- HOME
- Endpoint Management Analytics
- What is Data Exfiltration and how to prevent it using analytics?
What is Data Exfiltration and how to prevent it using analytics?
- Last Updated: July 1, 2024
- 657 Views
- 5 Min Read

There are many security threats that organizations face daily. Among these, data breaches and data exfiltration are the most prevalent. Attackers are constantly reinventing their techniques and methods of attack. Organizations need a state-of-the-art security framework, along with a robust analytics platform, to detect and assess such threats, and proactively prevent them in time. In February 2021, the Talos intelligence group discovered a new "Mass-logger" Trojan in one of its routine scans. The Trojan was sent through an email campaign designed to retrieve and exfiltrate user credentials from multiple sources, such as Microsoft Outlook, Google Chrome and instant messengers. Talos quickly discovered this Trojan and advised end users to configure their systems for logging PowerShell events, such as module loading, and executed script blocks. This threat demonstrates one of the many techniques customarily deployed in data exfiltration, which we'll discuss in this blog.
What is data exfiltration?
Data exfiltration is often the result of outsiders breaking into a network to obtain sensitive data or user credentials. Data exfiltration occurs through one or more of several cyberattack techniques and includes loss of data through physical means, such as loss of printed documents or drafts, notices, thumb drives, laptops, mobile phones, or through electronic means, such as loss of data from servers or databases. As more and more organizations have adapted to hybrid work and moved their data payloads to the cloud, data exfiltration through electronic means is more prevalent and potent.
How does data exfiltration occur?
Data exfiltration is a three-step process that starts with an attacker breaching an organization's security framework and ends with the attacker stealing data from the organization's servers or databases.
1. First, the attacker seeks out a vulnerability in the organization's security layer, and inserts a malware into one or more endpoints linked to the corporate network.
2. Then, the attacker then performs data discovery—identifying and locating sensitive information—to locate targeted data.
3. Finally, the attacker deploys data exfiltration techniques to siphon data away from an organization's security perimeter. Often, the stolen data is sold on the dark web, or used to seek a ransom from the organization.
