Set up ransomware alert and response
Multiple file modifications in a short period of time and evidence of encryption are two telltale signs of ransomware. Using a few simple patterns, DataSecurity Plus can detect these signs of ransomware early on and identify attacks right as they happen. Follow the steps below to configure DataSecurity Plus' automated threat response mechanism to shut down any ransomware attack right at its inception.
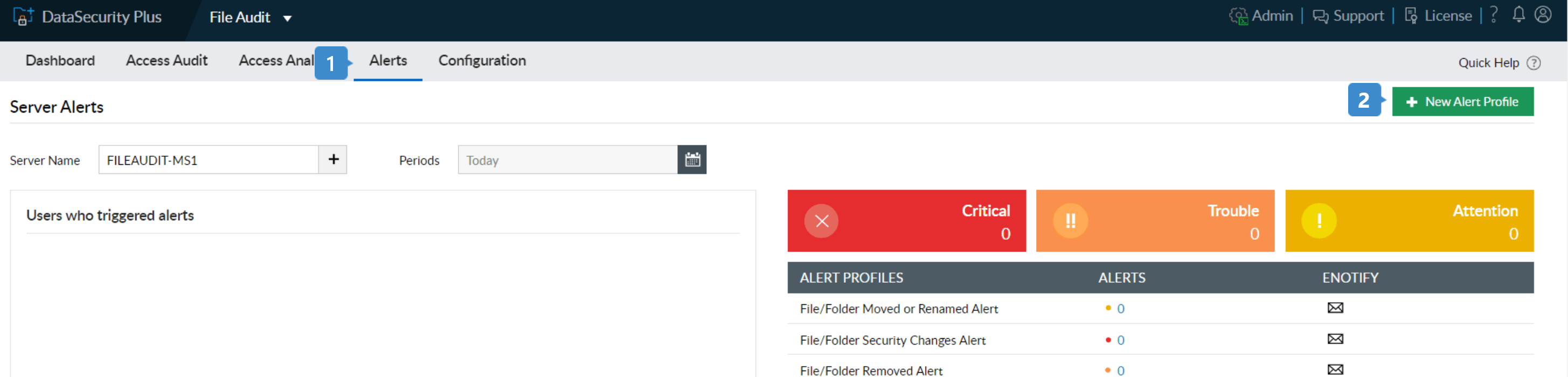
- 1. Run DataSecurity Plus Navigate to the Alerts tab
- 2. Click + New Alert Profile on the top right corner of the page.
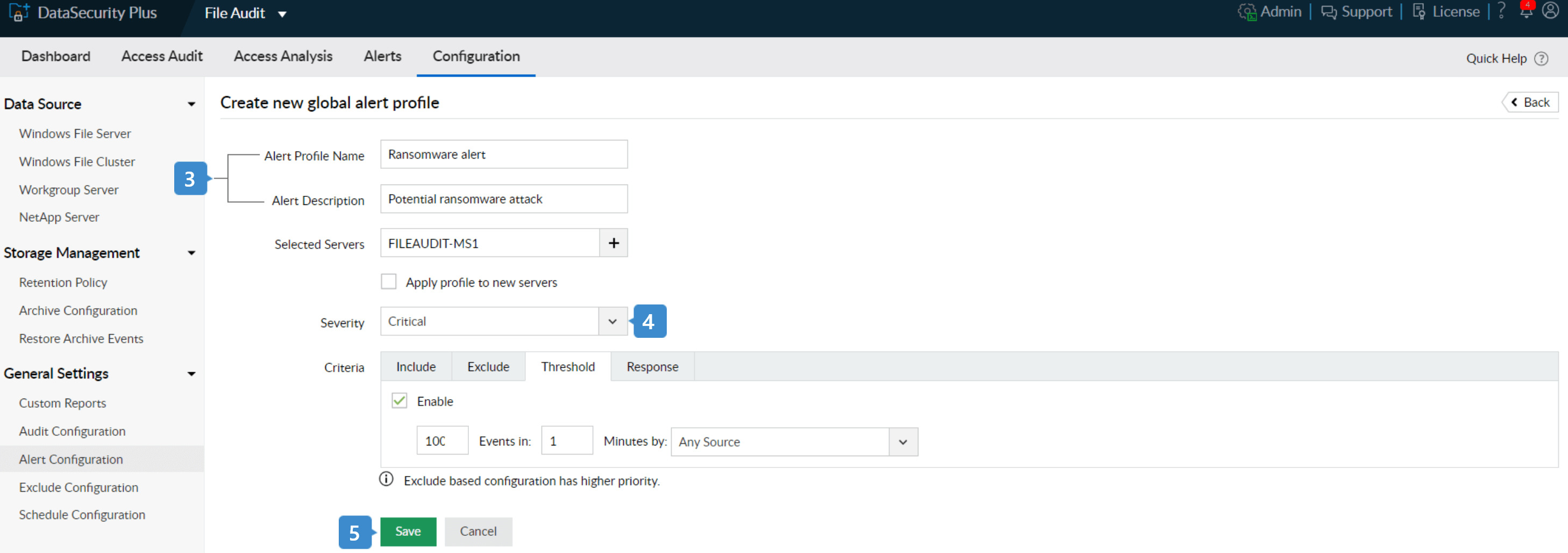
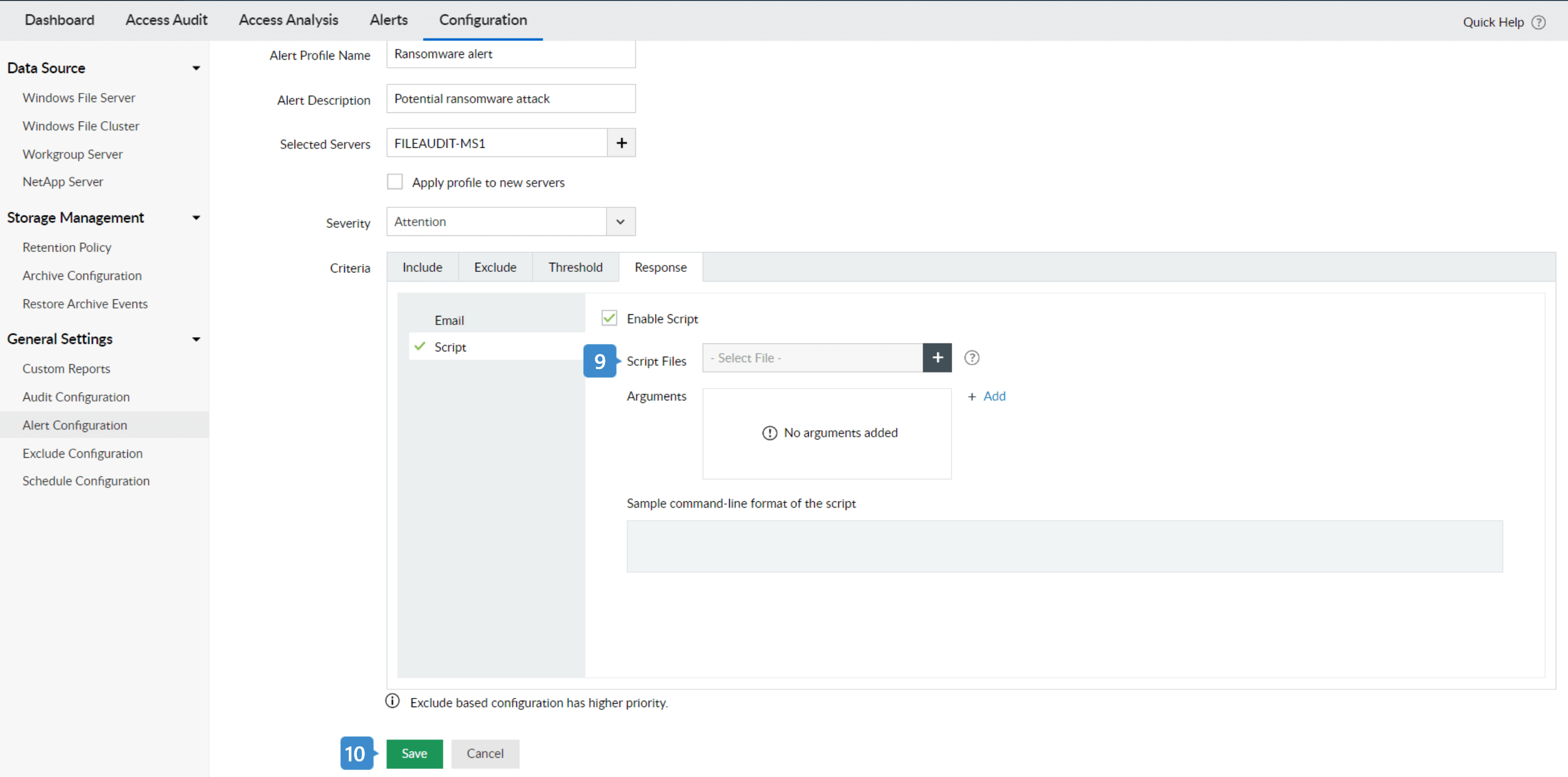
- 3. Name the alert profile and include an appropriate description (e.g., "Potential ransomware attack”).
