SSL Vulnerability
1. Overview
As with every technology, the Secure Sockets Layer (SSL) has its own downsides. SSL certificates form the pillars of internet security but merely installing SSL certificates does not suffice. There are a few post-installation configurations to be periodically checked for, in your domain servers to ensure that your website is completely secure from cyber attacks.
Key Manager Plus scans SSL certificates in its repository and flags certificates that are prone to any vulnerability. This way, users are kept informed of certificates / server configurations that are insecure. Users can then take necessary remedial measures to replace or change the SSL certificates or server configurations.
Analysing SSL servers and certificates for vulnerability
Key Manager Plus scans your SSL environment for the following categories of vulnerability.
- SSL Certificate Revocation Status
- SSL end-server vulnerability
2. SSL Certificate Revocation Status
This check is performed to get information about the revocation status of a selected certificate. If the certificate for any of your domains in use is revoked, you have to take steps to replace it immediately. Revocation status for a certificate is obtained using two methods.
2.1 Certificate Revocation List (CRL)
Error:
The selected certificate is revoked and can no longer be trusted.
Certificate Revocation List (CRL) is a list of SSL certificates that are revoked by the Certificate Authorities (CAs) before their expiration date. Certificates are revoked because of various reasons such as mis-issuances, private key compromise, CA compromise etc., CRLs are a kind of blacklist used by browsers to verify the validity of a certificate. Such tests are essential because, SSL certificates are the means by which browsers and users trust your identity and an invalid SSL certificate brings down their trust for your organization.
Key Manager Plus checks CRL revocation status for your certificates and flags certificates that have been revoked. Click here to know more about CRL.
2.2 Online Certificate Service Protocol (OCSP) Revocation Status
Error:
The selected certificate is revoked and can no longer be trusted.
What's the issue?
Online Certificate Service Protocol (OCSP) is an internet protocol used for obtaining the revocation status of a digital certificate. Web browsers send the certificate in question to the respective Certificate Authority (CA). The CA then returns the response - 'valid', 'revoked' or 'unknown'.
Key Manager Plus checks OCSP revocation status for your certificates and flags certificates that have been revoked. Click here to learn more about OCSP revocation
Workaround:
If any of the above tests render positive for certificate revocation, you have to immediately replace the particular certificate. Failing to do so might cause browsers to throw security errors for your website.
You can replace the revoked certificates with new certificates from trusted third parties directly from Key Manager Plus. Refer to the detailed help section to learn more about certificate request and deployment using Key Manager Plus.
3. SSL End-Server Vulnerability
End-server vulnerability is predominantly caused due to improper configuration of SSL protocol in your domain server. Key Manager Plus tests your domain servers for the following end-server vulnerability.
3.1 Heartbleed Bug
Error:
The selected server is prone to Heartbleed vulnerability.
What's the issue?
Heartbleed bug is a vulnerability in the OpenSSL, a popular open source cryptographic library that helps in the implementation of SSL and TLS protocols. This bug allows attackers to steal private keys attached to SSL certificates, usernames, passwords and other sensitive data without leaving a trace.
Key Manager Plus checks your domain servers for Heartbleed bug vulnerability and flags the affected servers. Click here to learn more about Heartbleed bug.
Patch your OpenSSL software. Replace the vulnerable versions with safe versions of the software.
3.2 POODLE SSL
Error:
The selected server is prone to POODLE attack.
What's the issue?
The POODLE is a form of a man-in-the-middle attack that exploits the vulnerability in the CBC encryption scheme as implemented in the SSL 3.0 protocol. Though POODLE is not as serious as the Heatbleed vulnerability, best practices recommend you discover and mitigate the problem as quickly as possible.
Key Manager Plus scans your servers and flags servers that are vulnerable to POODLE attack. Click here to learn more about POODLE.
Disable SSL 3.0 protocol and enable TLS protocols (1.0, 1.1 and 1.2) on the client-side. It's to be noted that by default, Key Manager Plus disables SSL 3.0 protocol on the Key Manager Plus server.
3.3 SSL 3.0 Enabled
Error:
The selected server exploits the outdated SSL 3.0 protocol, which is prone to known vulnerabilities.
