Securing sensitive financial data and ensuring its confidentiality, integrity, and availability online poses significant challenges for the banking, financial services, and insurance (BFSI) sector. With the prevalence of online banking, Unified Payments Interfaces (UPIs), protecting financial records (files) and data stores (file servers) from data tampering and insider threats is crucial. It demands organizations to employ a robust data security solution that is capable of auditing unauthorized access and modifications to critical files and ensuring compliance with data security mandates.
The role of file integrity monitoring in financial data security
File integrity monitoring (FIM) is the process of auditing unauthorized access and changes to critical files and folders to prevent attempts of data tampering. It helps to identify unauthorized file modifications, determine their origin, and track when and where the changes occurred. By carrying out file integrity checks, FIM tools enable comprehensive file monitoring and ensure the privacy and integrity of financial data.
A FIM solution with advanced change intelligence, file activity auditing, alert triaging, and compliance management capabilities might be a wise choice for ensuring data security and privacy, especially within the BFSI sector. It could serve as the first line of defense to prevent unauthorized access and changes to sensitive information to safeguard financial bodies from violations of financial privacy laws.
Before we explore how a FIM integrated SIEM tool such as ManageEngine Log360 can aid in bolstering data security and privacy in the banking and finance sector, let's first understand the various types of vulnerable data in this industry and the security use cases that present substantial threats to this data.
Types of data in the BFSI targeted by cyber criminals
Personally identifiable information (PII): BFSI companies collect customers' personal information via the Know Your Customer process. This includes the customer's name, age, gender, and contact details. Protecting customers' PII is mandated by data security regulations such as the General Data Protection Regulation (GDPR) for all financial institutions.
Personal financial information: Institutions in the BFSI collect personal financial information from their customers to assess their current financial position before sanctioning loans, mortgages, or other forms of funding. This information includes customers' bank account numbers, debit and credit card details, income statements, credit scores and insurance claims. The Gramm-Leach-Bliley Act (GLBA) enforces the protection of personal financial information to ensure the financial privacy of consumers.
Payment card information: Banks and payment card industries issue debit and credit cards to customers for cashless card-based transactions. These transactions are recorded, maintained, and protected by banks, payment card companies, and payment gateways because they contain sensitive financial details such as the cardholder's name, card number, expiration date, and the card verification value. The Payment Card Industry Data Security Standard (PCI DSS) mandates the above financial bodies to comply with debit/credit card information privacy policies to ensure the security of payment card information and transaction details.
Data security use cases in the banking and finance sector
Some common data security incidents in the banking and finance sector are:
Unauthorized access
Unauthorized access occurs when external threat actors or unauthorized users access sensitive financial data through illegitimate means. External threat actors gain access via unethical practices such as hacking, phishing, and credential theft. Conversely, malicious insiders may utilize stolen credentials of privileged users to brute force and compromise accounts, thereby accessing critical data. Both external and internal adversaries may then move laterally across the network and escalate their privileges to access other repositories of sensitive data.
Data manipulation
Adversaries may not always seek to steal or exfiltrate data once they access sensitive financial records. Instead, they may try to alter the actual data and modify certain sensitive areas to distort the perception towards a financial institution. For instance, attackers may modify the credit scores of customers, thereby affecting the overall credibility of the bank. This leads to various misconceptions about the bank that may cause devastating financial losses and reputational damage.
Data exfiltration
Data exfiltration is the act of stealing sensitive financial data like credit card details. Attackers tend to auction off the stolen card details on the dark web, making the data available to other illegal activists, affecting the confidentiality of data and the reputation of the bank. Attackers may also lure banks to pay hefty ransoms in exchange for the stolen data. In both cases, data exfiltration destroys the credibility of the financial institution, affecting its business outcomes thereafter.
Data sabotage
Data sabotage is the process by which sensitive files and folders are completely lost or made inaccessible to the financial body. It is a byproduct of data exfiltration that leads to data loss. It disrupts the fundamental operations of the business, leading to a complete loss of customer trust, which may further lead to unrecoverable financial losses.
These ramifications of a data breach are inevitable if your organization lacks a FIM solution. Having a FIM solution in place can help you detect suspicious activities that can lead to data breaches and secure sensitive financial data.
How file integrity monitoring in Log360 can protect financial data
Log360 can help defend against threats to sensitive data in BFSI with the following capabilities.
