Steps to configure OAuth/OpenID-Connect-based SSO for PingOne
About PingOne
PingOne is a cloud-based Identity as a Service platform that provides identity management capabilities for workforces.
The following steps will help you enable OAuth/OpenID-Connect-based single sign-on (SSO) for PingOne from ManageEngine Identity360.
Prerequisites
- The MFA and SSO license for Identity360 is required to enable SSO for enterprise applications. For more information, refer to the pricing details.
- Log in to Identity360 as an Admin or Super Admin, or as a Technician with a role that has Application Integration and Single Sign-on permissions.
- Navigate to Applications > Application Integration > Create New Application, and select PingOne from the applications displayed.
Note: You can also find PingOne from the search bar located at the top.
- Under the General Settings tab, enter the Application Name and Description.
- Under the Choose Capabilities tab, choose SSO and click Continue.
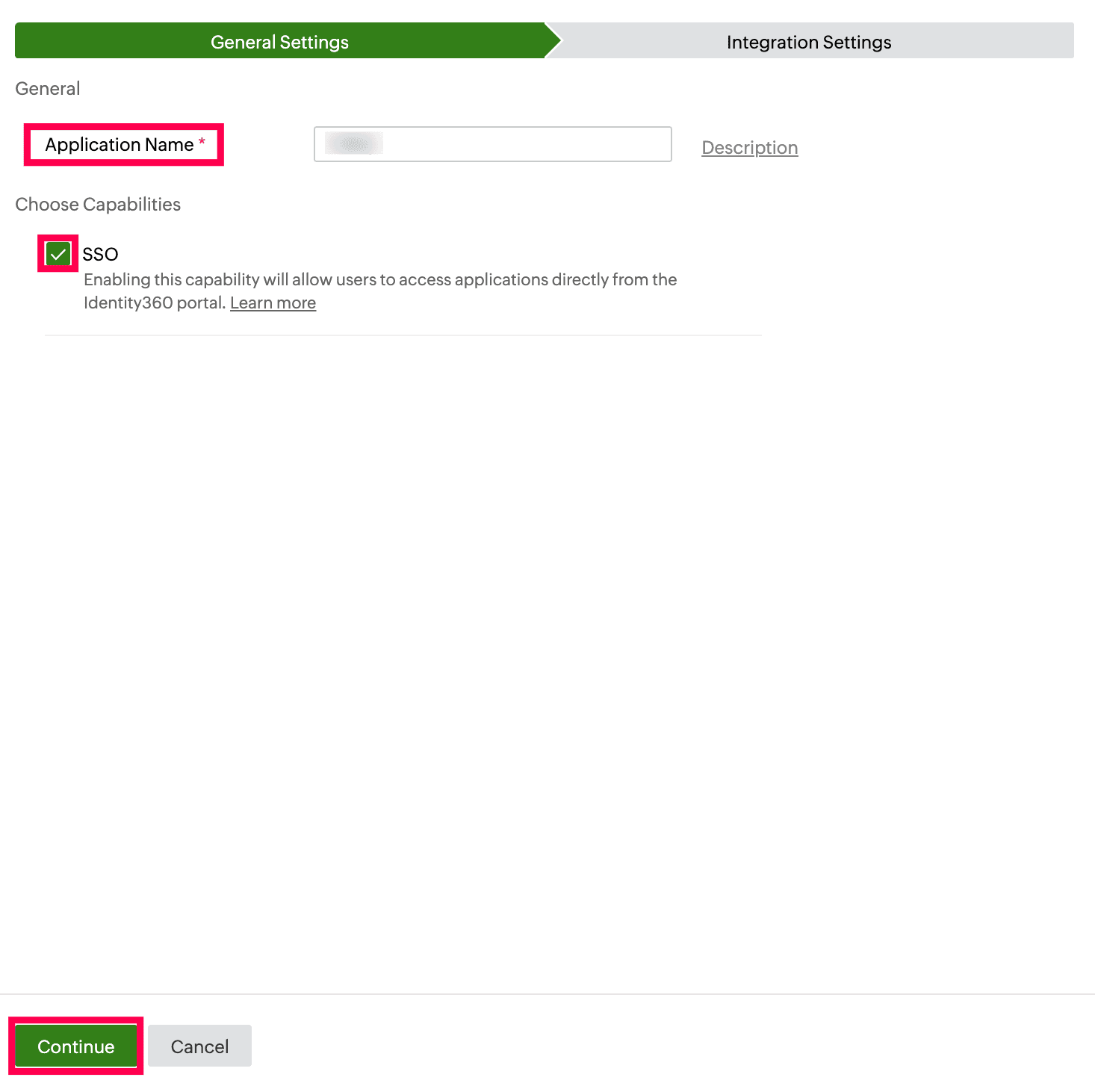 General Settings of SSO configuration for PingOne.
General Settings of SSO configuration for PingOne.
- Under Integration Settings, navigate to the Single Sign On tab, and select OAuth/OpenID Connect from the Method radio button. Click IdP Details and copy the highlighted field values in the screenshot below.
