Did you know that according to the 2023 Insider Threat Report by Cybersecurity Insiders, 74% of organizations say insider attacks have become more frequent and more than half of organizations have experienced an insider threat in 2022. Also, 8% of organizations experienced more than 20 insider threats.
In this page, we will unveil the preventative strategies to mitigate insider threat and shed light on how file integrity monitoring (FIM) plays an important role.
What is an insider threat?
A security threat that comes from within the intended organization is known as an insider threat. Usually, it involves a current or former employee or business associate who misuses their access to privileged accounts or sensitive data on an organization's network. Malicious, or even ignorant insiders, include third-party vendors, contractors, and partners.
Depending on their motives, insider threats can be unintentional or malicious. Insider risks that aren't purposeful can come from a negligent employee falling for a phishing attack. Intentional data theft, corporate espionage, and data destruction are examples of malicious threats.
For additional information regarding insider threats, check out this article.
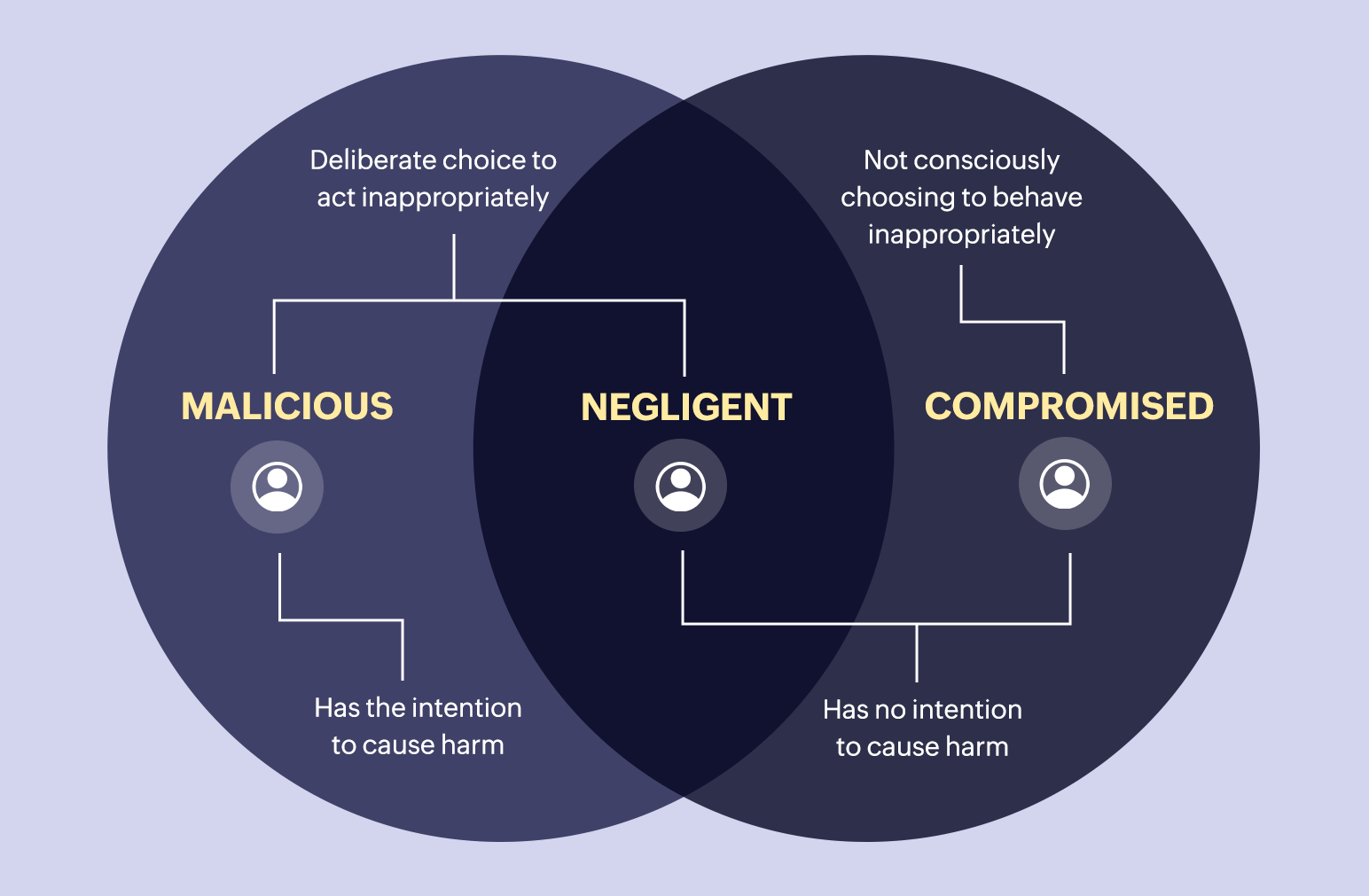
Figure 1: Types of Insider threat
How to prevent insider threat?
