Ransomware attacks are taking a new turn with the emergence of Ransomware as a Service (RaaS) providers. LockBit is one such RaaS provider that has been in existence since 2019. Over the years, it has posed greater challenges to cybersecurity than other types of ransomware. Reports suggest that the group accounted for over one-third of all ransomware attacks in the second half of 2022 and the first quarter of 2023.
This blog will steer you through the evolution of LockBit ransomware and help you understand the significance of mapping LockBit attack stages to the MITRE ATT&CK framework. MITRE ATT&CK serves as a knowledge base for understanding an attack scenario from the adversary's point of view. Mapping LockBit attack stages to MITRE ATT&CK enhances your threat detection and incident response. It helps you get a fix on the attacker's line of action and counteract them beforehand to prevent major damage.
It is crucial to understand the attack scenario of LockBit before we map it to MITRE ATT&CK. This section will help you understand what happens behind the scenes of a LockBit attack.
LockBit ransomware is infamous for its regular upgrades, making it one of the most complex ransomware strains. Let's look back at how LockBit has evolved over the years.
LockBit actors are working around the clock to upgrade their variants through disruptive innovations, not only to sabotage enterprise security but also to beat other RaaS providers. Therefore, in one way or another, the technological advancements in ransomware strains along with the increasing competition among RaaS providers have caused organizations to succumb to the vulnerabilities of ransomware attacks. The MITRE ATT&CK framework, an enhanced knowledge base of adversarial tactics, techniques, and common knowledge, aids despairing organizations in combating such attacks.
In this section, we'll cover some of the most predominant techniques employed by LockBit ransomware, as reported by CISA. The LockBit attack tactics include initial access, execution, exfiltration, and impact, as shown in Figure 1.
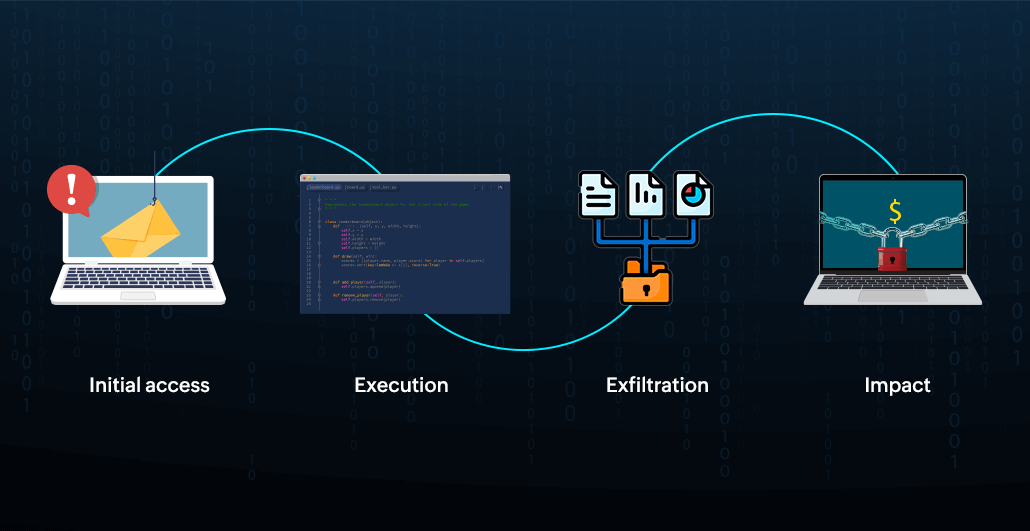 Figure 1: LockBit attack stages.
Figure 1: LockBit attack stages.
