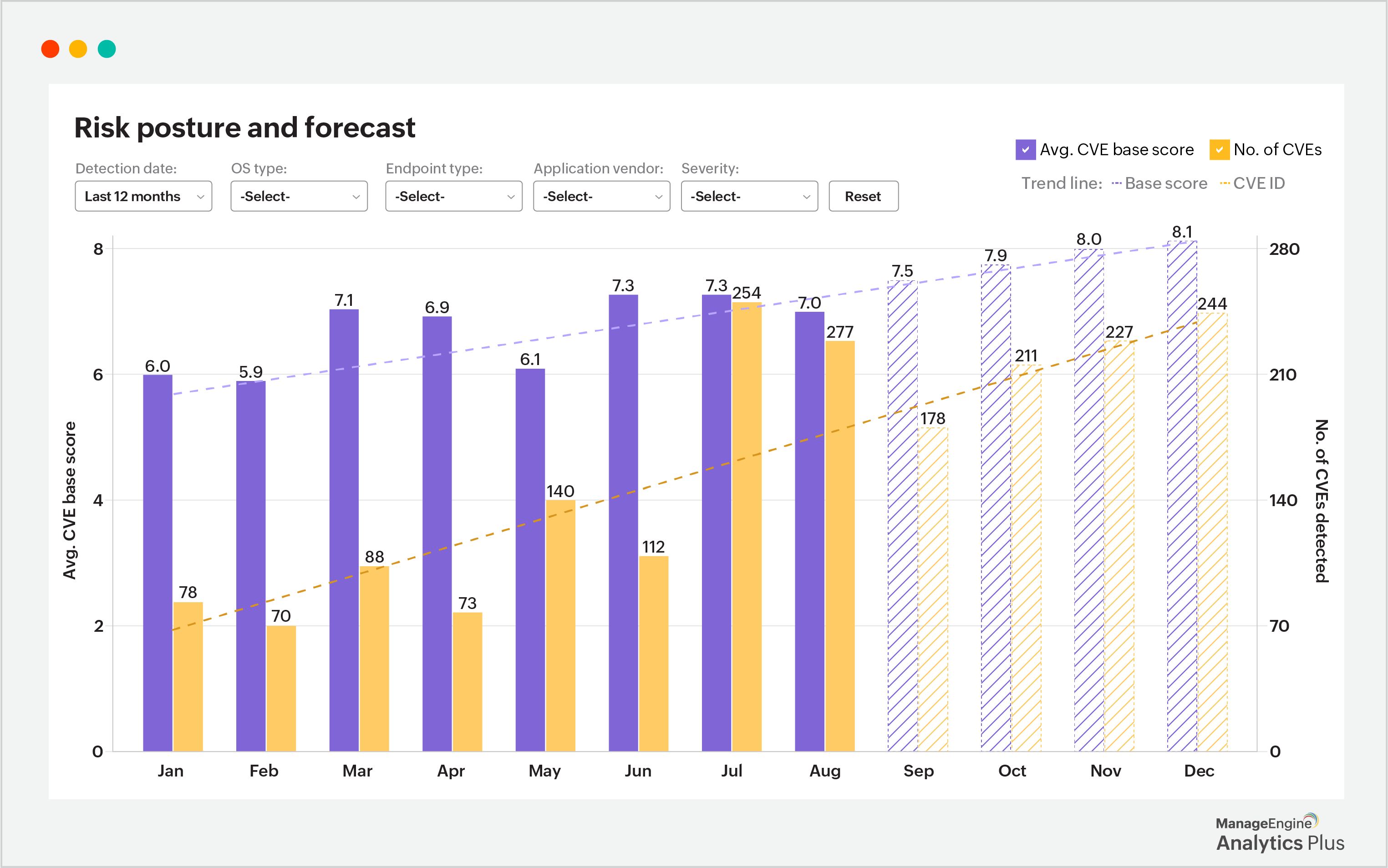
Another proactive strategy that can be undertaken is identifying and addressing potential security gaps. For example, if certain endpoints consistently show signs of vulnerability, you can highlight these as priority areas for enhanced security measures. This proactive approach significantly reduces the likelihood of a security breach and minimizes the impact if an attack does take place.
