Prevent data leaks linked to USB devices, Outlook clients, file sharing, clipboard activity, and more.
Monitor and control the use of USBs, emails, printers, clipboards, and more across your organization.
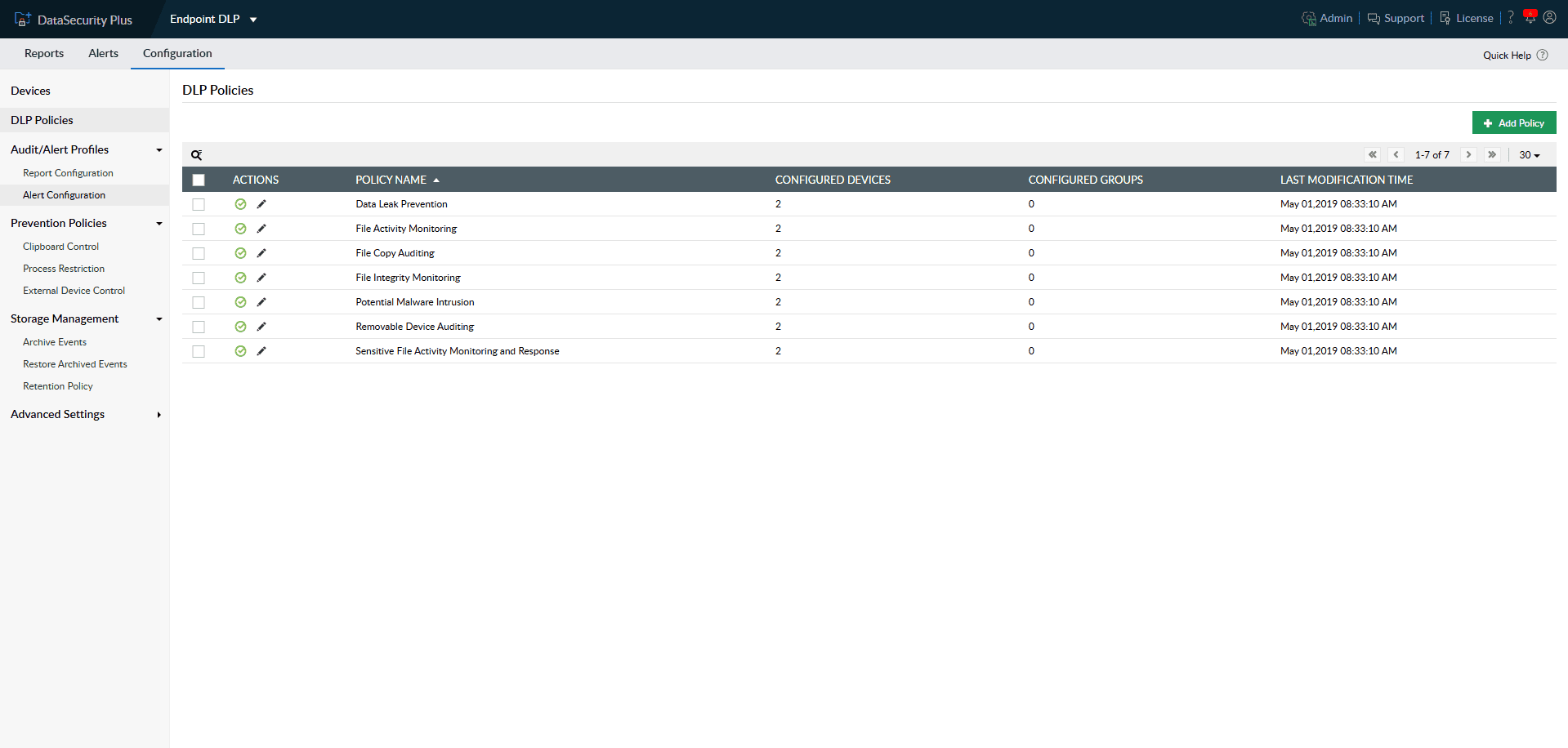
Speed up incident detection with multiple predefined DLP security policies that help respond to unauthorized data movement, malware intrusion, and more.
Stop security incidents before they occur by blocking unwarranted file copy actions, stopping high-risk executables from running, and more.
1.Improved data control: Monitor and control the use of USBs, emails, printers, clipboards, and more across your organization.
2.Preconfigured security: Speed up incident detection with multiple predefined DLP security policies that help respond to unauthorized data movement, malware intrusion, and more.