File change audit
Log360 actively tracks any unauthorized changes to your sensitive financial records (files and folders), and generates alerts in real time, enabling the detection of potential data breach incidents. It enables you to track malicious file activities such as unauthorized file creation, deletion, modification, and permission changes in real time.
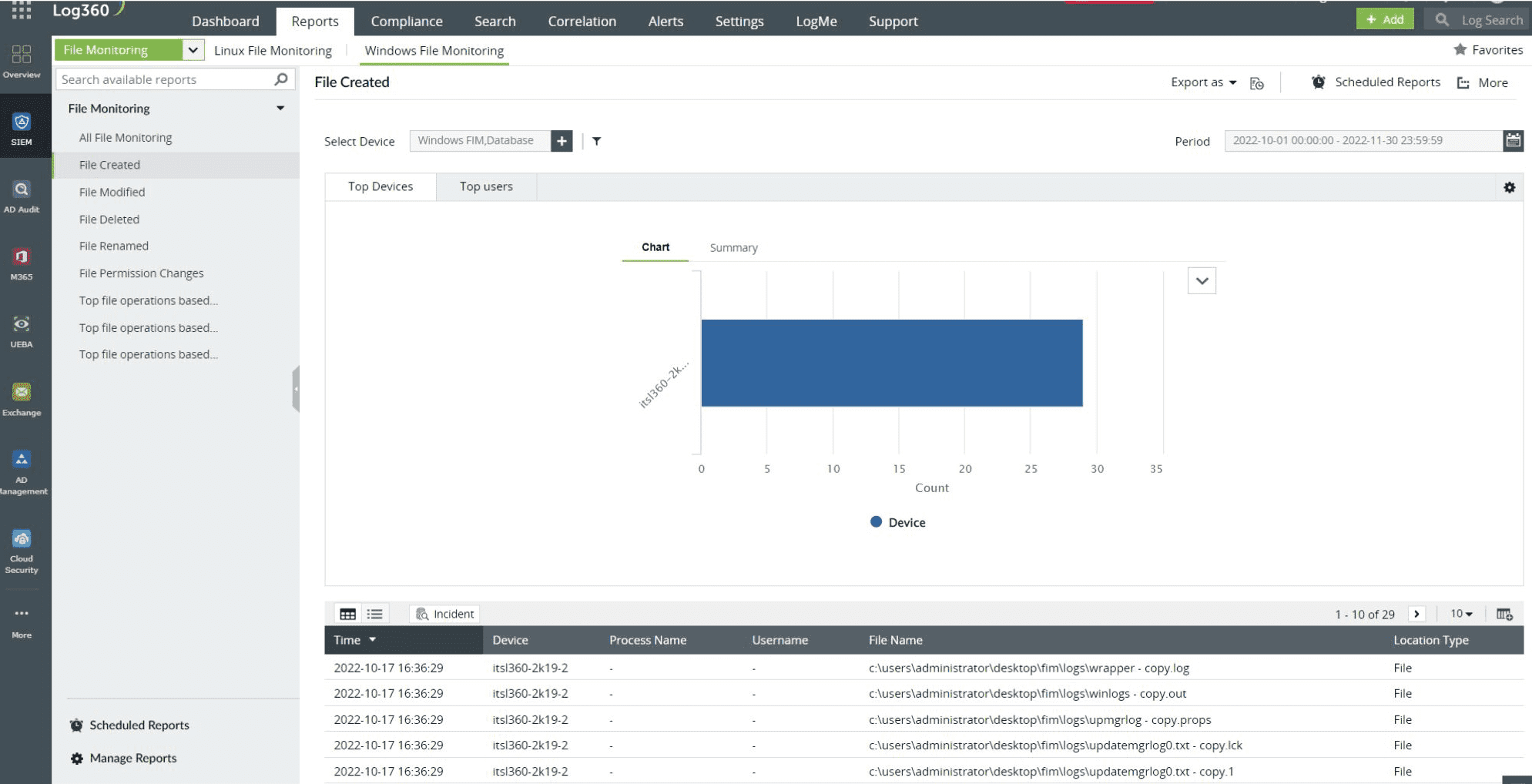
Figure 1: File Monitoring report in Log360
File-based anomaly detection
Log360's user and entity behavior analytics (UEBA) capabilities detect anomalous file activities like file creation, deletion, modification, read attempts, file permission changes, and system file changes. It tracks file anomalies based on the time at which financial data was accessed, the number of attempts to access or modify it, and suspicious patterns that associate unauthorized and unintended users with the data.
