The latest update to the service organization controls 2 (SOC 2), a voluntary compliance framework, was published in October 2022. SOC 2 helps organizations manage customer data securely. Organizations can use this framework to recognize loopholes in existing controls and cybersecurity policies, and map these loopholes with the listed controls in the standard. They can then implement better controls in line with their risk requirements. It is specifically intended for all service organizations. With the proliferation of SaaS and IaaS organizations, numerous companies will benefit from SOC 2 compliance.
This blog will explore the following topics:
SOC 2 is a voluntary certification and framework created by the American Institute of Certified Public Accountants (AICPA). It is part of a family of similar frameworks, like SOC 3 and SOC 1.
The SOC 2 is not a mandatory regulatory standard; it is a benchmark that is widely accepted and acknowledged. Similar to ISO 27001, SOC 2 lets companies decide which security controls they need to implement based on their unique risk exposure.
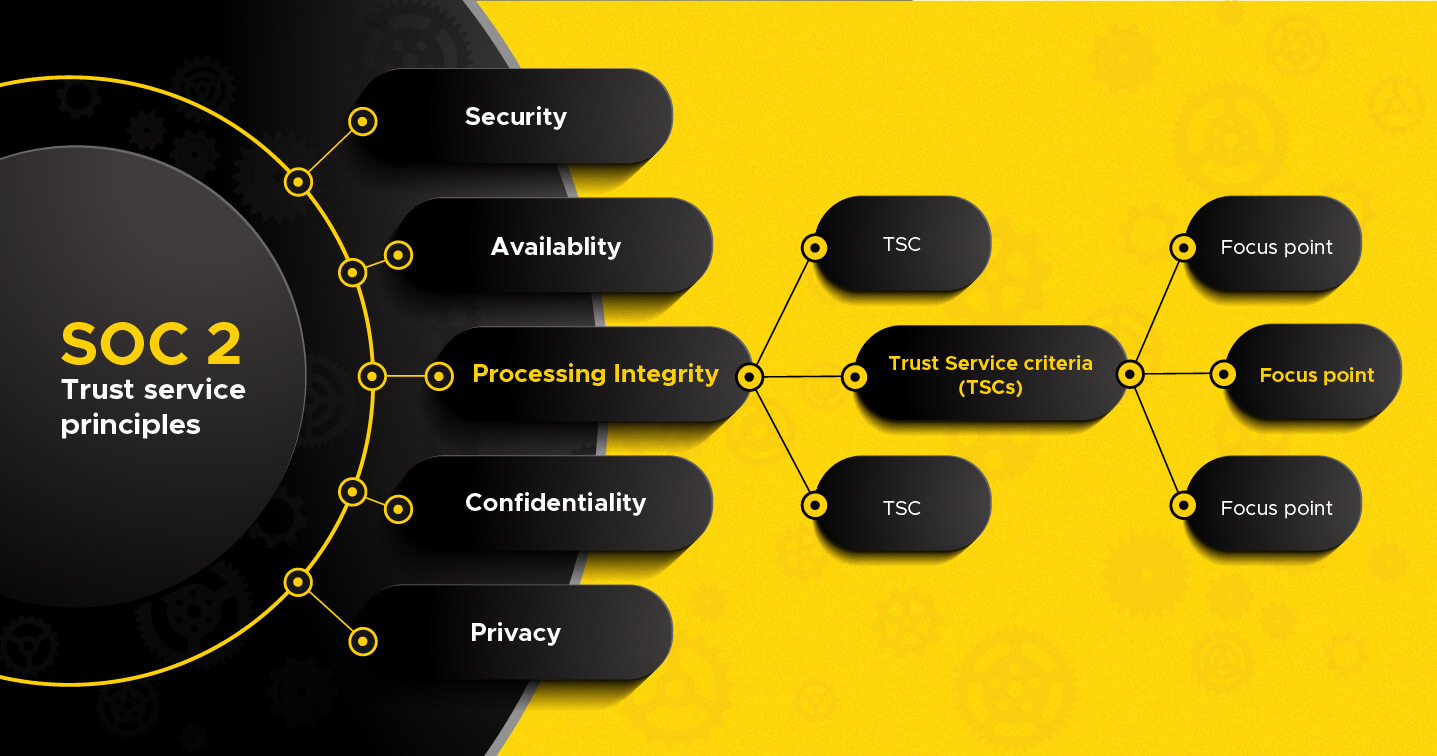
To understand the SOC 2 compliance requirements, we must first understand its structure. To do this, let us first explore three key terms or tiers in the structure.