Initial access is the tactic pursued by adversaries to set foot into the network. LockBit actors use the following techniques to infiltrate a victim's network:
| Technique | Description |
|---|---|
| External remote services [T1133] | Attackers masquerading as valid users connect to the internal enterprise network from external-facing remote services using legitimate user credentials obtained through credential pharming. |
| Drive-by compromise [T1189] | Threat actors lure users to a compromised or malicious website where an automatic script execution occurs. |
| Phishing [T1566] | Attackers phish the victims using emails containing malicious links and attachments to execute malicious codes on their devices. |
Execution is the tactic pursued by attackers to run malicious scripts to infect a victim's compromised device. Here is a common technique used by LockBit actors during execution and infection:
| Technique | Description |
|---|---|
| Command and scripting interpreter [T1059] | Threat actors execute malicious scripts by exploiting command interpreters like Windows Command Shell, PowerShell, Unix shells, and AppleScript. |
Exfiltration is the tactic pursued by threat actors to steal sensitive data from a victim's network. The exfiltration techniques used by LockBit are shown below:
| Technique | Description |
|---|---|
| Automated exfiltration [T1020] | Adversaries use built-in data theft tools like StealBit, which automatically transfers data via a command-and-control channel and eases the process of data exfiltration. |
| Exfiltration over web service: Exfiltration to cloud storage [T1567.002] | Attackers exploit existing communications with cloud services like Google Docs to transmit data directly to cloud storage rather than using a command-and-control channel. |
Impact is the closing tactic pursued by adversaries to disrupt operations in a victim's network. The table below is comprised of techniques used by LockBit to impact a victim's network:
| Technique | Description |
|---|---|
| Data encrypted for impact [T1486] | Adversaries encrypt the exfiltrated data by modifying the user's directory and file permissions in order to demand a hefty ransom in exchange for the decryption key. |
| Defacement: Internal defacement [T1491.001] | Attackers display a ransom note including payment instructions on the user's internal websites and desktop wallpapers to intimidate and threaten them. |
| Service stop [T1489] | Adversaries inhibit critical services in systems to render them unusable and hinder processes that aid incident response in the victim's network. |
| Inhibit system recovery [T1490] | Adversaries eliminate OS features that enable the recovery of corrupted systems, like backup, shadow copies, and automatic repair, to complement data encryption. |
Apart from the above tactics and techniques, various other tactics, techniques, and procedures of MITRE ATT&CK can be mapped to the LockBit attack scenario depending on the adversaries' line of action. You can find more information about MITRE ATT&CK in our e-book.
Now, the question is: How can organizations thwart ransomware attacks like LockBit while mapping them to MITRE ATT&CK?
The answer is: They need a unified SIEM solution that provides exclusive, analytics-driven reports pertaining to the MITRE ATT&CK framework and that augments threat-informed defense with the detection of signature-based attacks. The following Figures depict the possible reports that can be generated by a SIEM solution to correspond with the various tactics pursued by LockBit actors.
Figure 2 presents an example report on the initial access tactic, which is the first stage of the attack.
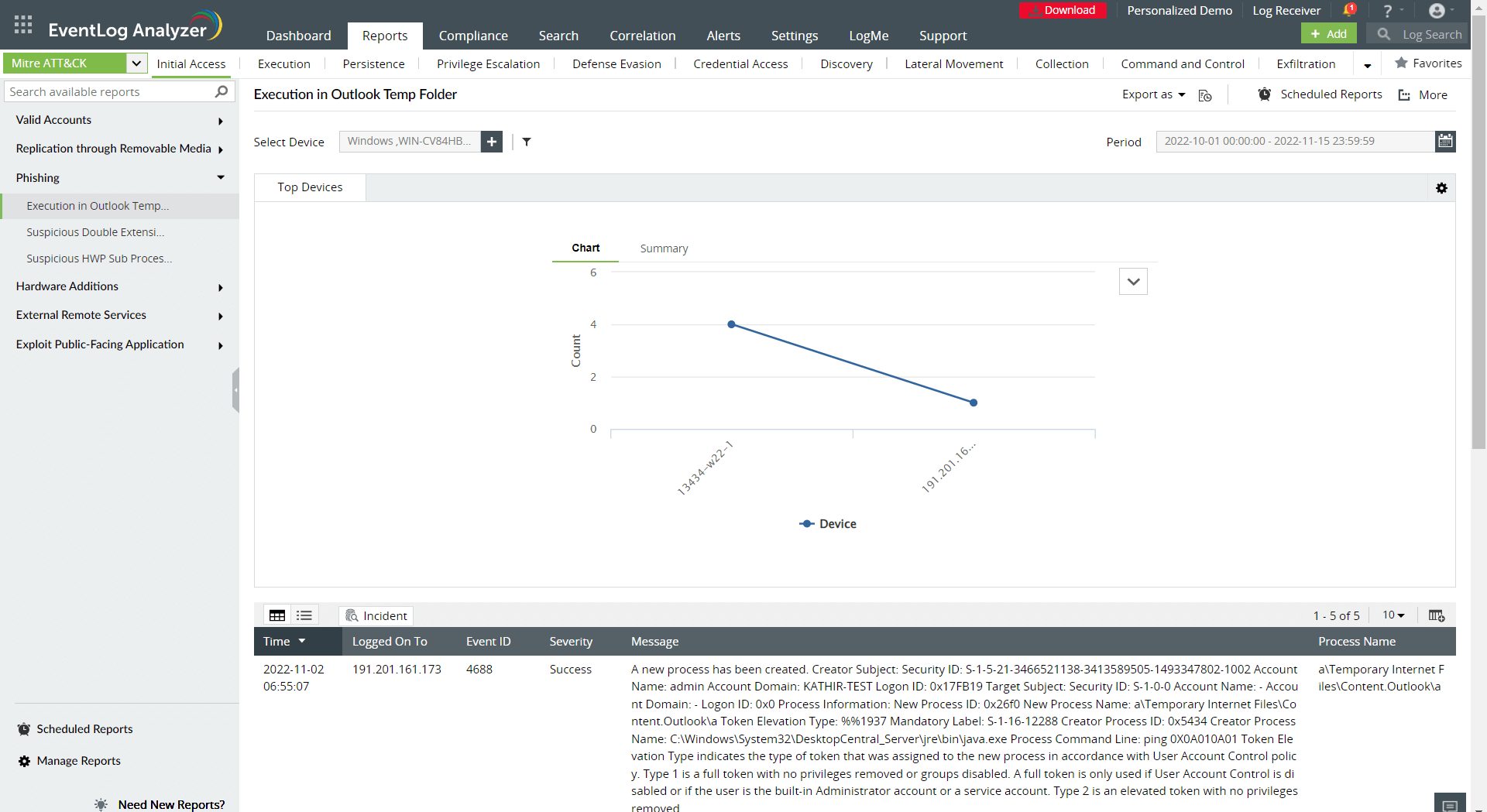 Figure 2: A MITRE ATT&CK initial access report.
