Amazon Virtual Private Cloud (VPC) is a commercial cloud computing service that enables users to create a logically isolated section of the AWS Cloud within which they can launch AWS resources in a virtual network defined by themselves. It essentially allows you to create resources like EC2 instances, databases, and other AWS services inside a private, isolated section of the AWS Cloud.
How will lack of logging and monitoring VPCs lead to cyberthreats?
Here's how the lack of logging and monitoring Virtual Private Cloud (VPC), can lead to various cybersecurity threats and increase the likelihood of successful attacks:
- Undetected threats: Security issues including malware infections, unauthorized access attempts, and unusual network activity could remain undetected if there are no logging and monitoring systems in place. Attackers can carry out malicious actions or take advantage ofvulnerabilities without triggering alerts, which enables them to operate in the environment for extended periods of time without being noticed.
- Lack of alerts: Security teams might not be promptly notified of security incidents or abnormalities occurring inside the environment if there is no real-time monitoring and alerting in place. Attackers will have additional time to carry out their malicious activities as a result of this delay in incident identification and response. This can in turn lead to data breaches, system compromises, or service interruptions.
- Inability to perform log forensics: The absence of comprehensive logging makes it difficult for security teams to carry out efficient forensic investigations and identify the root cause of the incident. It could be challenging to reconstruct the sequence of events leading up to the incident or to pinpoint the tactics, methods, and procedures (TTPs) used by the attackers in the absence of thorough logs of system and network activity.
- Non-compliance: The absence of adequate logging and monitoring measures may result in non-compliance with regulatory requirements, leading to potential fines, legal consequences, or reputational damage.
On the other hand, monitoring user activities, file accesses, and system modifications can help spot unusual activity, suggestive of insider threats, and prevent possible data breaches.
To detect and contain these incidents, the various components of Virtual Private Cloud (VPC) need to be monitored and analyzed using native monitoring tools offered by Amazon Web Services. like NAT Gateway Monitoring and VPC Flow Logs.
1. Monitoring NAT gateways
A Network Address Translation (NAT) gateway is a device that allows the instances in a private subnet to establish a connection with and send traffic to the internet or other AWS services. However, it does not allow the inbound traffic coming from the internet to reach the instance.
When the NAT gateway forwards the data sent by the instance to the internet, it replaces the private subnet IPv4 address with the NAT device address. Once a response is received, the NAT device address is replaced with the IPv4 address before forwarding the response to the instance. NAT gateways do not support IPv6 traffic. The NAT gateway service is completely managed by Amazon and does not require any effort on the part of the administrators.
Amazon CloudWatch—a service that is used to monitor and collect data from Amazon Web Services (AWS) resources as well as applications to provide actionable insights in real time—can be used for monitoring NAT gateways.
CloudWatch first collects data present in the form of logs, events, and metrics from AWS resources, applications, and services hosted on the AWS infrastructure. It also monitors the resources and provides key information related to various metrics such as CPU utilization, latency, and disk storage.
It provides standard reports and displays information on dashboards that can be used to analyze various trends, correlate data, and monitor the performance of resources. If any issues are detected, troubleshooting can be done immediately. Users can also configure alarms to trigger actions by setting thresholds for chosen metrics and enabling notifications that will be sent to the user if there are any changes.
The metric data from NAT gateways is provided to CloudWatch at one-minute intervals. CloudWatch collects data such as active connections, bytes transmitted, and number of packets and uses it to monitor the gateways. If any issues arise, you can troubleshoot them instantly. CloudWatch metric data is recorded and retained for a period of 15 months at no extra charge, after which the data points expire and are dropped on a rolling basis as new data points come in.
VPC enables appropriate and necessary things required for a proper cloud monitoring. These changes are to be monitoired to make sure that all of these changes does not affect the environment on the whole. The basic requirements of these are to be monitoied continuosult.
