At the surface level, a file integrity monitoring software appears to be a change monitoring tool that tracks file activities, audits file access, monitors file permissions changes, notifies abnormal file activities, and enables compliance auditing. But looking deeper shows that it's a complex solution that requires streamlined policies, fine tuned correlation rules, alert triaging, and audit ready reports to monitor unauthorized file tampering, and data loss. That is why it's essential to dive deeper than surface-level evaluation and into the intricacies of file integrity monitoring to choose the best FIM tool for your network.
1. Built-in asset inventory
For a distributed organization with a multitude of assets, a FIM software with asset management capabilities is highly essential. A built-in asset inventory within a FIM software enables you to organize and accommodate all critical assets in the network.It helps identify and prioritize assets that require continuous file monitoring, as monitoring files in non-critical assets can generate excessive logs, creating unwanted noise.
As a SIEM tool with integrated FIM capabilities, Log360 ensures data integrity monitoring for all files and folders and provides total data security coverage for your network. It also enables you to configure file monitoring and verify file integrity for all your data sources, including workstations and file servers, on a single console, thereby bringing security, compliance, and IT into focus.
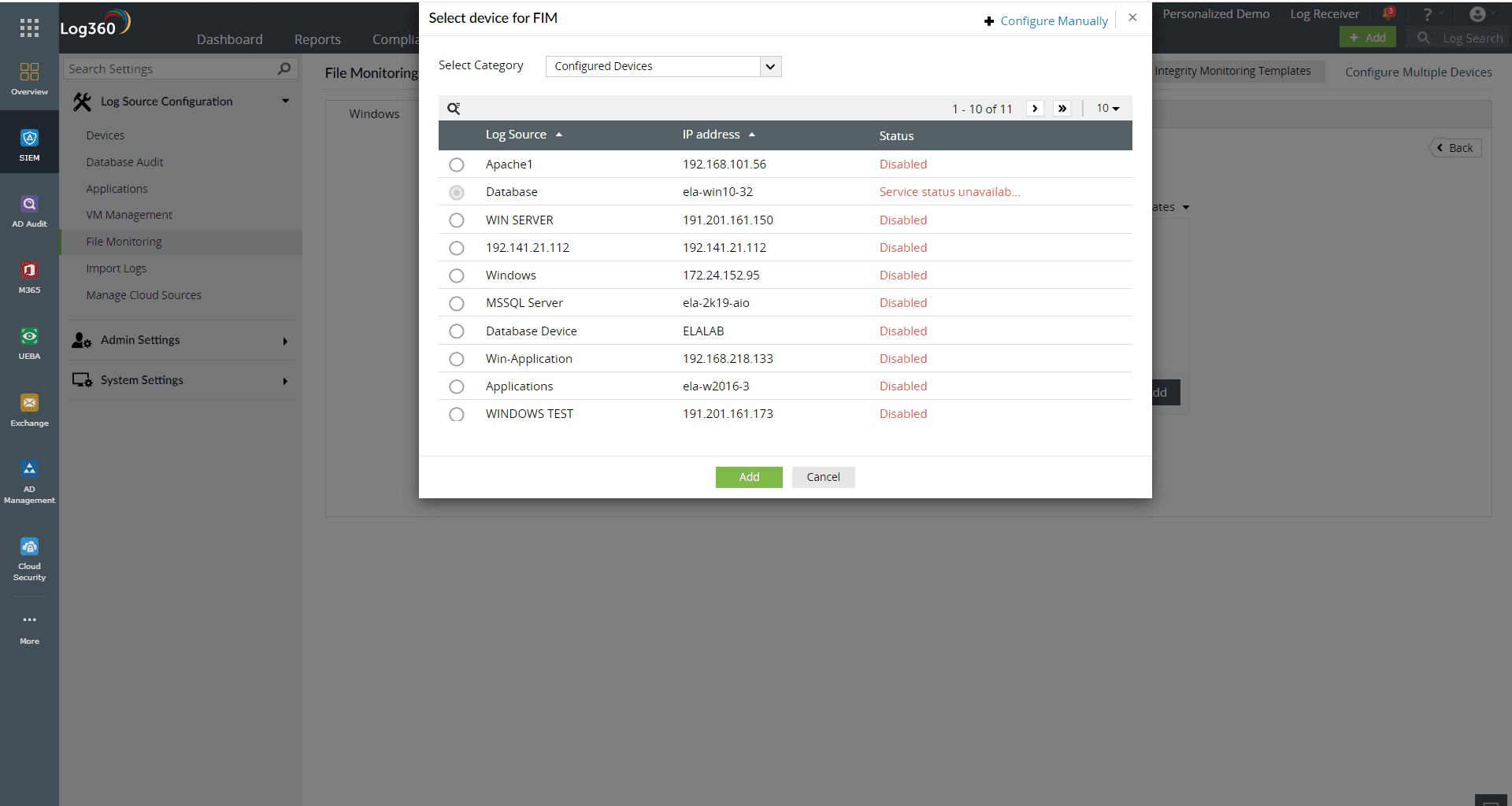
Figure 1: FIM configuration sources in Log360
2. 360 degree file coverage
A FIM tool should basically facilitate Windows and Linux file auditing. It should essentially track unauthorized file changes related to critical system files, configuration files, registry files and directory files in Windows and Linux devices. It should also enable data integrity monitoring and protect sensitive information in databases, file servers and file systems.
