With the ever-evolving threat landscape, cyberattacks have become more sophisticated; malicious actors are carrying out more advanced cyberattacks with serious consequences on users and organizations. An SQL injection attack is a popular web hacking technique that targets data-driven web applications.
Let's discuss what an SQL injection attack is, how the attack works, its impact, and preventive measures against the attack.
SQL injection is a common and prevalent method of attack that targets victims' databases through web applications. It enables cyberattackers to access, modify, or delete data, and thus manipulate the organization's databases. For any organization, data is one of the most critical and valuable assets, and an attack on its database can wreak havoc on and compromise the entire business.
The data here can include customer records, privileged or personal information, business-critical data, confidential data, or financial records of an organization.
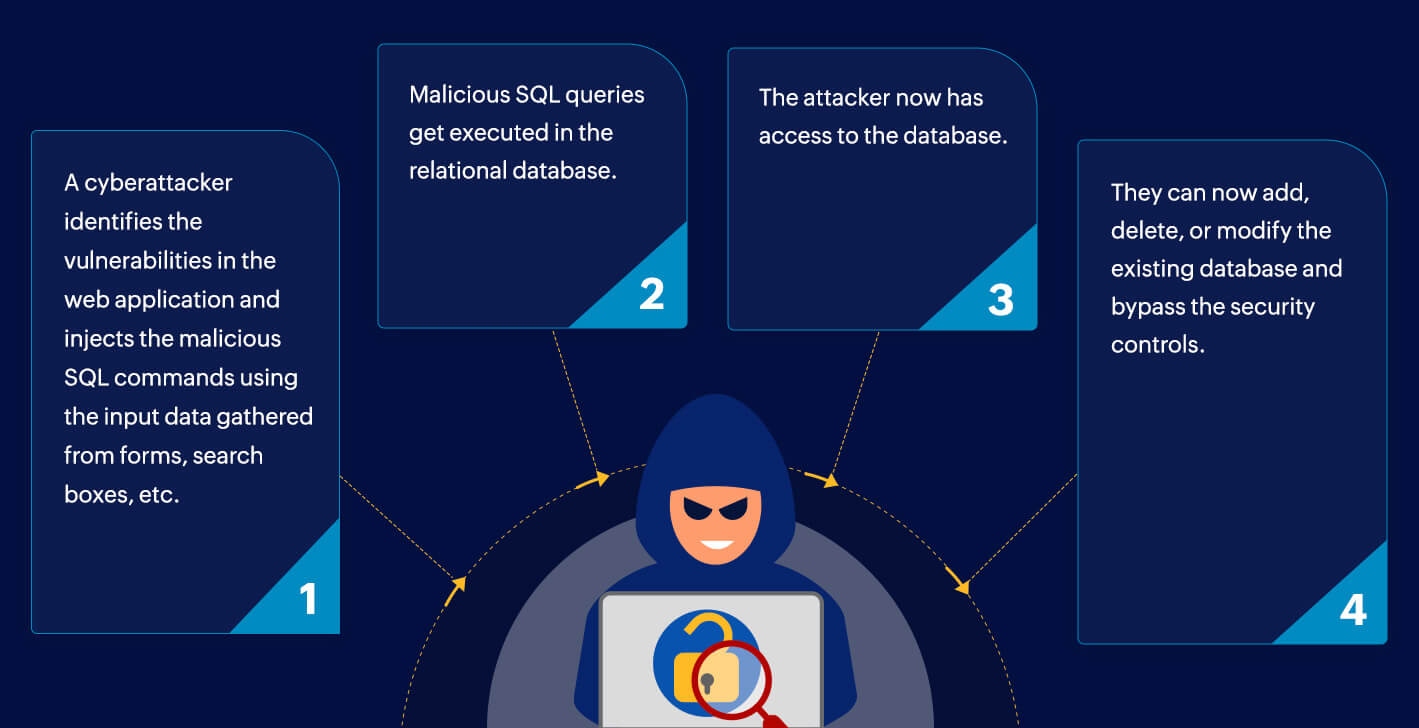
An SQL injection attack is carried out through the following steps:
An attacker researches the database that has to be targeted.
The attacker then identifies vulnerabilities in the webpage or application that can be exploited to carry out the attack. One example of an SQL vulnerability is insufficient user input validation; the attacker can create and submit their own input content by exploiting this vulnerability.
They further create malicious SQL inputs and inject them into the standard SQL queries.
This enables the attackers to carry out unintended and malicious actions on the web application and exploit the database. The attackers can now extract confidential information, bypass security controls, modify records, or delete the entire database.
Following an SQL injection attack, an attacker can:
To secure your organization against SQL injection attacks:
SQL injection is one of the most popular attack vectors used by malicious actors; however, by maintaining a good database hygiene and taking required precautions, you can minimize the risk of becoming a victim to this kind of attack.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.