What's the issue?
It has been discovered that SSL 3.0 protocol has a flaw in its design that makes it vulnerable to man-in-the-middle attacks. If you have a public facing website dealing with payments, you should immediately discover all servers that exploit SSL 3.0 and upgrade to TLS version.
Key Manager Plus scans servers in your network and flags all servers that make use of this protocol. Click here to learn more about SSL 3.0 vulnerability.
Disable SSL 3.0 protocol and enable TLS protocols (1.0, 1.1 and 1.2) on the client-side. It's to be noted that by default, Key Manager Plus disables SSL 3.0 protocol on the Key Manager Plus server.
3.4 Weak Cipher Suites
Error:
The selected server exploits weak SSL ciphers,which is a medium risk vulnerability.
What's the issue?
Many organizations knowingly or unknowingly exploit weak SSL protocols and cipher suites in their domain servers which makes their website vulnerable to various MITM attacks. To play safe, they have to identify those weak ciphers, disable them and re-configure the domain servers. By default, SSL 3.0 is disabled on Key Manager Plus server, which is a weak SSL protocol. In addition, Key Manager Plus scans the end-point servers and flags the weak ciphers used in the TLS (1.0,1.1 and 1.2) protocol.
Disable weak cipher suites and re-configure your domain server.
4. Key Takeaways