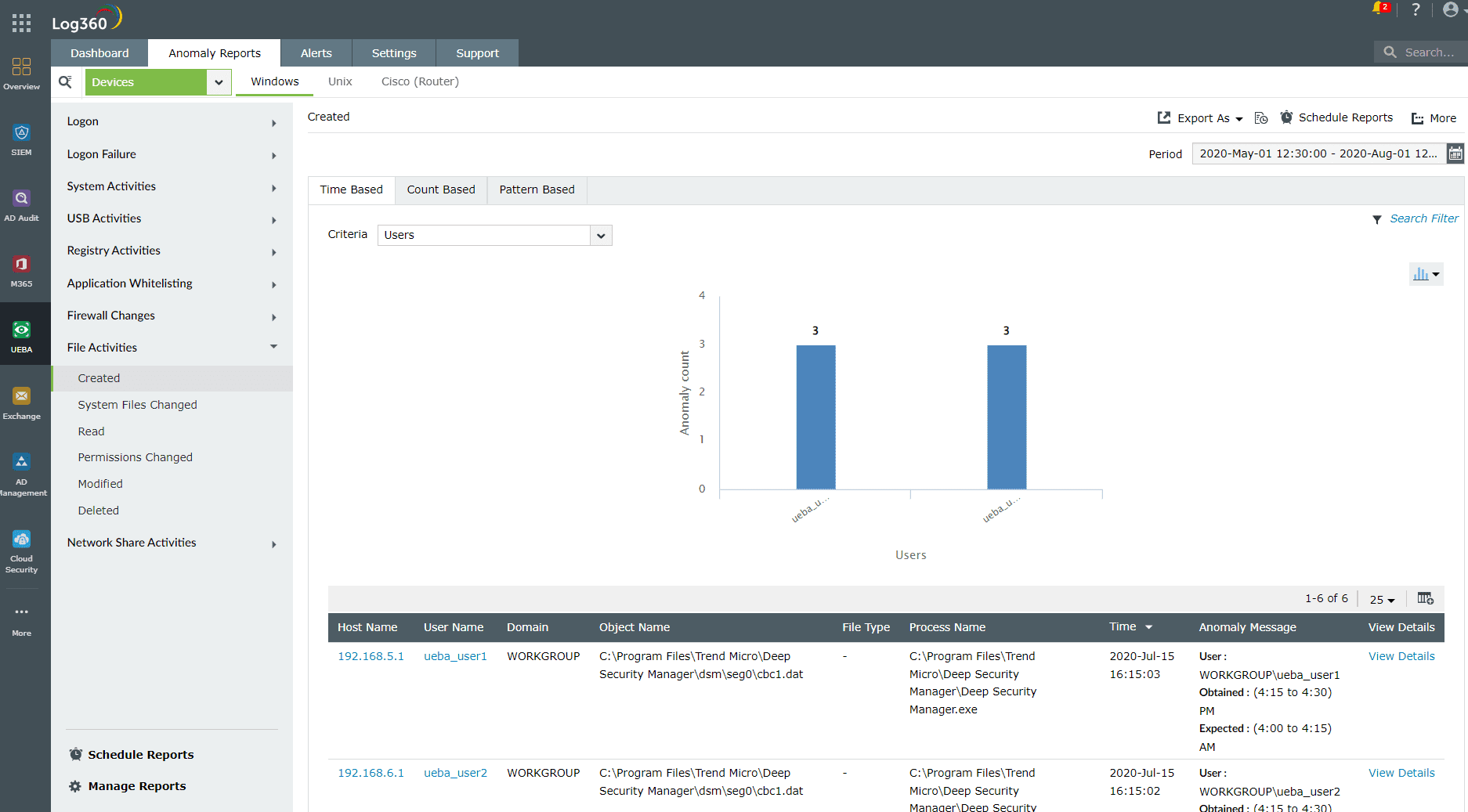
Figure 2: File-activity-based anomaly report in Log360
Compliance with data security regulations
Log360 provides audit-ready reports on file activities like file creation, modification, and deletion with respect to PII, personal financial information, payment card details and financial records that prove adherence to compliance mandates regulating data security. It comprises predefined reports and alert profiles for major compliance mandates in the BFSI sector, including PCI DSS, GLBA, SOX, and GDPR.
