Malicious actors target healthcare organizations around the world for the vast amounts of sensitive patient information they contain. In the event of a global health crisis, when hospitals are on the front lines, they also become targets for crippling ransomware attacks. These incidents put a strain on the IT teams in healthcare that are already stretched thin in these unprecedented times.
How Log360 can help
Secure patient health information
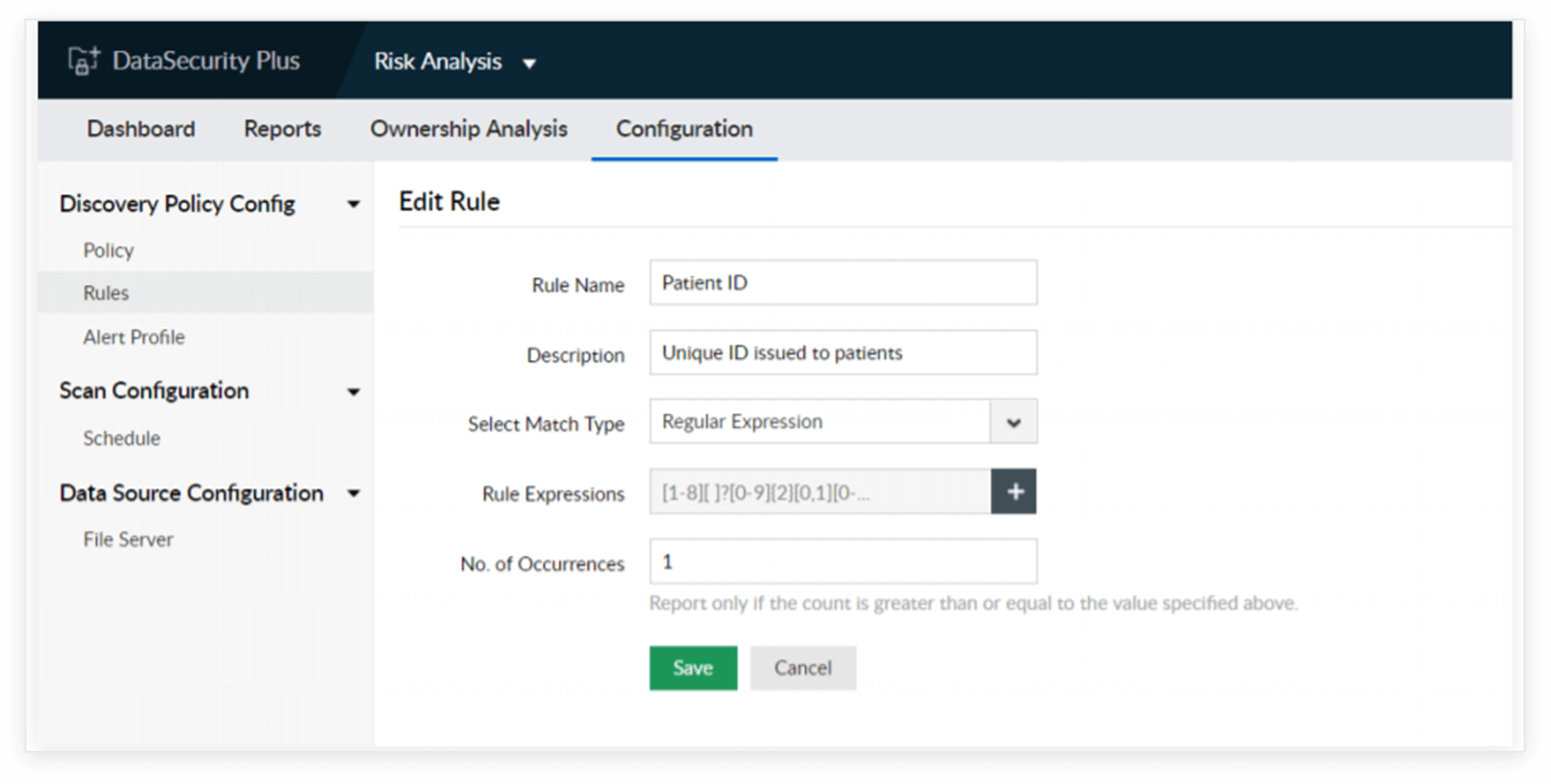
To secure sensitive health records, it's essential to discover all instances of this data across all devices in your network. If a user unwittingly downloads it in a workstation with lesser security controls, the security posture of the entire organization could be at risk. It's therefore crucial to discover all instances of sensitive data across every single device in your network and ensure that unnecessary copies are duly eliminated. Log360 can help you do this with its predefined rules to discover sensitive data like personally identifiable information. If the data you want to scan for isn't defined in the existing rules, you can set the required parameters and create your own rules. Based on this, Log360 will start looking for the information right away.