3.Employ prevention strategies: Stop security incidents before they occur by blocking unwarranted file copy actions, stopping high-risk executables from running, and more.
Granularly control and limit external storage devices' capabilities like read, write, and execute access.
Direct which groups can access multiple endpoint devices, including Wi-Fi routers, Bluetooth adapters, CD/DVD drives, floppy drives, and more.
Create device blocklists to prohibit the use of suspicious and unvetted devices across your endpoints.
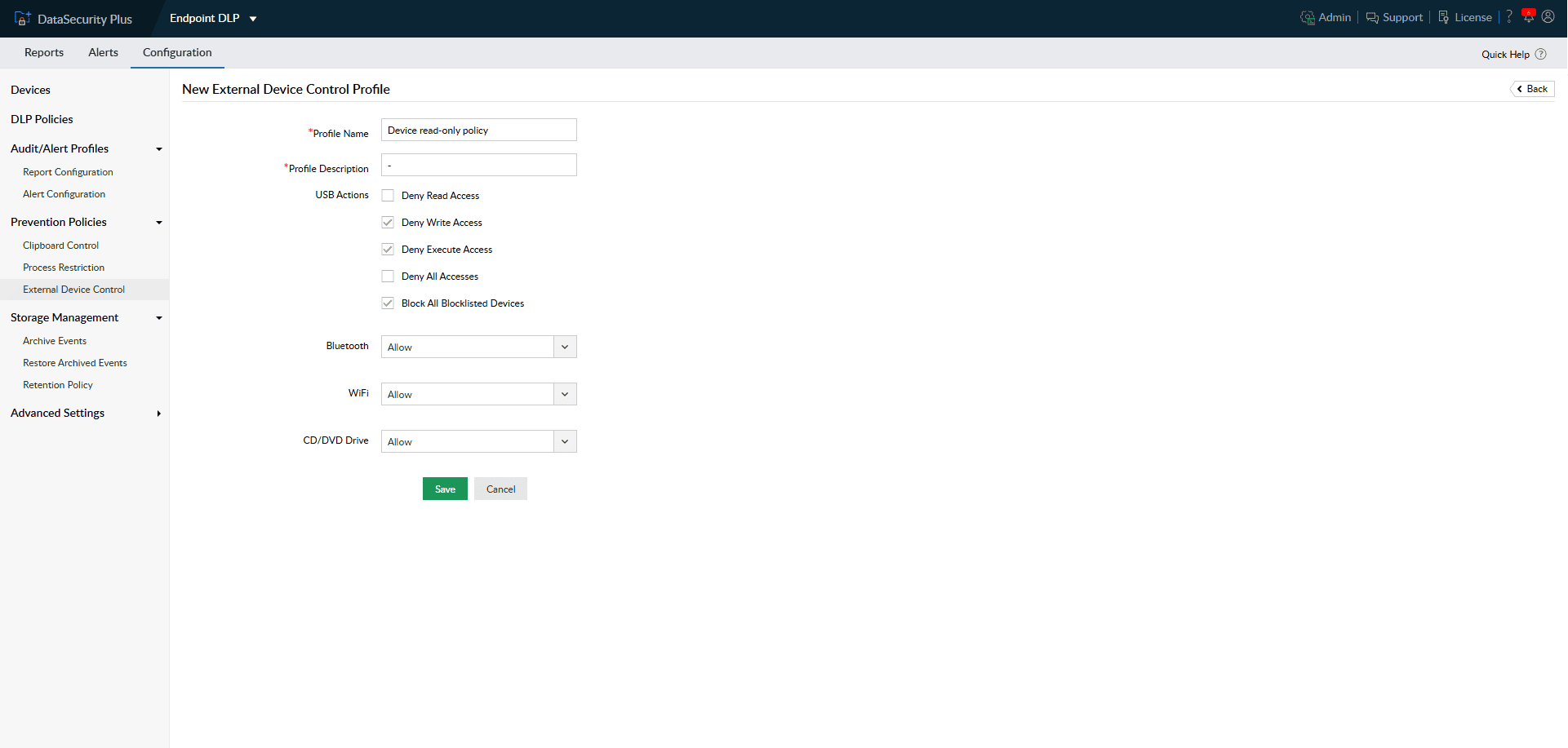
1.Control USB usage: Granularly control and limit external storage devices' capabilities like read, write, and execute access.