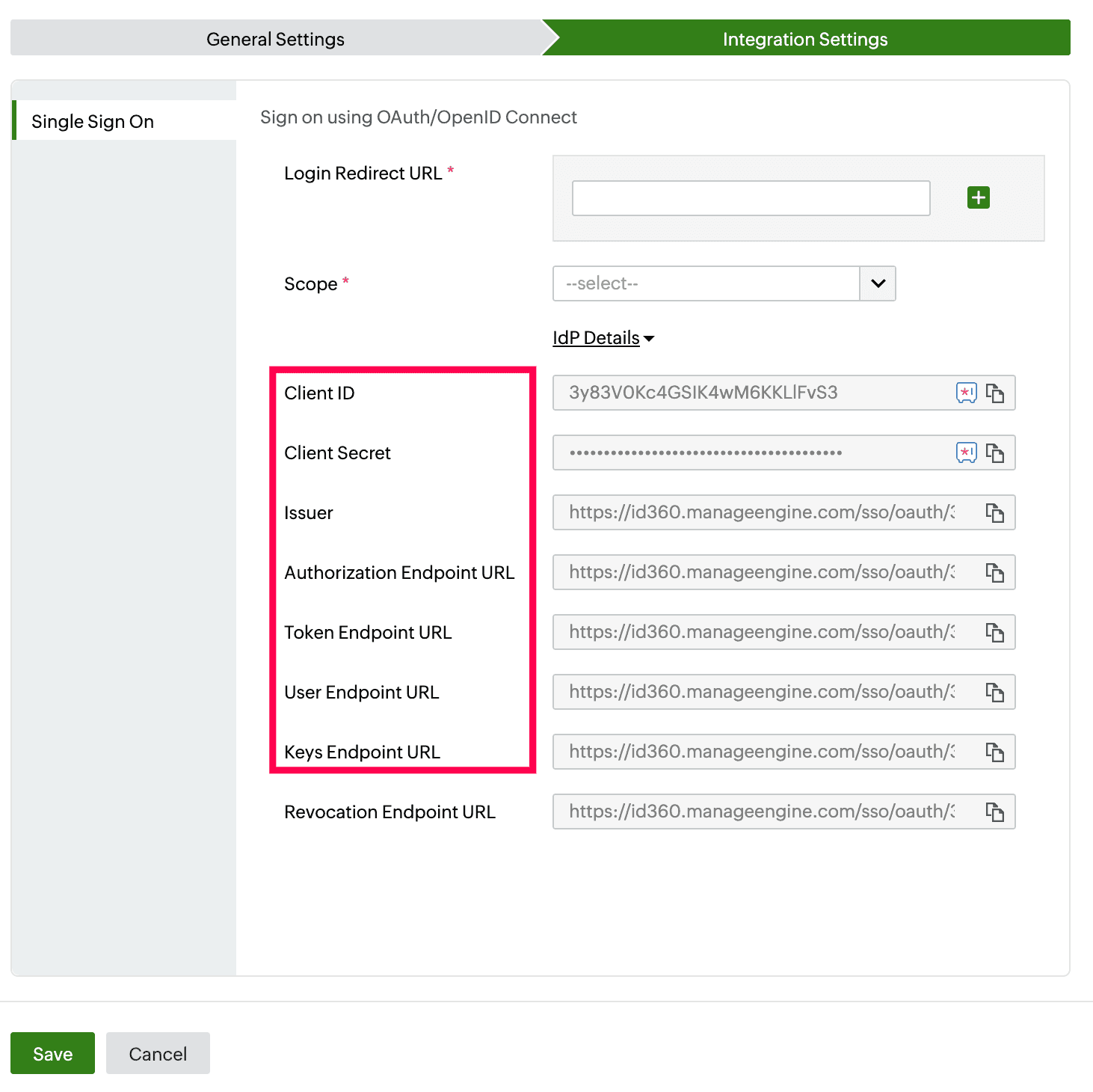 Integration Settings of SSO configuration for PingOne.
Integration Settings of SSO configuration for PingOne.
PingOne (service provider) configuration steps
- Log in to PingOne as an administrator.
- Go to Environments > End User Sandbox environment > Manage Environment.