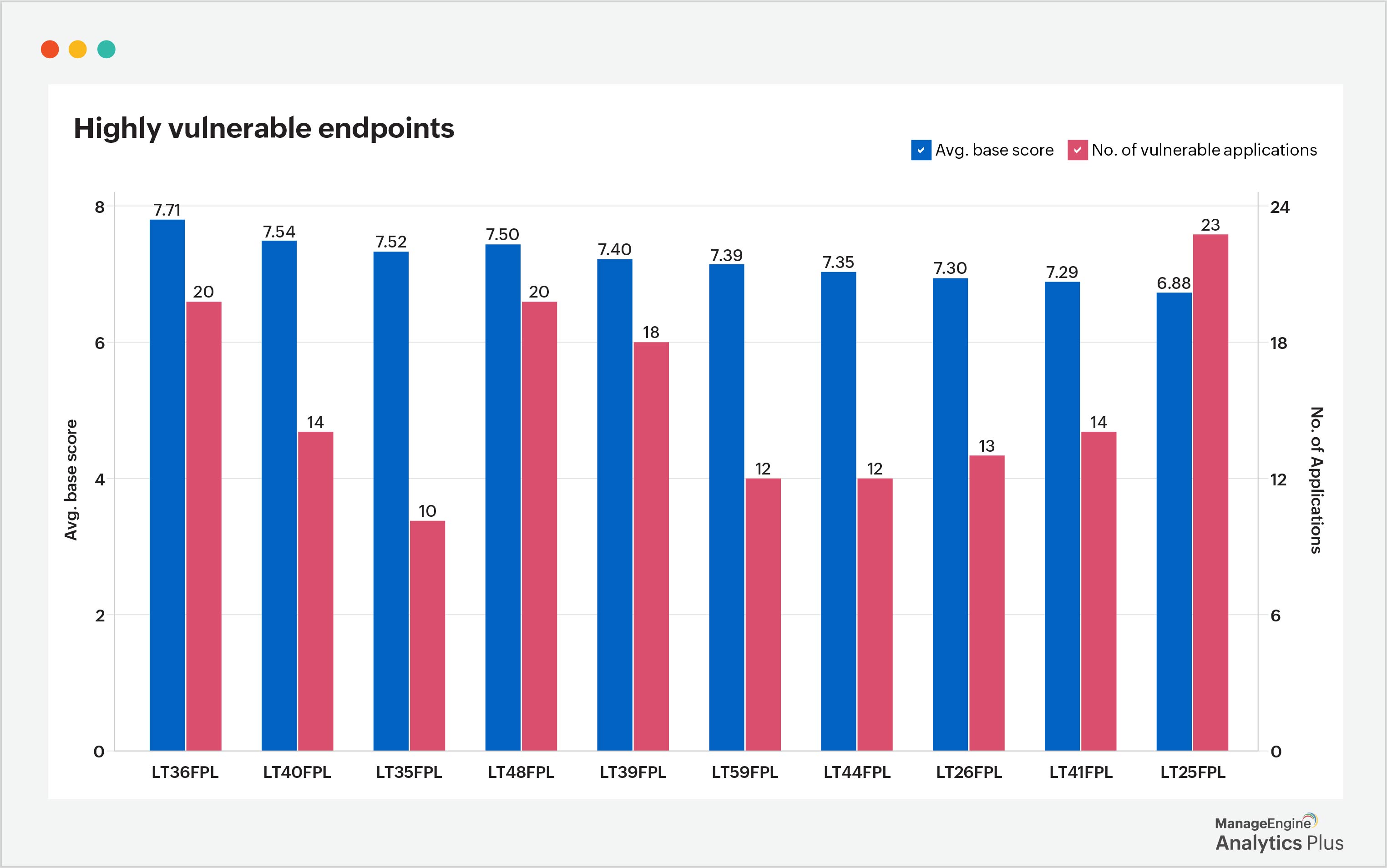
3. Streamlined incident response plan
When a cybersecurity incident occurs, swift response is crucial to contain damage. By visually highlighting when and where the most critical incidents are occurring, especially at their starting stages, it enables security teams to prioritize their response efforts, allocate resources effectively, and implement targeted measures to prevent future incidents. This streamlined approach enhances overall incident management and response efficiency, allowing for quicker mitigation of ongoing threats.
