What is cross-site scripting (XSS)?
- How it works: A XSS attack example
- Types of XSS attacks
- How to prevent XSS attacks?
- How to detect XSS attacks using a SIEM solution?
- Home
- Cybersecurity glossary
- What is cross-site scripting (XSS)?
XSS (cross-site scripting), is a prominent security vulnerability in web applications, where an adversary adds a malicious code into legitimate web pages. The malicious code can be injected in several ways, for instance it can be added to the end of a URL or posted directly onto a page that displays user-generated content. The exploitation of XSS can lead to a multitude of consequences for users, as the attackers can perform session hijacking, credential theft, data exfiltration, impersonate victim user, account hijacking, and more. This makes XSS one of the most common web application vulnerabilities.
How it works: A XSS attack example
Consider a web application, for example an e-commerce website, with a built-in search function. When a user searches for a product, their query is directly displayed on the results page. However, this process lacks adequate input validation and output encoding. A malicious attacker could recognize this vulnerability and create a harmful URL link to exploit the vulnerability.
https://example.com/search?q=<script>alert('XSS Attack!')</script>
The attacker will send this link to the user, pretending it's related to the product and the user might click on it. The web application will process the search query, including the injected script, without proper validation or encoding.
The response contains the malicious script, and the page displayed to the user looks like this:
<div>Search results for: <script>alert('XSS Attack!')</script></div>
The impact of this attack can vary based on the attacker's intentions. The attacker might aim to steal the user's session cookies, perform actions on their behalf, or redirect them to a phishing site.
Types of XSS attacks
XSS vulnerabilities come in different types, each with its own characteristics and attack vectors. Understanding these types is crucial for both web developers and security professionals to prevent effectively and mitigate XSS attacks. The main types of XSS are:
- Stored XSS (persistent XSS): A stored or persistent XSS attack is where the malicious code is permanently saved on the target server. It can be embedded in a database, user-generated content, or other permanent data storage areas. When a user accesses a page containing the stored script, the script is served directly from the server to the user's browser. Examples for stored XSS include message forums, blog comments, user profiles, or profile fields that contain XSS payloads.
- Reflected XSS: This is the most common XSS attack performed by adversaries. In this case, the malicious script is embedded at the end of the URL of a trusted website or within the data transmitted to the web server. Adversaries usually trick the users with social engineering containing the malicious payload, and the script is executed within the context of the user's browser. Examples include search queries, login forms, or any input fields that reflect user-provided data back in the response.
- DOM-based XSS: DOM-based XSS is a type of security vulnerability that occurs when a web application takes untrusted data from a user and uses it to update the document object model (DOM) of a web page. In simpler terms, it happens when a website allows user input to affect what you see and interact with on the page, and an attacker takes advantage of that to execute malicious code in your web browser. A DOM-based attack is unusual, as it exploits security vulnerabilities on the client-side code. Examples include modifying URLs to trigger JavaScript execution or manipulating client-side JavaScript variables.
How to prevent XSS attacks?
Preventing XSS vulnerabilities is crucial for web application security. Here are some effective measures to help prevent XSS attacks:
- Input validation: Input validation is the process of inspecting and validating user-provided data before it is processed by a web application. The goal is to ensure that the input adheres to expected formats, constraints, and security requirements. If the input does not meet these criteria, it is rejected or sanitized to remove or neutralize potentially harmful content. Input validation helps prevent a wide range of security vulnerabilities, like SQL injection, XSS, or command injection.
- Output encoding: Output encoding is the process of encoding data before rendering it in a webpage or response. This encoding ensures that user-generated or untrusted data is treated as data, not code, and cannot be executed as scripts or interpreted as HTML, JavaScript, or other scripting languages. Output encoding protects against XSS attacks. Even if an attacker manages to inject malicious scripts into the application's data, proper output encoding ensures that these scripts are treated as plain text and not executed when displayed in a webpage.
- Content security policy (CSP):
Content security policy (CSP) is a security feature that helps to prevent XSS attacks by controlling which scripts are allowed to execute on a webpage. CSP enables web developers to specify a policy that defines the trusted sources that scripts, styles, and other resources can be loaded from.