3. Simplified deployment
A FIM tool should be easily deployable across the network for all file systems, file servers, workstations and databases from a single console. Log360 enables organizations to configure FIM for all network assets from a unified console. Once the organization domain is configured under Log360, all the devices and applications in the domain are automatically discovered by Log360. You can then configure file monitoring by selecting the discovered devices or applications in the domain along with their corresponding file locations that contain sensitive data.
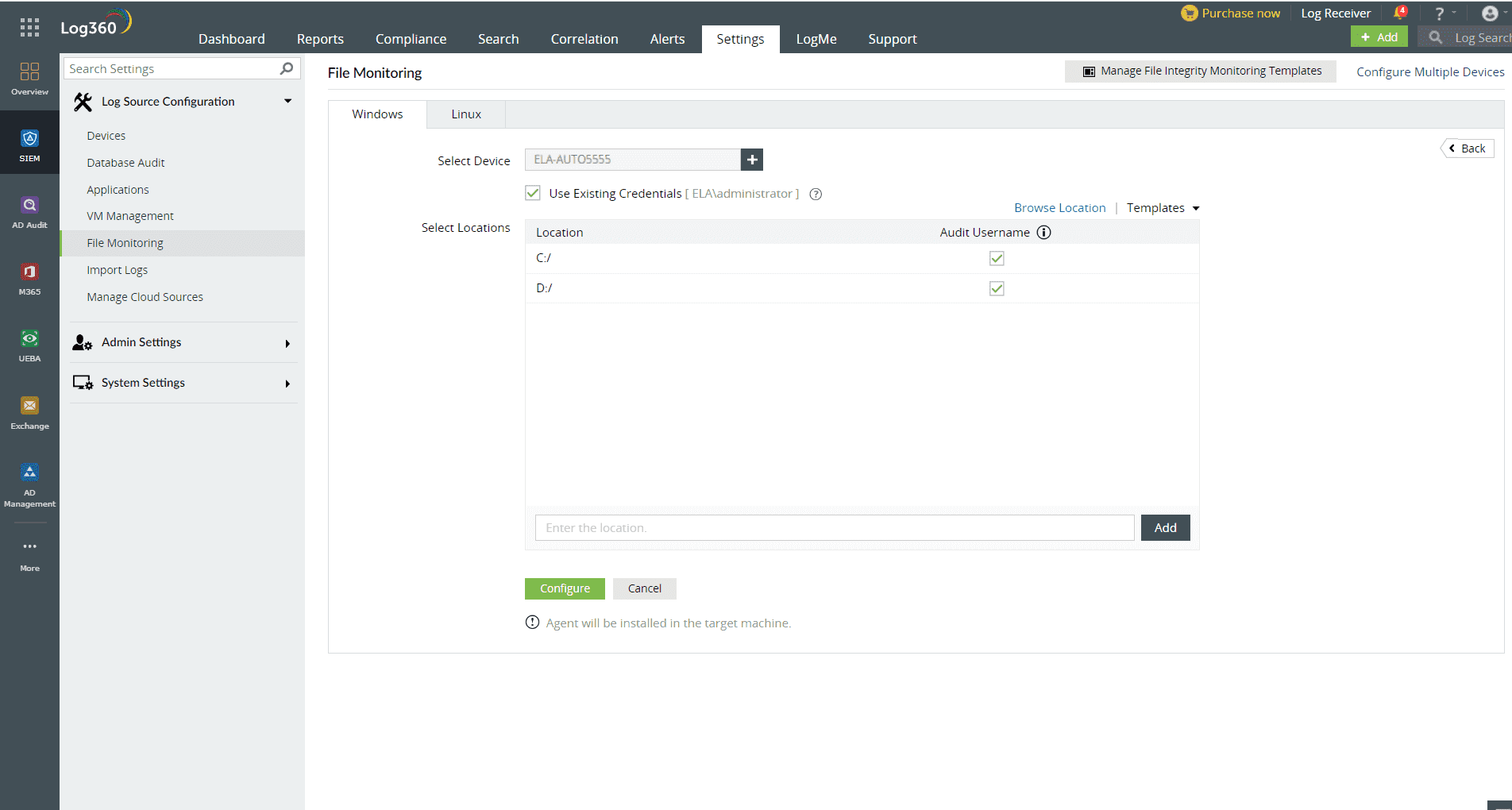
Figure 2: File monitoring configuration in Log360
4. APIs and integrations
Your FIM tool needs to work in unison and coexist with other security software in the cybersecurity ecosystem. A FIM tool should include built-in APIs and allow integrations to communicate with other security solutions. Integrations with solutions like security information and event management (SIEM); security orchestration, automation, and response (SOAR); and user and entity behavior analytics (UEBA) can provide a holistic approach to file-based threats by correlating and detecting anomalies, and offering automated responses.
Log360 combines the capabilities of SIEM, UEBA, and FIM to track unauthorized file/folder changes, audit file servers, monitor file activities in shared folders and audit user attempts to tamper critical files that contain sensitive information. It also detects insider threats aimed at data manipulation, data theft and data sabotage.
5. Agile policy management