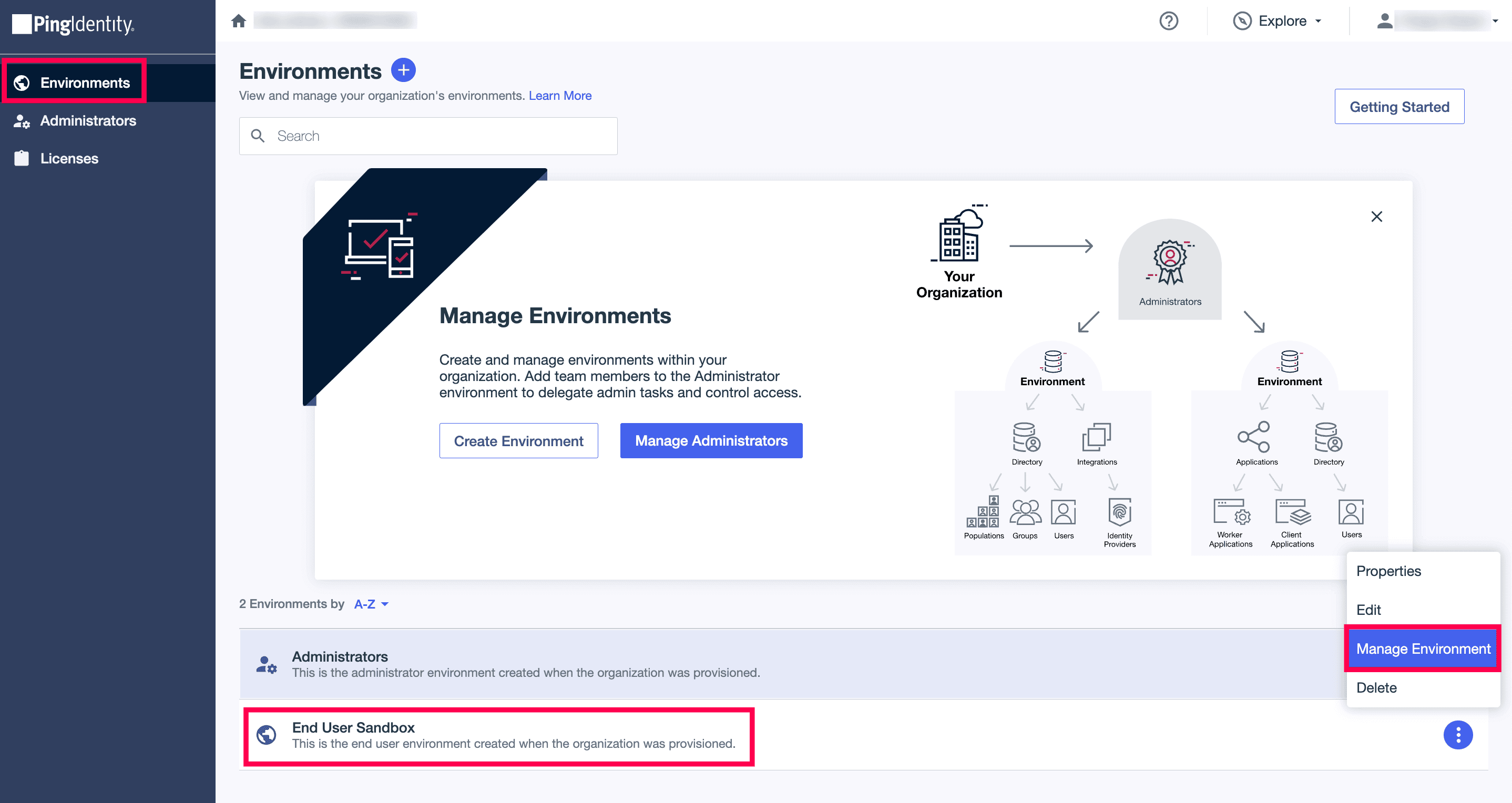 PingOne admin portal view.
PingOne admin portal view.
- Click Integrations > External IdPs > + Add Provider.
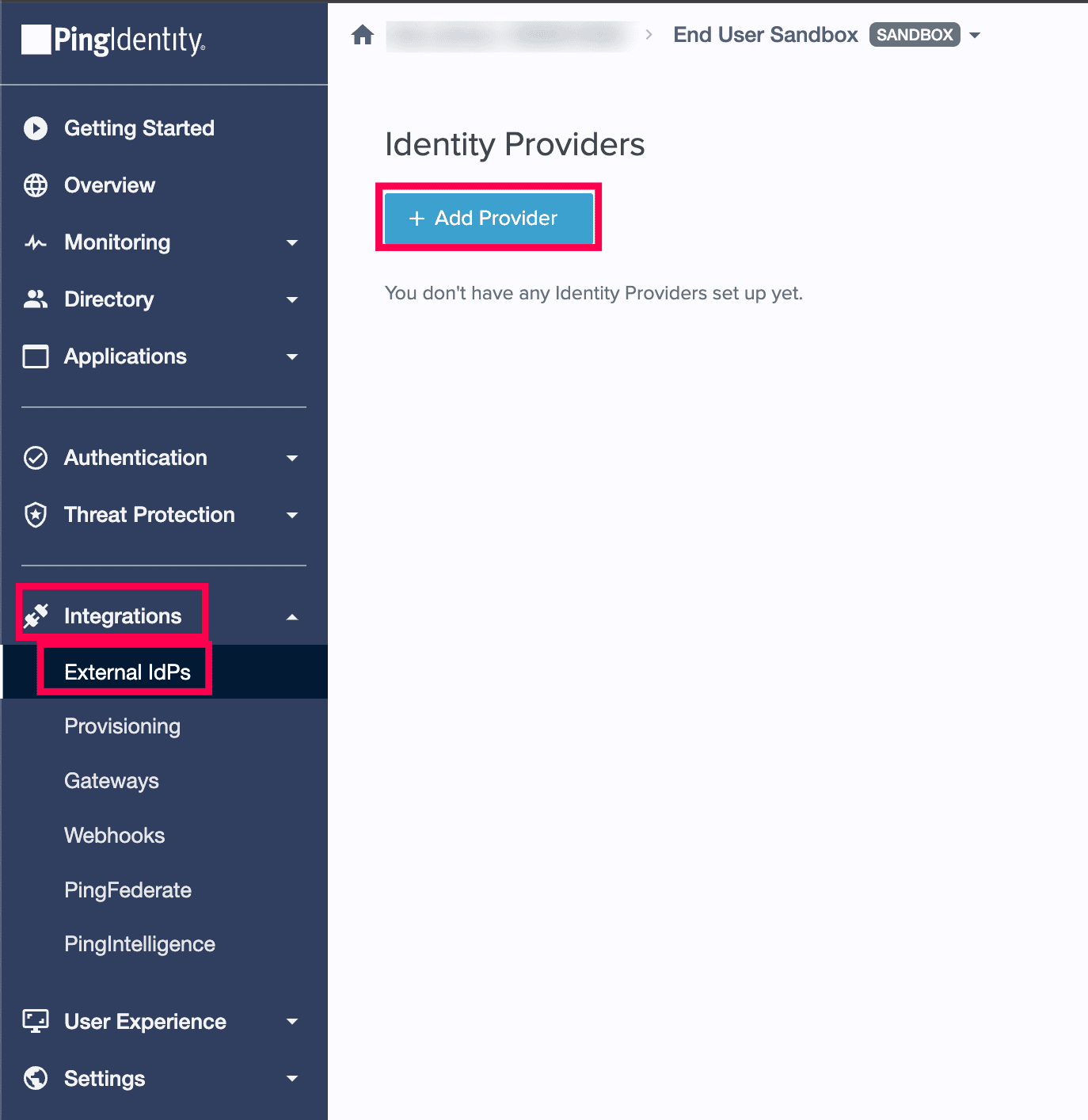 Adding an identity provider from PingOne.