2. Network monitoring using Amazon VPC flow logs
A flow log collects information about the network traffic that is entering or leaving the network interfaces in a VPC. It can be created for a VPC subnet, a VPC, or a network interface. When a flow log is created for a subnet or a VPC, all the network interfaces in the subnet or the VPC will be monitored.
These VPC flow logs help security teams monitor the flow of traffic in the entire virtual network, detect anomalies, take action if there are any suspicious activities taking place, and identify excessively restrictive rules in security groups.
The different information types collected by flow logs include source and destination IP addresses, port numbers and protocols used, packets and bytes transferred, network traffic allowed and denied by security groups, network access control lists, and more. They are recorded as flow log records. Each flow log record consists of values of the various components of the IP traffic flow occurring within an aggregation interval (capture window).
The default format for the flow log record consists of the following fields in the same order:
<version> <account-id> <interface-id> <srcaddr> <dstaddr> <srcport> <dstport> <protocol> <packets> <bytes> <start> <end> <action> <log-status>
The default format only records information for a subset of all the available fields of a flow log record. If you want to record information for all the available fields or for a different subset of the fields, you can choose a custom format. Custom formats will help you create flow logs as per your requirements.
Here's an example of a flow log record. In this instance, SSH traffic was allowed to enter the network interface eni-1235b8ca134556889 in the account 12456788010.
2 12456788010 eni-135b8ca1234556889 172.31.16.139 172.31.16.21 20641 22 6 20 4229 1417630010 1418530070 ACCEPT OK
Utilizing ManageEngine Log360 to monitor your Amazon VPC
ManageEngine Log360 allows you to collect and analyze log data from a variety of sources within your VPC environment, such as VPC Flow Logs, CloudTrail logs, and system logs from your EC2 instances, to offer a comprehensive picture of your VPC activities.