- 4. In the Severity tab, select Critical.
- 5. Check the Threshold Limit section and specify the number of events to be monitored (e.g., "100 file modifications in one minute")*.
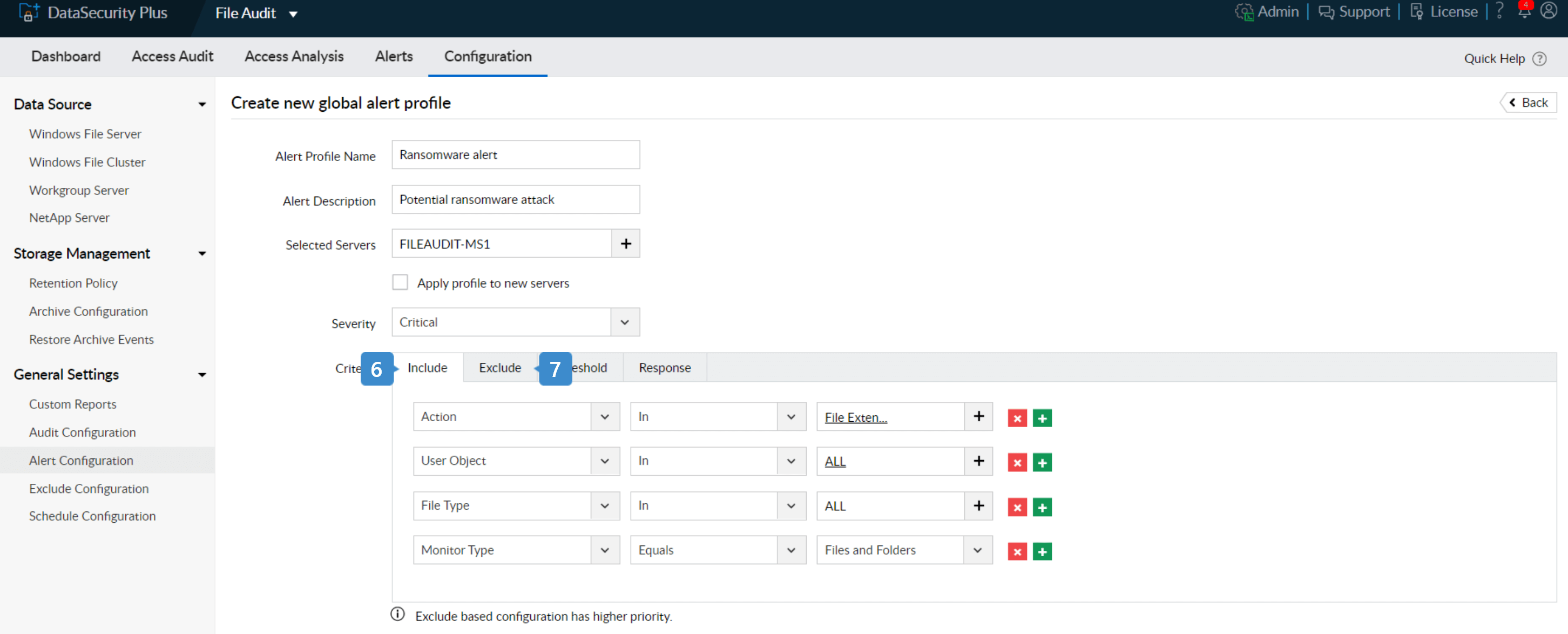
- 6. Navigate to the criteria section and add these filters under the Include tab:
- Actions: Create, Modify, Rename, and File Extension Change
- Monitor Type: Files and folders
- File Type: All
- User Object: All
- 7. Use the Exclude tab to ignore individual files, organization specific file types, and folders for selective monitoring to reduce false positives.