Figure 2: A MITRE ATT&CK initial access report.
Figure 3 shows a possible report generated by a SIEM solution to track the execution tactic.
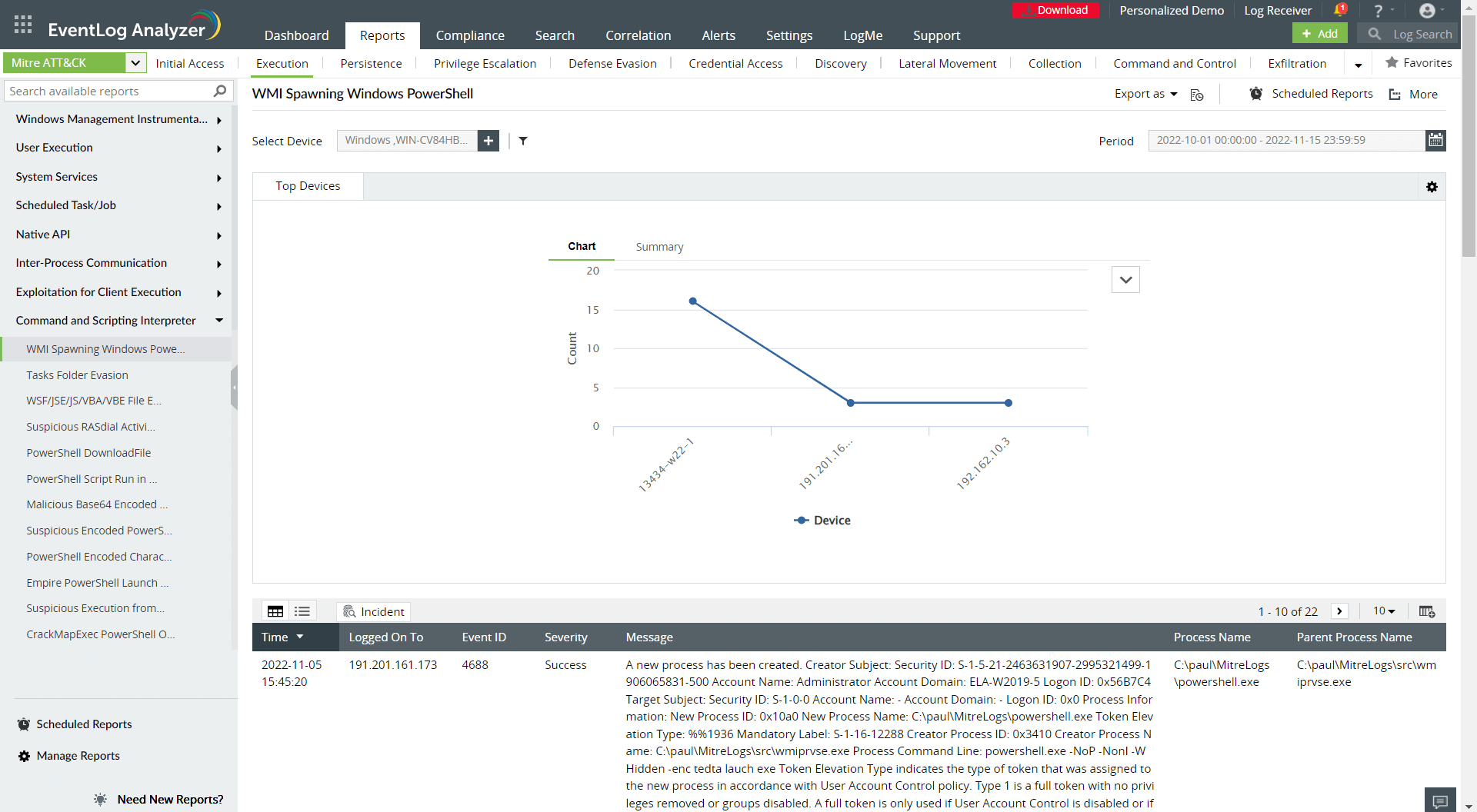 Figure 3: A MITRE ATT&CK execution report.