- The Log360 VPC activity reports can automatically scan VPC flow logs to detect the changes made to the VPCs, network gateways, VPC endpoints, VPC route tables, subnets, and VPC routes. You can also set up custom alerts to receive notifications about any unwanted changes to VPCs and know who made the change, when, and from where(Refer to Figure 1)
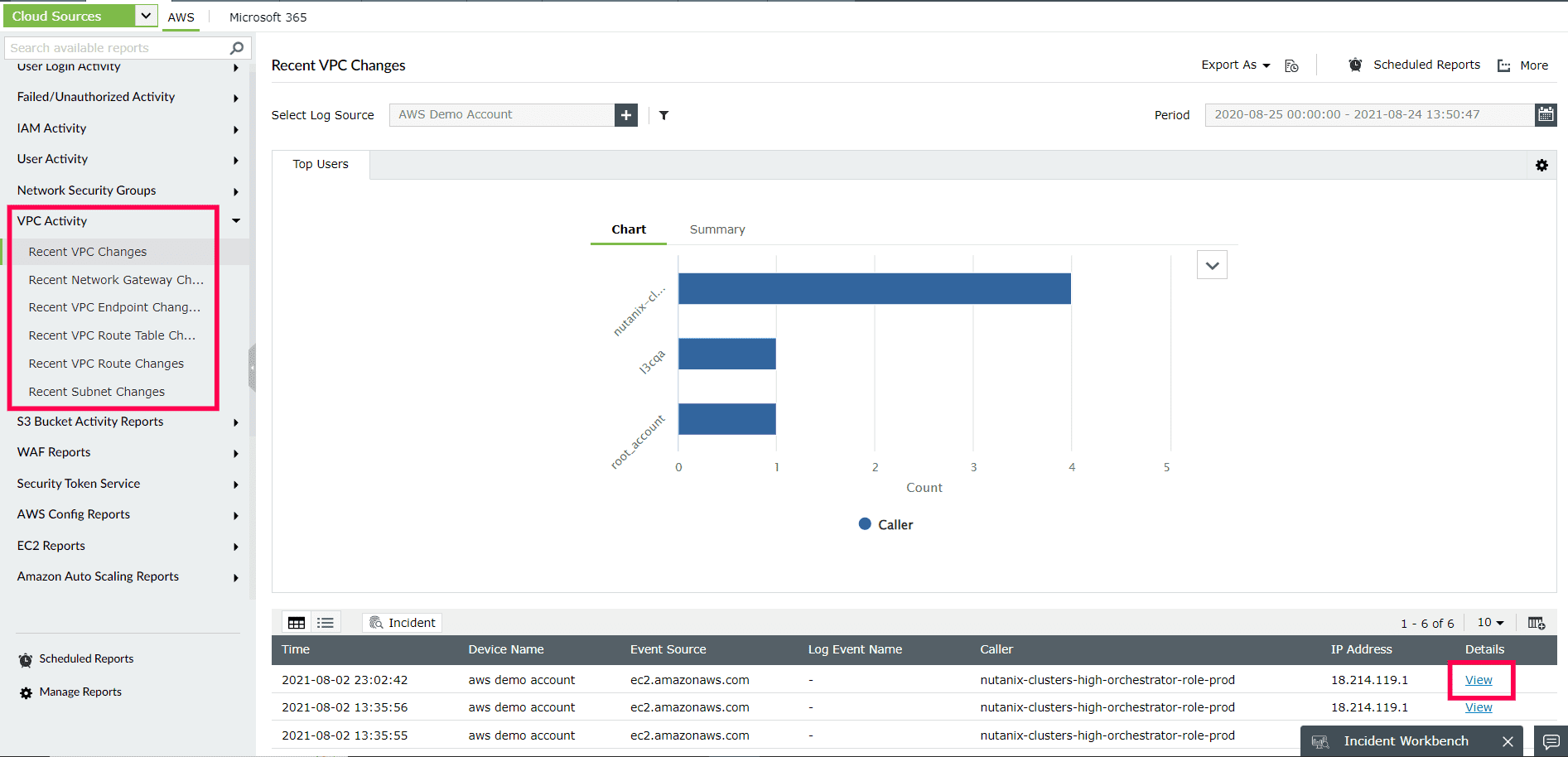
Figure 1: ManageEngine Log360's VPC activity report
- Gain visibility into the recent configuration changes that has been made, such as adding IP addresses to security groups or utilizing security group rules to approve inbound traffic. The reports generated by Log360 offer insights into security group creation and deletion, configuration modifications, authorized and revoked security group ingress and egress, network gateway modifications, and network access control list (ACL) modifications(Refer to Figure 2). You can identify possible security issues and the malicious activities directed towards your cloud instances with the help of this comprehensive information.
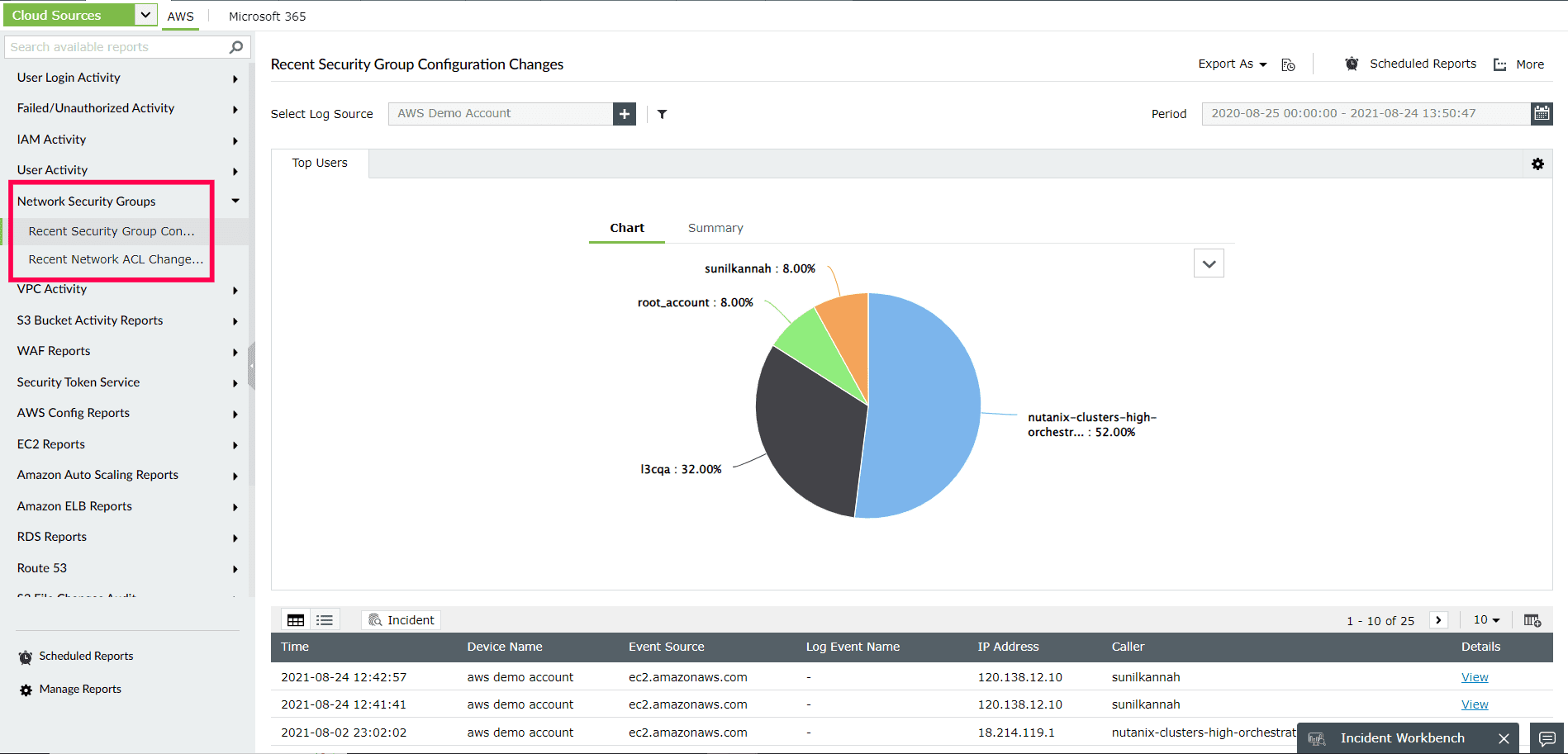
