Educational institutions are huge data mines that contain personally identifiable information, such as the social security numbers, health records, scholarship data, or payment data of numerous students, parents, and faculty members. They are also repositories for a wide range of confidential research data.
According to a Research and Markets report, the market value of cloud computing in higher education is expected to grow to USD 8.7791 billion by 2027. As a result, cloud data security and privacy are persistent challenges in this industry. Any compromise can lead to severe consequences, including identity theft, financial losses, and the compromise of sensitive academic research. By following laws such as the Family Educational Rights and Privacy Act (FERPA) and implementing comprehensive privacy policies, institutions can secure data and gain the trust of their stakeholders.
Organizations belonging to the education sector use different cloud technologies, such as Microsoft Azure, Amazon Web Services (AWS), and Google Cloud, for various reasons; the data transfers that occur using these platforms must be monitored continuously, and the changes must be logged. Apart from hardening security, monitoring also helps organizations meet compliance mandates.
Cloud use in educational institutions
The education sector uses the cloud for a variety of purposes, including:
- Data storage: Storing data in the cloud is safer and more cost-effective.
- Collaboration: Students can collaborate with one another, access resources such as videos, and submit assignments efficiently. Faculty can also collaborate to work on research projects and interact with students.
- Virtual classes: With the adoption of the cloud, students can learn from remote locations worldwide.
- Data analysis: Platforms such as Google Cloud Smart Analytics have accelerated the process of data analysis for researchers.
- Content management systems or learning management systems: There are entire suites of cloud tools for learning, enhancing the experience for both teachers and students.
Multiple cloud platforms are used by educational institutions to accomplish the purposes listed above. However, Azure, AWS, and Google Cloud are the top three cloud providers. They all have a sizable consumer base and they each have a unique offering designed particularly for the education sector.
Securing Azure
Securing Azure is paramount for managing resources, facilitating collaboration, improving learning, and storing data. Key services such as Azure Education Hub, Microsoft Entra, Azure Virtual Machines, Azure Blob Storage, Azure SQL Database, and Azure Virtual Network are widely used among educators and researchers. These services have a common critical element: data security.
Microsoft Entra ID, previously known as Azure Active Directory, is Azure's cloud-based identity and access management (IAM) solution. This service is essential for educational institutions as it manages comprehensive user information, including that of students, staff members, and researchers. Ensuring the security of Entra ID is crucial as it safeguards sensitive identity data against unauthorized access and potential breaches. Azure Virtual Machines also plays a significant role in security. For companies that heavily invest in research, securing the data on these virtual machines is vital to protecting intellectual property and research outcomes.
Other services like Azure Blob Storage, Azure SQL Database, and Azure Virtual Network must also be secured to ensure the integrity, confidentiality, and availability of stored data. Implementing robust security measures across these services, such as encryption, access controls, continuous monitoring, and incident response plans, helps you maintain a secure Azure environment.
Securing Azure is not just about protecting individual services but also ensuring the overall security posture of the cloud environment, making it a safe, reliable platform for education and research.
Securing AWS
Amazon provides educational institutions with a wide range of programs tailored to different types of organizations, whether they are involved in basic education, secondary education, higher education, or EdTech. Popular services such as Amazon Connect, Amazon Simple Storage Service (S3), Amazon WorkSpaces, Virtual Proctoring, and Amazon AppStream 2.0 are widely used to enhance educational experiences and operations.
Ensuring the security of these services is critical to protecting sensitive data and maintaining the integrity of educational processes. For example, Amazon S3 is a widely used storage service that must be secured to protect the vast amounts of data that educational institutions handle, including student records, research data, and administrative information. Ensuring data security involves implementing robust encryption, managing access permissions, and continuously monitoring for any suspicious activities.
Securing Google Cloud
Google is an established name in the education sector, providing a suite of products that enhance teaching and learning processes for educators and learners alike. Popular tools such as Chromebooks, Google Sheets, Google Meet, Google Slides, Google Docs, and Google Forms are widely used in educational environments.
Ensuring the security of these tools is essential to protecting sensitive data and maintaining the integrity of educational activities. For example, Google Meet, used extensively for virtual classrooms and meetings, must be secured to protect against unauthorized access and eavesdropping. Utilizing features such as secure meeting codes, participant management controls, and the encryption of data in transit ensures a secure virtual meeting environment.
This increased dependence on the cloud is only going to grow in the years to come because of its scalability, cost-effectiveness, and efficiency. But just as the dependence on the cloud has skyrocketed, so has the value of the data that resides in the cloud. So, securing the cloud is a priority.
The need for cloud security in the education sector
A cyberattack can have massive aftereffects on an educational institution, including:
- Lost trust: Every educational institution has an implicit pact with students or their parents to safeguard their information. It is this pact that gives them the confidence to disclose their personal information. Thus, if a data breach occurs, there is a breach of trust, too.