2.Manage endpoint devices: Direct which groups can access multiple endpoint devices, including Wi-Fi routers, Bluetooth adapters, CD/DVD drives, floppy drives, and more.
3.Restrict blocklisted device: Create device blocklists to prohibit the use of suspicious and unvetted devices across your endpoints.
Assess and handle critical policy violations using custom scripts or default remediation options for deleting and quarantining files.
Detect ransomware infections across local systems and initiate custom scripts to shut down the infected system, disconnect corrupted devices from the network, and more.
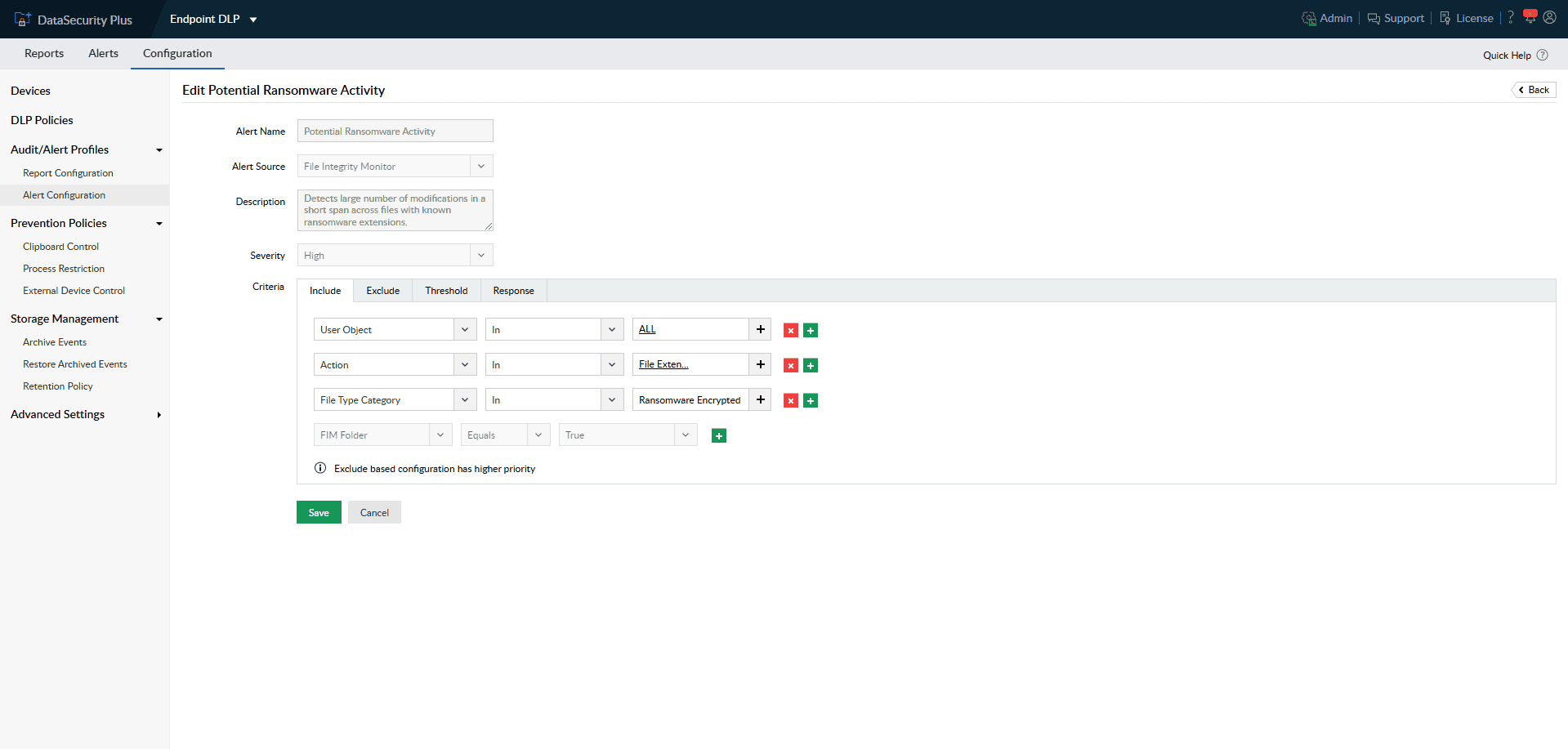
1.Activate threat management: Assess and handle critical policy violations using custom scripts or default remediation options for deleting and quarantining files.