FIM policies serve as fundamental frameworks that determine the assets to be monitored by your FIM software. They also specify the types of changes to be monitored based on asset type and criticality. Further, these policies need to align with the security demands of your network such that they enable you to identify unauthorized changes, who made them, when they were made, and from where the changes were made. This makes compatibility and agility key aspects of policy management in FIM. Your FIM tool should offer the following provisions:
- Policy customization to meet future requirements.
- Support for policy diversification based on asset type.
- Streamlined policy revisions and application across the network.
- Hassle-free policy management via a single console.
6. Trusted paradigms and baselines
Paradigms and baselines determine the integrity of files to create a digital fingerprint for each file and track all kinds of changes related to the file. Paradigms and baselines reflect expected file actions and file-related behavior in a network. A FIM software should be capable of optimizing the paradigms and baselines to generate true positive alerts that may otherwise lead to excessive noise of false positives and alert fatigue.
Therefore, it is imperative for a FIM solution to possess trusted paradigms and baselines so that you can gain true actionable insights for an alert and alleviate unnecessary noise. Log360 UEBA, with its advanced anomaly modeling capabilities, enables you to create anomaly models to detect file-related anomalies based on time, count, and pattern. It also involves peer group analysis and seasonality analysis to reduce false positives, thereby enhancing anomaly detection and alert generation.