Here's a quick summary on how Key Manager Plus scans your domain servers for vulnerability.
- Key Manager Plus initially scans the domain servers (to which the selected SSL certificate is deployed) and flags the weak ciphers.
- Your domain server is then scanned for HEARTBLEED and POODLE vulnerability, followed by CRL and OCSP revocation statuses.
- When one or more of the above vulnerability checks renders a positive result, Key Manager Plus flags the particular certificate as vulnerable.
- Also, you can schedule automatic periodic vulnerability checks for your SSL certificates using Key Manager Plus and opt an e-mail notification to the administrators as and when the tests are completed.
- Also, Key Manager Plus provides dedicated, comprehensive, periodic reports on SSL vulnerability.
5. SSL Vulnerability Scan
To perform SSL vulnerability check on your domain server,
- Navigate to SSL >> Certificates.
- Click on Vulnerability icon (
 ) present to the left of the required certificate.
) present to the left of the required certificate. - You will be redirected to a window which displays the certificates and the list of servers in which it is deployed.
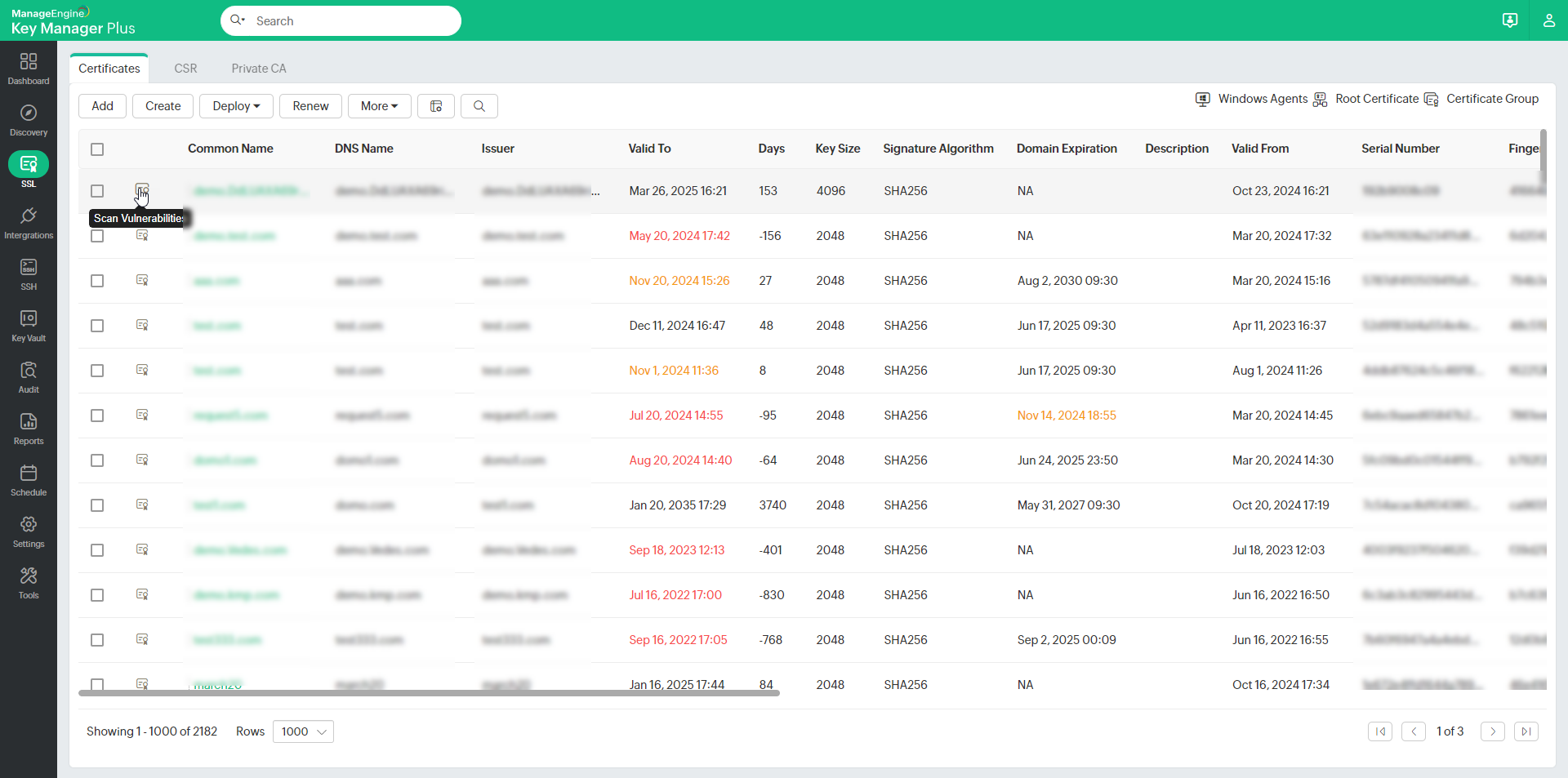
- Click Scan. If you want to perform the vulnerability scan on SANs also, enable Include SAN check box. If you want to perform this scan only for the servers in which the particular certificate is deployed (as discovered by Key Manager Plus), enable Only deployed servers check box.
