Enterprise networks are large and complex, dealing with huge volumes of business-critical data. These sensitive files are in continuous transit across the enterprise network and are stored, shared, and accessed by several users and entities. FIM tools or SIEM solutions with FIM capabilities enable enterprises to track unauthorized file changes, malicious access to sensitive information, data tampering attempts and insider threats.
How FIM helps improve data security in enterprises
Following are the major ways in which FIM helps ensure data integrity and security in enterprises.
- Monitoring unauthorized file changes in Windows and Linux systems
FIM detects suspicious modifications to critical files in Windows and Linux systems. System files, configuration files, directory files, and registry files, which regulate the operation of these systems, are particularly vulnerable to data tampering attempts. By recording and reporting changes to such critical files, FIM ensures data security for the entire Windows and Linux systems.
- Auditing file access permission changes
Malicious insiders may attempt to change file permissions by manipulating the file access list. They may modify user access controls to read, write, or copy sensitive information, compromising the security and integrity of data. By monitoring changes in file permissions and user attempts to access, modify, or delete confidential files or folders, FIM helps you detect unauthorized changes to file permissions and prevent data manipulation attempts.
- Compliance auditing
Regulatory mandates such as PCI DSS, HIPAA, GDPR, SOX, and GLBA have established guidelines that prioritize data security and privacy. By generating real time reports on malicious file activities like file creation, modification, deletion and file permission changes, FIM simplifies compliance audits and helps prove adherence to compliance mandates.
FIM challenges for enterprises
In the long term, as enterprises upscale their network and business structures, many traditional FIM tools struggle to cope with the sophistication of the business and the volume of data. Enterprises confront various challenges while dealing with FIM solutions. Some of them are:
- Complexity: FIM solutions can be sophisticated and complex in nature. Configuring and deploying a FIM solution across the enterprise network requires professional expertise. Most traditional FIM tools are configured manually and involve varied procedures based on the type of device and the type of files that are to be monitored. This causes enterprises to outsource professional service providers to deploy and configure a FIM solution.
- Scalability: Enterprises are in a continuous transit of growth and development, giving rise to expanded networks and resources. Traditional FIM solutions are not easily scalable and have limitations on the number of network assets and sensitive files that can be monitored. This leads enterprises to invest more in FIM software licenses or invest in finding a new FIM solution every time they expand the network.
- False positives: Traditional FIM fails to detect and distinguish legitimate file changes from suspicious file changes. This creates excessive noise in the enterprise network, giving rise to excessive false positives. These false positives tend to distract the SOC from identifying potential data breaches and waste their time and energy on non-existent threats.
- Change prevention: Monitoring unauthorized file changes and generating alerts is the end goal of a traditional FIM software. But today, with excessive false positives and alert fatigue, enterprises need a FIM solution that can be proactive and reactive at the same time to prevent potential data breach incidents and ensure data security.
How to overcome FIM challenges with Log360
ManageEngine Log360 is a comprehensive SIEM solution with FIM capabilities. It can cater to the security needs of enterprises to ensure file integrity and data security. Log360 addresses the following FIM concerns of enterprises:
- Simplified deployment: Log360 enables enterprises to configure FIM for all network assets from a single console. Once the enterprise domain is configured, all the devices and applications in the domain are automatically discovered by Log360. You can then configure file monitoring by selecting the discovered devices or applications in the domain along with their corresponding file locations that contain sensitive data.
- Ability to scale: Log360's FIM capabilities can meet the data security needs of expanding enterprise networks. Log360 installs a lightweight agent for collecting file activity logs from different devices. The agent facilitates easy log collection across WANs and through firewalls in an expanding network. In an extensive network, it helps to establish network connection between Log360 and the FIM-configured device to collect log data. Moreover, the agent helps to balance the overhead load across a large network and promotes seamless functioning of FIM.
- Noise reduction: Log360 consists of predefined correlation rules and alert profiles on file integrity threats. The correlation rules and alert profiles can also be customized to flag a consecutive set of file-related events that can be potential indications of malicious file activity. By creating a custom correlation rule and enabling the corresponding alert profile, a suspicious sequence of activities can be mapped, triggering an alert. Figures 1 and 2 depict a custom correlation rule for data tampering and its associated alert profile, respectively.
