As explored in Part 1, phishing is a social engineering attack in which attackers prey on human error and the vulnerability of users and systems in order to obtain sensitive information. There are several types of phishing attacks, each of which involves specific attack vectors and methodologies.
With the evolution of each type, the number of phishing attacks has increased. According to the FBI's Internet Crime Report 2021, phishing attacks have increased the most out of the top five cybercrimes in the United States over the past five years. The number has increased from 25,344 attacks in 2017 to 323,972 attacks in 2021.
The cyberwar between Russia and Ukraine triggered several phishing email scams where criminals collected data and cryptocurrency while claiming to gather funds for Ukraine. The United Kingdom's national cybercrime reporting center, Action Fraud, received over 196 reports of phishing emails asking people to donate to the welfare of Ukrainian citizens.
Social media has also been increasingly used for phishing attempts of late, with LinkedIn becoming a popular choice for cybercriminals. The attacker can either send a fake notification email with a link claiming to lead to a LinkedIn page or lure users using fake job offers that redirect them to forms that collect their personal information, like bank details.
A recent PSA put out by the FBI points to an increase in business email compromise (BEC) attacks where scamsters reach out to businesses or individuals and convince them to carry out funds transfers or to provide PII and financial documents. Or, in the case of cryptocurrency wallets, scammers ask for the secret phrase that can be used to hack into the wallets. According to the announcement, there has been a 65% increase in global exposed losses (both potential and actual losses) due to BEC attacks.
Like the advancement of the Ransomware as a Service (RaaS) model, PhaaS has evolved into a thriving business model on the dark web. Attackers can create fake pages and leverage them to carry out phishing operations online. A recent PhaaS discovery was the application Frappo, which helps cybercriminals create and use premium phishing pages called phishlets to collect victims' information, like their IP addresses, login credentials, and user-agents.
Frappo is completely anonymous and uses a Docker container and an API to collect credentials. Threat actors don't even have to register or create an account. Once the application is configured, data about page visits, authorization, and uptime is automatically collected and visualized. Originally designed to be a cryptocurrency wallet, Frappo now facilitates the large-scale development of phishing kits.
PhaaS businesses like Frappo offer two kinds of purchase models. One model is a one-time purchase of an item called a phishing kit. Phishing kits are usually packaged ZIP files and are of two types: simple and advanced. Simple kits contain an HTML page with a form to collect victims' data as well as the required content (images, text, and multimedia) that would help it ape popular websites like Facebook. More advanced kits include features like geoblocking and antidetection elements to evade antiphishing bots and search engines.
The other purchase model customers can go for is a subscription-based model where a PhaaS operation takes care of the entire phishing campaign, or a large part of it, for the customer. This includes services like providing and deploying HTML pages and scripts (as present in phishing kits), hosting the website, and parsing and redistributing credentials.
A notorious addition to organized cybercrime, PhaaS is much like the RaaS model (previously discussed here). The first noticeable PhaaS operation was BulletProofLink, discovered by Microsoft in 2020. Many aspects of the operation, be it the services it offered, its business model, or its double extortion method, had similarities to RaaS.
ATT&CK (which stands for adversarial tactics, techniques, and common knowledge) was created in 2013 by MITRE, an American not-for-profit research organization. Designed to gauge adversary behavior in the post-compromise stages of an attack, it is a matrix consisting of various tactics and techniques.
The image below shows a list of possible enterprise tactics and the phishing techniques and sub-techniques that can be used to carry out the tactics.