Adding an identity provider from PingOne.
- Select OPENID CONNECT.
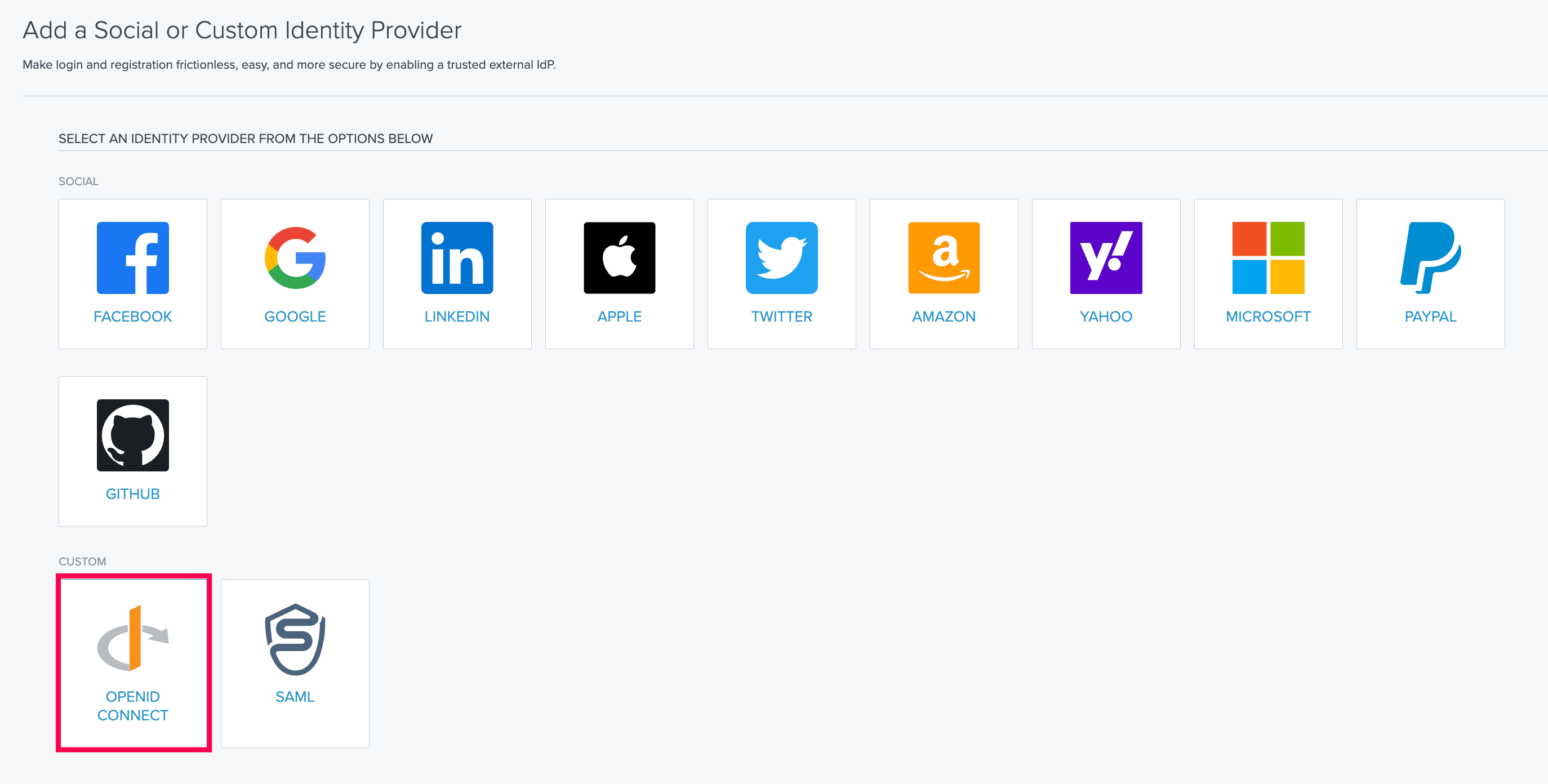 Select OIDC IdP from PingOne.
Select OIDC IdP from PingOne.
- Under Create Profile, enter a suitable name for Identity360. You can also give a description and customize the icon and login button in this section. Click Continue.