Figure 2: ManageEngine Log360's Network Security Groups report
- Log360 obtains and analyzes your S3 server access logs and AWS CloudTrail logs to provide insightful reports about your AWS environment(Refer to Figure 3). The tedious configuration procedure required to obtain the CloudTrail logs is made simpler by an auto-configuration feature. Also, providing flexible log storage and an effective search mechanism simplifies manual forensic analysis.
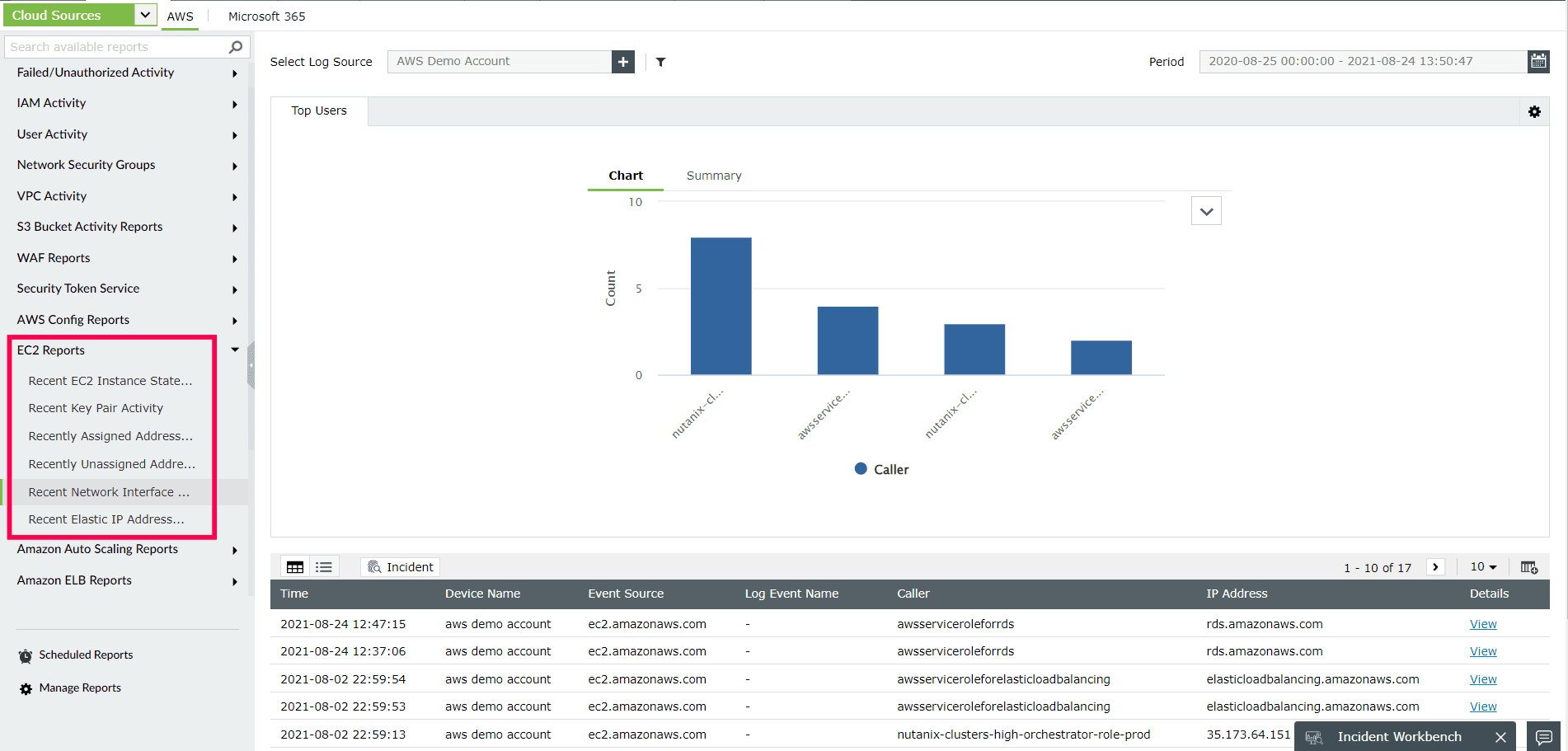
Figure 3: ManageEngine Log360's EC2 Reports
- Monitor the S3 bucket changes in your AWS VPC environment by running reports on crucial actions like bucket creation and deletion(Refer to Figure 4). These offer crucial details such as who did the action, the originating IP address, the time of the event, and any errors that occurred. Log360 collects all of the S3 service failure events and gives information on the issue that led to the activity failing, including the error number and message. Both the bucket and the object levels record deletion events like DELETE Bucket lifecycle, DELETE Bucket policy, and DeleteMultipleObjects.