How can analytics catch or prevent data exfiltration?
Data exfiltration is challenging to spot since the events leading up the actual exfiltration often conceal themselves behind legitimate, everyday operations. Here are five ways analytics can help you catch or prevent data exfiltration:
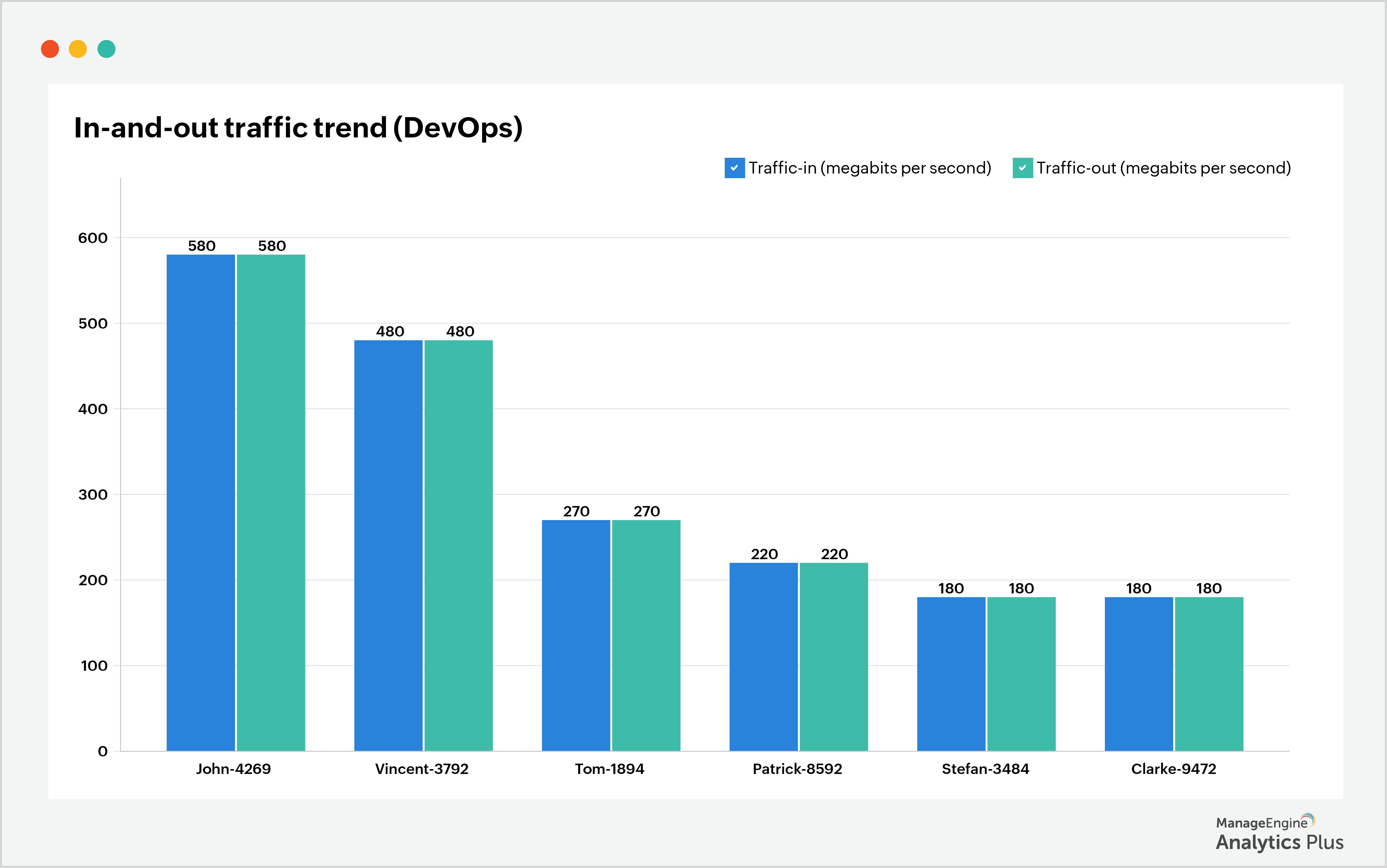
1. Tracking your network in-and-out traffic: In any organization, it's natural for data to move frequently across networks. Attackers with the intent to steal data, typically do it in spurts rather than all at once. This makes it challenging to detect data exfiltration as it's well-hidden behind regular network traffic patterns. However, with careful monitoring of network traffic, it's possible to catch small spikes in data movement. Though monitoring thousands of users' network traffic is no easy task, keeping tabs on every department's in-and-out traffic individually can help you spot anomalies easily. In the sample report below, two users from the DevOps team show higher data transfer than the others. This is an anomaly that requires further attention.
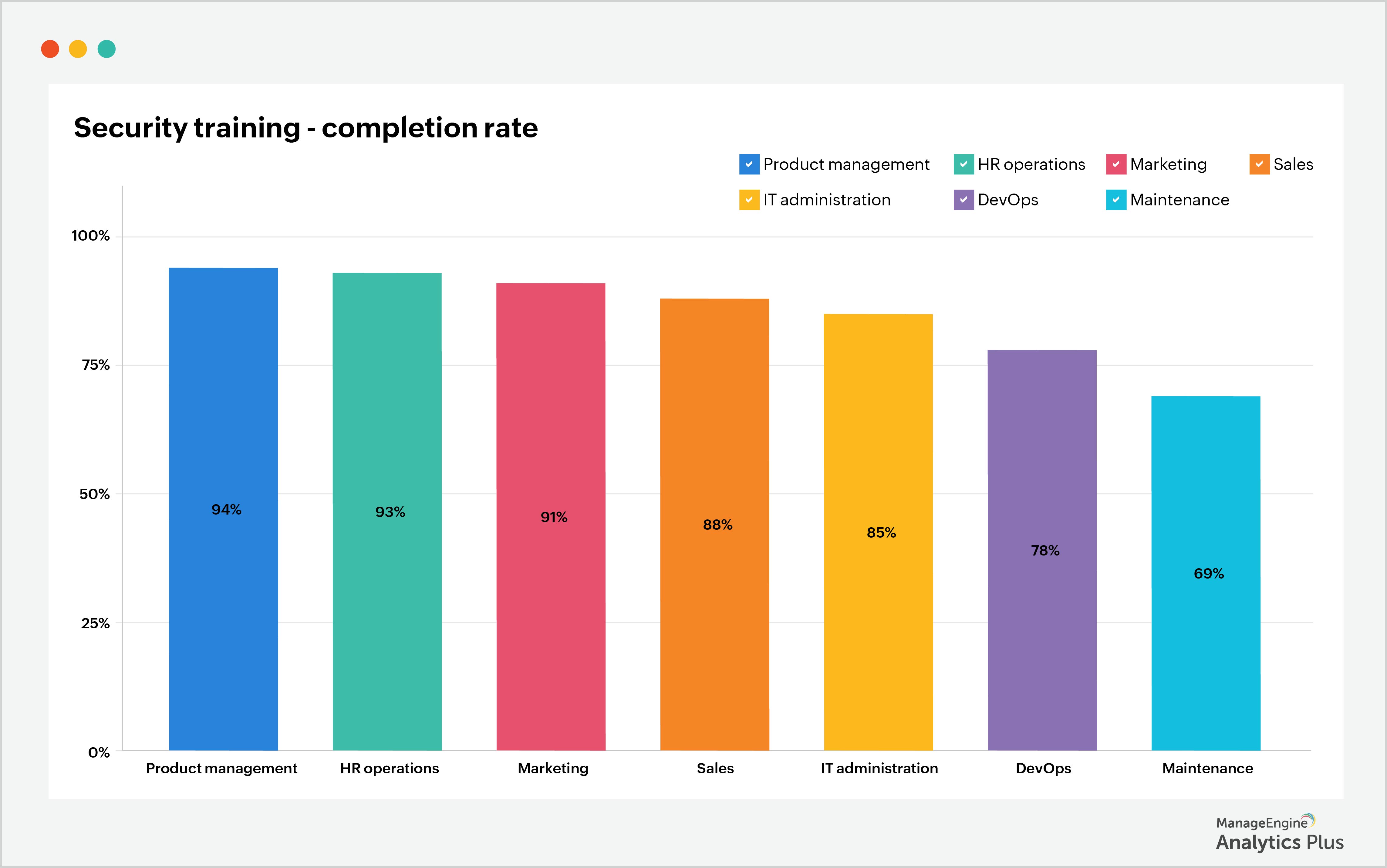