Figure 3: A MITRE ATT&CK execution report.
Figure 4 depicts an exfiltration tactic report provided by a SIEM solution.
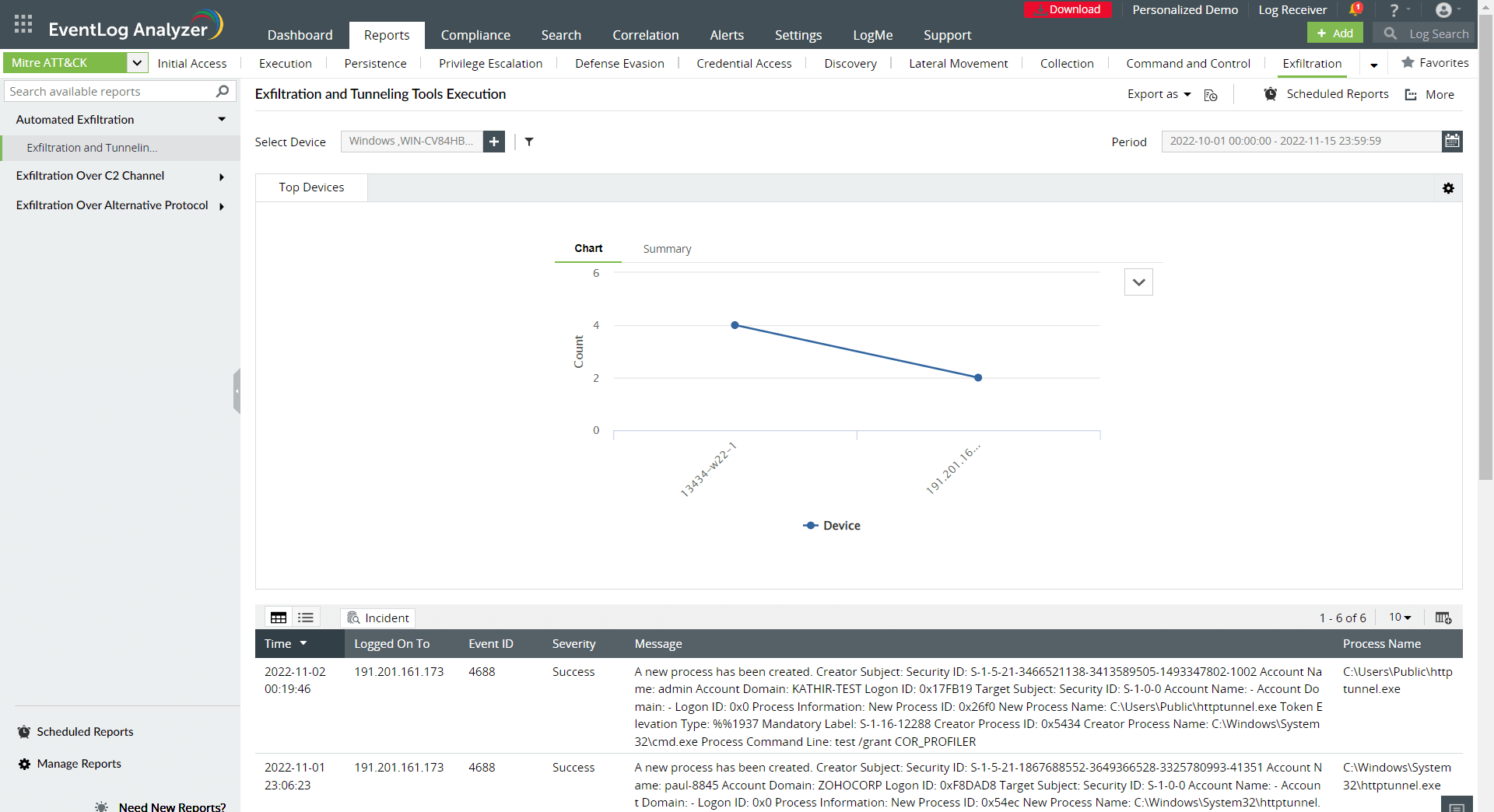 Figure 4: A MITRE ATT&CK exfiltration report.