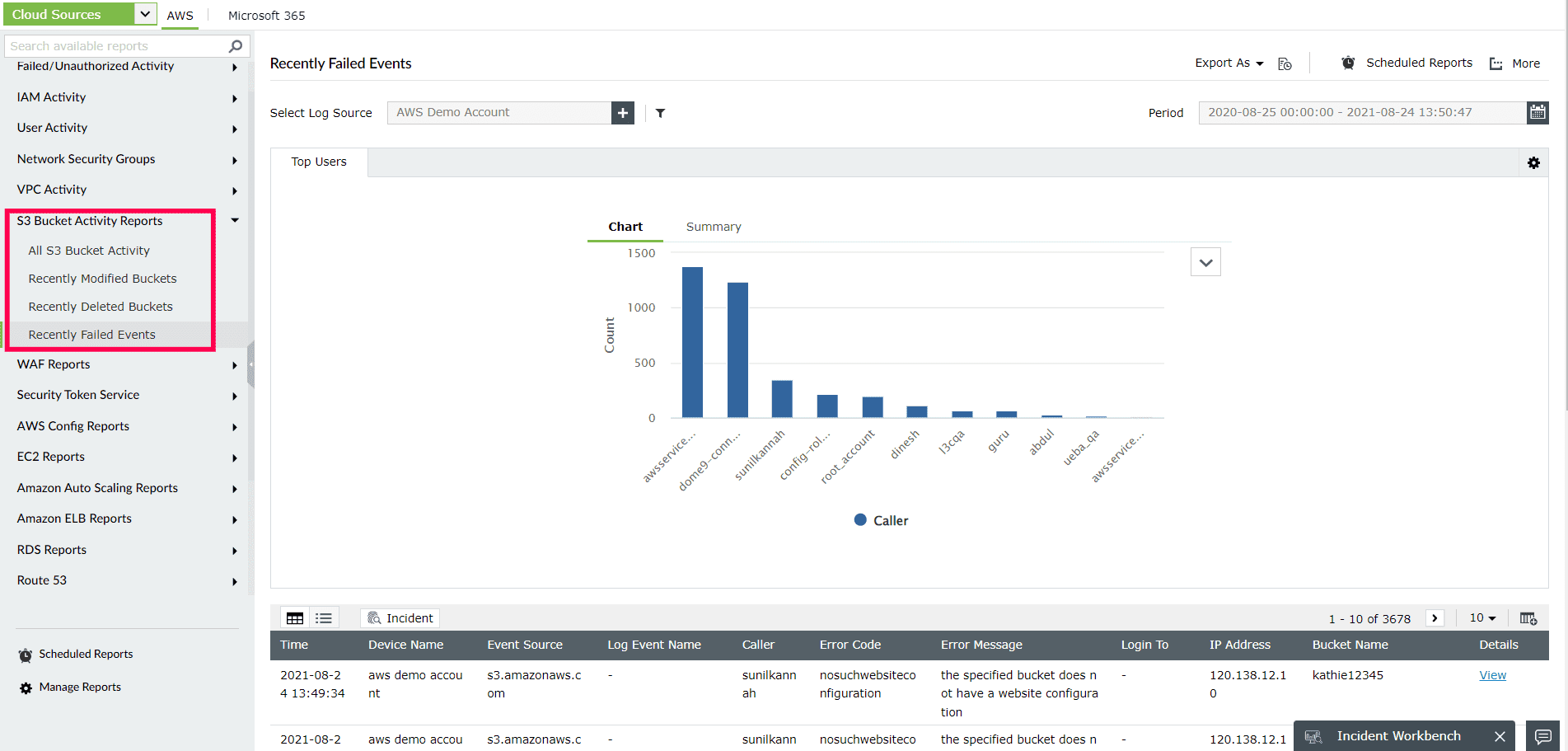
Figure 4: ManageEngine Log360's S3 Bucket Activity Reports
- To ensure the security of sensitive enterprise dat hosted in the cloud, identify possible security issues, and meet regulatory requirements, keep a close eye on modifications made to AWS EC2 instances(Refer to Figure 5). Log360 helps you keep track of EC2 state changes such as instance starting, rebooting, and halting, and provides information on who executed the event, when and where it occured.