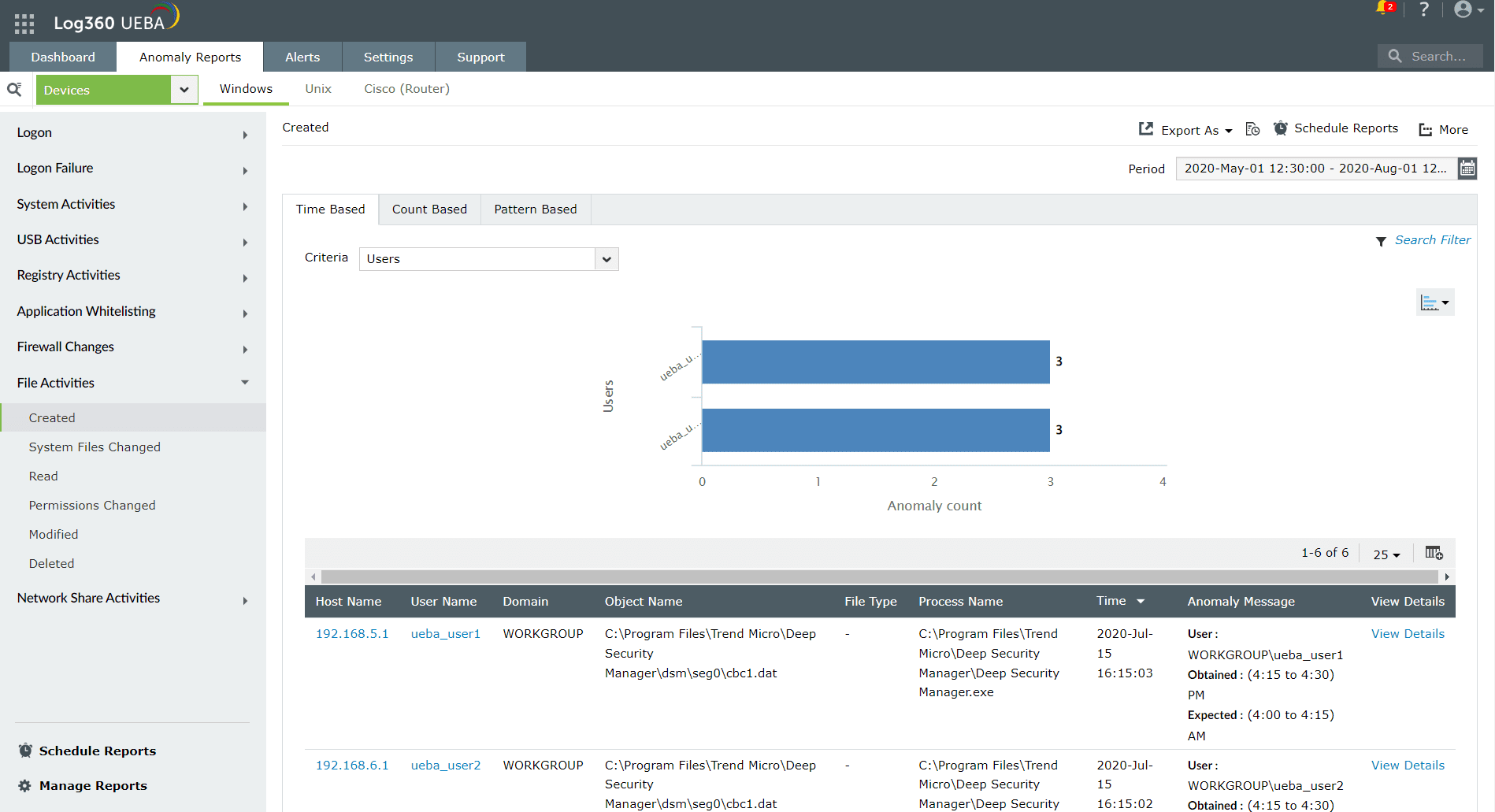
Figure 3: Anomaly report for file activities in Log360
7. Proactive monitoring and alerting
Proactive file monitoring and alerting is imperative to detect suspicious file activities in your network as and when they occur. The real-time alerting capability of proactive FIM is often accompanied by the generation of false positives. These false positives create unintended noise that distracts you from alert triaging and the identification of true positives, leading to alert fatigue.
A suitable FIM tool should auto-promote expected file activities and distinguish between anticipated and anomalous file changes. This can help validate the generated alerts and enhance alert triaging and proactive alerting in real time. Log360, with predefined correlation rules and alert profiles for file monitoring, can help you proactively detect potential file threats and mitigate malicious file activities.