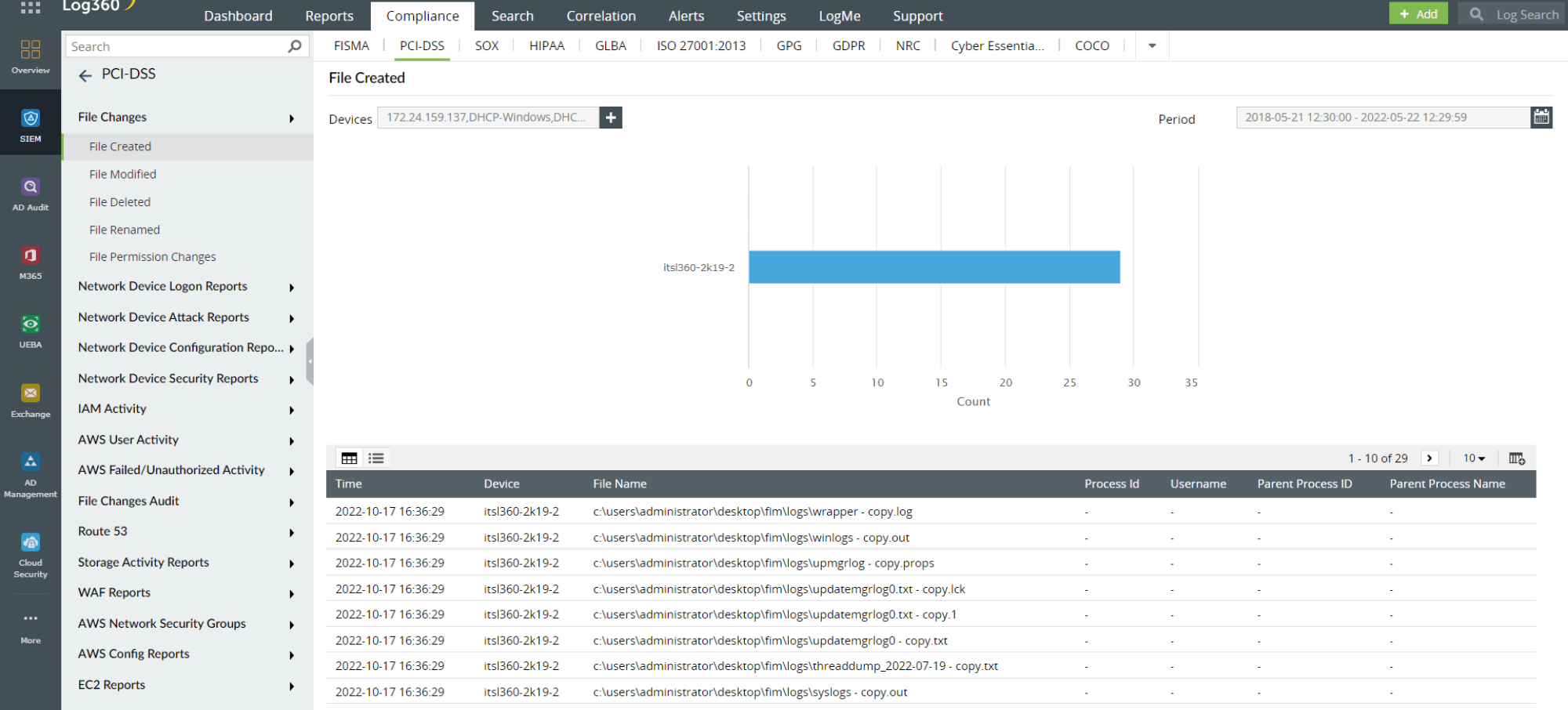
Figure 3: File-activity-based compliance report in Log360
Further, Log360 provides complete security in your network with centralized log management, real-time correlation, ML-based anomaly detection, integrated CASB and DLP capabilities, and much more.
To explore more, sign up for a personalized demo or try a free, 30-day trial of Log360 now!



