What is WinPEAS?
WinPEAS, also known as Windows privilege escalation awesome scripts, is an open source tool created by CarlosPolop. It is used to search for all possible paths to escalate privileges on Windows hosts and uses a color-coded system that shows which areas require attention. The color-coded output makes it easier for the administrators to detect something.
The color scheme includes red for special privilege detection, green for the presence of enabled protection or defenses, cyan to indicate active users, blue for disabled users, and yellow to highlight links. Other colors are utilized, each serving a distinct purpose in conveying information.
With the help of WinPEAS script, system administrators, penetration testers, or security researchers can identify security misconfigurations, vulnerabilities, weak points in a Windows environment, scheduled tasks, and much else.
How can WinPEAS be used for privilege escalation?
To execute the WinPEAS for privilege escalation, follow these steps.
1. Download WinPEAS script
Obtain the latest version of WinPEAS from the official a GitHub repository.
2. Transfer WinPEAS to the target machine
Transfer the WinPEAS script to the target Windows machine. You can use various methods such as copying it through a shared network folder, using a USB drive, or any other means of file transfer.
3. Execute WinPEAS
Run WinPEAS on the target machine. Open Command Prompt or PowerShell and execute the script as shown below:
.\winPEAS.exe or winpeas.exe cmd > output.txt
Allow WinPEAS to execute and complete its scan. This may take a few minutes. With the help of this script, we can detect the following configurations:
Basic system information
- Hostname
- OS version and architecture
User and Group information
- Active users (highlighted in cyan)
- Disabled users (highlighted in blue)
File and directory permissions
- Writable directories
- Insecure directories
Service information
- Running services and their permissions
- Unquoted service paths
Scheduled tasks
- Information about scheduled tasks
- Misconfigured scheduled tasks