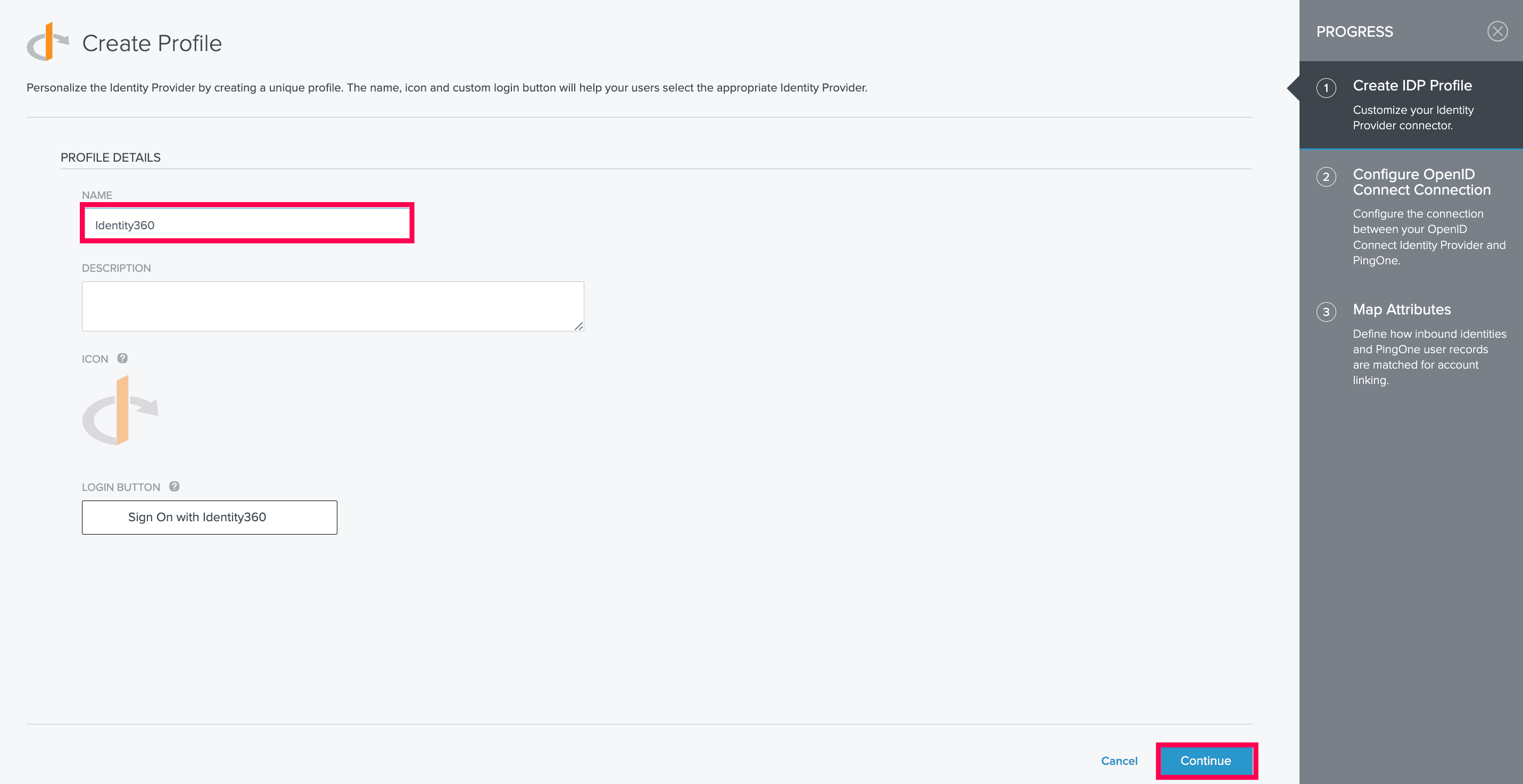 Creating an IdP profile in PingOne.
Creating an IdP profile in PingOne.
- On the Configure OpenID Connect Connection page, copy the CALLBACK URL, as it will be required during Identity360 configuration.
- Fill in the required fields with details copied in step 6 of the prerequisites:
- CLIENT ID: Client ID
- CLIENT SECRET: Client Secret
- AUTHORIZATION ENDPOINT: Authorization Endpoint URL
- TOKEN ENDPOINT: Token Endpoint URL
- JWKS ENDPOINT: Keys Endpoint URL
- ISSUER: Issuer
- USER INFORMATION ENDPOINT: User Endpoint URL
- Under the REQUESTED SCOPES field, enter openid, email, profile.
- Under the TOKEN ENDPOINT AUTHENTICATION METHOD field, choose the Client Secret Basic radio button.
- Click Save and Continue.