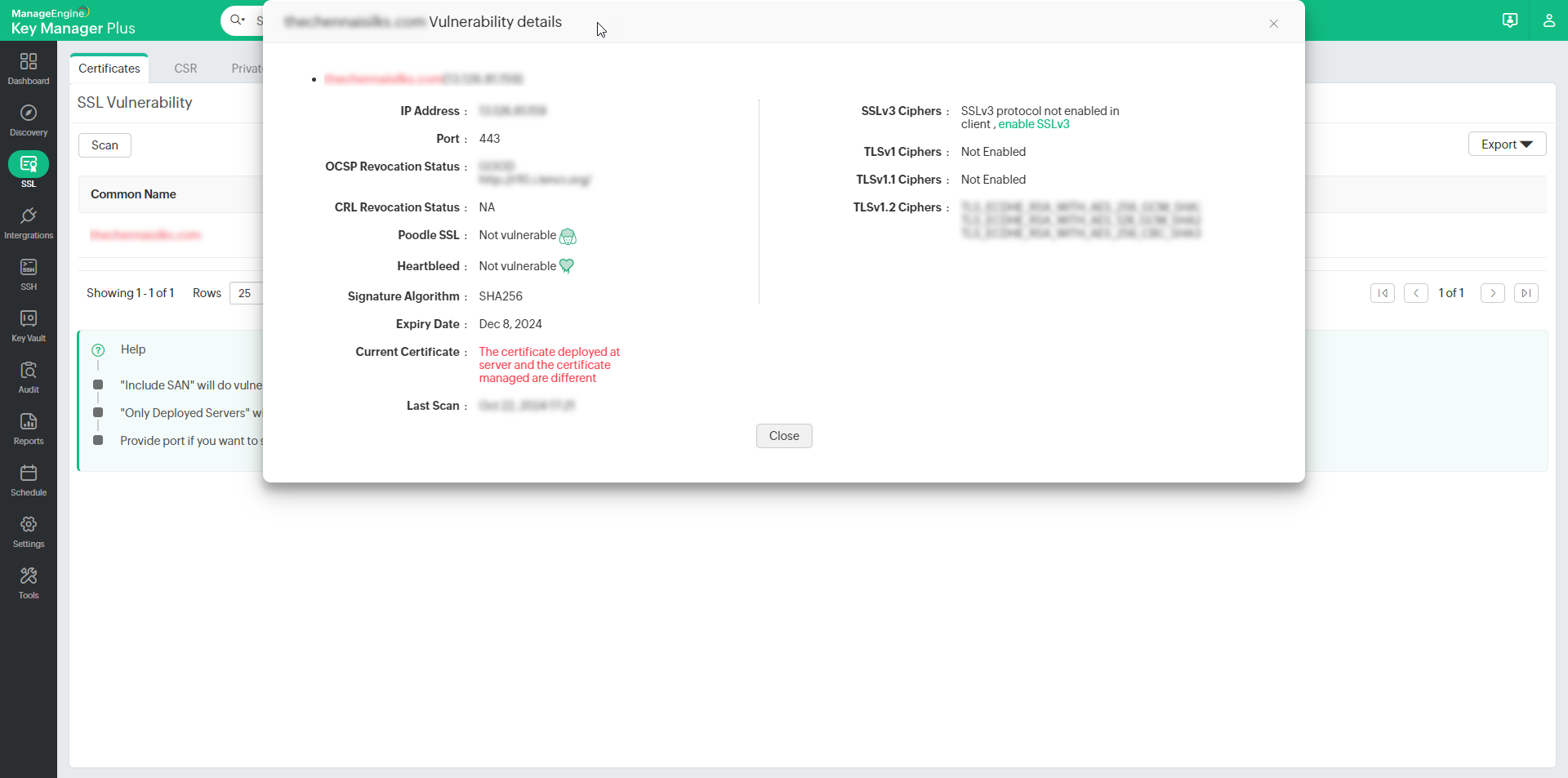
- Key Manager Plus runs the scan and displays the results in a separate window. It comprises of the following details:
- IP address, Port corresponding to the domain server.
- CRL, OCSP revocation statuses.
- POODLE SSL, HEARTBLEED vulnerability status.
- Information on whether the current version of the certificate (version of certificate being scanned) is deployed on domain servers.
- List of insecure ciphers in SSL 3.0 and TLS (1.0, 1.1, 1.2) protocols in the domain server.
- Click Export to export the report in the form of pdf or e-mail to specific mail ids for better interpretation.
Notes:
- By default, SSL 3.0 protocol is disabled in Key Manager Plus server for security purposes. To scan SSL 3.0 protocol on your domain servers, you have to first enable SSL 3.0 protocol on Key Manager Plus server and then restart the server.
- Click here to view the list of ciphers flagged insecure by Key Manager Plus. In any case, should you want to modify the list for compatability purposes, you can do so by the editing the list. Navigate to the conf folder under Key Manager Plus home directory. Open the file named InsecureCiphers.txt and modify the list as required and restart the Key Manager Plus server.