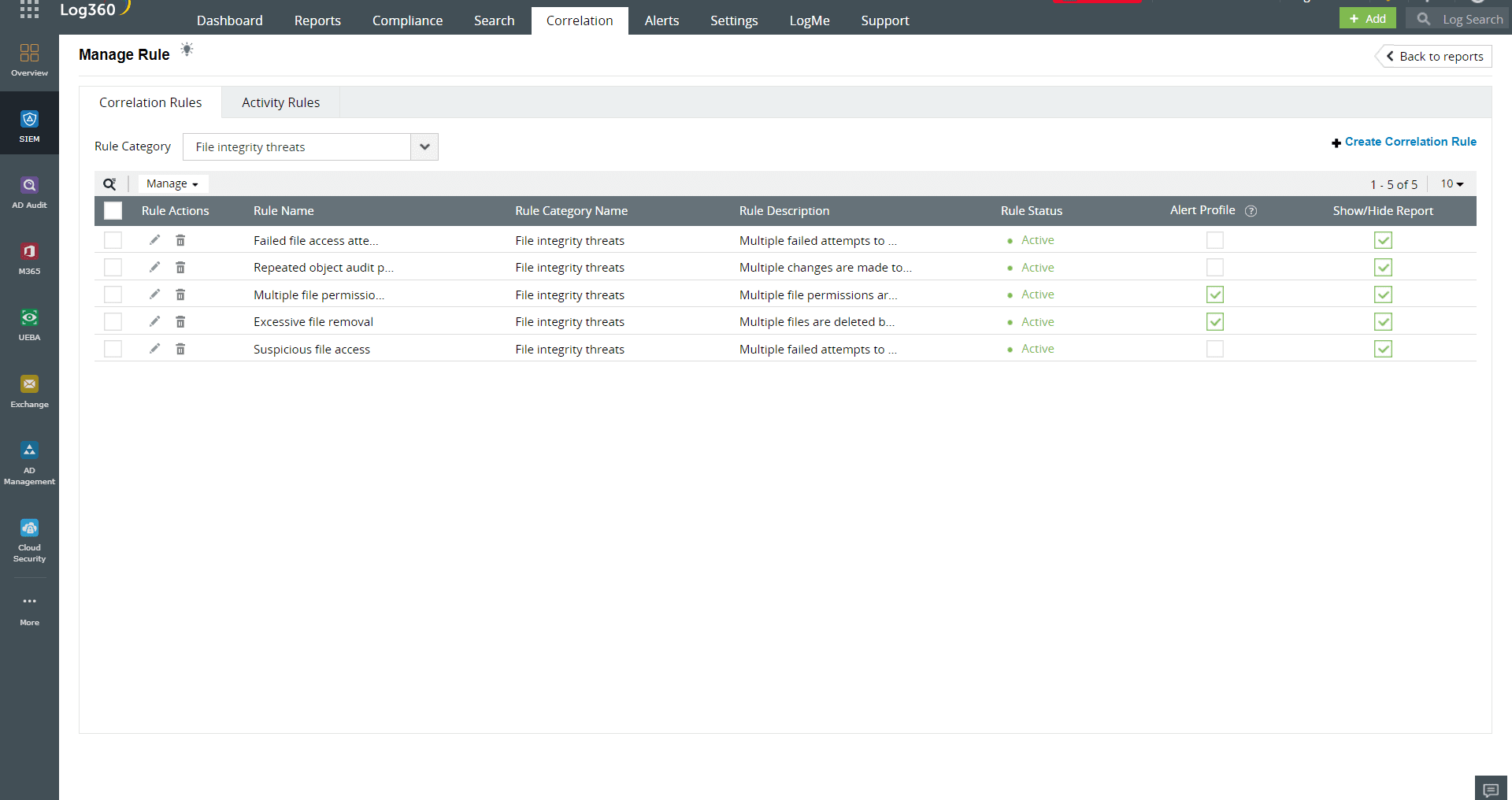
Figure 4: Correlation rules with alert profiles for file integrity threats in Log360
8. Audiy-ready reports
Reporting file-related changes is essential not only to monitor the integrity of critical files but also to adhere to regulatory mandates that promote data security. These mandates primarily focus on the confidentiality, integrity, and accessibility (CIA) of files. This makes real-time reporting essential for all types of file activities. A FIM tool is required to generate audit-ready reports onfile creation, modification, and deletion, file rename, file permission changes, and unauthorized file access attempts to read, write, copy and paste sensitive information.
A FIM software must track and record all types of changes to sensitive files and folders and generate audit-ready reports to adhere to some of the major mandates that regulate data security, like the PCI DSS, the NERC CIP, FISMA, SOX, NIST, and HIPAA. Log360 provides comprehensive audit reports on all file-related activities to help you prove adherence to the above mandates.