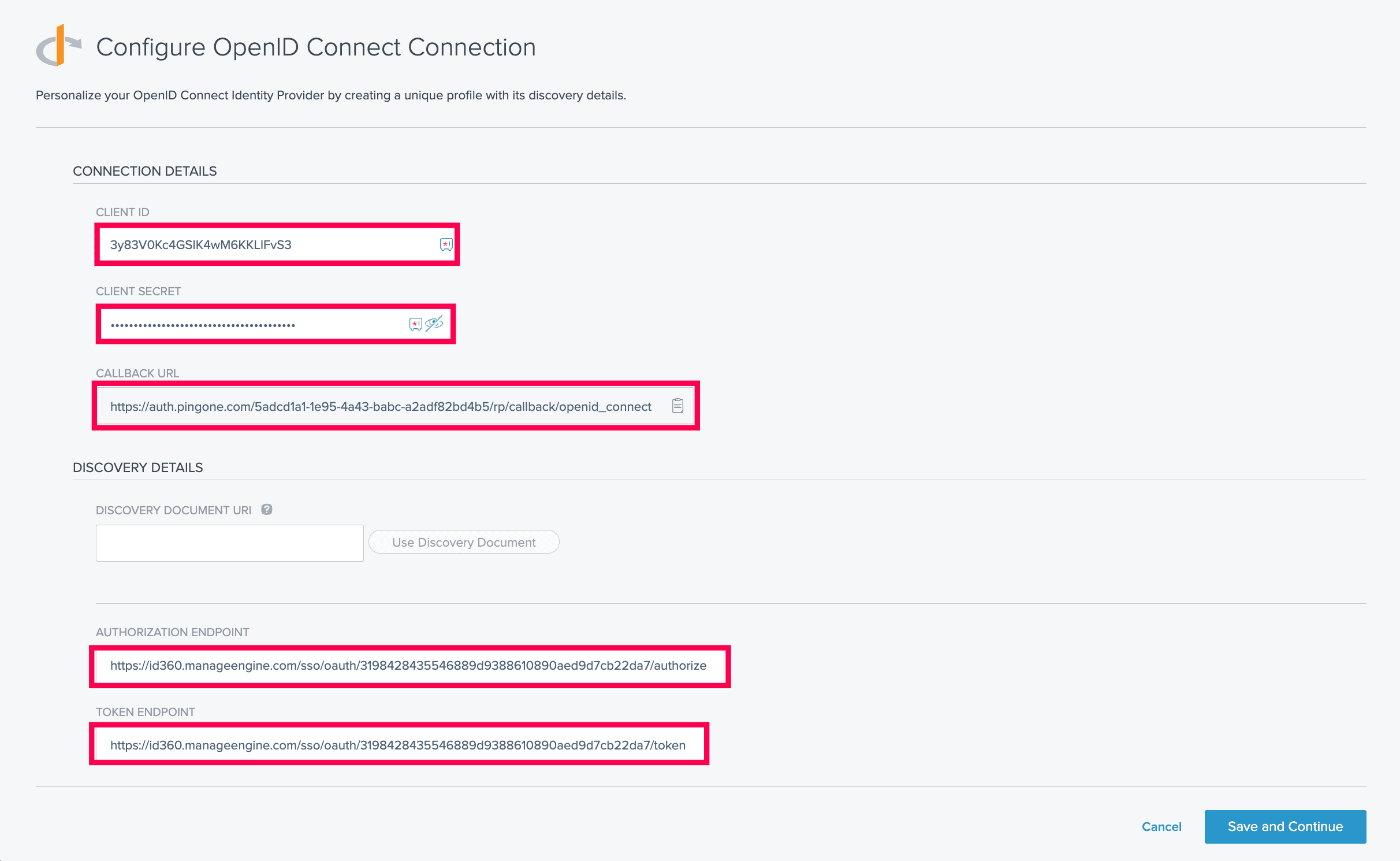 Configuring the OIDC connection in PingOne.
Configuring the OIDC connection in PingOne.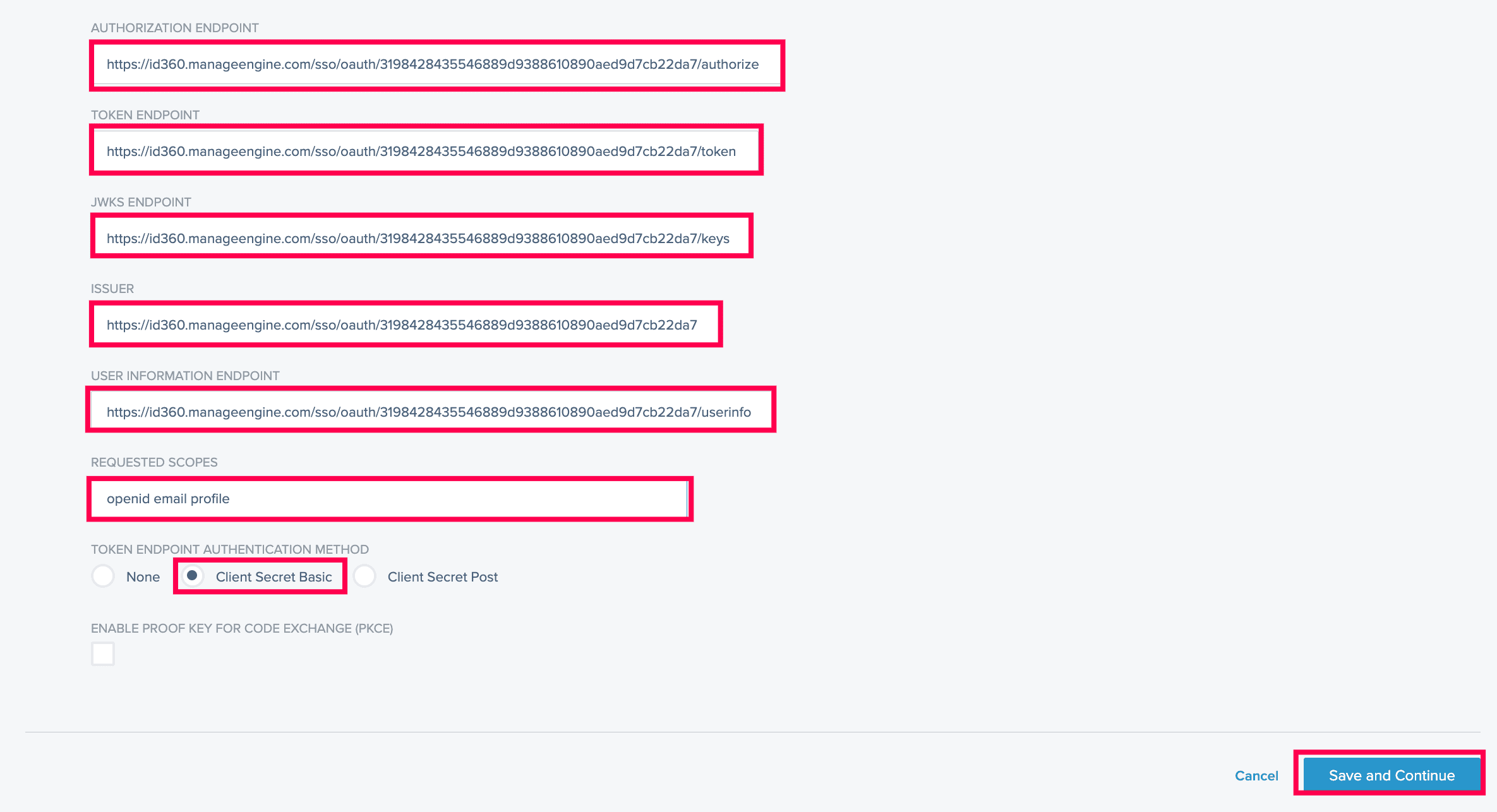 Configuring the OIDC connection in PingOne.
Configuring the OIDC connection in PingOne.