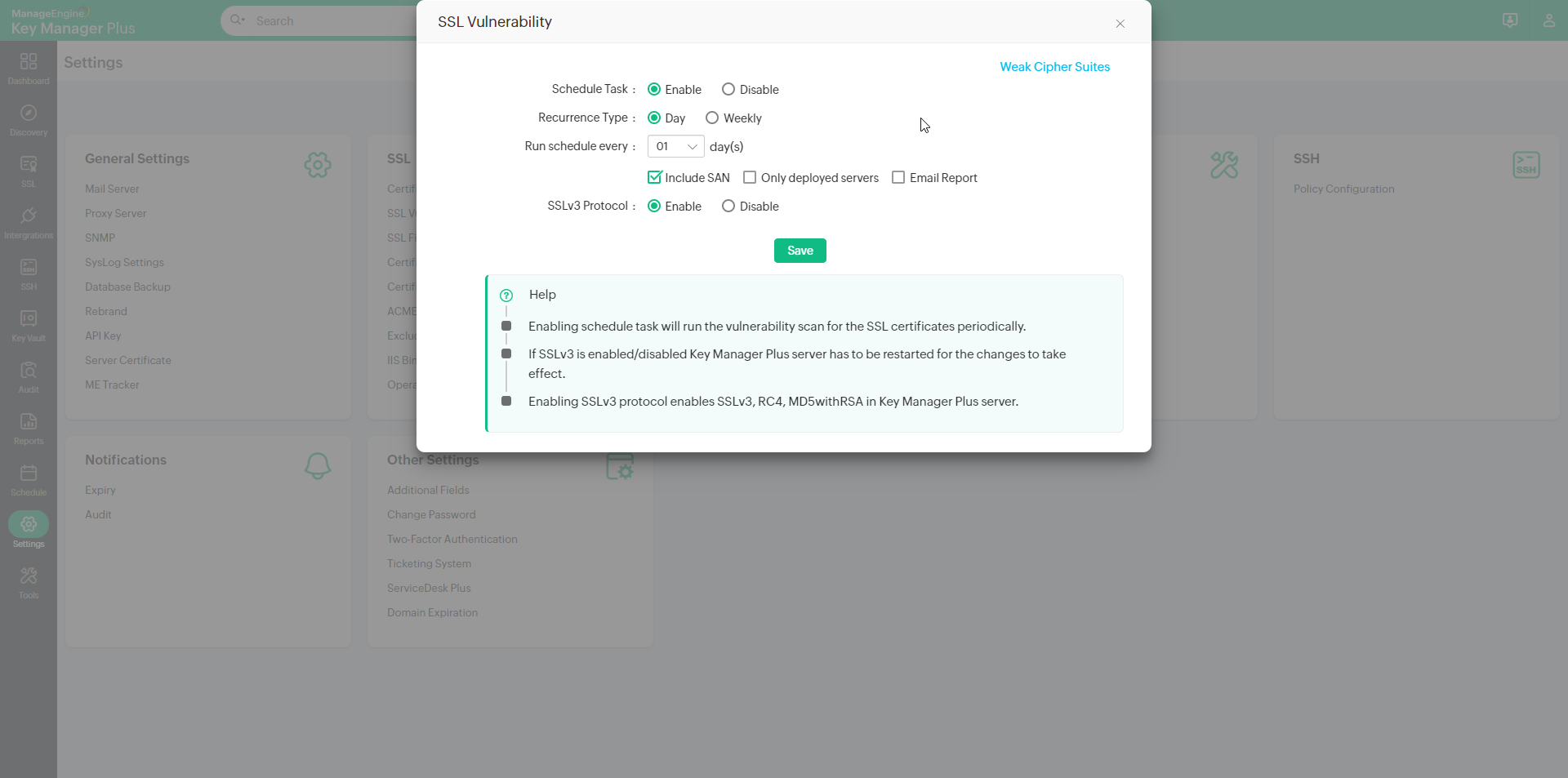
To schedule automatic vulnerability scan,
- Navigate to Settings >> SSL >> SSL Vulnerability.
- Enable scheduled task by selecting the Enable radio button.
- Choose the recurrence type and specify the time interval.
- You can opt to receive e-mail notifications to specific email ids after every scan by enabling the Enable Report check box.
- To enable scanning SSL 3.0 protocol in domain servers, enable the same in Key Manager Plus server by choosing the enable option.
- Click Save. The scheduled task is saved and vulnerability scan is carried out as per the scheduled time interval.
Notes:
- The above technique is used to perform vulnerability scan for all certificates in the Key Manager Plus repository. Should you want to run the scan only for selected certificates, you can do so from the Schedules tab. Refer to the help section on schedules to learn how to schedule vulnerability scan for selected certificates.
- Key Manager Plus generates instant, comprehensive reports on SSL Vulnerability for better interpretation, which can be accessed from Reports tab. To learn more, refer to the detailed help section on reports.