Web developers should include a CSP header in the HTTP response to implement the CSP. The CSP header defines the security policy for a web page. If adversaries try to inject malicious scripts into a page, the CSP policy will block the execution of those scripts, if they are not loaded from trusted sources specified in the policy.
- HTTP-only and secure cookies: HTTP-only and secure cookies are security attributes that can be applied to cookies in web applications to help prevent XSS attacks and protect user data.
- HTTP-only cookies: An HTTP-only cookie is a cookie that is set with an attribute that prevents it from being accessed or manipulated by the JavaScript code running in a webpage. This helps protect the cookie from being stolen in XSS attacks. For instance, when a customer is logging into a website, the website stores your session ID in a cookie and it doesn't have a HTTP-only attribute. Adversaries can successfully injects malicious scripts into the webpage and could potentially steal your session cookie using JavaScript and hijack your session.
- Secure cookies: A secure cookie is a cookie that is only transmitted over a secure HTTPS connection, ensuring that it's not exposed to interception or manipulation during transmission. This helps protect the cookie's content, including sensitive user data. When a cookie is marked as secure, it is only transmitted over HTTPS connections, which encrypt the data during transmission. When attackers try to intercept it, they won't be able to read its contents because it is encrypted.
How to detect XSS attacks using a SIEM solution?
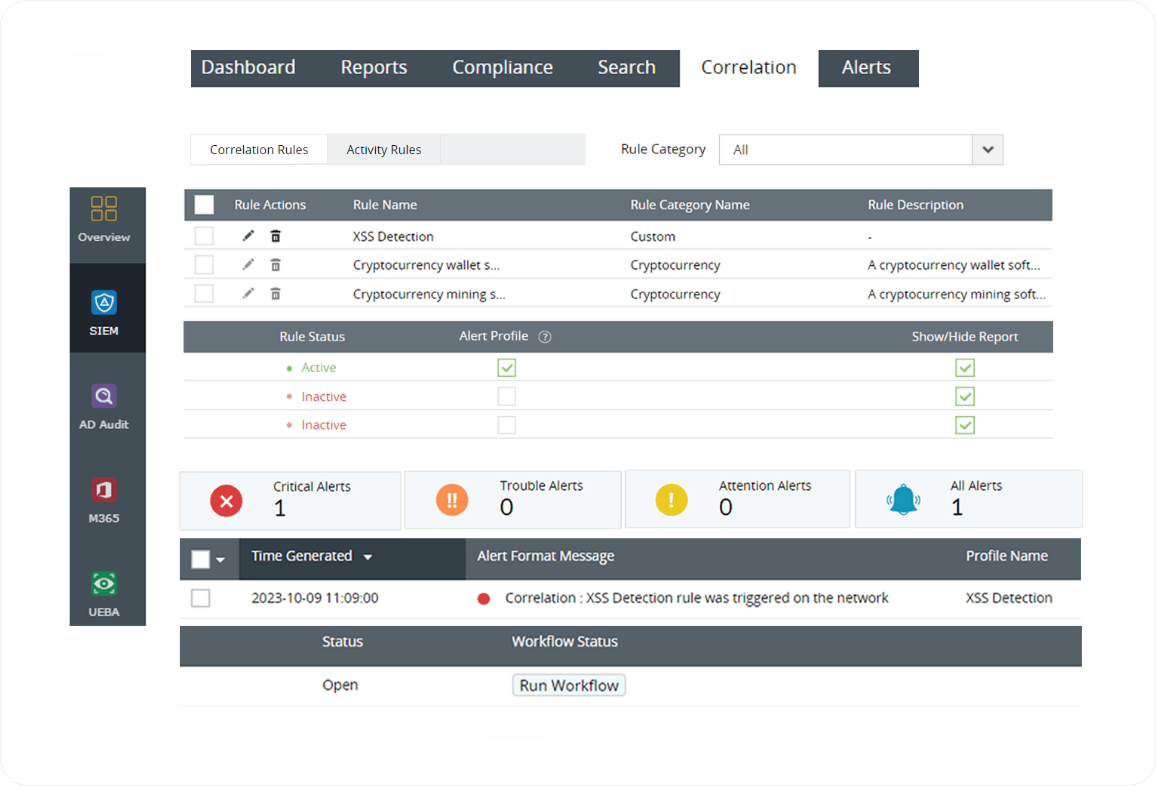
We know XSS is one of the most common attacks faced by thousands of websites and also by millions of users. It is crucial to detect and mitigate this threat as early as possible to avoid system compromise or any data leak. A SIEM solution like Log360 will be helpful for organizations as it collects and correlates the data you need to identify patterns that signal an attack.
