Cyberattackers are always on the lookout for any potential vulnerability that can be exploited by multiple tactics and techniques like phishing, brute force attack, malware injection, social engineering, web hacking and more to fulfill their malicious intentions and bring organizations and businesses to a standstill.
In this blog we will shed light on two of the most common yet popular web hacking techniques among hackers: SQL injection attack and cross-site scripting (XSS).
SQL injection is a common and prevalent method of attack that targets victims' databases through web applications. It enables cyberattackers to access, modify, or delete data, and thus manipulate the organization's databases. For any organization, data is one of the most critical and valuable assets, and an attack on its database can wreak havoc on the entire business.
Data can include customer records, privileged or personal information, business-critical data, confidential data, or financial records of an organization.
According to MITRE ATT&CK, cyberattackers often exploit public-facing applications to gain the initial foothold within an organization's network. These applications are generally websites but can also include databases like SQL.
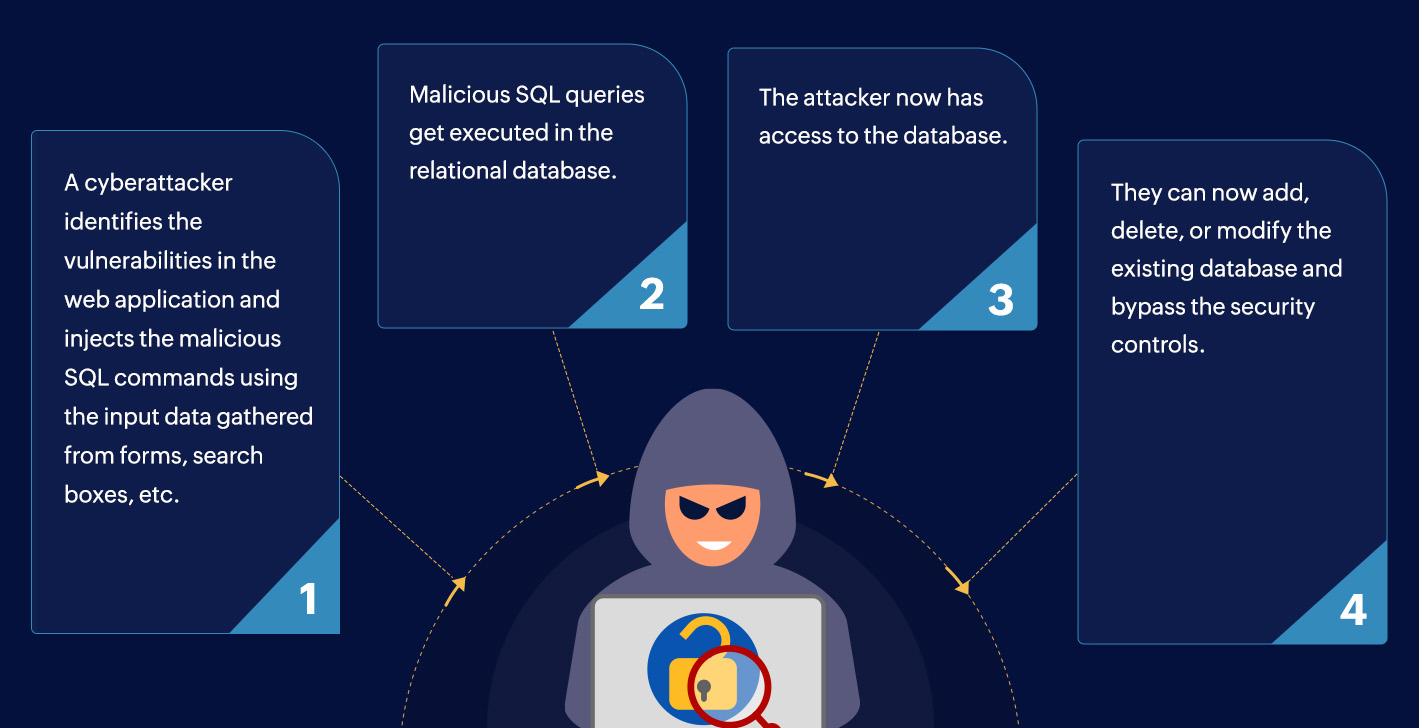
An SQL injection attack is carried out through the following steps:
Cross-site scripting (XSS) attack is a popular attack technique used by hackers to target web applications. Here, the attackers inject malicious client-side scripts into a user's browsers or web pages, allowing them to download malware into the target user's system, impersonate the target, and carry out data exfiltration, session hijacking, changes in user settings, and more.
According to MITRE ATT&CK, cross-site scripting is an example of a drive-by compromise technique used by adversaries to gain initial access within the network. The technique aims to exploit website vulnerabilities through malicious client side scripts or code. This provides them with access to systems on the internal network and also allows them to use compromised websites to direct the victims to malicious applications meant to steal and acquire Application Access Tokens (used to make authorized and legitimate API requests on behalf of users/services to access resources in cloud or SaaS applications).

An XSS attack is carried out through the following steps:
XSS is broadly categorized into three types, which are:
The attacker injects the malicious script in the DOM through a URL for instance, and when the user performs any action on that page or visits the page through that URL, the application updates the DOM to execute the malicious script.
Even though both SQL injection and XSS attack are common web hacking techniques, there are a few key differences between the two.
| SQL injection attack | Cross-site scripting attack | |
| Attack definition | An attack technique where attackers target data-driven applications and compromise user/organization databases by performing certain actions. | An attack technique where attackers execute malicious code in the victim users browsers which they can control. |
| Entry point | The initial access in SQL attack is achieved through drive-by compromise technique. | The initial access in XSS attack is achieved through exploiting public-facing application technique. |
| Attack technique | The attacker injects malicious SQL queries into web form input field. | The attacker injects malicious client-side scripts into webpages/websites. |
| Impact | Upon successful execution, the attacker can add, delete, or modify the existing database and bypass the security controls. | Upon successful execution, the attacker can perform session hijacking, credential theft, data exfiltration, impersonate victim user, account hijacking, etc. |
| Attack language | The most common language used in the attack is SQL. | The most common language used in the attack is JavaScript. |
Although SQL injection and cross-site scripting attack continue to be popular among attackers, continuous monitoring, testing, and deploying the best preventive measures will help organizations keep their websites from becoming prey to such attacks and neutralize any threats preemptively.
You will receive regular updates on the latest news on cybersecurity.
© 2021 Zoho Corporation Pvt. Ltd. All rights reserved.