Figure 4: A MITRE ATT&CK exfiltration report.
Figure 5 is an example report exhibiting the final tactic: impact.
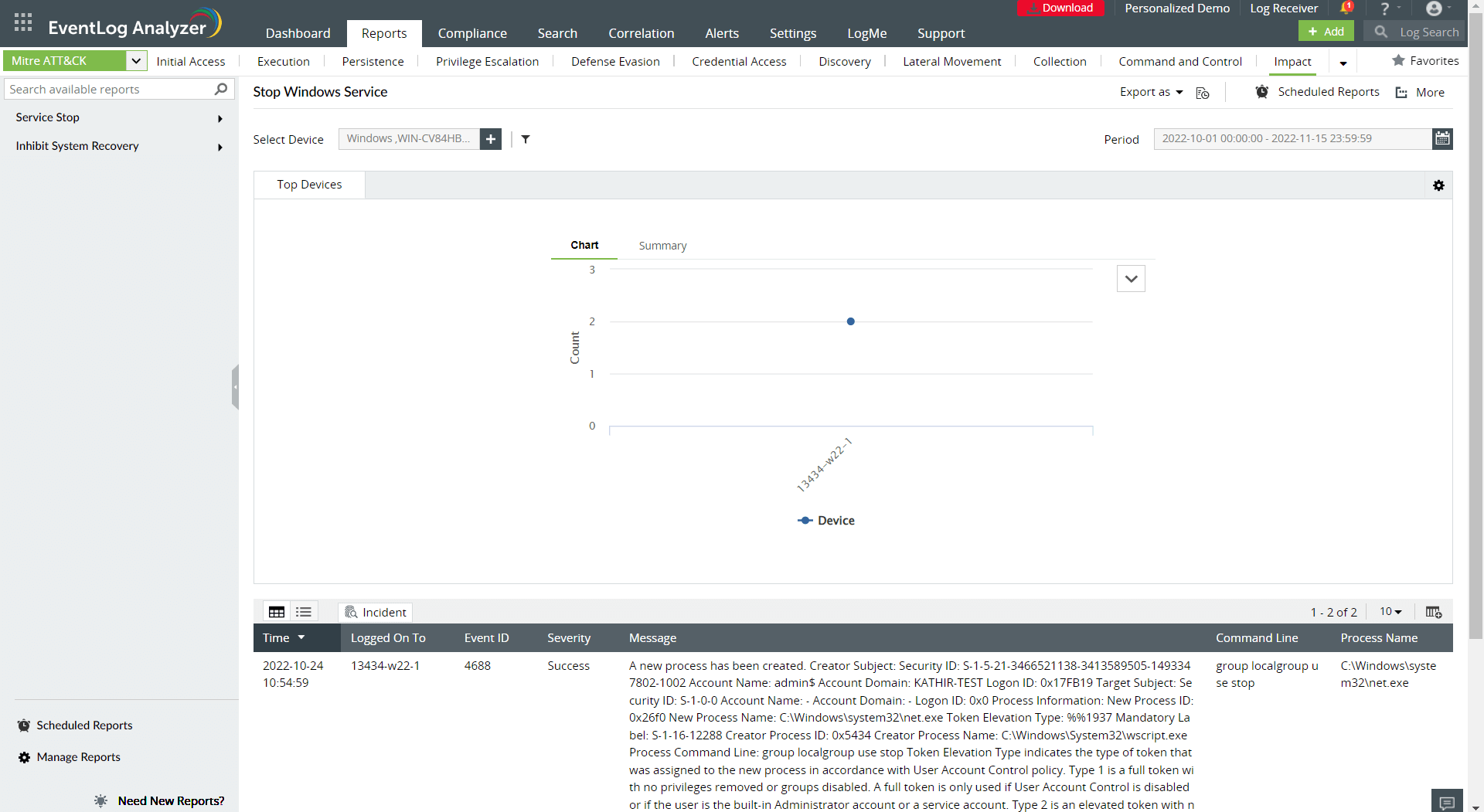 Figure 5: A MITRE ATT&CK impact report.
Figure 5: A MITRE ATT&CK impact report.
Would you like to secure your organization against ransomware such as LockBit? You may wish to sign up for a personalized demo of ManageEngine Log360, a comprehensive SIEM solution with data security and cloud security capabilities.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.