Amazon Virtual Private Cloud (Amazon VPC) provides an isolated cloud environment within the AWS public cloud framework. It enables enterprises to secure their resources and data even though they are hosted on a public cloud platform. Amazon VPC controls access to the hosted resources with a set of rules called network access control lists (ACLs).
A network ACL is a layer of security for your VPC that acts as a firewall for controlling traffic in and out of one or more subnets. The ACLs are configured with rules, and the VPC checks incoming or outgoing packets based on these rules.
There are a few things you should know about network ACL rules:
- AWS allows you to configure custom ACLs and assign them to one or more subnets.
- Before you associate an ACL with any subnet in your VPC, AWS provides a default ACL that allows all inbound and outbound traffic.
- Once you create a network ACL, you have to explicitly associate the ACL with a subnet. If this is not done, the subnet is associated with the default ACL.
- A custom ACL denies all inbound and outbound traffic (rule *) unless it is configured with rules.
- Once you have created the rules for a custom ACL and associated the ACL with particular subnets, any inbound or outbound traffic is evaluated based on the rules mentioned in the ACL.
- When the ACL encounters a packet, the following steps occur.
- The rules are evaluated in ascending order starting from the lowest numbered rule.
- Once a rule matches the traffic, it is applied and the remaining higher numbered rules are ignored.
- The highest number for a rule is set to 32,766. AWS recommends incrementing rule numbers with intervals (such as 10 or 100) so you can add new rules later as and when required.
- If no rule matches the traffic, the last rule in the list (*) is applied, which denies all traffic.
- Network ACLs are stateless. This means that an ACL does not keep track of connection information. It does not take into account whether the traffic is a new request or a reply to a previous request. The ACL only examines the source, destination IP and port numbers to allow traffic based on the rules defined.
The tables below show the final Allow/Deny action performed by the ACL for inbound rules and outbound rules.
Inbound rules
| Rule number | Type | Protocol | Port range | Source | Allow/Deny |
|---|---|---|---|---|---|
| 100 | HTTP | TCP | 80 | 0.0.0.0/0 | ALLOW |
| 200 | HTTPS | TCP | 443 | 0.0.0.0/0 | ALLOW |
| 300 | SSH | TCP | 22 | 0.0.0.0/0 | ALLOW |
| * | All traffic | All | All | 0.0.0.0/0 | DENY |
Outbound rules
| Rule number | Type | Protocol | Port range | Source | Allow/Deny |
|---|---|---|---|---|---|
| 100 | HTTP | TCP | 80 | 0.0.0.0/0 | ALLOW |
| 200 | HTTPS | TCP | 443 | 0.0.0.0/0 | ALLOW |
| * | All traffic | All | All | 0.0.0.0/0 | DENY |
- Rule number: Defines the order in which the rules are evaluated. In the table above, whenever traffic is encountered—either incoming or outgoing—first rule number 100 is checked. If that rule is not satisfied, rule 200 is checked and so on. If rule number 200 is satisfied, the rules higher than 200 (i.e., 300 and *) are ignored.
- Type: Defines the type of traffic, such as HTTP, HTTPS, and RDP.
- Protocol: Specifies the protocol. You can define any protocol with a standard protocol number.
- Port range: Defines the port range to which the rule applies.
- Source: Defines the source IP address of the packet. This is present in inbound rules only.
- Destination: Defines the destination IP address of the packet. This is present in outbound rules only.
- Allow/Deny: Specifies the final action to be performed by the ACL—either to allow or deny the traffic.
These are the things you should keep in mind while configuring your VPC with a custom network ACL. A properly configured VPC helps your enterprise utilize AWS's cloud computing features to their full potential and scale greater heights in terms of productivity and performance.
With Log360, you can gain visibility into configuration modifications, such as adding IP addresses to security groups or authorizing inbound traffic through security group rules. This comprehensive tool will also detect activities, like suspicious logons, failed logons and also failed events and provide real-time alerts and extensive reports that can help amplify your organization's security posture.
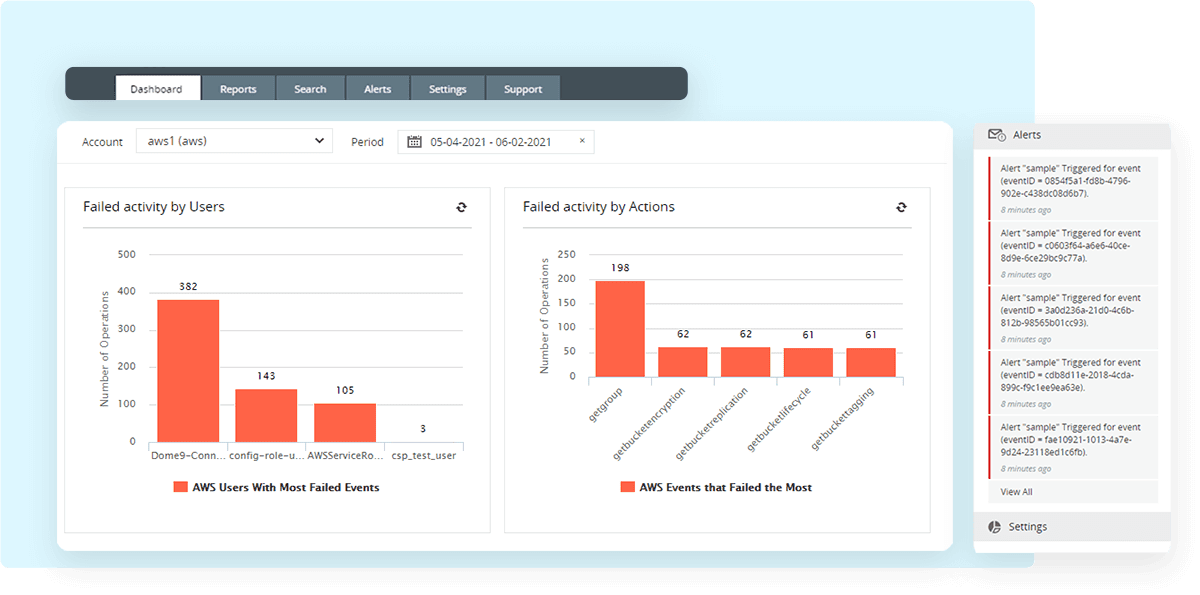
AWS failed activity reports from Log360
You can also learn more on your own through a free, fully functional 30-day trial, or a free personalized demo that can be scheduled according to your convenience.