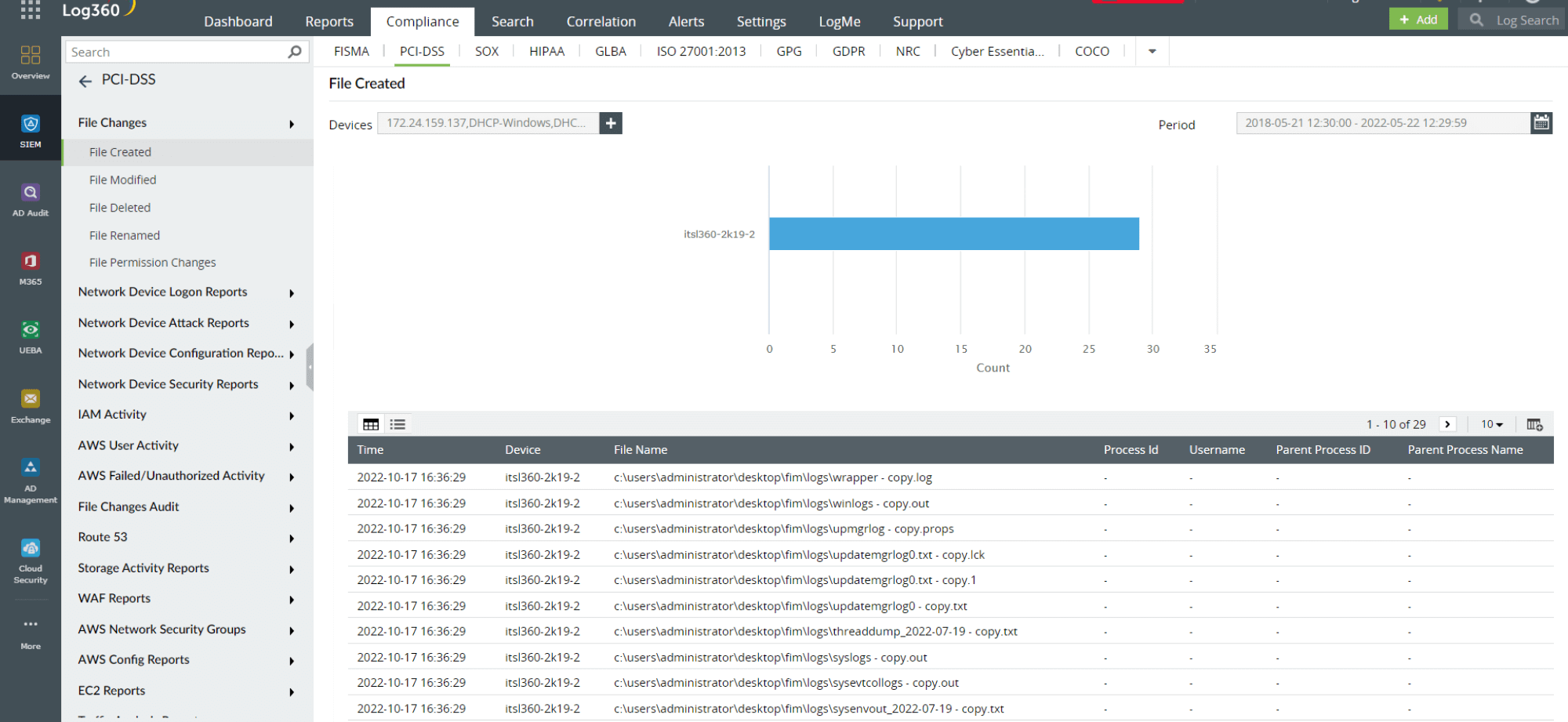
Figure 5: Audit-ready compliance reports for file changes in Log360
9. Enhanced user experience
FIM enhances the user experience, as it helps users understand the security posture and the security status of sensitive files in the network. A FIM tool that can provide a good user experience not only helps users derive actionable file integrity insights but also helps users analyze the trend of sensitive file changes.
Intuitive dashboards, interactive graphs, detailed reports, and audit summaries can simplify and amplify the implications of an FIM solution simultaneously. Figure 6 below showcases the top five file integrity monitoring events reported by Log360. Users can view the underlying events and logs by clicking on the graph.