- On the Map Attributes page, keep the default settings, and click Save & Finish.
 Mapping attributes in PingOne.
Mapping attributes in PingOne.
Identity360 (identity provider) configuration steps
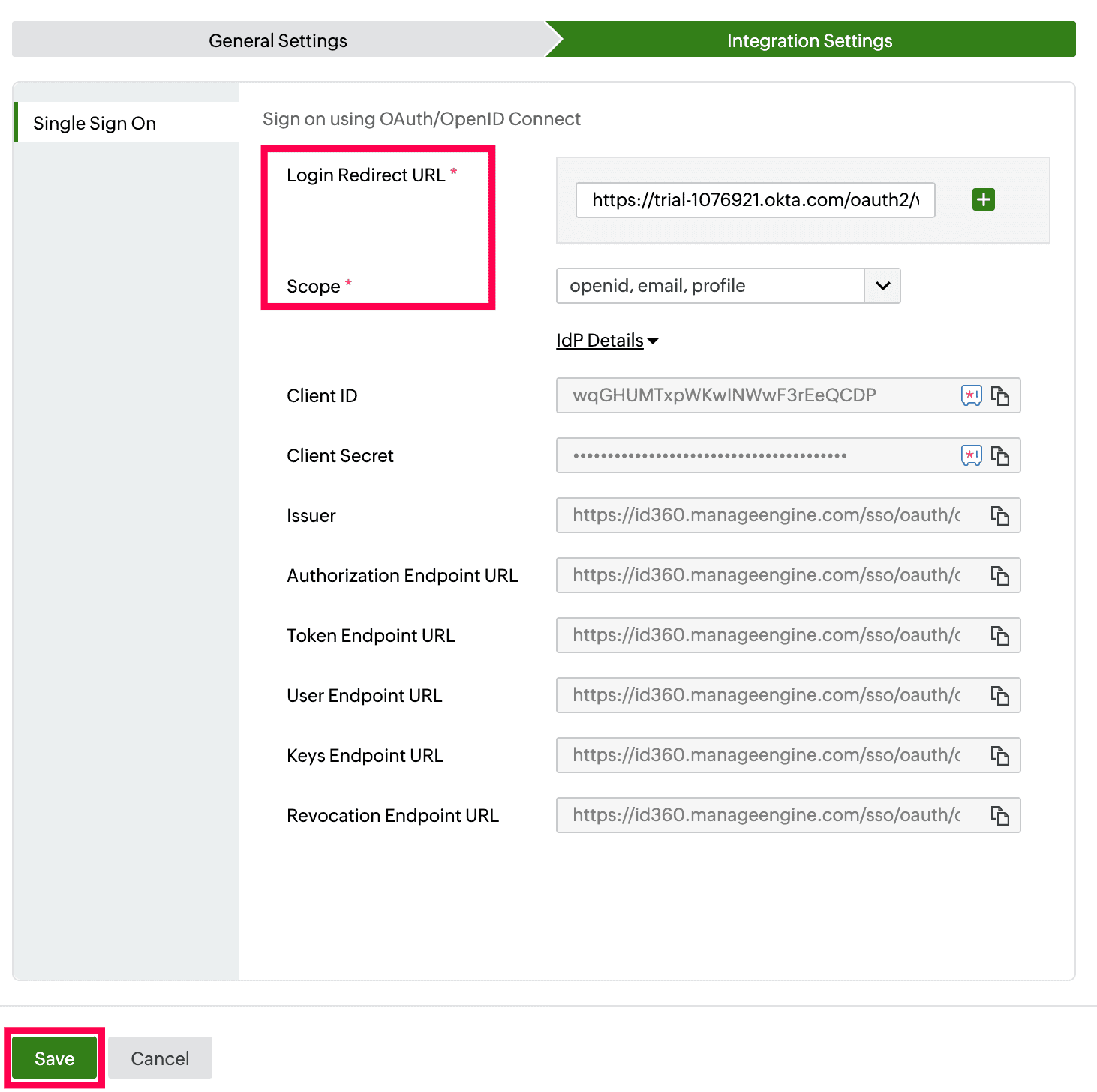
- Switch to Identity360's application configuration page.