2. Monitor security training completion rate: Human error is a well-documented cause of cyberattacks such as data exfiltration. According to the Chief Executive survey, almost 90% of cyberattacks are caused by human errors. Sometimes, employees may unintentionally open up a gateway for hackers to enter. To prevent such incidents, educating employees against common threats and hacking techniques is important. This includes tracking the percentage of employees who have completed their security training, and enforcing having the remaining employees complete their security training. The sample report below shows the percentage of employees by department who've completed security training.
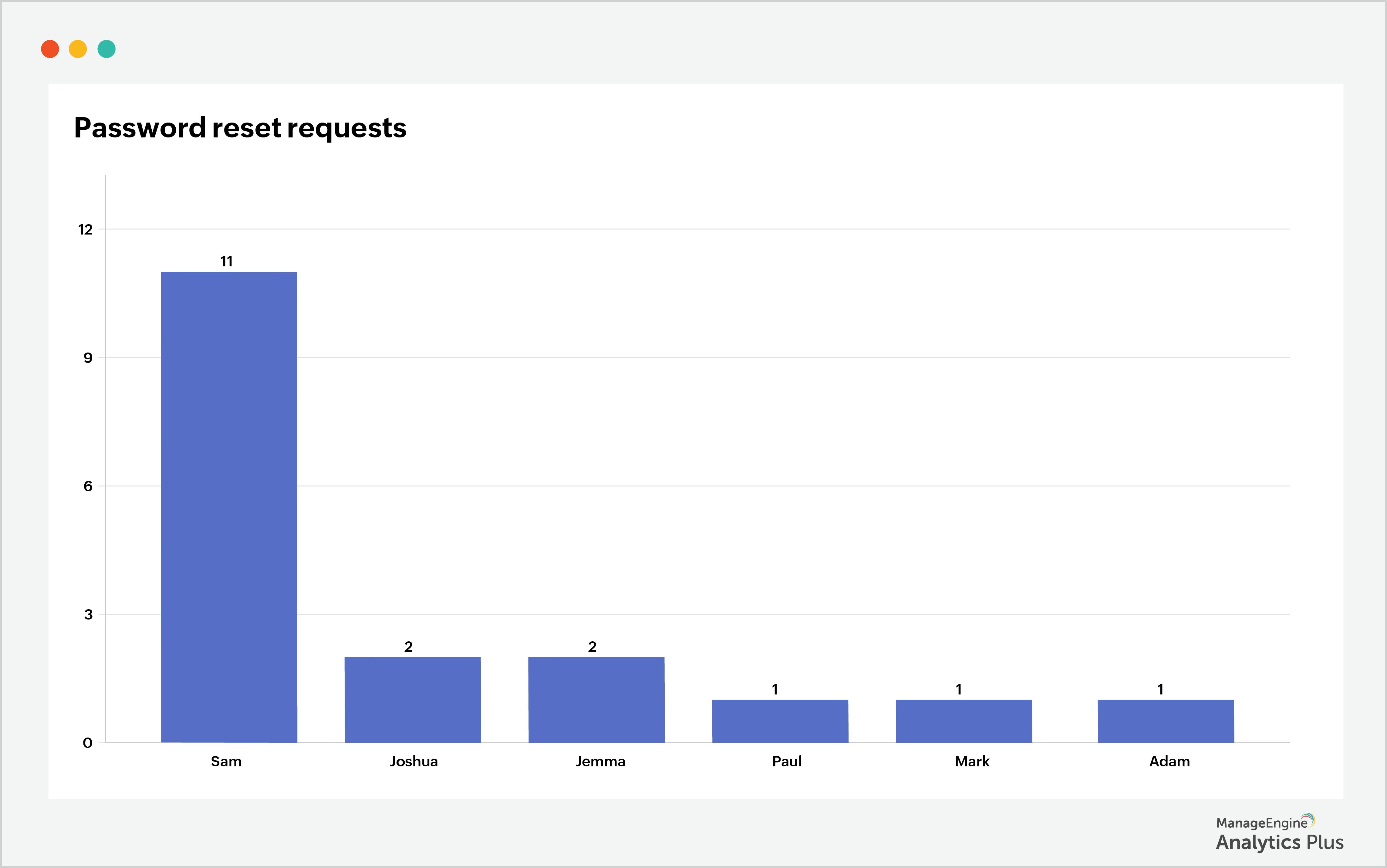
3. Monitor password reset requests from privileged accounts: Privileged accounts are master keys that have access to the organization's most sensitive data, networks, and critical systems, which also makes them vulnerable targets to attackers who are relentlessly looking for flaws to exploit an organization's cyberdefense. Once an attacker gets access to a privileged account, it's easy for them to infiltrate other privileged accounts. It is critical to secure privileged accounts. You can do this by monitoring the password reset requests from privileged accounts and watching for spikes. Here's a sample report that shows the password reset requests from privileged accounts.
