MITRE's ATT&CK® framework matrix has been invaluable to security teams because of the way it comprehensively covers attack styles, detection methods, and mitigation measures. MITRE has also been quite proactive in updating the matrix with new threats, ensuring that the cybersecurity community is well aware of any known threat that an organization can be vulnerable to.
Now MITRE has gone further and developed the MITRE D3FEND framework with the aid of the NSA. This framework dives deep into cybersecurity countermeasure techniques that organizations can adopt. These countermeasure techniques involve strategies that a SOC team can use to model digital systems; harden access to computer networks; and detect, isolate, deceive, and evict a hacker carrying out a malicious attack strategy on the network.
The model tactic is primarily concerned with the discovery and mapping of assets in the network, whereas the other tactics are more concerned with defending the network against potential attacks. So, in this blog, we will take a closer look at the harden, detect, isolate, deceive, and evict tactics that constitute the five defensive goals of the D3FEND graph.
D3FEND stands for Detection, Denial, and Disruption Framework Empowering Network Defense. D3FEND is a graph that shows how each ATT&CK technique is executed based on which digital artifacts the attackers interact with. This produces a map that depicts countermeasures for these attack scenarios. Figure 1 shows a schematic of how ATT&CK and D3FEND techniques are correlated.
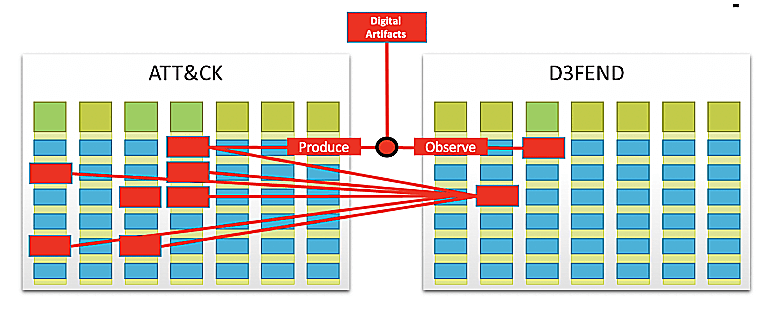 Figure 1. Correlative mapping between ATT&CK and D3FEND.
Figure 1. Correlative mapping between ATT&CK and D3FEND.
In the schematic above:
Let's look at the D3FEND graph more closely. Like MITRE's ATT&CK enterprise framework, the D3FEND graph also sports a tactic-and-technique-style matrix where the tactics include the following five defensive goals:
Each of these defensive tactics consists of specific defensive techniques.
Harden: This tactic is comprised of application, credential, message, and platform hardening techniques. These teach SOC teams how to handle attack surface management, vulnerability management, and access management through authentication. The tactic deals with provisioning access to computer networks. The techniques suggested encompass most of the security protocols that compliance mandates require for access restrictions.
Detect: With the D3FEND knowledge graph at hand, SOC teams everywhere are presented with a major use case. The D3FEND matrix helps SOC teams improve their detection engineering and threat modeling capabilities. SOC teams can analyze their detection requirements by answering the following questions:
The detect tactic relies on analyzing threats and correlating attack techniques from the ATT&CK framework. The technique categories listed for this tactic are as follows:
From the countermeasures listed, you'll see that the detection solutions the D3FEND framework is pushing for are SIEM solutions and other similar tools like extended detection and response (XDR) services or managed detection and response (MDR) services. A SIEM solution collects and processes security information to detect potential threats and protect the network. A robust SIEM solution like ManageEngine Log360, which provides predefined and custom correlation rules and anomaly detection capabilities, can help with user behavior analysis, file analysis, and message analysis.
Isolate: This tactic consists of execution isolation and network isolation techniques that involve disconnecting compromised hosts from the network. By involving IP and DNS filtering, the SOC team can create physical and logical barriers in the network, which prevent the threat actor from probing further.
Deceive: This tactic encompasses decoy environment and decoy object techniques. It focuses on creating a honeypot of the environment with decoys of the files, network resources, user profiles, credentials, and more. This points the attacker away from critical resources to a highly monitored environment where the SOC team can analyze the attacker's behavior to understand what sort of damage the attacker wants to inflict on the network. This is a good way of countering the discovery tactic outlined in the ATT&CK framework.
Evict: The evict tactic involves credential, file, and process eviction techniques. These are used to eliminate compromised credentials and files from the network and to terminate undesired processes running in the network.