- Financial losses: Organizations have to pay heavy noncompliance penalties, compensatory fines, and legal fees in the event of a data breach.
- Reputational damage: This is a byproduct of a loss of trust among stakeholders. Trust is synonymous with loyalty, so a loss of trust means a loss of brand loyalty.
Cloud security, also called cloud computing security, involves a set of security practices that help your cloud infrastructure remain safe from cyberattacks. These practices include continuously monitoring cloud environments, securing access control policies, and formulating effective incident response plans.
Real cases of breaches
Here are a few real-life examples of breaches from the education industry:
- In 2022, the records of one million students from New York were compromised due to a significant data breach at one of the New York City Department of Education's vendors.
- A threat actor named Kimsuky used backdoor techniques and command executions to steal information from research institutes in South Korea in 2023.
- In 2023, almost 250,000 user records from Indiana University were exposed due to a third-party vendor's misconfiguration.
- In 2023, an attacker gained unauthorized access to the database of the University of Minnesota and posted the personal information of students, faculty, and others online.
Cybersecurity tools, like SIEM or IAM solutions, can help universities and colleges detect threats at an early stage. Let us consider a couple scenarios.
Attack scenarios at educational institutions
Scenario 1: An attack on Azure Virtual Machines at a research facility
- Without a cybersecurity solution: This research facility has multiple VMs set up on Azure, where they store sensitive research data, student records, and other sensitive information. An attacker gains unauthorized access to the facility's Azure environment through a phishing email. Exploiting vulnerabilities within the system, they get access to admin credentials, which they use to manage the different resources, including Azure VMs. They deploy many more malicious VMs that initiate different types of attacks, such as SQL injection or cross-site scripting attacks, targeting students and faculty. Once they compromise the whole system, they transfer all the sensitive data to an external server that is under their control.
- With a cybersecurity solution: This research facility has multiple VMs set up on Azure, where they store sensitive research data, student records, and other sensitive information. An attacker gains unauthorized access to the facility's Azure environment through a phishing email. The moment the phishing email is received, the cybersecurity tool notifies the admins that a malicious source is trying to infiltrate the system. If the solution is more advanced, the admins can leverage different threat feeds to detect malicious IP interactions. If the attacker poses as a student and uses a known IP, the tool's anomaly detection module can spot the anomalous user activity, sending alerts to the admins due to the behavior deviation. This way, the attack can be stopped right there.
Scenario 2: A brute-force attack on Google Workspace at a school
- Without a cybersecurity solution: Let us consider an example where an attacker gets access to an educator's account through brute force. By using the account, the attacker compromises the systems of other teachers and students through social engineering attacks. In this manner, they can enter Google Workspace and take control of confidential information, numerous passwords, and other environment-related data.
- With a cybersecurity solution: When a brute-force attack is launched, a series of events occurs: malicious software installations, anomalous login activity, the clearing of event logs, and successive login failures. A cybersecurity tool looks out for such security events, alerts the admin team, and automatically executes response workflows.
Cloud security compliance in the education sector
Compliance is essential, regardless of the type of institution. Cloud compliance refers to the process of adhering to the laws, standards, guidelines, and regulations set by your industry, nation, federal government, or other jurisdictional bodies.
Being compliant not only helps your institution save money but also increases stakeholder trust in your institution by:
- Improving risk management: Compliance standards such as the General Data Protection Regulation (GDPR) and Health Insurance Portability and Accountability Act (HIPAA) require your organization to be proactive and help you identify and mitigate threats related to data breaches.
- Strengthening contracts: For example, a contract with an educational institution is more trustworthy when that institution is FERPA-compliant.
- Maintaining distinct standards: Adhering to ISO/IEC 27001 for security shows your educational institution's commitment to data protection.
- Ensuring easy audits: Being compliant means you already have all the documents and evidence to demonstrate adherence to the law, making audits easier.
Some of the most common compliance mandates in the education sector are FERPA, HIPAA (if you hold the health records of students), the Payment Card Industry Data Security Standard (PCI DSS) (if you save the card information of parents or students), the GDPR (for all institutes under the European Union), and ISO/IEC 27001.
Cloud security best practices for the education sector
Here are seven things you can do to ensure that your cloud infrastructure remains secure:
- Educate staff and students about phishing and other cyberattacks.
- Establish stringent cloud security policies and have proper incident response plans.
- Use penetration testing to continuously scan your system for vulnerabilities in order to detect and reduce security concerns.
- Understand what you are responsible for in your cloud environment. Have a proper understanding of the risks associated with using cloud service providers and other vendors. Have a transparent conversation about the best practices to follow, the code review process, and strategies to mitigate and prevent vulnerabilities during software development.