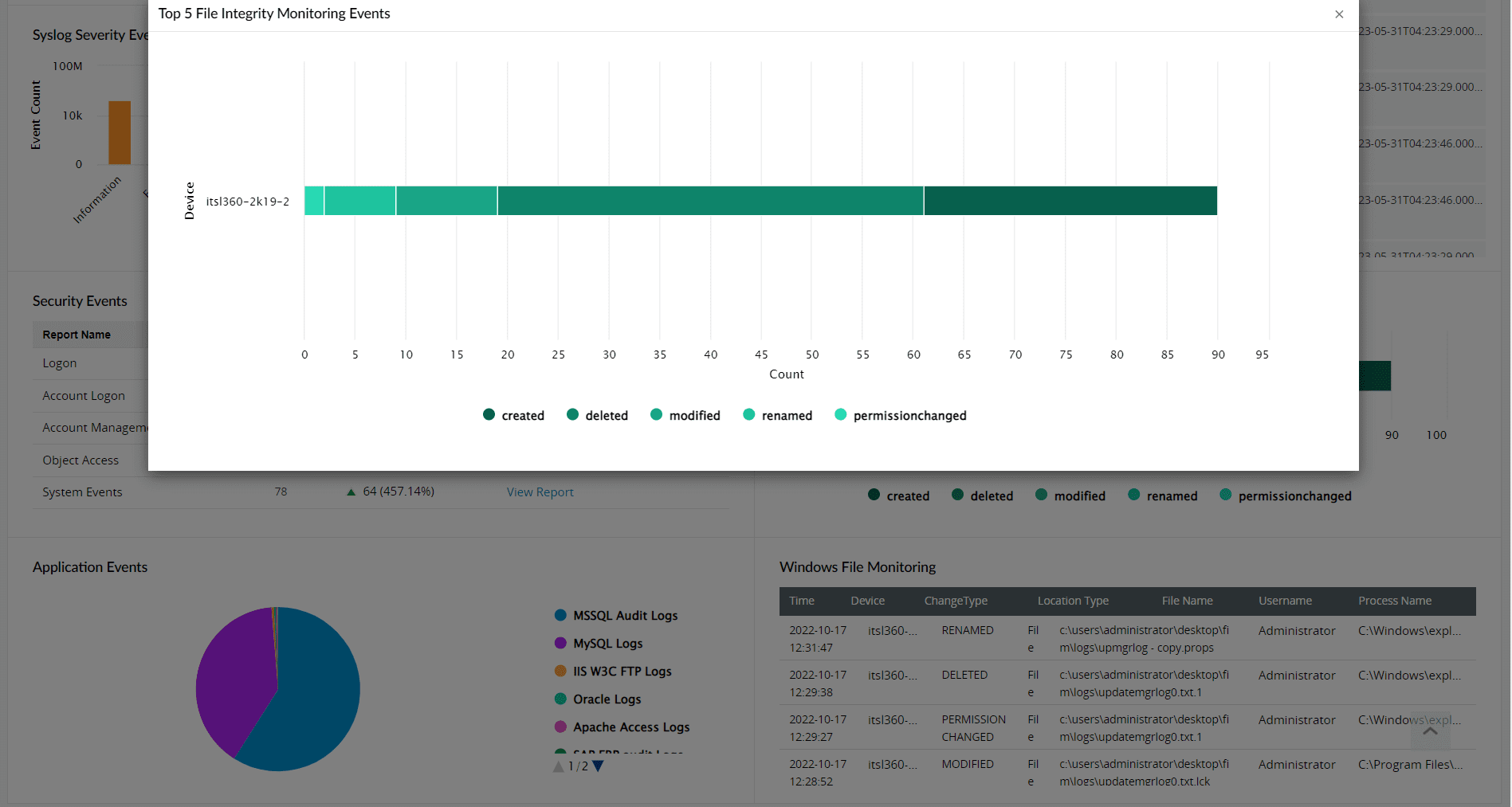
Figure 6: Top five file integrity monitoring events reported by Log360
10. Scalability
A FIM tool should be capable of scaling up to meet the growing data security needs of expanding networks. Log360 installs a lightweight agent for collecting file activity logs from different devices. The agent facilitates easy log collection across WANs and through firewalls in an expanding network. In an extensive network, it helps to establish network connection between Log360 and the FIM-configured device to collect log data. Moreover, the agent helps to balance the overhead load across a large network and promotes seamless functioning of FIM.
The above FIM capabilities are crucial for ensuring the safety and security of your sensitive files and folders and critical file servers. Log360 comes with all the essential FIM capabilities to ensure file integrity and data security in your network. Sign up for a personalized demo of Log360 to explore its features yourself.