- Clearly define your policies and procedures: Provide clear instructions to employees on permissible use policies, data management practices, and security protocols. Ensure that every employee is aware of their responsibilities with regards to sensitive data.
- Put role based access controls (RBAC) into practice: Restrict access to systems and sensitive data according to the roles and responsibilities of employees. Employees should only have access to the data required to carry out their duties.
- Track user activity: Use tools to keep tabs on user behavior, systems, and network of the organization.
- Implement strong authentication: Use MFA to add an extra layer of security to access private and sensitive information.
- Educate employees: Regularly train employees and conduct awareness campaigns to inform them of insider threat risks and teach them how to spot and report suspicious activity.
- Review and update security policies on a regular basis: It is imperative to periodically assess and revise security policies and processes in order to tackle emerging risks and vulnerabilities, as security threats and technology undergo constant evolution.
- Implement DLP solutions: Use DLP solutions to monitor and stop sensitive data from being sent outside of the company's network without authorization. Policies pertaining to the management of sensitive information can be enforced with the use of DLP solutions.
Preventing insider threats using FIM in Log360

Figure 2: FIM features to prevent insider threats
FIM is a valuable tool in detecting, mitigating, and preventing insider threats. Here's how FIM addresses insider threats:
Monitoring user activities
FIM keeps an eye on everything that users do, including accessing, modifying, and deleting files. FIM can identify unusual behaviors and potential insider threats by monitoring user interactions with sensitive files and directories. Unauthorized access attempts, unusual file modifications, and suspicious file activity patterns fall under this category.
ManageEngine Log360 generates thorough reports with accurate integrity information (file creation, deletion, modification, permission changes, operation changes) in multiple formats, including CSV and PDF. You can automatically receive the reports at regular intervals with the help of flexible report scheduling.
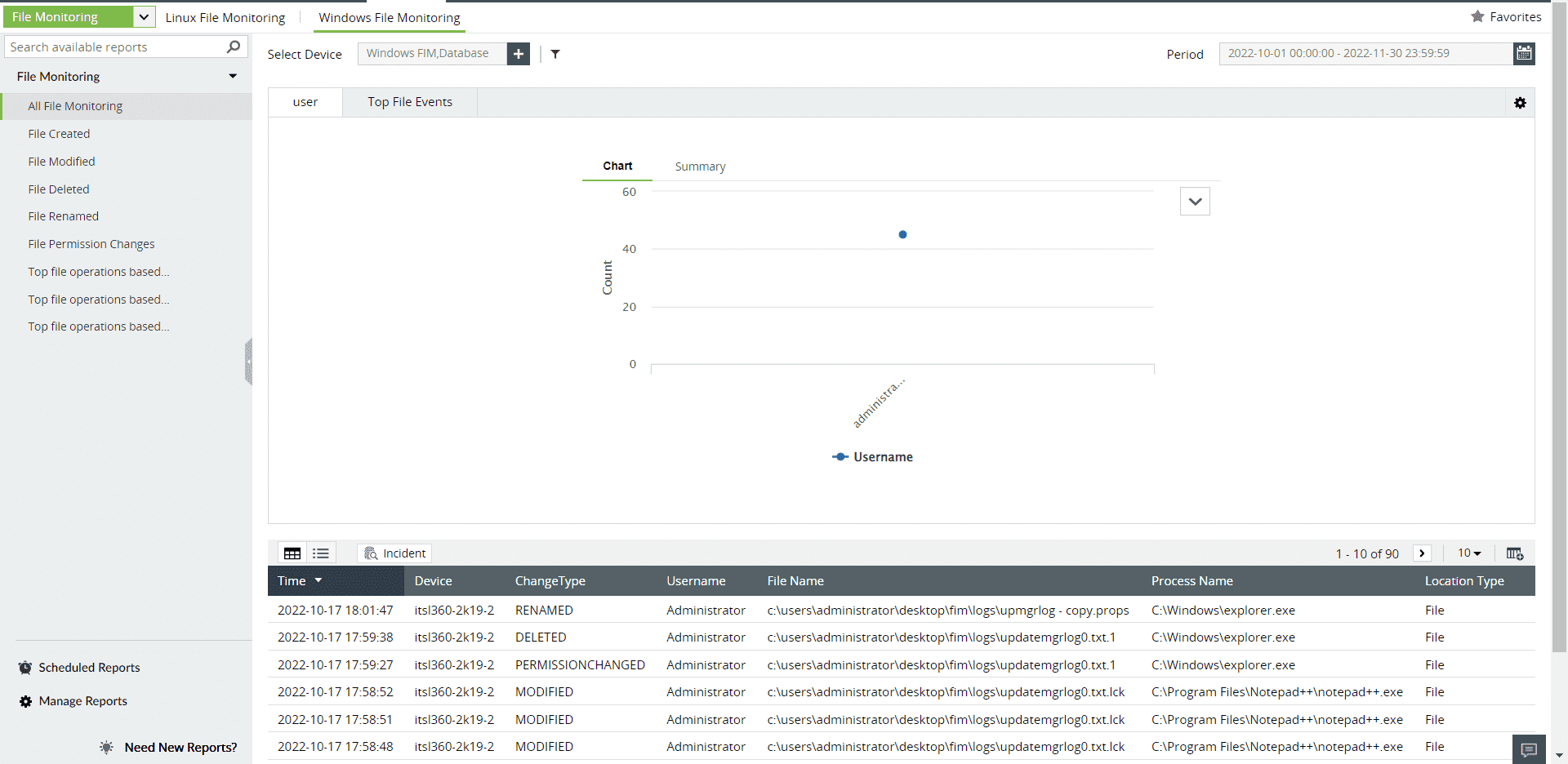
Figure 3: File Monitoring Reports tab in ManageEngine Log360
Identifying Abnormal Behavior
Within an organization, FIM sets standard file activity and user behavior. Alerts can be triggered by any departure from this baseline, including illegal modifications to crucial system configurations or excessive access to private data. Security teams can look into this further and ascertain whether the activity is harmless or suggestive of insider threats.
ManageEngine Log360 provides immediate alerts for important updates, including change in rules or access policies for database-stored files and folders. You can do this while configuring the alert criteria (see Figure 3) as per your needs. Alert criteria can also be created based on custom thresholds and user actions.