2.Contain ransomware attacks: Detect ransomware infections across local systems and initiate custom scripts to shut down the infected system, disconnect corrupted devices from the network, and more.
Track the movements of highly sensitive files and configure policies to restrict both local and network file copy activities.
Pinpoint all movements of the file with restricted classification tags via removable media devices, email, printer, and more.
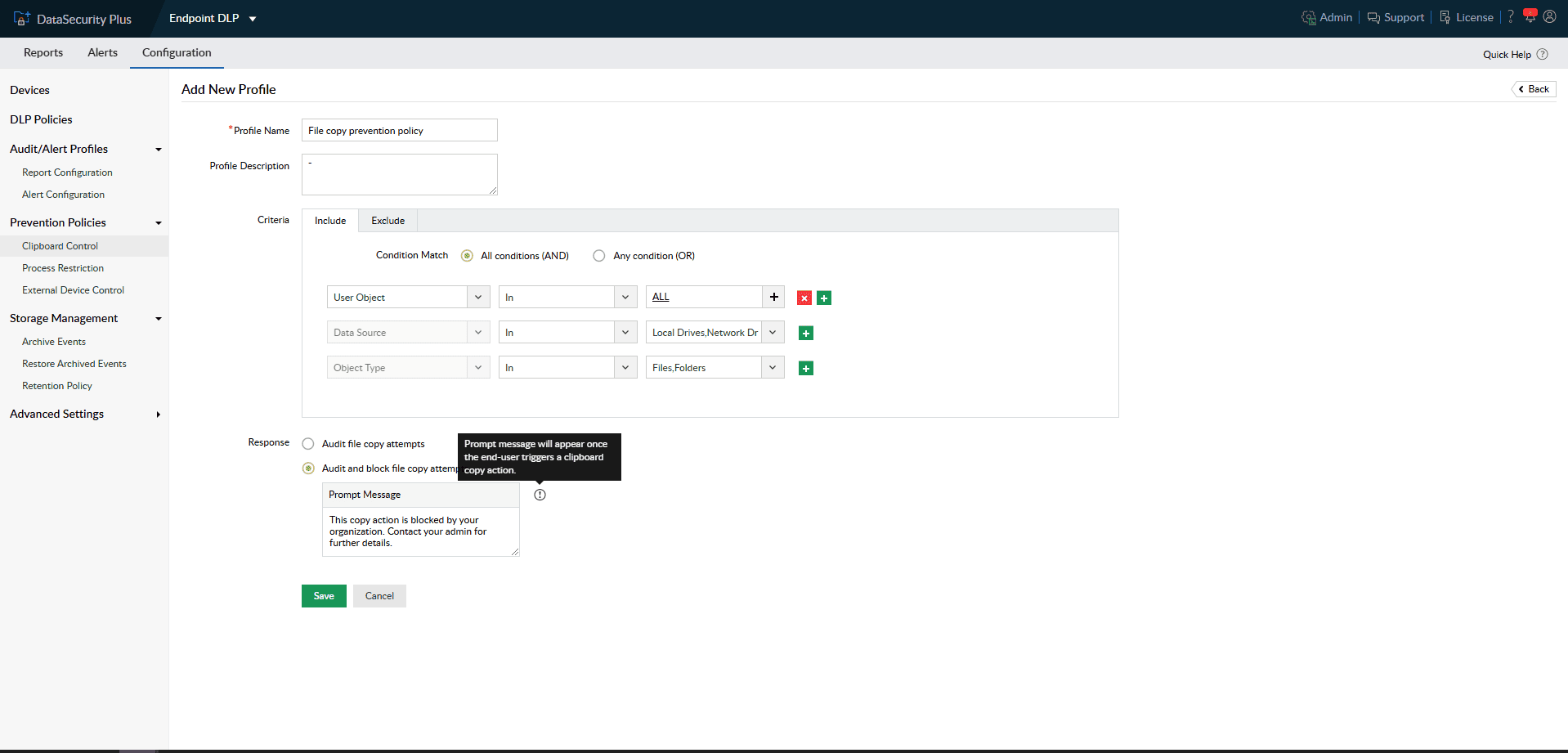
1.Implement file copy limitation: Track the movements of highly sensitive files and configure policies to restrict both local and network file copy activities.
2.Focus on what matters most: Pinpoint all movements of the file with restricted classification tags via removable media devices, email, printer, and more.