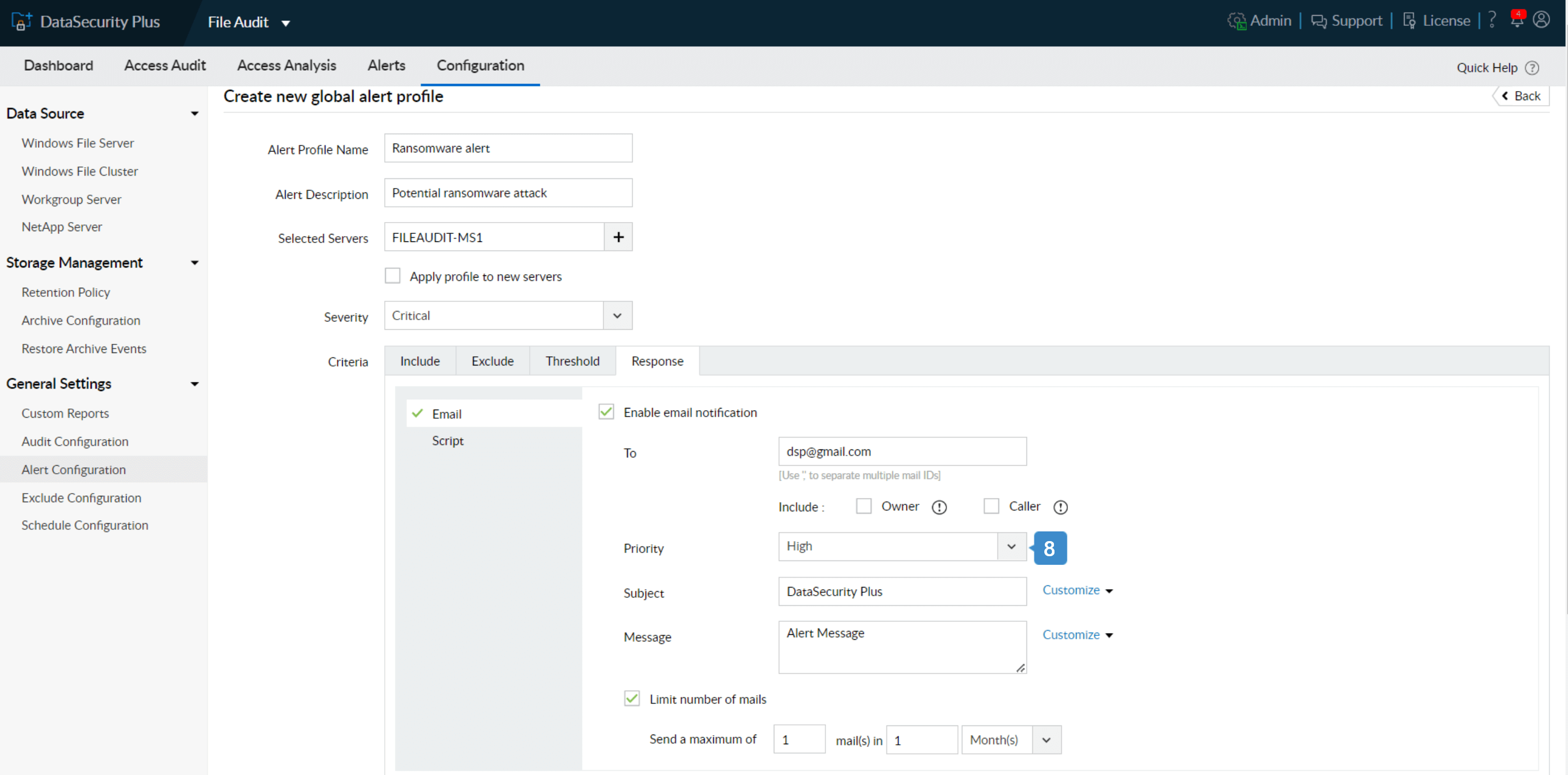
- 8. Check the Email Notifications option and specify one or more email addresses you'd like to send alerts to. Set Email Priority to High.
- 9. In the Script Files text box, select the script based on your business needs. Ensure to save the script in [installation_directory]\bin\alertScripts] path for DataSecurity Plus to execute them. Note: You can also execute other scripts that disable user account, disable network, or one of your own scripts tailored to your organization's needs.
- 10. To save the configured alert, click Save.
You have now successfully configured DataSecurity Plus to detect and respond to a scenario where more than 100 files events such as create, modify, and rename are detected within one minute.
*The threshold limit will vary depending on the server size, the number of users, and on its usage level.