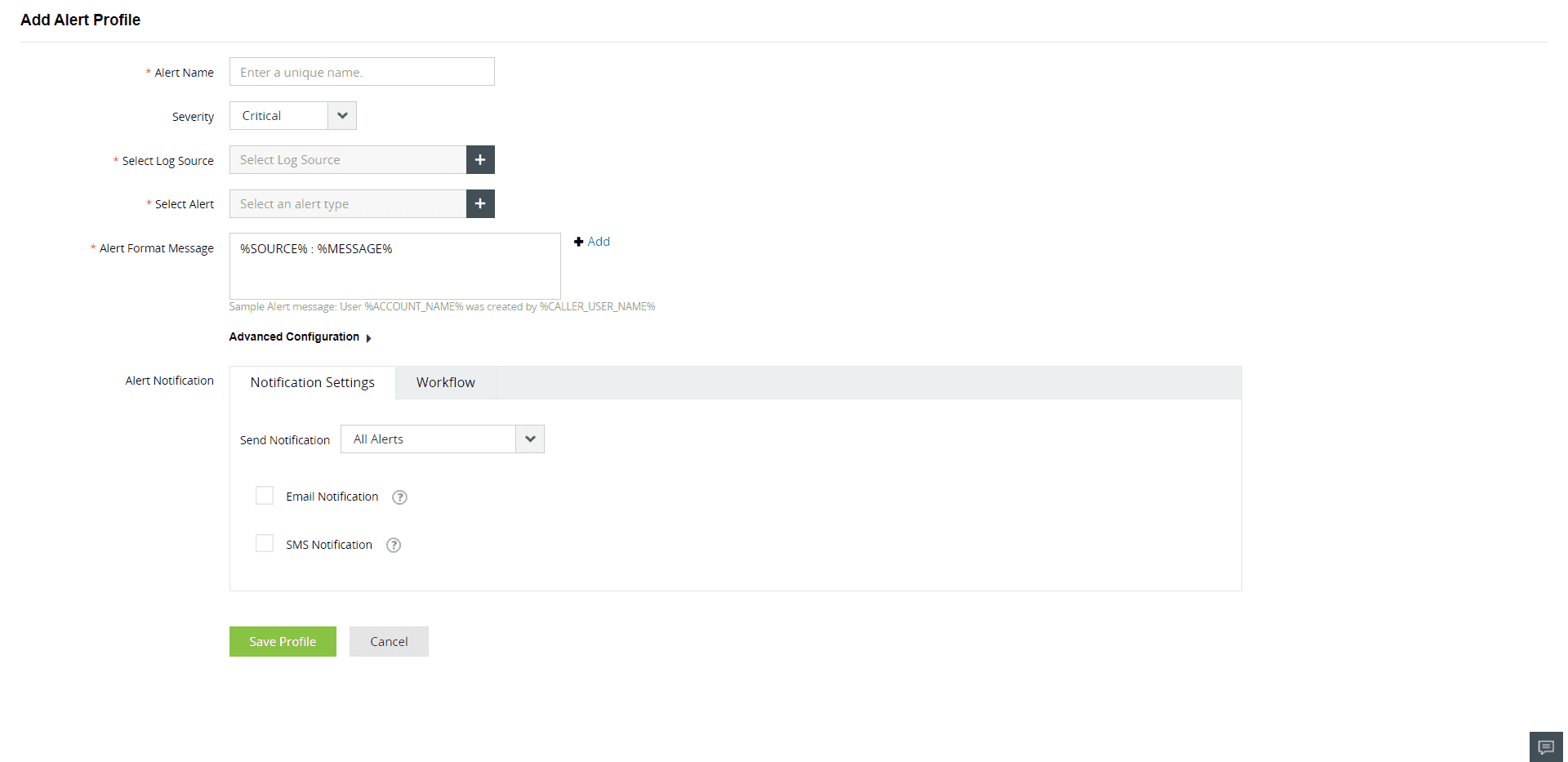
Figure 4: Creating alert profiles in ManageEngine Log360
For example, a predefined alert is triggered when a file is deleted in Linux platform with FIM as host type.
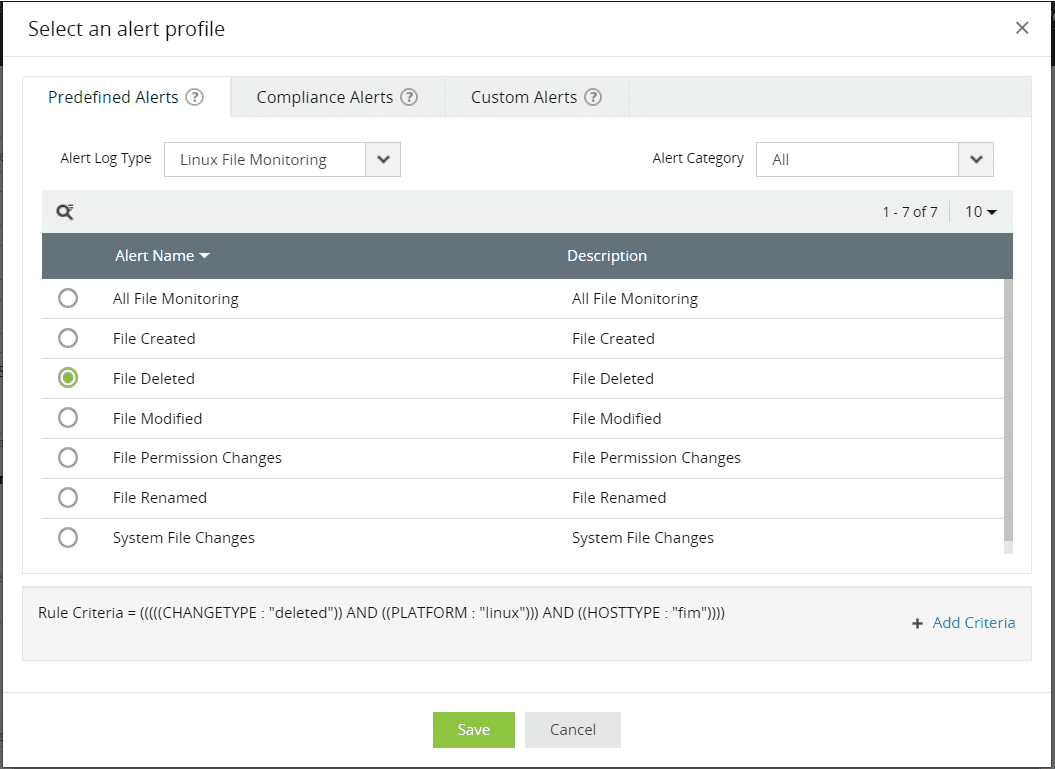