Stop users and groups from running any unauthorized executables or scripts that may be malicious.
Address shadow IT concerns by blocking certain applications and processes from running.
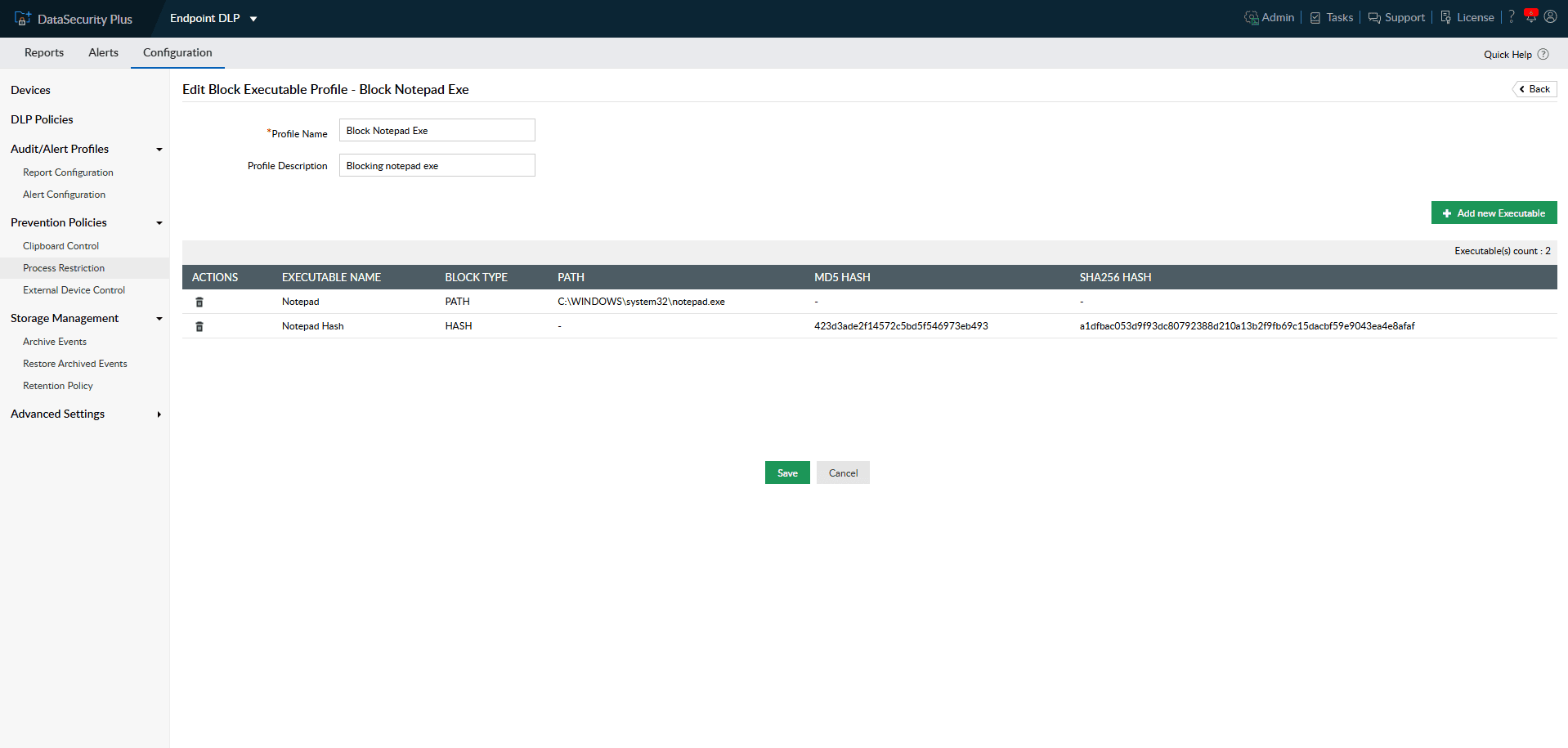
1.Prevent accidental malware execution: Stop users and groups from running any unauthorized executables or scripts that may be malicious.
2.Control applications usage: Address shadow IT concerns by blocking certain applications and processes from running.
Choose to block file uploads from various cloud applications that are deemed unauthorized or malicious by your organization.
Block complete access to cloud apps and suites, block specific domains, block file transfers to and from storage services, and much more.