- In the Login Redirect URL field, paste the Redirect URI copied from step 6 of PingOne configuration.
- Choose the required Scope from the drop-down.
Note: Relay State is an optional parameter used with a SAML message to remember where you were or to direct you to a specific page after logging in.
- openid: Establishes that this is an OpenID Connect request.
- email: Requests the user's email attribute.
- profile: Requests the user's profile claims (FirstName and LastName).
- Click Save.
 Integration Settings of SSO configuration for PingOne.
Integration Settings of SSO configuration for PingOne.
- To learn how to assign users and groups to one or more applications, refer to this page.
Your users should now be able to sign in to PingOne through the Identity360 portal.
Note: For PingOne, SP-initiated flow is supported when SSO is enabled through OAuth.
Steps to enable MFA for PingOne
Setting up MFA for PingOne using Identity360 involves the following steps:
- Set up one or more authenticators for identity verification when users attempt to log in to PingOne. Identity360 supports various authenticators, including Google Authenticator, Zoho OneAuth, and email-based verification codes. Click here for steps to set up the different authenticators.
- Integrate PingOne with Identity360 by configuring SSO using the steps listed here.
- Now, activate MFA for PingOne by following the steps mentioned here.
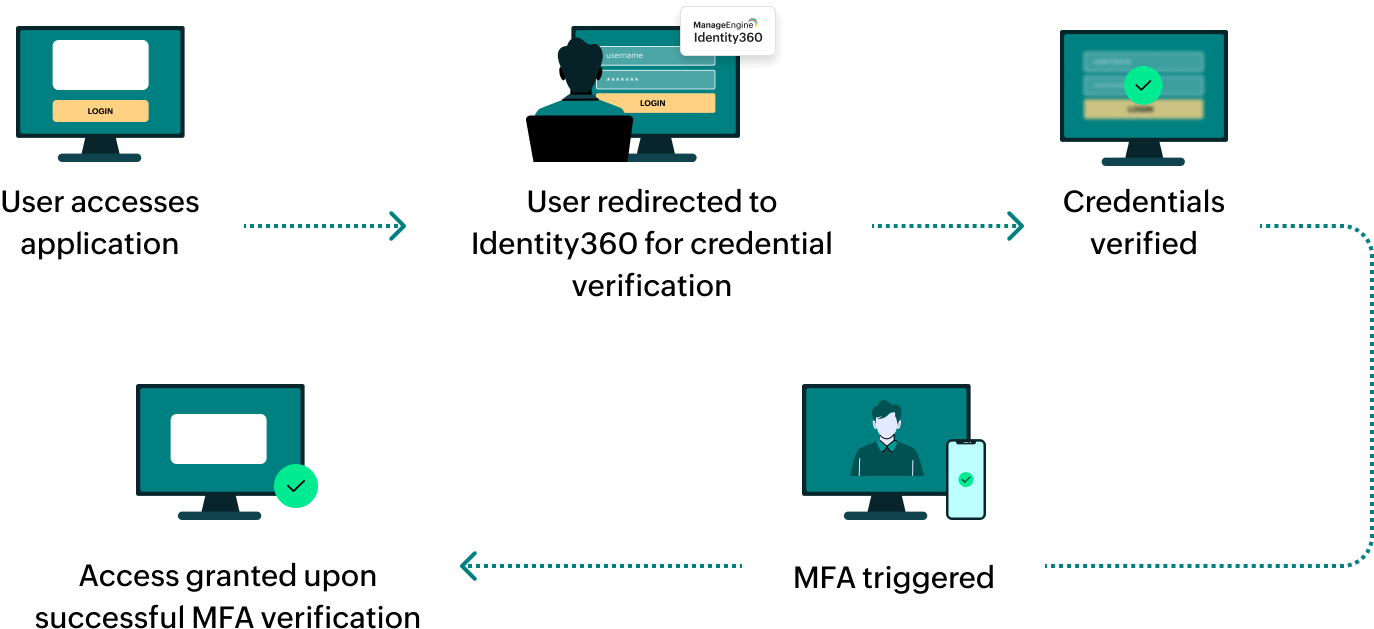
How does MFA for applications work in Identity360?
 General Settings of SSO configuration for PingOne.
General Settings of SSO configuration for PingOne. Integration Settings of SSO configuration for PingOne.
Integration Settings of SSO configuration for PingOne. PingOne admin portal view.
PingOne admin portal view. Adding an identity provider from PingOne.
Adding an identity provider from PingOne. Select OIDC IdP from PingOne.
Select OIDC IdP from PingOne. Creating an IdP profile in PingOne.
Creating an IdP profile in PingOne. Configuring the OIDC connection in PingOne.
Configuring the OIDC connection in PingOne. Configuring the OIDC connection in PingOne.
Configuring the OIDC connection in PingOne. Mapping attributes in PingOne.
Mapping attributes in PingOne. Integration Settings of SSO configuration for PingOne.
Integration Settings of SSO configuration for PingOne.