Figure 2 shows how the ATT&CK techniques and D3FEND techniques are mapped to each other so that a blue team knows which countermeasures to carry out based on the type of attack and the defense goals the team wants to accomplish. Steganography is a technique detailed in the ATT&CK framework. The digital artifact this technique produces is outbound internet network traffic. The D3FEND matrix shows several detect techniques that a blue team can use by analyzing the outbound internet network traffic.
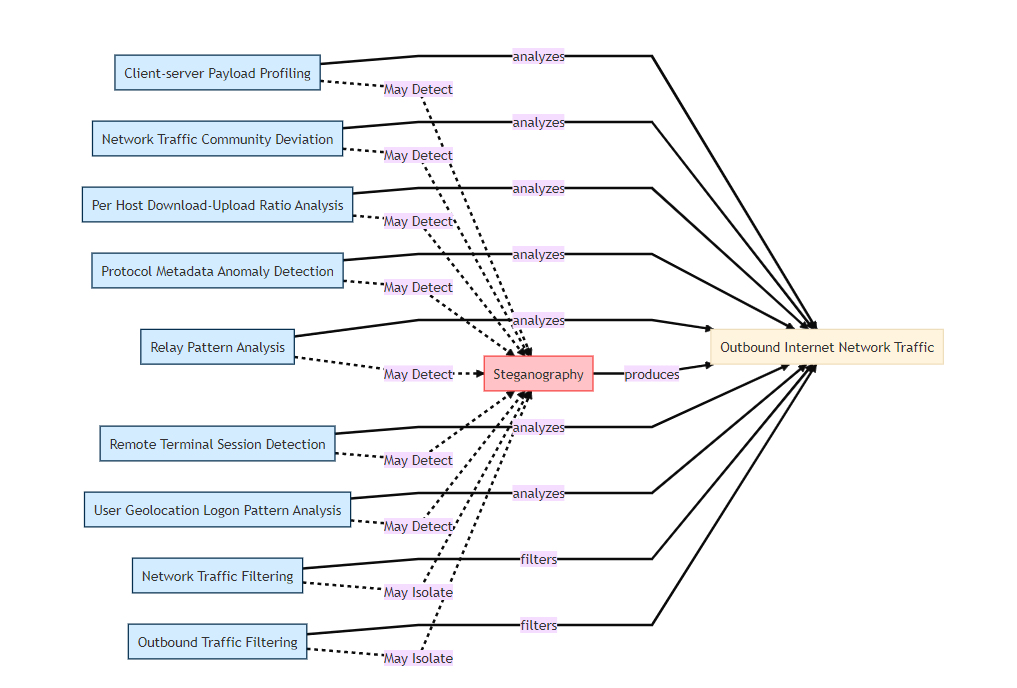 Figure 2. Countermeasure technique mapping between ATT&CK and D3FEND, displaying detect techniques.
Figure 2. Countermeasure technique mapping between ATT&CK and D3FEND, displaying detect techniques.
Figure 3 shows filtering techniques (found under the isolate tactic) that isolate the malicious traffic (the digital artifact) to prevent the attack from spreading further.
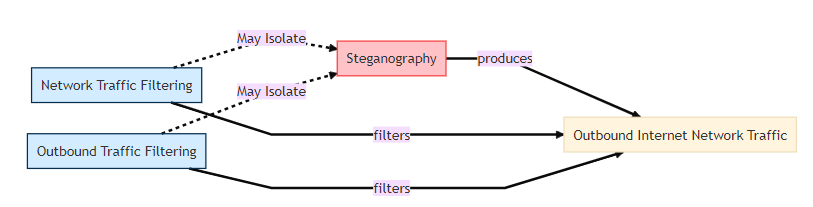 Figure 3. Countermeasure technique mapping between ATT&CK and D3FEND, displaying isolate techniques.
Figure 3. Countermeasure technique mapping between ATT&CK and D3FEND, displaying isolate techniques.
Another beneficial by-product of the D3FEND matrix is improved semantics. Countermeasures and security technologies have been difficult to understand due to the vendor-specific vocabulary that exists. The D3FEND model has been thoroughly researched, taking all existing security nomenclature into account to create more vendor-agnostic security terminologies that help security practitioners understand exactly what security capabilities vendors are offering.
Although still in its beta phase, the D3FEND graph, like ATT&CK, is being developed to accommodate frequent updates to the countermeasures listed. The overall goal of the graph, as stated by its creators, is to allow blue team practitioners to evaluate their security strategies, implement more effective defense measures, and make more informed decisions when choosing security solutions.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.