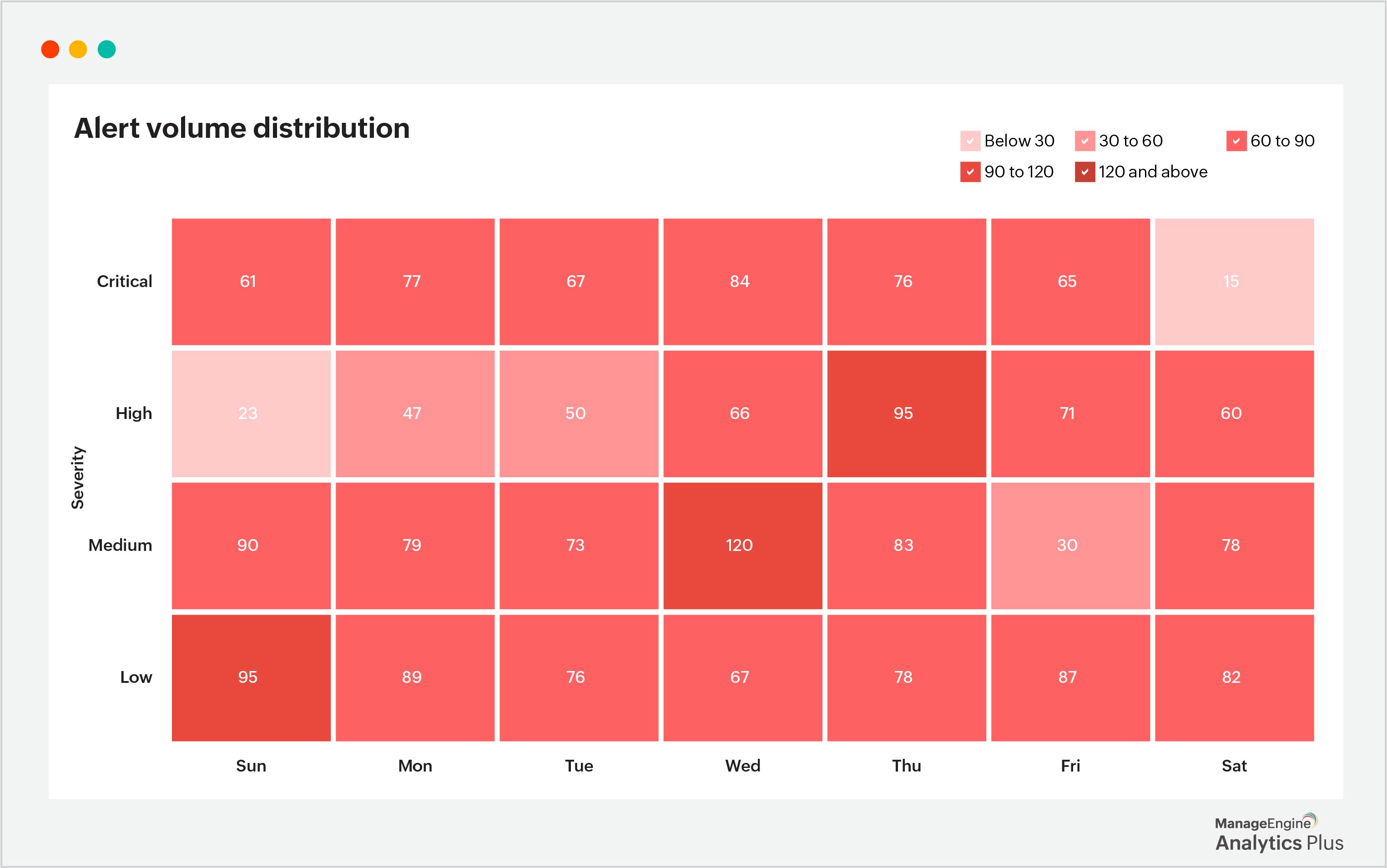
4. Root cause analysis for improved cybersecurity posture
Understanding the root cause of an incident is crucial to preventing future breaches. With powerful analytics tools, you can easily dig deep into incidents to understand what went wrong and why in seconds. Root cause analysis can be applied to understand what factors are contributing to spikes or declines in threat activity. For example, a spike in malware detections could step from an unpatched system vulnerability or insufficient endpoint protection.