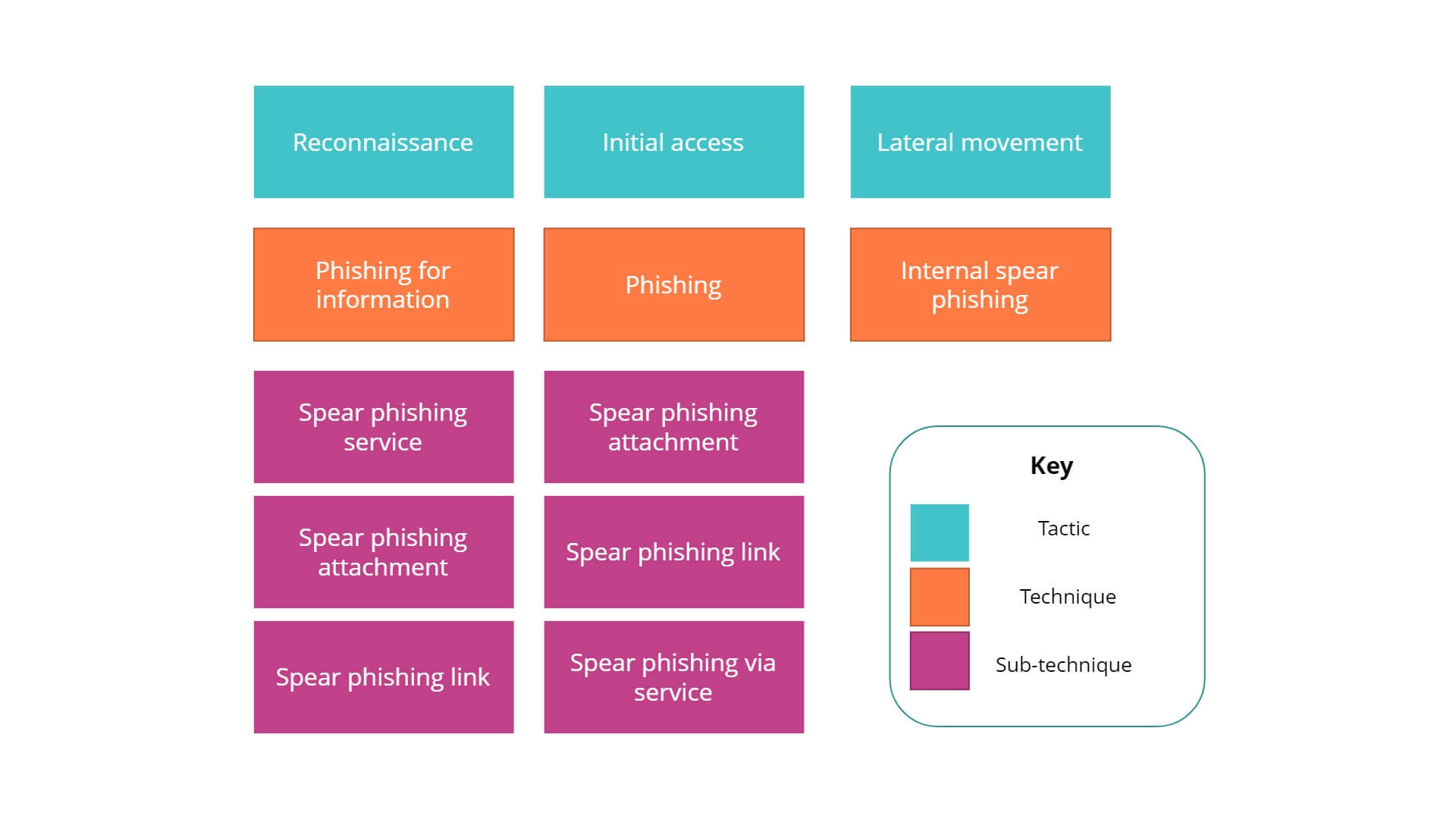
As mentioned above, we will try to understand the intentions behind the techniques used by phishers through the MITRE ATT&CK matrix. Listed below are descriptions of the tactics, the phishing techniques used to carry them out, corresponding sub-techniques, and recommended detection strategies.
Tactic: Reconnaissance
Technique: Phishing for information
Sub-techniques: Spear phishing service, attachment, and link
Reconnaissance is the stage during which adversaries gather intelligence and conduct research into a target organization before initiating an attack. According to the MITRE ATT&CK framework, an adversary can use phishing for information and three of its sub-techniques to collect enterprise information during the reconnaissance stage. Here, the differentiation between phishing for information and phishing itself is that the specific objective of this attack is obtaining the victim’s information, not gaining access. The attack is carried out using spear phishing, either via third-party services or via emails that contain a malicious attachment or link.
Tactic: Initial access
Technique: Phishing
Sub-techniques: Spear phishing attachment, link, and service
This is when the adversary tries to enter the enterprise network and uses techniques like phishing to gain initial entry. As in the reconnaissance stage, phishing can be carried out using sub-techniques like spear phishing via emails with attachments or links and spear phishing via third-party services.
Tactic: Lateral movement
Technique: Internal spear phishing
Here, the adversaries are already in the network, exploring it further to find vulnerable systems to exploit. The primary aim is to gain control over these vulnerable systems and use them to carry out malicious activities like escalation of privileges or credential dumping. This can be done using internal spear phishing, which involves attackers using an already compromised user's email account or credentials to send targeted spear phishing emails to other users in the network with malicious links or attachments.
MITRE ATT&CK recommends the following detection strategies for the phishing techniques and sub-techniques for the three mentioned tactics (reconnaissance, initial access, and lateral movement).
Like we've seen so far, social engineering attacks like phishing require continuous monitoring of network traffic and processes to ensure early threat detection and swift incident response. As recommended by the MITRE ATT&CK framework, it is necessary to deploy a security solution that collects and analyzes application logs, regularly monitors network activity, and sends immediate SMS and email alerts in case of critical security incidents.
Here's how organizations can use Log360, our SIEM solution, to detect suspicious activity that could lead to phishing attacks:
To learn more about how Log360 can help you detect and prevent phishing attacks, request a free demo with our product experts.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.