The ever-increasing number and complexity of cyberattacks has led to an increase in the efforts to combat and reduce them. Organizations and security agencies understand the importance of having effective cybersecurity measures in place, continuing to work towards building better, more modern approaches to identifying, managing, and mitigating growing cyber risks. At present, organizations are essentially adopting Zero Trust to have a defense mechanism against sophisticated cyberthreats and to improve their security posture.
Zero Trust is a term used to define a set of concepts and security standards that prevent unauthorized access to systems and networks. Zero Trust architecture works on the inherent assumption that no user, device, or network is trustworthy. Any unauthorized access to the internal IT infrastructure and resources will be denied, allowing only required access and only to those with verified authentication. In other words, Zero Trust architecture blocks any unauthorized attempts to access internal data or resources.
The United States’ Cybersecurity and Infrastructure Security Agency (CISA) defines Zero Trust as "an approach where access to data, networks, and infrastructure is kept to what is minimally required and the legitimacy of that access must be continuously verified."
CISA formulated the Zero Trust Maturity Model (ZTMM), which provides the framework for organizations to transition towards a Zero Trust architecture. The first version of CISA's ZTMM was released in September 2021, while the second, more advanced version was released in April 2023. The second version includes updates based on the latest government guidelines and the feedback received on the first version.
The latest version of the ZTMM defines the four maturity stages: traditional, initial, advanced, and optimal. It is worth noting that the first version of the ZTMM only had three stages. An additional stage called initial was added between the traditional and advanced stages in the second update. This addition makes the transition more practical and achievable. Each subsequent stage requires adopting increasingly complex strategies for greater levels of protection and security.
The ZTMM consists of five pillars, namely identity, devices, networks, applications and workloads, and data. These pillars represent a gradient of implementation. The model also includes details on three cross-cutting capabilities: visibility and analytics, automation and orchestration, and governance. Let us understand the key aspects of each of these pillars across the different stages of maturity.
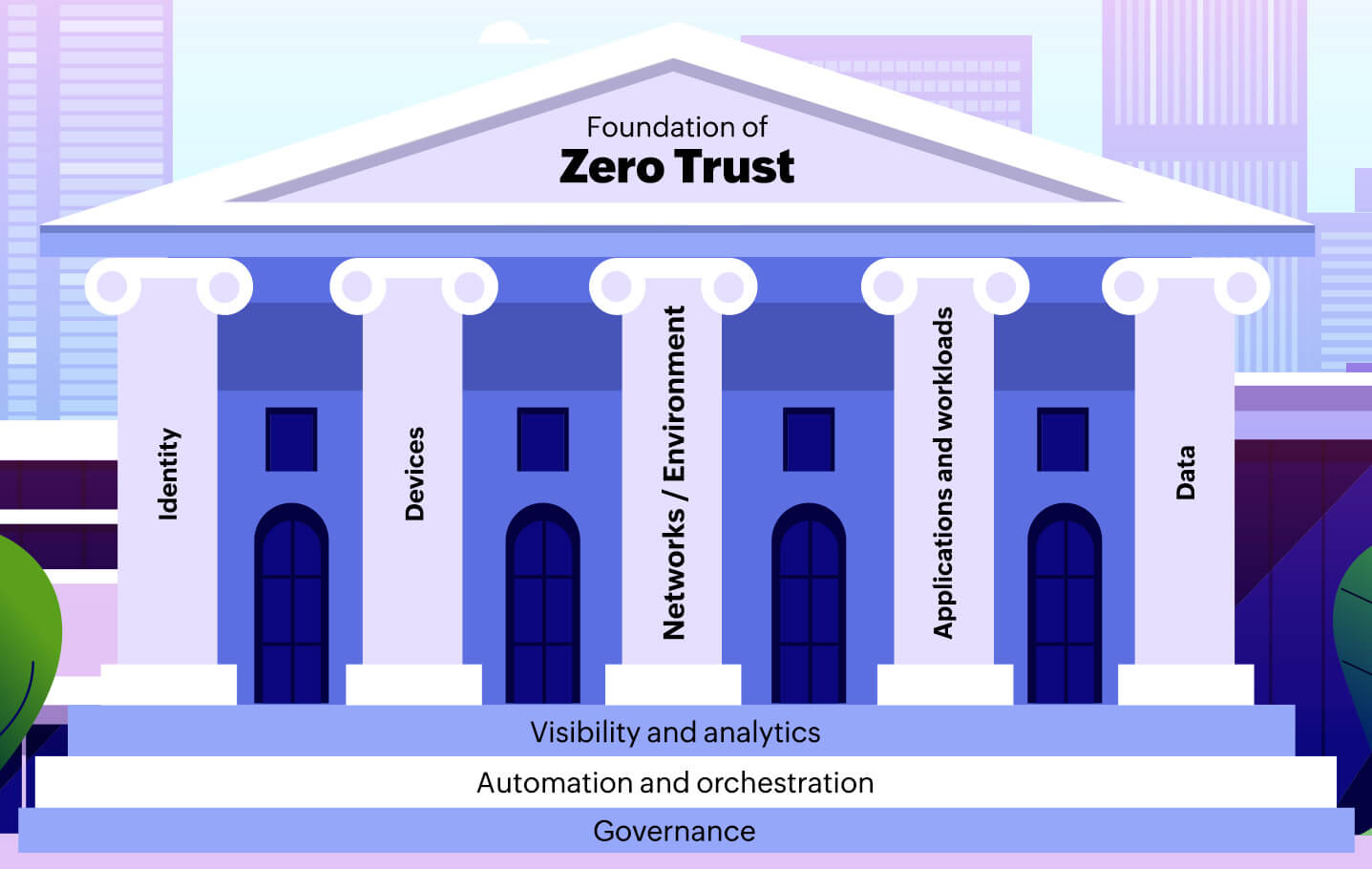 Figure: Foundation of Zero Trust
Figure: Foundation of Zero Trust
This pillar, as the name suggests, focuses on identifying users and devices that are authentic and have authorized access. According to CISA, "identity refers to an attribute or set of attributes that uniquely describes an agency user or entity, including non-person entities." Identity functions include authentication and risk assessment. As organizations progress across the different maturity stages from traditional to optimal, they move from using single passwords to MFA to phishing-resistant MFA and finally towards continuous validation and risk analysis. They also move from limited, manual risk assessment based on static rules towards a more automated process based on dynamic, real-time assessment of user behavior.