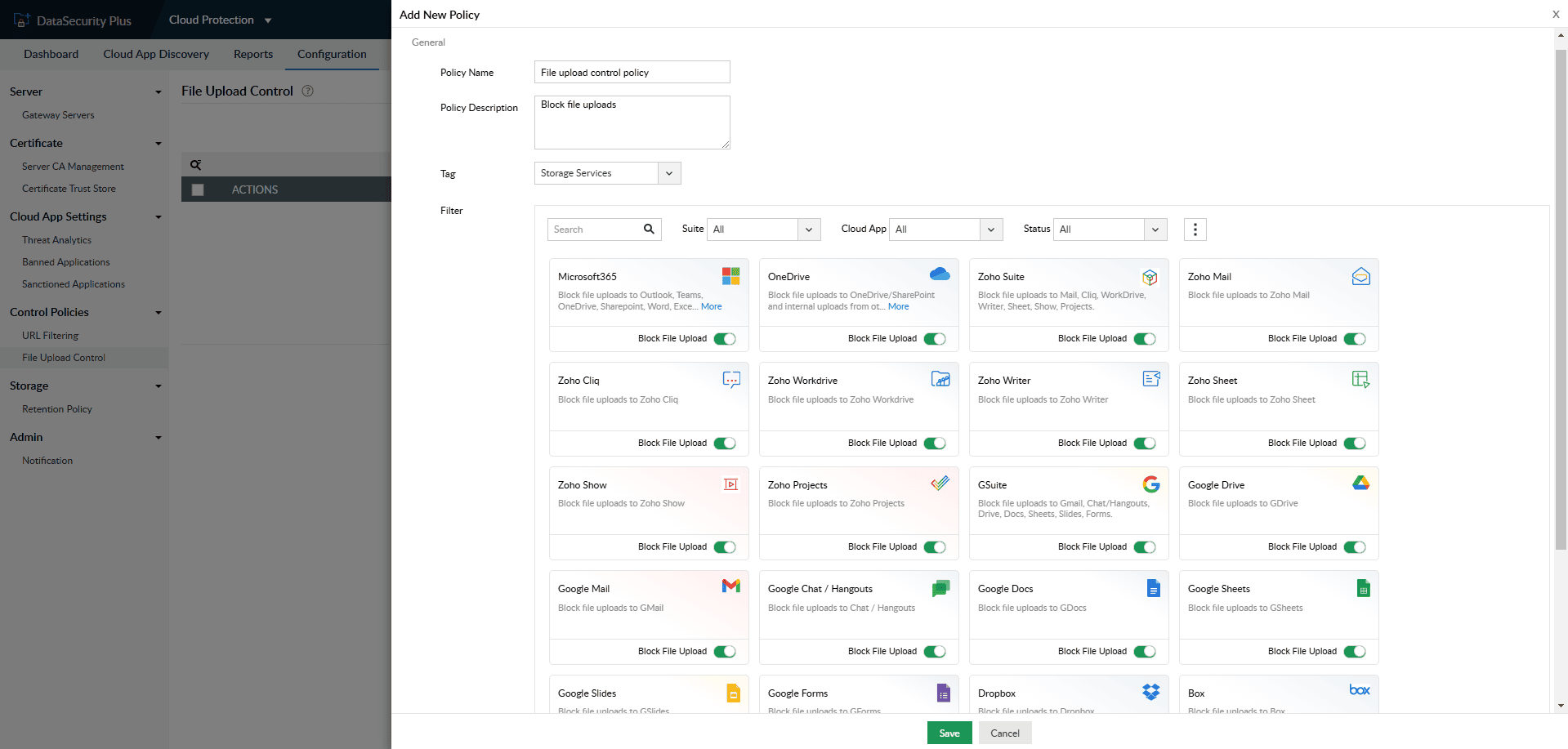
1.Block unsafe file transfers: Choose to block file uploads from various cloud applications that are deemed unauthorized or malicious by your organization.
2.All around content control: Block complete access to cloud apps and suites, block specific domains, block file transfers to and from storage services, and much more.
Thanks! One of our solution experts will get in touch with you shortly.
Monitor, analyze, and report on all file server accesses and modifications in real time.
Learn moreAnalyze file security permissions, optimize disk space usage, and manage junk files.
Learn moreDiscover sensitive personal data, and classify files based on their level of vulnerability.
Learn moreReport on enterprise web traffic, and control the use of web applications.
Learn morePerfect your DLP strategy with this detailed guide on developing an effective DLP plan.