The five trust service principles are:
Each of the TSCs listed under the security principle have relevant focus points under them for organizations to implement.
Once you grasp the five trust service principles and understand which apply to your situation, be prepared to carry out a risk assessment at least once a year. This is because a SOC 2 certification is valid only for a period of 12 months from it's date of issue. After a risk assessment, the next step is conducting a gap analysis, and then mapping the existing internal controls with the TSCs listed in SOC 2 to understand which of the controls must be implemented. Documentation of these processes is required for a successful SOC 2 audit.
Companies that aim to get SOC 2 certified must conduct internal and external audits. While the common practice is to conduct at least one internal audit every year, the AICPA prescribes two kinds of external audits. Let's take a look at how each type works.
Type 1: In a SOC 2 Type 1 audit, the aim is to give a glimpse of the current compliance status of the company to the auditors. Organizations can expect audits conducted on specific dates with the objective of assessing whether enterprise systems are suitable for implementing the necessary SOC 2 controls. The auditor might take a look at one specific requirement at random to check whether it has been implemented correctly.
Type 2: The objective of a SOC 2 Type 2 audit is to see whether an organization can consistently comply with the required security controls for a prolonged period. Organizations will be assessed for a particular evaluation period and regularly checked to ensure they are SOC 2 compliant throughout. The auditor will examine the required controls, all security systems and processes, and their operational efficiency for the evaluation period.
SOC 2 is similar to ISO 27001 in several ways. Both are frameworks that are risk-based and let the organization determine which security controls need to be implemented as per its requirements. SOC 2 and ISO 27001 are reputable certifications that clients and users expect from organizations that deal with their confidential information. While SOC 2 is limited to US-based companies, ISO 27001 is a certification that applies to companies all over the world.
While it is specifically meant for US-based companies, SOC 2 is not restricted to a particular sector or industry. Typically, SOC 2 compliance is important for service-based organizations. You should consider getting a SOC 2 certification if you're a:
Cloud security is a hot topic due to the increasing risk of data theft and unauthorized access to important files. According to Gartner, end-user spending on the cloud is predicted to increase by 20% in 2023. Whether you are a MSP who directly deals with end users, or an organization that offers Technology as a Service (TaaS) products or services to businesses that deal with end users, SOC 2 is a framework that you'll be expected to comply with.
With the fast-paced increase in cloud adoption and hybrid work, organizations will have to invest in solutions that address both on-premises and cloud security needs. ManageEngine Log360, a SIEM solution with integrated cloud security capabilities, helps enterprises with SOC 2 compliance and cloud security needs in several ways.
CASB: Log360 performs deep packet inspection to scan files and inform you about possible data exfiltration. It also provides visibility into shadow applications and prevents data leakage.
Monitoring cloud platforms: Log360 comes with a dedicated cloud security add-on that helps security analysts collect, monitor, and analyze logs from major cloud platforms like Amazon Web Services, Microsoft Azure, Google Cloud Platform, and Salesforce. Its alerting and reporting features provide several predefined reports to track user activity on the network.
Risk scoring and automated incident response: Equipped with SOAR and UEBA capabilities, Log360 employs ML algorithms to detect anomalies in the behavioral pattern of users and assigns a suitable risk score to alert the analysts. It also lets security admins set up automated workflows to respond to threats immediately.
Compliance management: Compliance analysts can create custom compliance reports and schedule them according to their requirements. They can also choose to be notified automatically via email whenever their scheduled report is created. Analysts can use Log360 to create customized reports for Type 1 or Type 2 audits.
If you're a service based enterprise that is planning to get SOC 2 certified anytime soon, you should consider opting for a compliance management solution like Log360, which can help you automate several tedious processes like audit reporting, monitoring security controls, and incident response.
To get started, you can choose to speak with our product experts and receive a personalized demo, or download a free trial version for 30 days to check it out for yourself.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.