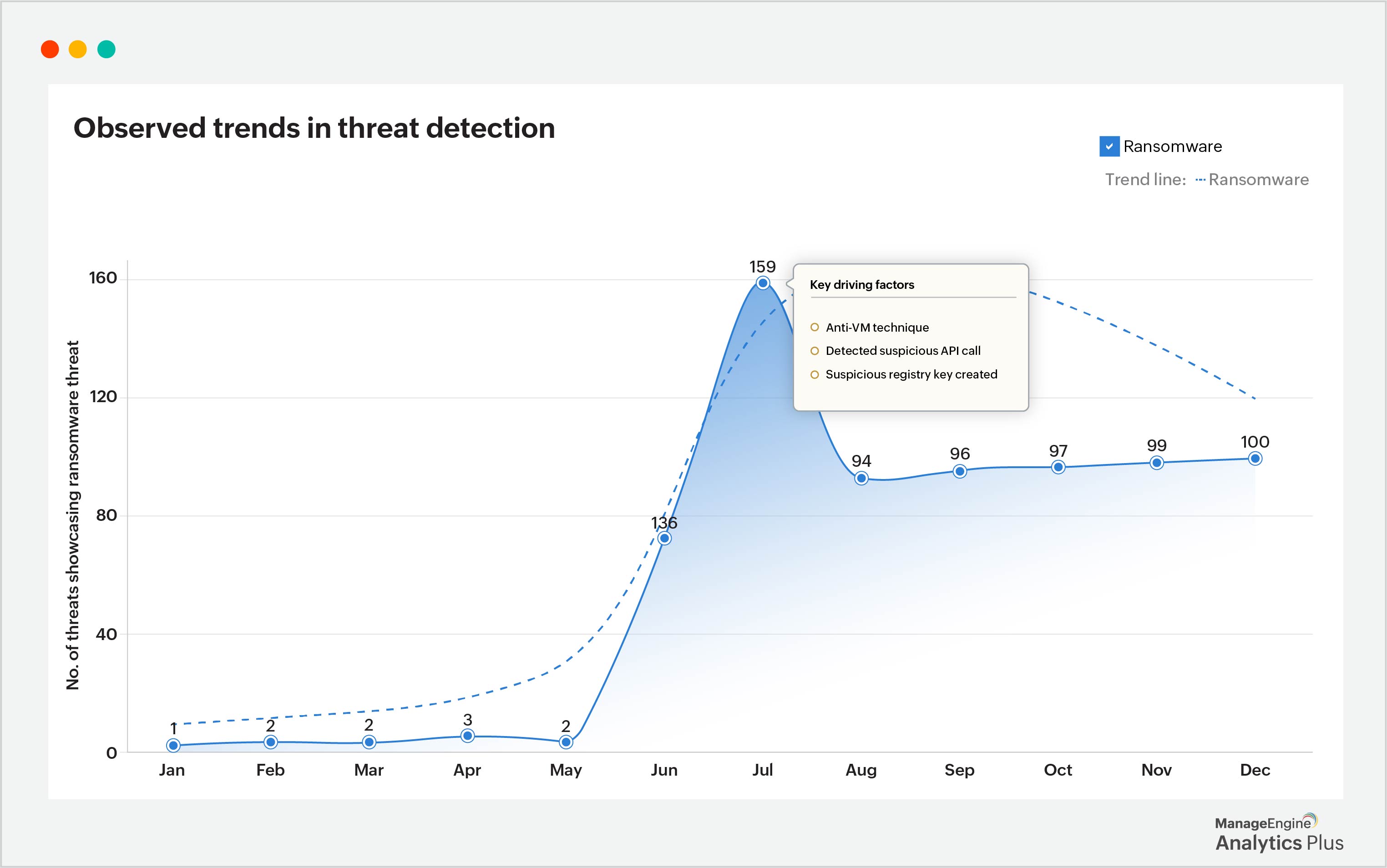
By automatically identifying the root causes behind these trends, security teams can take targeted actions immediately—such as patching software, strengthening security configurations, or improving employee training—to address these vulnerabilities and reduce the likelihood of future incidents. Continually implementing this functionality helps refine the organization's cybersecurity strategy and make proactive improvements before breaches occur.
