Ransomware remains one of the most devastating forms of cyberattack. In June 2021, the average weekly ransomware activity was 10.7 times higher than the previous year. The average ransomware payment in 2021 was $570,000, almost double the amount paid the previous year. NotPetya, a ransomware variant, was one of the most powerful malware unleashed in the last decade, causing catastrophic damage around the world.
NotPetya took the cybersecurity world by storm. Kaspersky named this ransomware as NotPetya due to its similarities to Petya, a family of encrypting malware first discovered in 2016. Unlike other ransomware targeting personal files like photos and documents, Petya ransomware locks up the entire hard drive, preventing the computer from booting up. Petya spreads through e-mails with malicious attachments, which when downloaded, release the malware onto the victim's device. The keys for encryption for Petya and NotPetya are different, and each has unique reboot styles, displays, and notes. However, both have been equally destructive.
According to WIRED, the NotPetya ransomware first appeared in Ukraine, on the afternoon of June 27, 2017, a few hours before the celebration of Ukraine's Constitution Day. It is possible that the attack was planned around this time because most IT employees wouldn't have been working due to the national holiday. Most of the infected machines were reported from Ukraine, which confirms the idea that Ukraine was the main target of the attack. Even though attacks were detected in 64 other countries, including the United States and European countries, they only appear to be collateral damage.
According to the Ukrainian police, this ransomware spread through M.E.Doc, a popular accounting software in Ukraine. Cisco Talos reported that attackers created a backdoor inside M.E.Doc disguised as a software update. Unlike older variations in the Petya family, the malicious code of this ransomware did not just encrypt important files, it encrypted the whole system. By infecting the master boot record (MBR), a sector of the hard drive that's essential for locating operating systems and files, the entire system was rendered unusable.
NotPetya exploited the EternalBlue vulnerability in the Windows operating system, the same used by the Wannacry ransomware. Additionally, it took advantage of other vulnerabilities in the Windows operating system such as PsExec, Windows Management Instrumentation (WMI), and EternalRomance. As a result, NotPetya gained administrator rights and propagated to other computers on the same network, leaving patched computers compromised too.
When a computer was under attack by NotPetya, a threatening message appeared on the screen. The message said that all the files on the device were encrypted and demanded $300 in bitcoin as ransom. It also claimed that upon paying the ransom, a decryption key would be given. However, the promise of a decryption key was just a hoax—leading many experts to believe NotPetya was actually a disguised wiper.
Here's an image of the message:
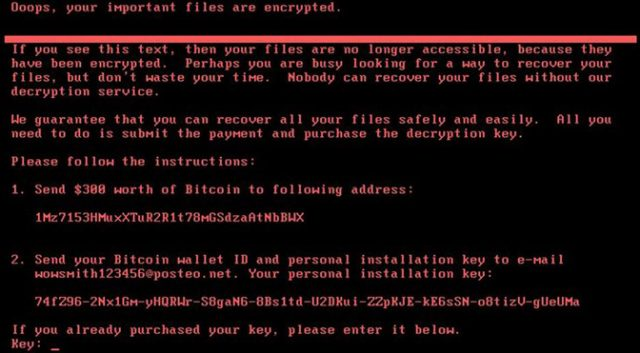
Image source: Google
Maersk, a Danish shipping company located in Copenhagen, was one of the major victims of this attack. Maersk had installed M.E.Doc on just one of its computers, and that was enough for the malware to spread throughout the network. Out of Maersk's 76 terminals, 17 were shut down. It took Maersk two weeks to bounce back after suffering the attack and a loss of over USD 300 million in revenue.
Mondelēz, Merck, WPP, Reckitt Benckiser, Saint-Gobain, and TNT Express are some of the other major companies affected by the NotPetya ransomware. Although Ukraine was the main target, it spread for five days, infecting computers in the US, Europe, and Asia, compromising more than 200,000 computers worldwide. The estimated damage of the whole attack is more than USD 10 billion.
“It was the equivalent of using a nuclear bomb to achieve a small tactical victory,” said Tom Bossert, the homeland security advisor at the time.
Keeping systems up to date is one of the most basic proactive measures organizations can take to prevent or minimize damage caused by modern cyberattacks. It's also important to have strong reactive security strategies in place.
A security information and event management (SIEM) solution will help organizations recognize potential security threats and vulnerabilities before they have a chance to disrupt business operations. Log360 is a unified SIEM solution with integrated DLP and CASB capabilities that detects, prioritizes, investigates, and responds to security threats. It provides holistic security visibility across on-premises, cloud, and hybrid networks with its intuitive and advanced security analytics and monitoring capabilities.
Schedule a personalized demo with our product experts to learn more about Log360.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.