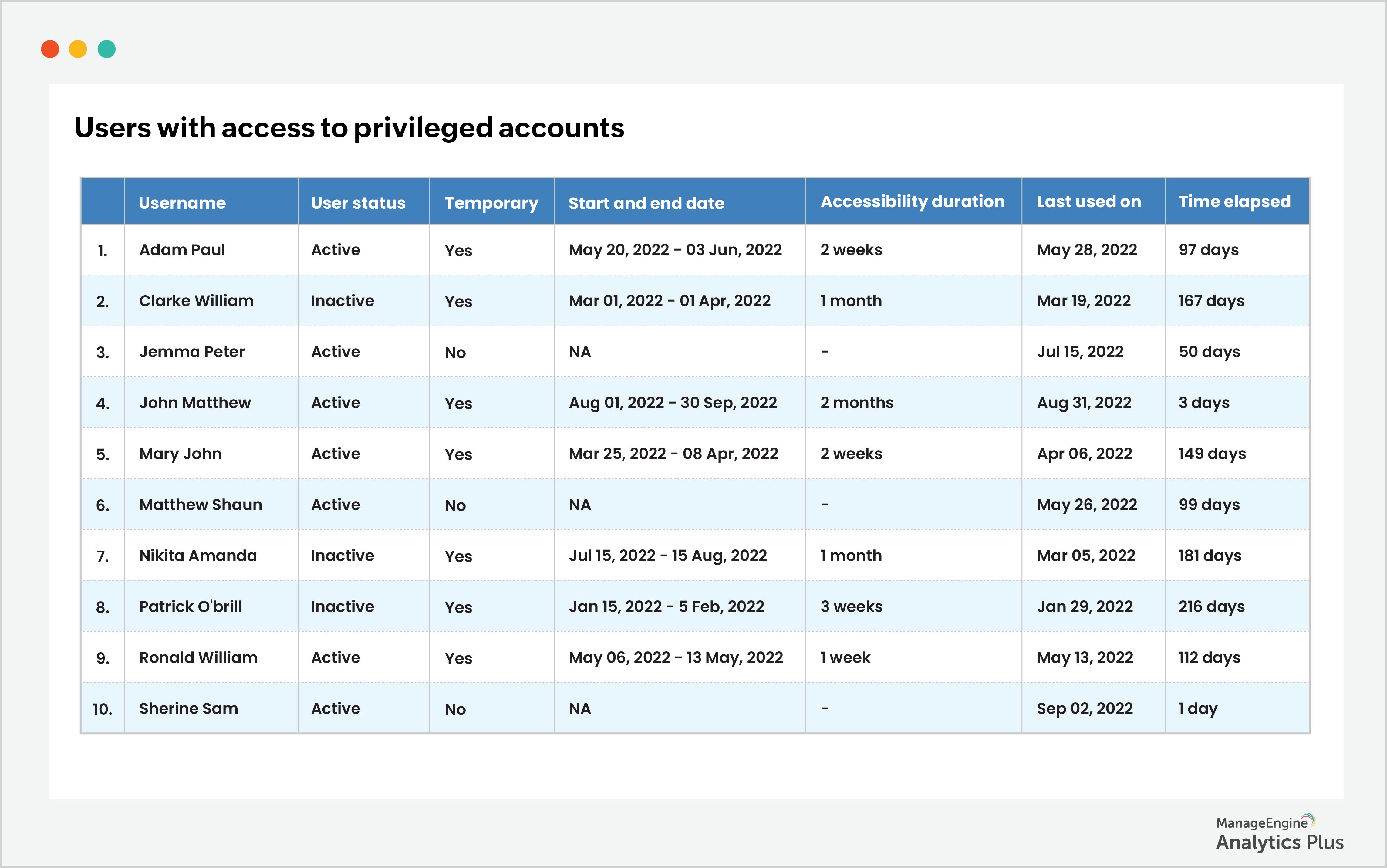
4. Keep track of the privileged accounts accessed: Keeping tabs on who has access to privileged accounts and granting limited, or temporary access, to privileged accounts will prevent your organization from falling prey to attacks. You can also track the privileged users' activity status and revoke access to inactive users. For user accounts that are active but haven't accessed their accounts in three months or more, access can be revoked to ensure security. Here's a report that lists the users categorized by their activity status, their access status, (that is, whether they have temporary or permanent access), and the time elapsed since their last access.
5. User logon patterns in non-working-hours: The best way to identify possible cyberattacks comes from unusual login attempts. For instance, when you notice an employee login in after hours and trying to access files, chances that it could be an attacker are high. Monitoring unusual logon patterns during non-working hours and observing user activity can protect your organization from such threats. Though not all non-working-hours logons indicate a security threat, it is critical to monitor non-working-hours logons and lookout for potential threats.