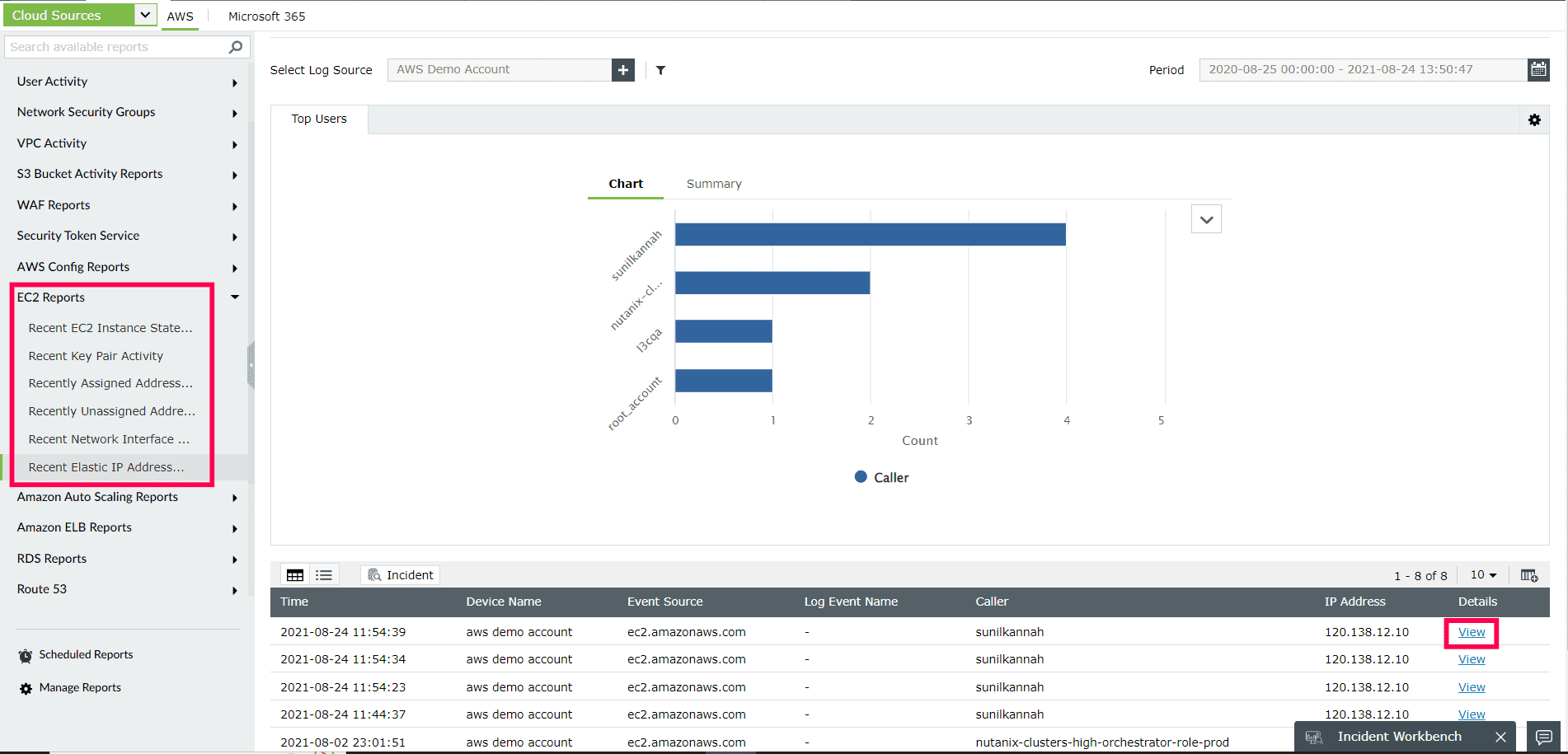
Figure 5: ManageEngine Log360's EC2 Reports
- The interactive dashboard of ManageEngine Log360 provides visual data with insights on various actions performed on the cloud environment. All modifications have real-time answers to the "what, when, where, and how" of changes(Refer to Figure 6).