- Consider using trusted security tools, such as IAM, SIEM, or CASB-integrated SIEM solutions, to monitor your cloud environment.
- Mandate multi-factor authentication for all the users in your system or follow a Zero Trust model to minimize potential threats.
- Protect data with encryption.
Cloud security solutions for the education sector
A single solution may not solve all the problems of your various services. But you can optimize a solution to solve most of your problems.
Regardless of the security solution you choose, a few features remain constant: log monitoring, security analytics, threat detection, automated incident response, alerting, and compliance management.
Log360 is the one-stop destination for all your security needs. This unified SIEM solution with integrated DLP and CASB capabilities is designed to process, audit, and monitor Azure, AWS, and Google Cloud logs and ensure security. The solution also provides compliance reports with predefined templates for a wide range of policies, including FERPA, HIPAA, the PCI DSS, and FISMA. Here is an example of a FERPA report offered by Log360:
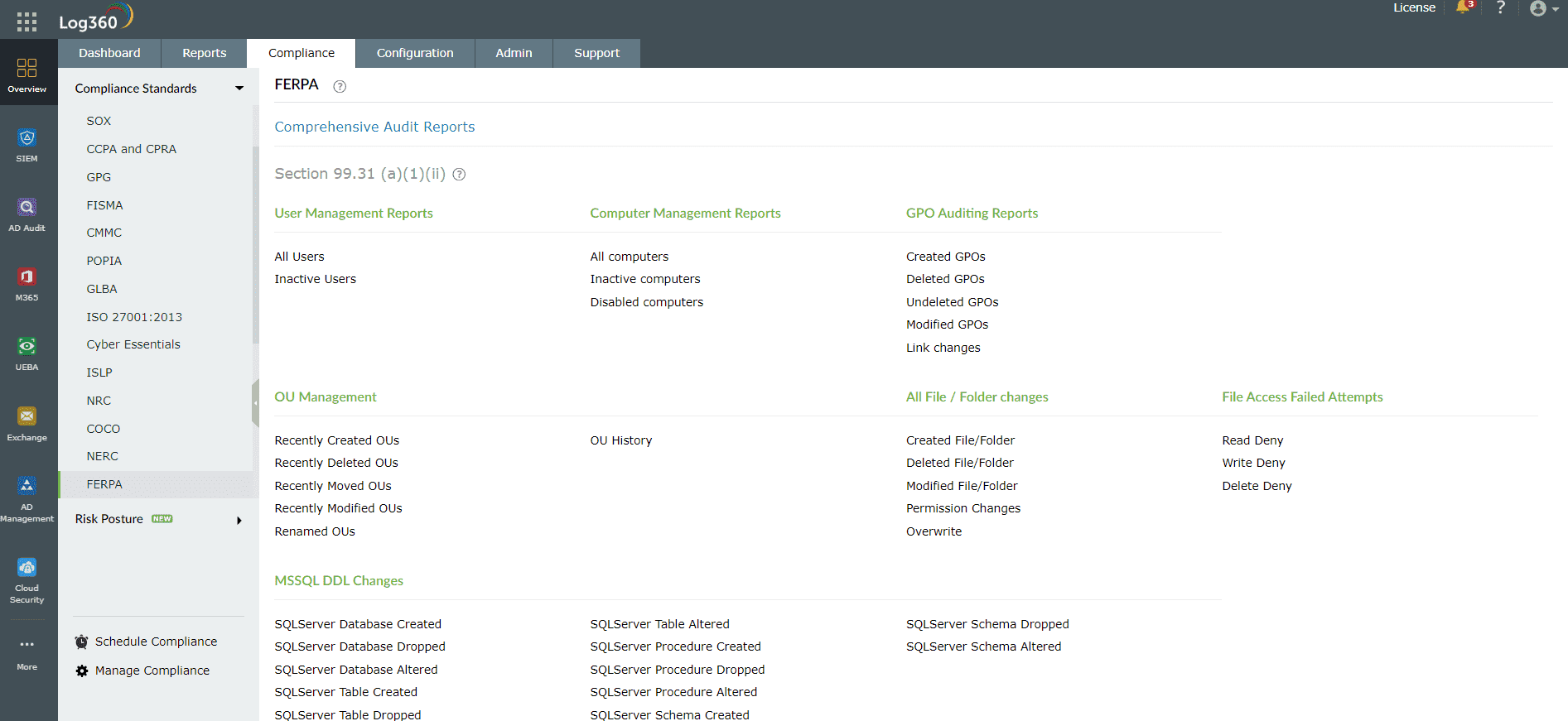
Figure 1: A screenshot from Log360 that shows all the clauses that come under Log360's FERPA compliance reports
There is no doubt that the cloud is here to stay. By prioritizing cloud security, educational institutions can ensure that they create a safe, secure digital environment for students, staff, and other stakeholders.