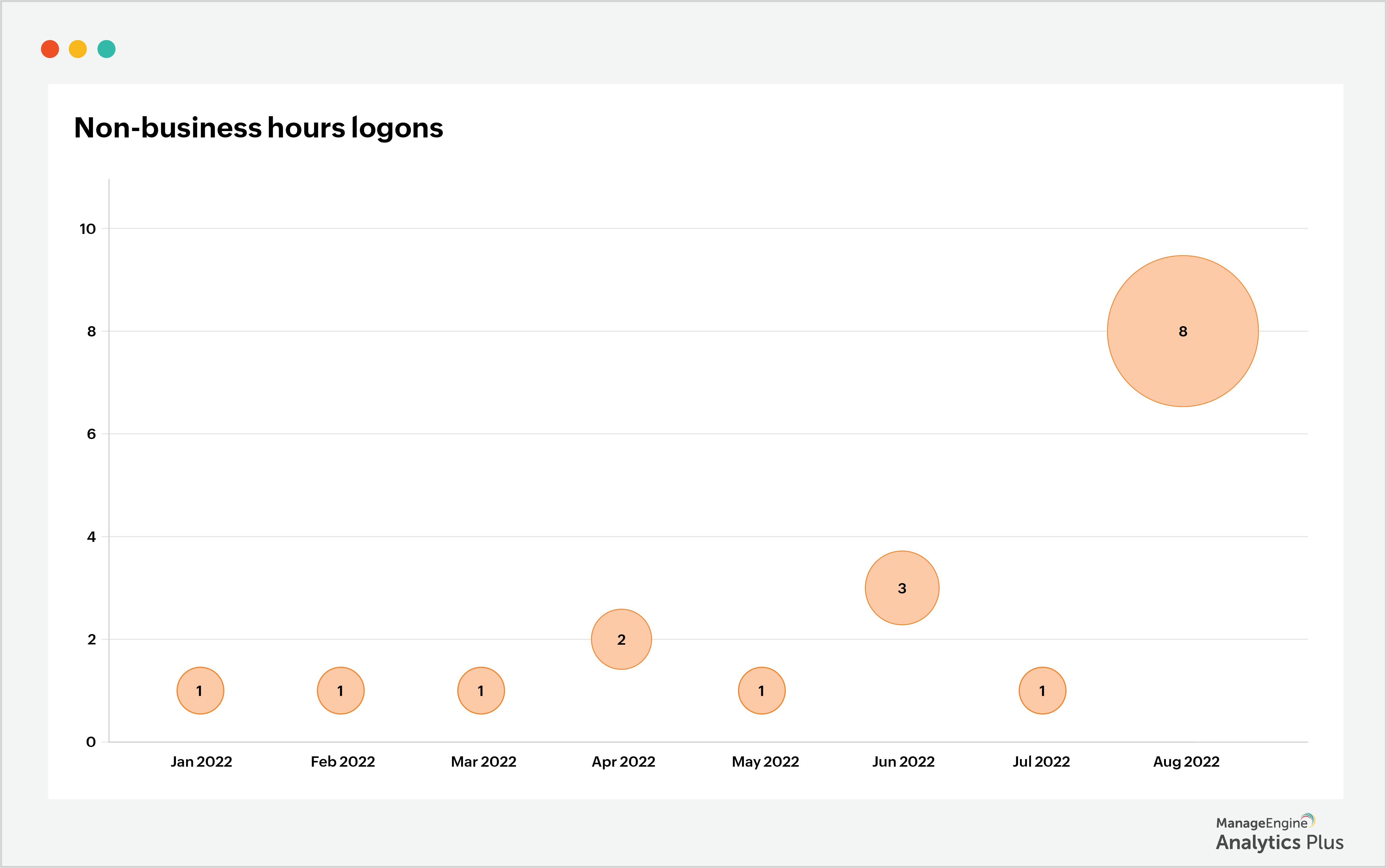
Conclusion
Besides establishing a security fortress, organizations should always keep an eye out for security threats. Tracking every possible point of entry for attacks is a critical step for protecting your sensitive data. Seal all security gaps and periodically check your security perimeter for unauthorized entries or entry attempts. And, finally, educate your employees to always be on guard, use safe networks to login, opt for multi-factor authentication, and follow other security best practices. Analytics can help you ensure users follow these security best practices and help you spot deviations as and when they occur.
These reports were built using Analytics Plus, ManageEngine's AI-enabled IT analytics application. If you'd like to create similar reports using your IT data, try Analytics Plus for free.
Need to know more about analytics for IT operations? Talk to our experts to discover all the ways you can benefit from deploying analytics in your IT.