- Incident response: Log360 enables you to configure workflows for the alert profiles when file-related alerts are triggered. The workflows serve as an effective part of the incident response mechanism to help you prevent the data breach and combat the impending threat to sensitive data. Figure 3 depicts the different workflows that can be configured for a custom alert profile to detect data tampering.
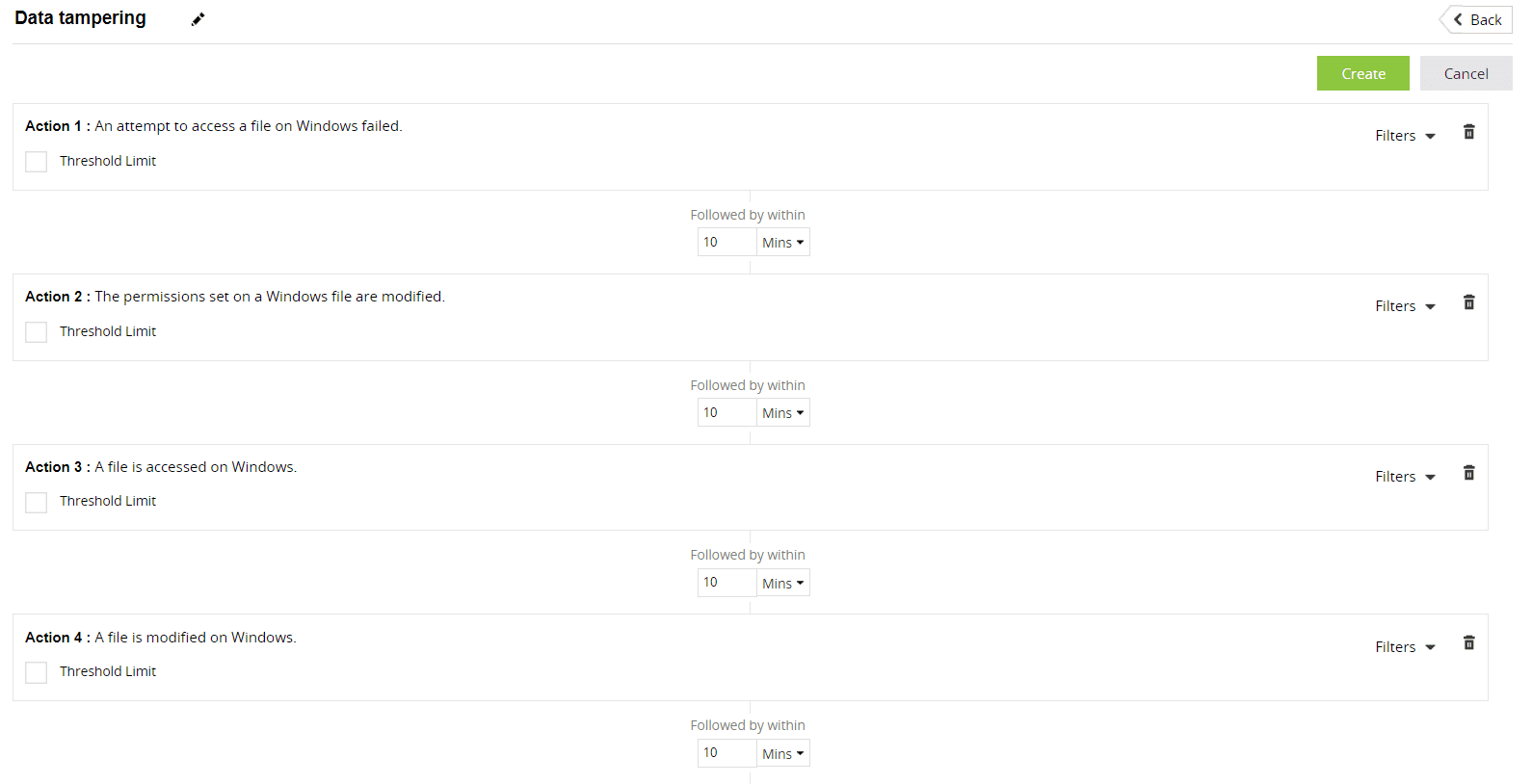
Figure 1: Custom correlation rule for data tampering in Log360
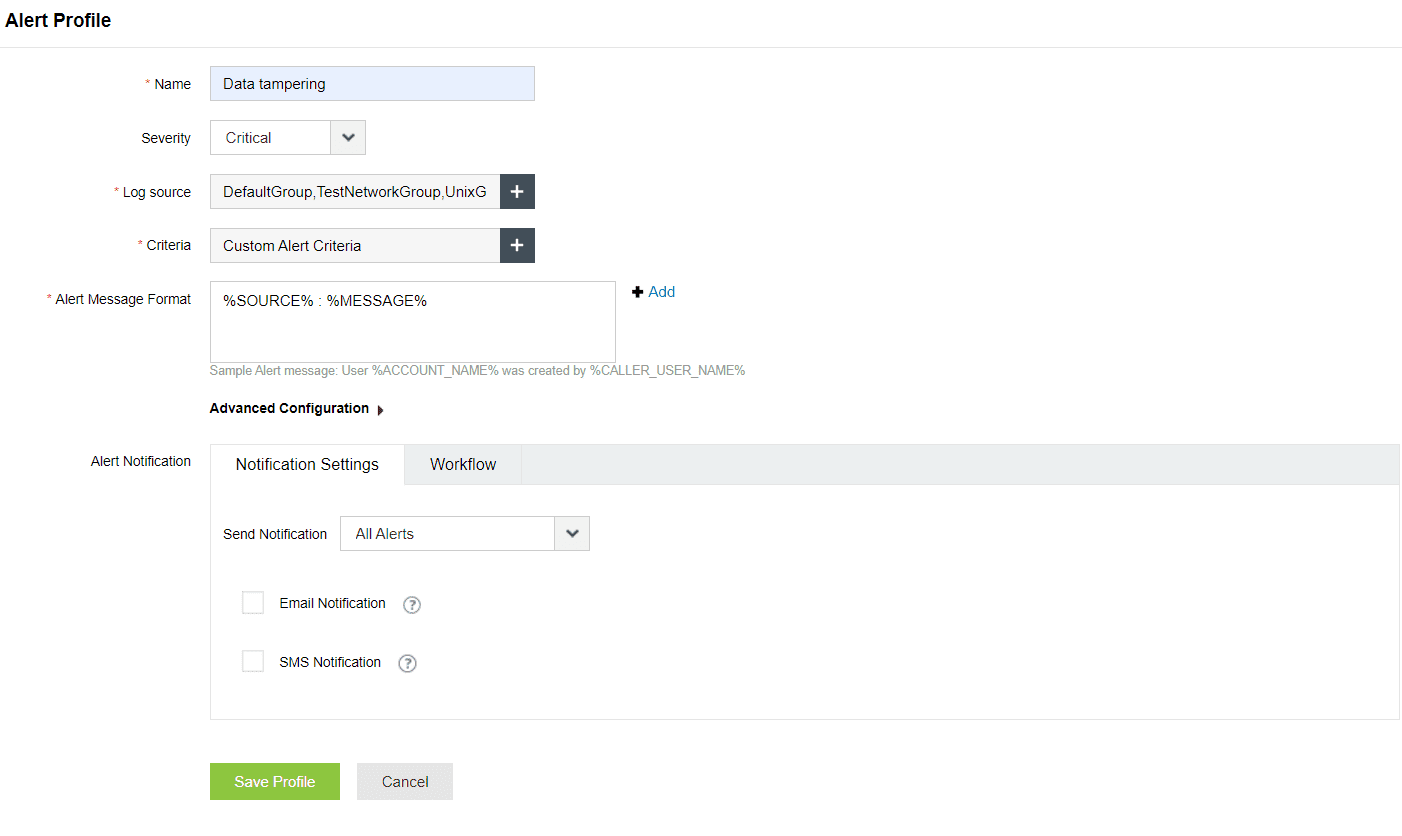
Figure 2: Correlation alert profile for data tampering in Log360
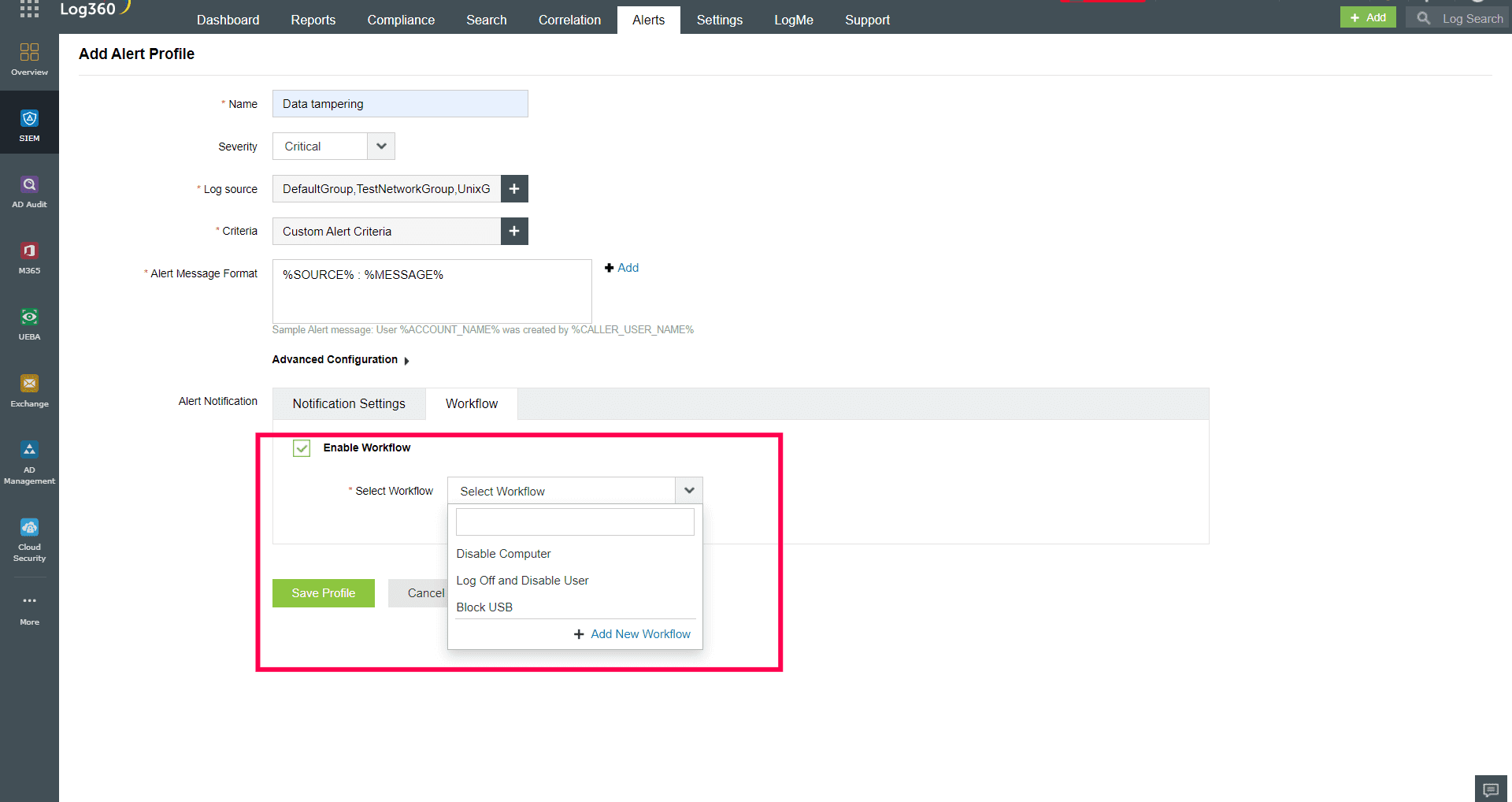
Figure 3: Incident response workflows for data tampering in Log360
Log360's file monitoring capabilities don't stop here. It is a FIM-integrated SIEM solution that can help your enterprise ensure file integrity and data security at a large scale. It equips your enterprise network with 360-degree threat detection to defend against attacks like ransomware, social engineering attacks, and Active Directory attacks.
So, what's the next step? If you would like to know more about our comprehensive FIM-integrated SIEM solution, sign up for a personalized demo or try a free, 30-day trial of Log360 now!