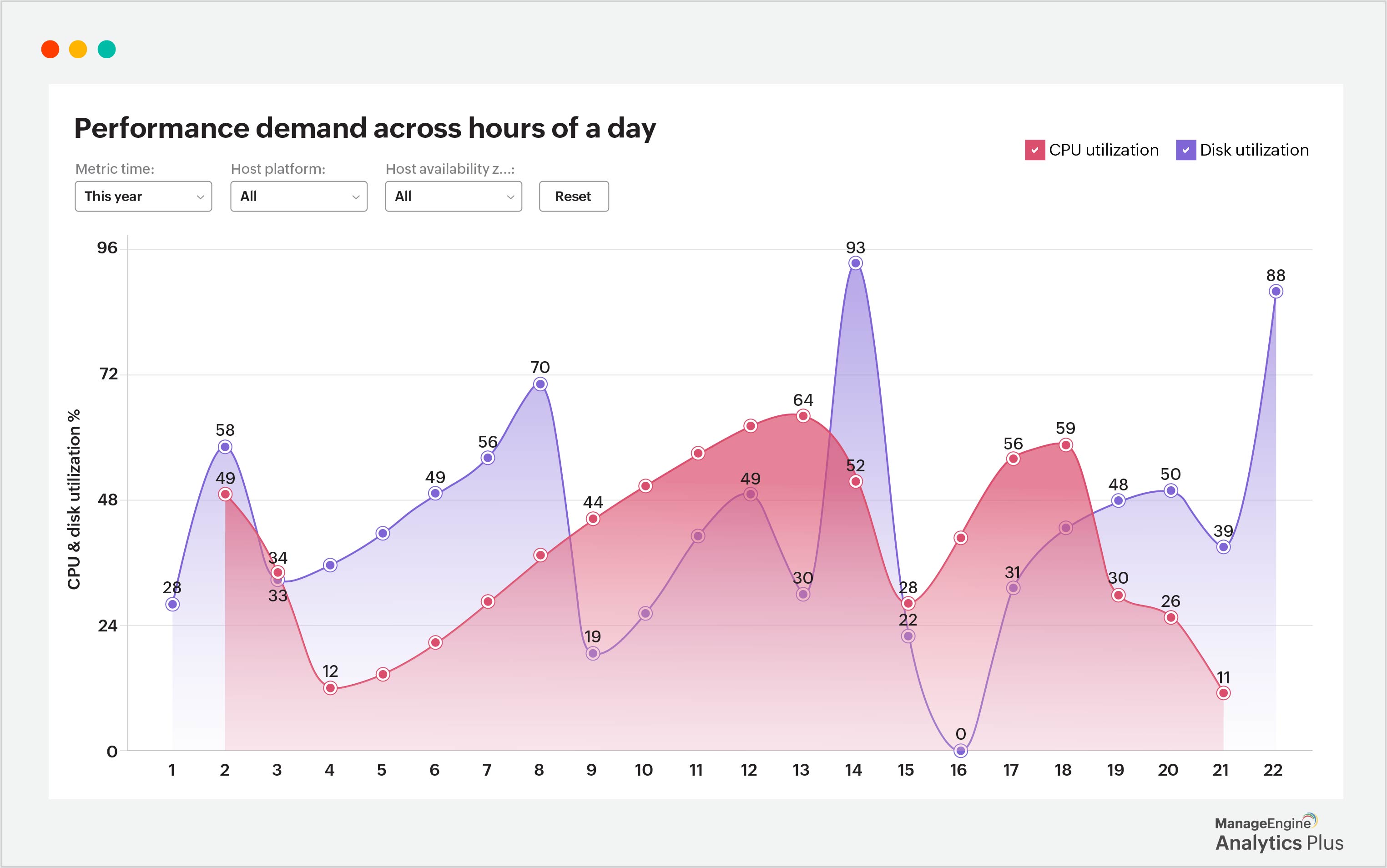
5. Capacity planning for cybersecurity resources
Cybersecurity often requires not just the right tools but also the right allocation of resources, whether it be bandwidth, storage, or manpower. If organizational data reveals a pattern of increased network traffic that might require additional bandwidth, or if certain servers are at risk of exceeding capacity, preemptive action can be taken to allocate the necessary resources.
Proper capacity planning ensures that there is no gap in the cybersecurity framework due to resource limitations, especially during high-risk times when DDoS attacks or other threats could push the existing infrastructure to its limits.
Moving towards a resilient cybersecurity future
The days of isolated security measures are gone. As organizations navigate an increasingly complex threat landscape, peppered with AI's footprints, cybersecurity must be embedded across every level of business operations. By investing in effective cybersecurity measures, staying informed, and fostering a culture of security awareness, organizations can enhance their resilience, protect valuable data, and ensure business continuity in the face of ever-evolving threats.
The reports shown in this blog were built using Analytics Plus, ManageEngine's AI-enabled IT analytics application. If you'd like to create similar reports using your IT analytics data, try Analytics Plus for free.
Talk to our experts to discover all the ways you can leverage security analytics to step up your cybersecurity measures.