The focus here is on securing any devices that can connect to the organization’s network, including systems, laptops, servers, and IoT devices. This pillar addresses compliance monitoring, asset management, and data access. Organizations move from limited visibility over device compliance towards enforced compliance integrated with threat protections across all devices. From manual tracking of device inventories, companies evolve towards automated, continuous device management and tracking. Data access granted to devices also moves towards becoming more secure with real-time device risk analytics.
This pillar is focused on monitoring and securing all network communications across the organization’s internal network and the internet. Functions of this pillar include network segmentation, encryption, and threat protection. From using a large perimeter or macrosegmentation to define their network architecture, organizations strive to move towards fully distributed ingress or egress micro-perimeters and deeper internal microsegmentation. Encryption of internal and external traffic also improves tremendously across the stages. In terms of threat protection, organizations move from relying on known threats, static traffic filtering, and basic analytics towards more advanced and more thorough ML-based threat protection and filtering.
The focus here is to monitor and secure all system applications and workloads executed both on-premises and remotely (in the cloud). This pillar addresses access authorization, threat protection, accessibility, and application security. The progress across the maturity stages includes moving from local authorization and static attributes to centralized, continuous authentication based on real-time risk analytics as well as moving from threat protection with minimal workflow integrations towards strongly integrated threat protection with dynamic analytics based on application behavior. While the initial stages rely largely on application testing prior to deployment, the later stages ensure regular, automated security testing integrated throughout the application life cycle.
Securing all forms of data—whether at rest or in transit—across different devices, applications, and networks forms the crux of this pillar. Functions addressed by this pillar include inventory management, encryption, and access determination. From manually categorizing and inventorying data, organizations move towards integrating data categorization with ML models using automated, continuous data inventorying with robust tagging and tracking. From storing data primarily unencrypted and on-premises, organizations evolve towards encrypting all data and storing it in the cloud or in remote environments. They also move towards advanced data protection and access controls, using the principles of just in time and just enough data access.
It is worth noting that the journey towards achieving Zero Trust is not an easy feat. It involves a lot of investment and restructuring on the part of the organization. It is also not a plug-and-play solution that can be implemented and forgotten about. As the technology landscape continually evolves, so does the threat landscape. Even after implementing and achieving a state of Zero Trust architecture, an organization needs to monitor that architecture continuously and regularly update it in order to keep up with and address the latest and upcoming cyberthreats. It is thus crucial to work towards solutions that address these changes and continue doing so.
While CISA's ZTMM is primarily intended for federal agencies, other organizations across different industries can also benefit hugely from it. The model provides a detailed, step-by-step framework to help organizations shift towards adopting Zero Trust architecture. It allows organizations to identify, detect, respond to, and mitigate cyberthreats more effectively. It also focuses on continuous improvement, staying up to date with emerging threats, and adapting ZTMM strategies accordingly. With this model, organizations will be much better prepared to combat threats in this ever-evolving, dynamic environment.
In a digital environment, there are lots of network devices involved all across the network. Essentially, it is important to monitor these network devices to enhance the cybersecurity of the enterprise through maintaining efficient network infrastructure while minimizing risks and mitigating potential cyberthreats. Monitoring these devices helps in proactive threat detection, incident response, compliance adherence, asset management, performance optimization, and network troubleshooting.
Our SIEM solution, ManageEngine Log360, helps prevent attacks by restricting access to systems, detecting any unusual events or activities, and initiating automatic remediation processes. To see how Log360 can help your organization defend against cyberattacks, sign up for a free, personalized demo.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.