Weak Cipher Suites
TLS_DH_anon_WITH_AES_256_GCM_SHA384
TLS_DH_anon_WITH_AES_128_GCM_SHA256
TLS_DH_anon_WITH_AES_256_CBC_SHA256
TLS_ECDH_anon_WITH_AES_256_CBC_SHA
TLS_DH_anon_WITH_AES_256_CBC_SHA
TLS_DH_anon_WITH_AES_128_CBC_SHA256
TLS_ECDH_anon_WITH_AES_128_CBC_SHA
TLS_DH_anon_WITH_AES_128_CBC_SHA
TLS_ECDH_anon_WITH_3DES_EDE_CBC_SHA
SSL_DH_anon_WITH_3DES_EDE_CBC_SHA
TLS_ECDHE_ECDSA_WITH_RC4_128_SHA
TLS_ECDHE_RSA_WITH_RC4_128_SHA
SSL_RSA_WITH_RC4_128_SHA
TLS_ECDH_ECDSA_WITH_RC4_128_SHA
TLS_ECDH_RSA_WITH_RC4_128_SHA
SSL_RSA_WITH_RC4_128_MD5
TLS_ECDH_anon_WITH_RC4_128_SHA
SSL_DH_anon_WITH_RC4_128_MD5
SSL_RSA_WITH_DES_CBC_SHA
SSL_DHE_RSA_WITH_DES_CBC_SHA
SSL_DHE_DSS_WITH_DES_CBC_SHA
SSL_DH_anon_WITH_DES_CBC_SHA
SSL_RSA_EXPORT_WITH_DES40_CBC_SHA
SSL_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA
SSL_DHE_DSS_EXPORT_WITH_DES40_CBC_SHA
SSL_DH_anon_EXPORT_WITH_DES40_CBC_SHA
SSL_RSA_EXPORT_WITH_RC4_40_MD5
SSL_DH_anon_EXPORT_WITH_RC4_40_MD5
TLS_RSA_WITH_NULL_SHA256
TLS_ECDHE_ECDSA_WITH_NULL_SHA
TLS_ECDHE_RSA_WITH_NULL_SHA
SSL_RSA_WITH_NULL_SHA
TLS_ECDH_ECDSA_WITH_NULL_SHA
TLS_ECDH_RSA_WITH_NULL_SHA
TLS_ECDH_anon_WITH_NULL_SHA
SSL_RSA_WITH_NULL_MD5
TLS_KRB5_WITH_3DES_EDE_CBC_SHA
TLS_KRB5_WITH_3DES_EDE_CBC_MD5
TLS_KRB5_WITH_RC4_128_SHA
TLS_KRB5_WITH_RC4_128_MD5
TLS_KRB5_WITH_DES_CBC_SHA
TLS_KRB5_WITH_DES_CBC_MD5
TLS_KRB5_EXPORT_WITH_DES_CBC_40_SHA
TLS_KRB5_EXPORT_WITH_DES_CBC_40_MD5
TLS_KRB5_EXPORT_WITH_RC4_40_SHA
TLS_KRB5_EXPORT_WITH_RC4_40_MD5
TLS_ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA
TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA
SSL_RSA_WITH_3DES_EDE_CBC_SHA
TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA
TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA
SSL_DHE_RSA_WITH_3DES_EDE_CBC_SHA
SSL_DHE_DSS_WITH_3DES_EDE_CBC_SHA
TLS_DHE_RSA_WITH_AES_256_CBC_SHA256
TLS_DHE_DSS_WITH_AES_256_CBC_SHA256
TLS_DHE_RSA_WITH_AES_256_CBC_SHA
TLS_DHE_DSS_WITH_AES_256_CBC_SHA
TLS_DHE_RSA_WITH_AES_128_CBC_SHA256
TLS_DHE_DSS_WITH_AES_128_CBC_SHA256
TLS_DHE_RSA_WITH_AES_128_CBC_SHA
TLS_DHE_DSS_WITH_AES_128_CBC_SHA
TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
TLS_DHE_DSS_WITH_AES_256_GCM_SHA384
TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
TLS_DHE_DSS_WITH_AES_128_GCM_SHA256