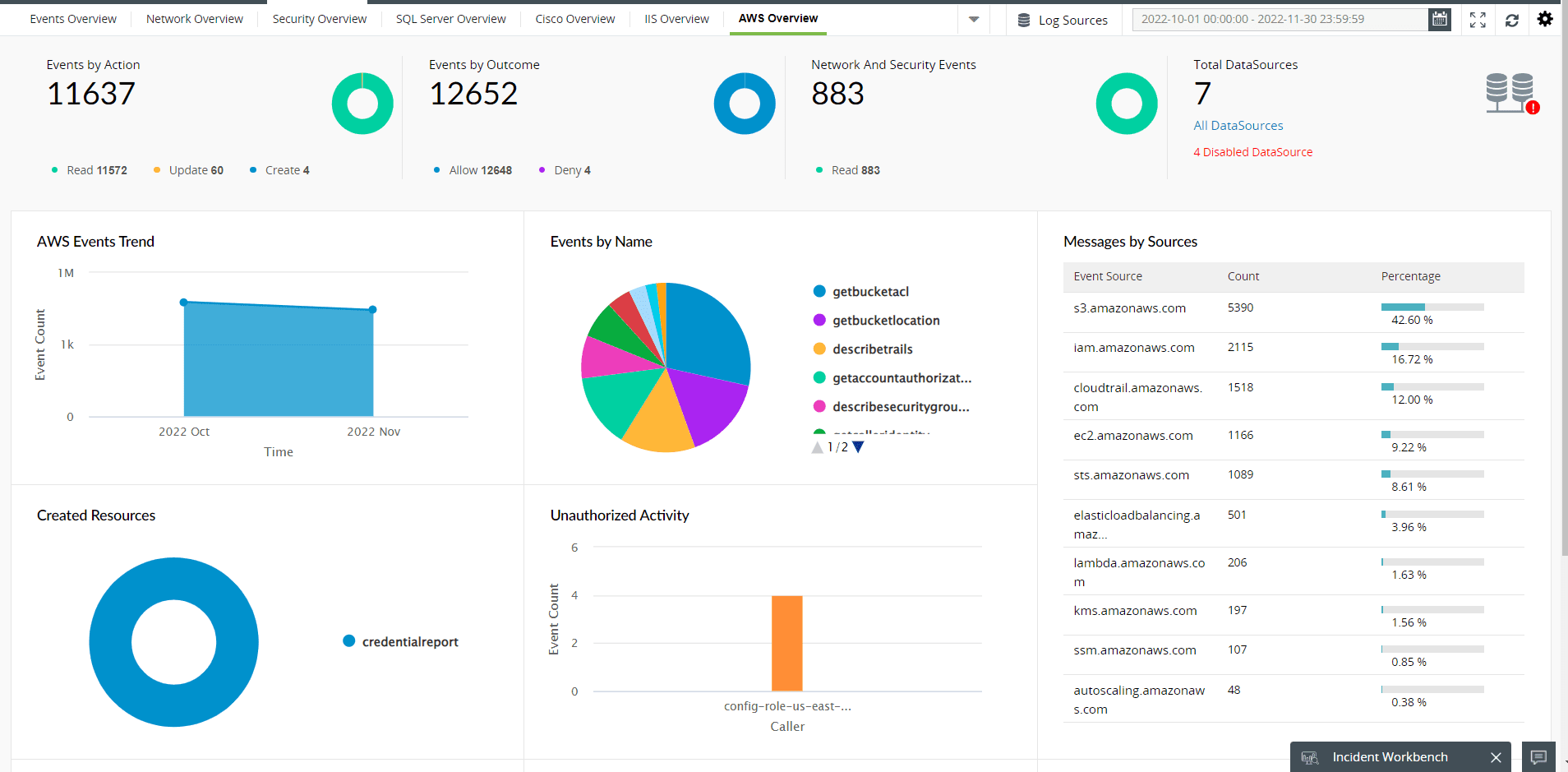
Figure 6: AWS Overview dashboard in Log360
To learn more about Amazon VPC check out this page:
Ready for the next step?
Explore how you can protect your organization's sensitive information from being misused. Sign up for a personalized demo of ManageEngine Log360, a comprehensive SIEM solution that can help you detect, prioritize, investigate, and respond to security threats.
You can also explore on your own with a free, fully functional, 30-day trial of Log360.