Figure 5: Predefined alerts tab in ManageEngine Log360
You can also create custom alerts as shown below.
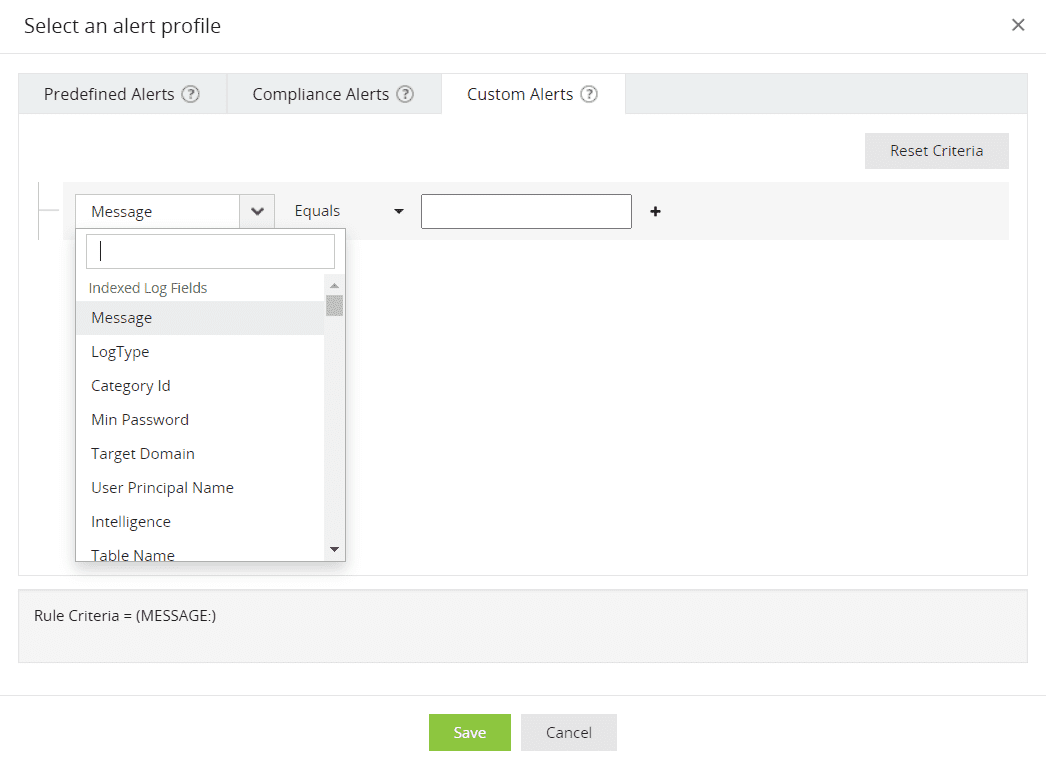
Figure 6: Custom alerts tab in ManageEngine Log360
Obtain instant alerts on critical changes that take place in your files and folders.