Registry information
- Insecure registry entries
- Autostart registry keys
DLL hijacking opportunities
- Information about potential DLL hijacking opportunities
Firewall and antivirus status
- Status of Windows Firewall
- Information about installed antivirus software
Active network connections
- Details about active network connections
4. Assess post-deployment
Once WinPEAS completes its scan, it generates a comprehensive output highlighting potential privilege escalation opportunities. Administrators need to focus on sections related to file permissions, services, scheduled tasks, registry entries, and other security-relevant information.
How can attackers use this tool for their advantage?
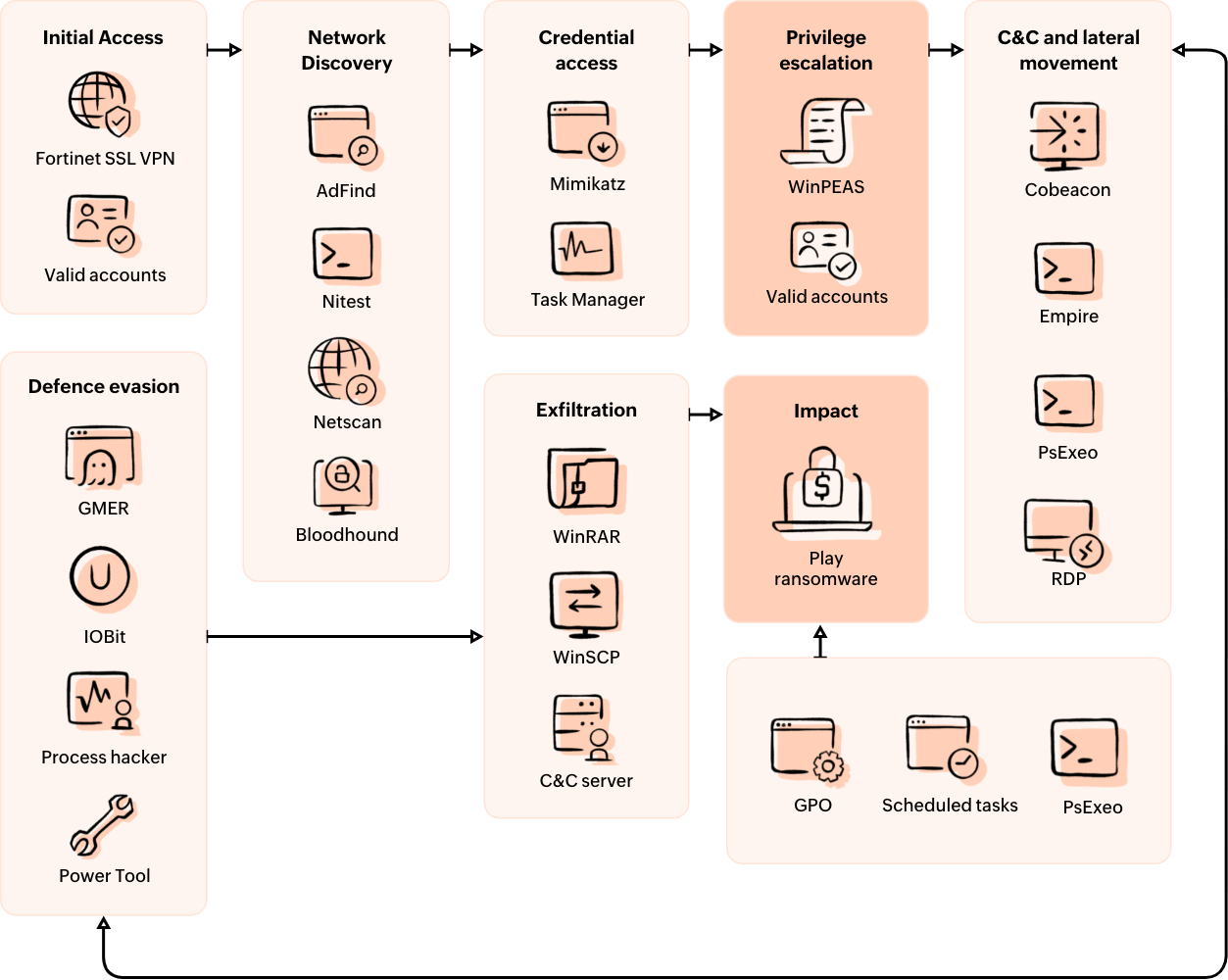
Though this tool is used by security professionals to check for any vulnerabilities and address security vulnerabilities, attackers could misuse it to find weaknesses in a Windows system for unauthorized privilege escalation or system compromise. Let's take Play ransomware as an example to understand how WinPEAS was used in the extortion ransomware attack.
Play ransomware
Play ransomware, also known as PlayCrypt, emerged in late June 2022, targeting organizations across Latin America, Europe, and the United States. To gain initial access, the group exploits known vulnerabilities in public-facing assets and compromises legitimate accounts. For reconnaissance, evasion of defenses, and establishing persistence within the victim's network, the ransomware actors utilize a mix of custom and publicly available tools, such as BloodHound, Cobalt Strike, GMER, Mimikatz, and WinPEAS.
How does Play ransomware use WinPEAS for privilege escalation?
By using Mimikatz, Play ransomware retrieves high privilege credentials that are stored in the memory. With the help of this information, it then elevates the privileges of certain accounts, like adding them to privileged groups such as Domain Administrators. It then utilizes WinPEAS to identify possible ways to escalate privileges locally.
How does Log360 help in detecting WinPEAS script?