Comply with regulatory mandates like HIPAA
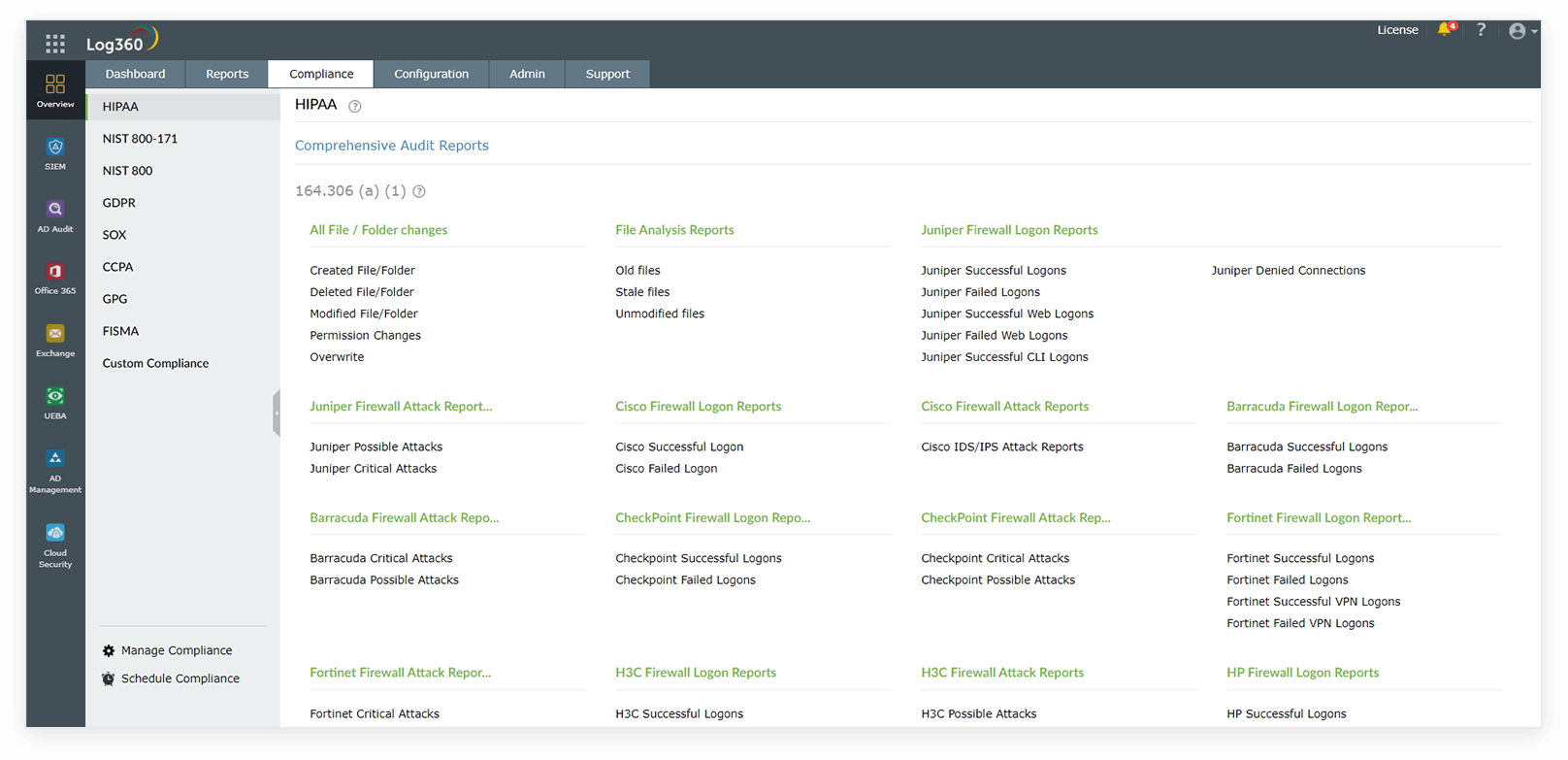
The Health Insurance Portability and Accountability Act (HIPAA) is a compliance regulation that states that every patient's health information should be protected from unauthorized access. To comply with this, all health care organizations need to establish systems and controls to ensure that this data is secured. Log360 helps IT admins comply with HIPAA by auditing access to critical data. If a compliance violation is detected, the security admin will be alerted immediately via email or SMS.
Detect insider threats and advanced persistent threats with machine learning
To preempt possible attacks by malicious actors inside the organization, Log360's user and entity behavior analytics (UEBA) add-on is equipped with machine learning algorithms that can detect anomalies in the behavior of all users and entities in a network. Any deviation from the baseline will be logged as an anomaly and a risk score will be added. Any user with a high risk score will be flagged by the system and placed on a watch list. Similarly, UEBA can help in detecting sophisticated malware or advanced persistent threats designed to evade detection. Once a threat actor infiltrates a network by taking over a compromised user account or system, it's bound to cause variations in the baseline behavior patterns. Even if all other safeguards fail, this module can help detect and mitigate a breach.
Stop ransomware attacks in time
Healthcare organizations are prime targets for ransomware attacks since the price of not having access to critical files is likely to be a patient's life. Malicious actors know and exploit this. With Log360, it's possible to detect some early signs of a ransomware infection, such as changes made to the Remote Desktop Protocol or unusual software installations. It also has an option to automate responses to these incidents, like shutting down a system or killing a process.
The benefits of using Log360 for the healthcare industry
Easily comply with regulations such as HIPAA
Leverage automated incident detection and response
Preempt insider threats with UEBA
Secure sensitive patient information