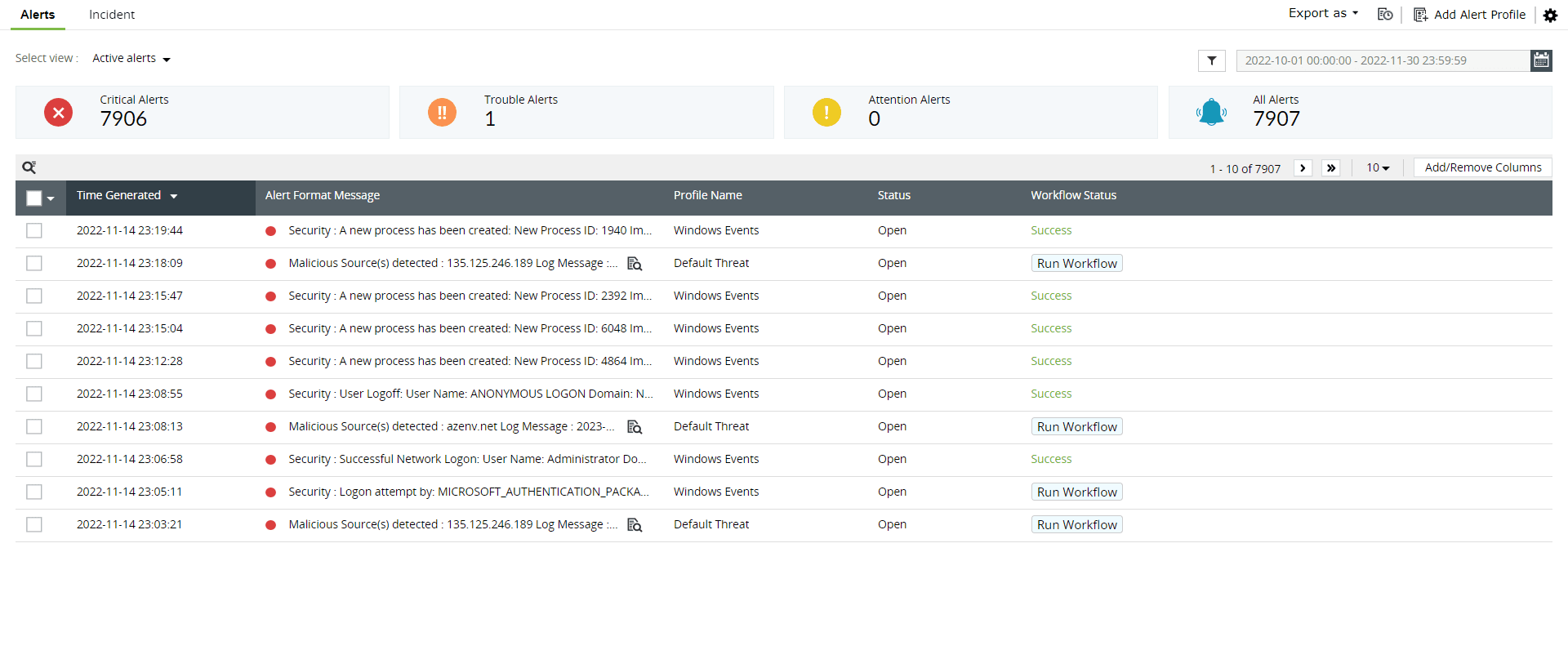
Figure 7: Alerts tab in ManageEngine Log360
Monitoring data exfiltration and privileged users:
Employees or contractors who attempt to steal confidential information are frequently considered insider threats. Unauthorized attempts to upload or copy sensitive data to unapproved cloud services or external storage devices can be identified by FIM. Privilege users with higher privileges within the organizations can also pose a threat to the organization. System administrators and database administrators are examples of privileged users whose activities can be monitored by FIM to make sure they are not misusing their access privileges or carrying out malicious activities.