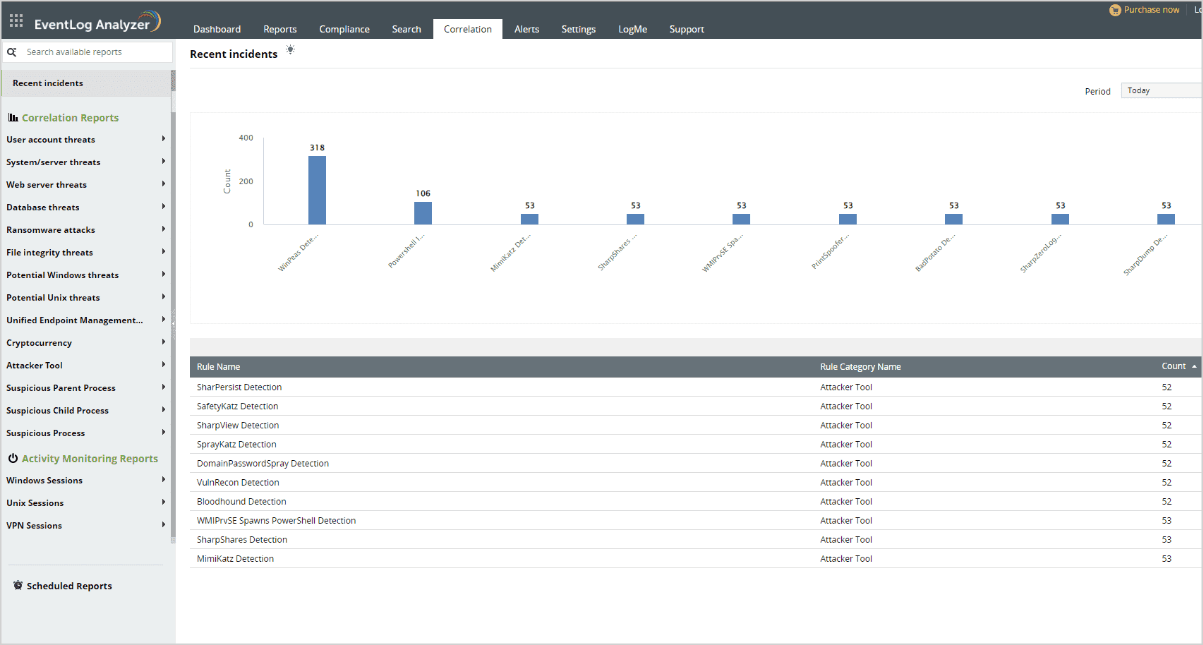
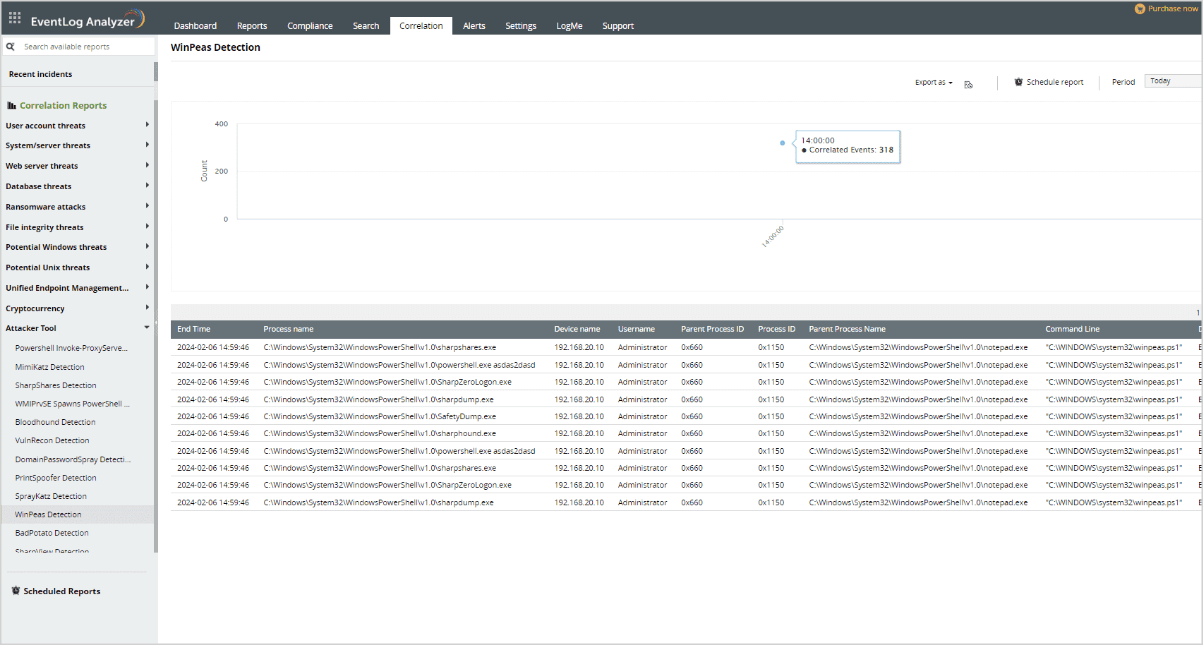
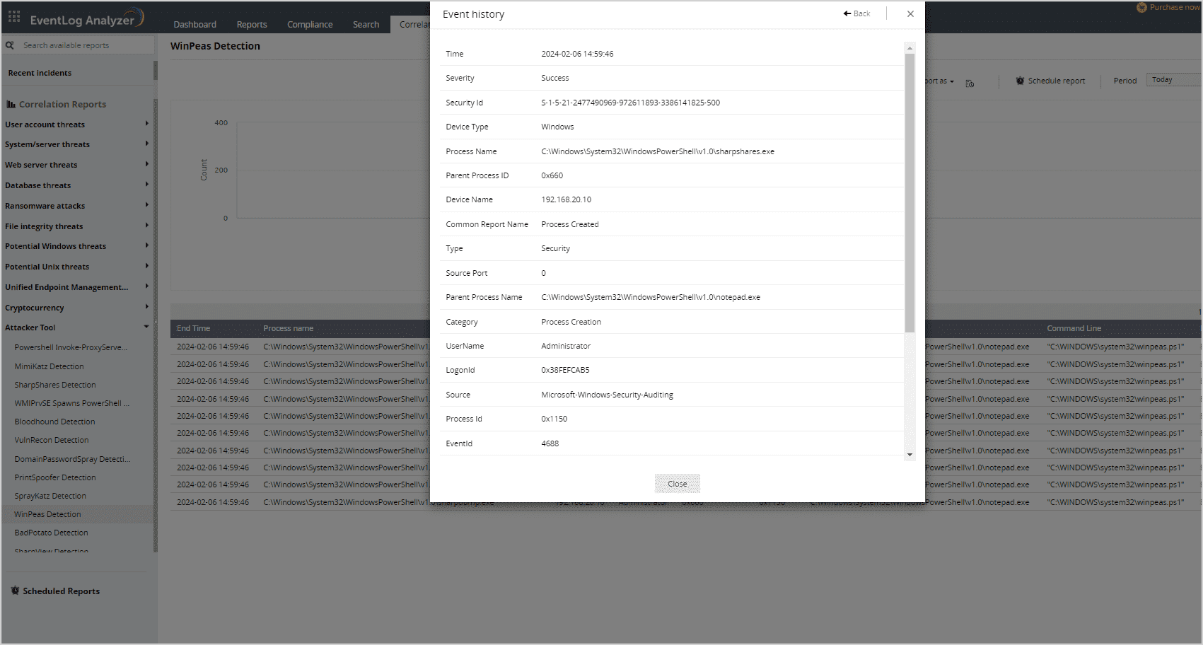
Log360 provides predefined correlation rules meticulously crafted to detect attack patterns accurately and minimize false alerts.
With the help of this solution, system administrators can use the pre-defined rules to easily identify whether there are any post-exploitation tools like WinPEAS.
The WinPEAS detection rule has some criteria like original file name that ends with "winPEAS. exe", command line that contains "winPEAS.bat" or "winPEAS.ps1", or the process name that contains "asdas2dasd" string.
By creating an alert profile with the correlation rule, the solution will alert whenever any WinPEAS script is executed.
What's next?
Interested to know more about the advanced network security features of Log360? Explore the free, 30-day trial with technical assistance.
- What is WinPEAS?
- How can WinPEAS be used for privilege escalation?
- How can attackers use this tool for their advantage?
- How does Log360 help in detecting WinPEAS script?