ManageEngine Log360's dashboard's provides in-depth graphical representation of all the activities performed on the files and folders. These are represented as separate sections as shown below:
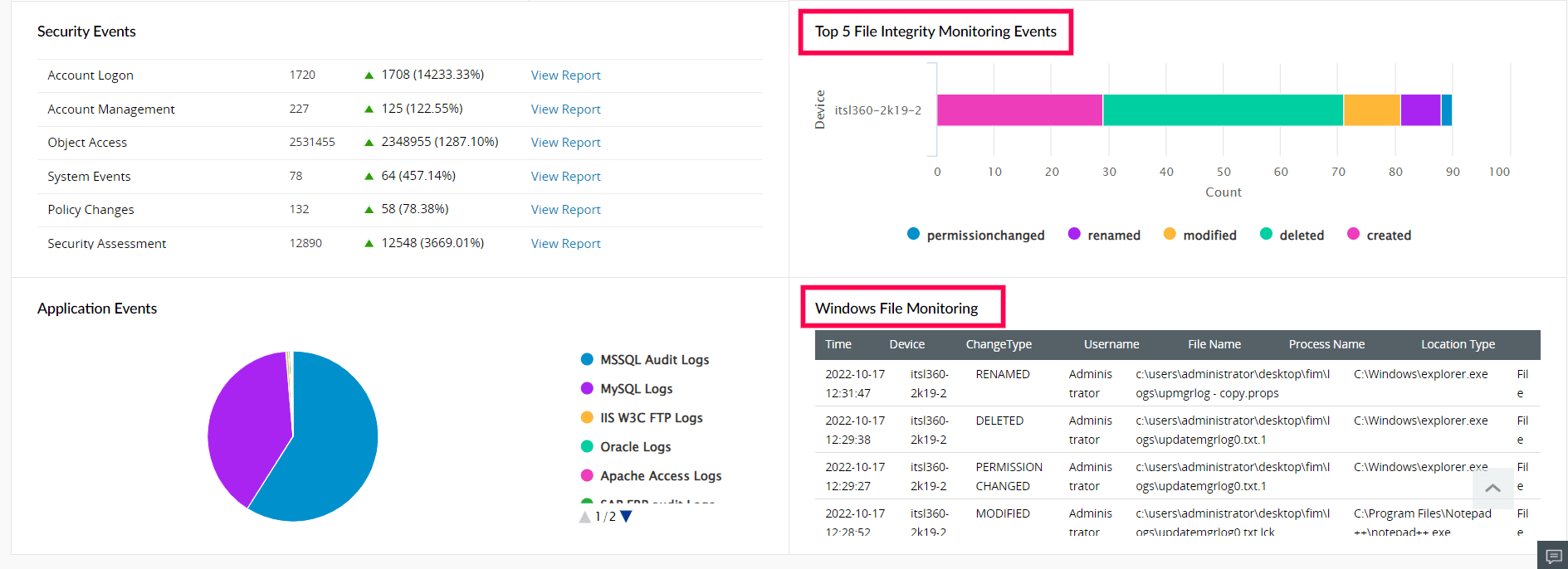
Figure 8: File based widgets in ManageEngine Log360's dashboards
Enforcing Security Policies
Through its ability to verify that files and system configurations follow defined security standards, FIM assists in the enforcement of security policies and compliance requirements. It can impose file permissions, encryption protocols, and access controls to stop insiders from gaining unwanted access or modifying confidential information.
ManageEngine Log360 enables organizations to fulfill the requirements of essential regulatory mandates like PCI DSS, SOX, HIPAA, and FISMA.
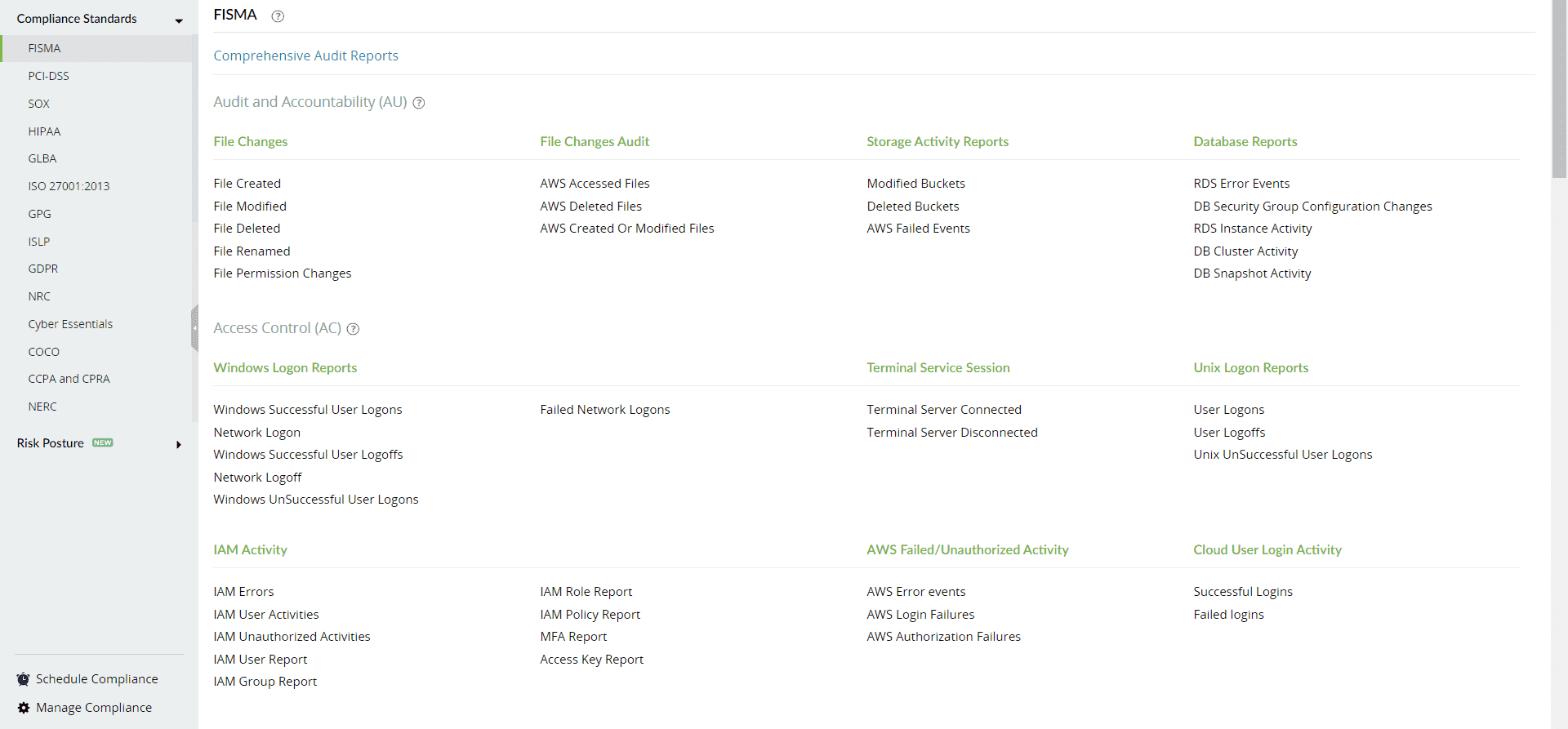
Figure 9: Compliance tab in ManageEngine Log360
Correlate events to ensure file integrity
Users can specify a sequence of events that can indicate an anomaly or a security loophole. A deeper understanding of the incident can be obtained by correlating the events occurring within your network, which may have been overlooked while examining the situation at the individual level.
All modifications have real-time answers to the "what, when, where, and how" in the correlation reports of ManageEngine Log360. A thorough audit record of every modification made to files and folders is available in the correlation reports.
Figure 10: Correlation reports in ManageEngine Log360
Organizations seeking to minimize insider threats and safeguard sensitive data and systems from illegal access, modification, and exfiltration should consider using FIM. Organizations can lessen the likelihood of data breaches and security incidents by proactively monitoring file integrity and user actions. This allows for more effective detection, investigation, and response to insider threats.
Ready for the next step?
Are you looking for ways in which you can protect your organization's sensitive information from being misused? Sign up for a personalized demo of ManageEngine Log360, a comprehensive SIEM solution that can help you detect, prioritize, investigate, and respond to security threats.