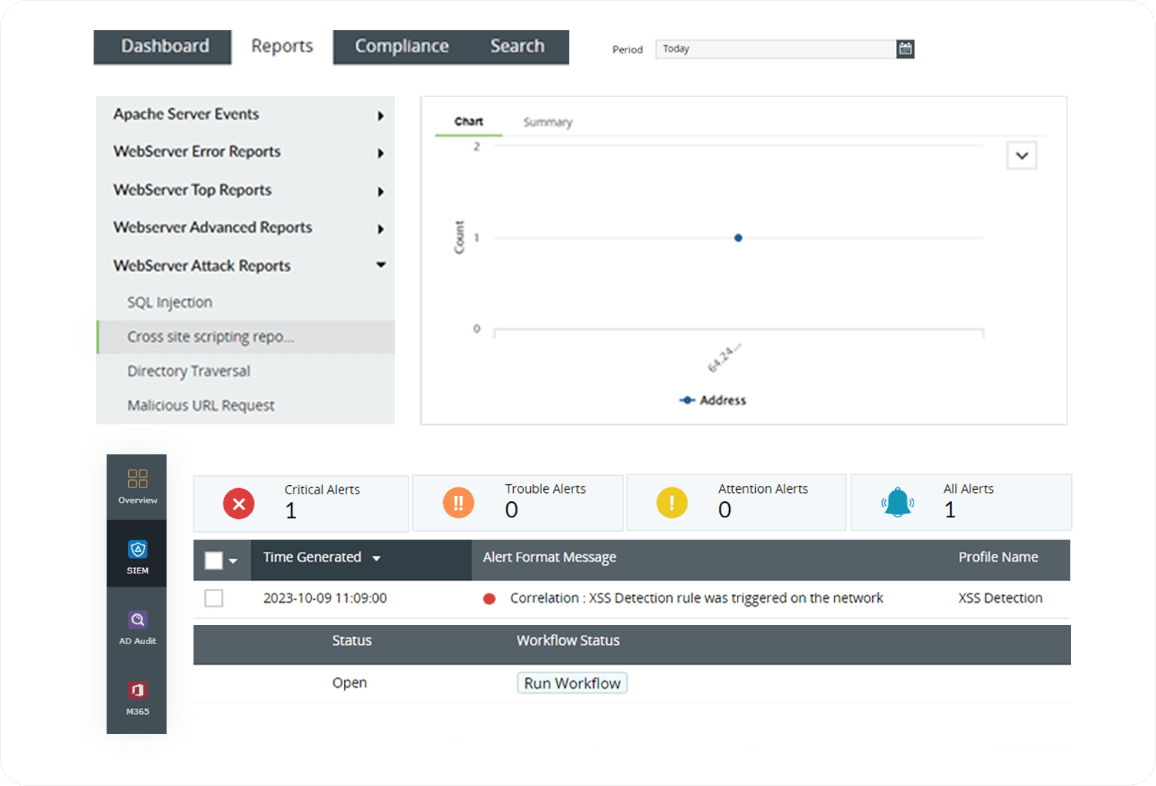
Audit web server logs
Websites are frequently targeted for attacks, especially those involving XSS, as they are accessible to the public and interact with external users. When an XSS attack occurs, web servers record potential attack attempts, including details like their origin, timing, and related information. Analyzing web server logs (like Apache server) for XSS incidents is crucial for enhancing online security and offers essential insights into security breach attempts. Log360 monitors all web servers in your network to look for vulnerabilities. If there are any error logs for unusual requests or error messages in a web server, an alert will be triggered and the security admin will be notified via email or SMS.
Event correlation
Log360's event correlation involves analyzing and connecting various security events and logs from different sources to identify patterns or sequences of events that may indicate a security incident. For example, Log360 can link a detected XSS event to user login logs or access control events, helping security admin understand the context of the attack.
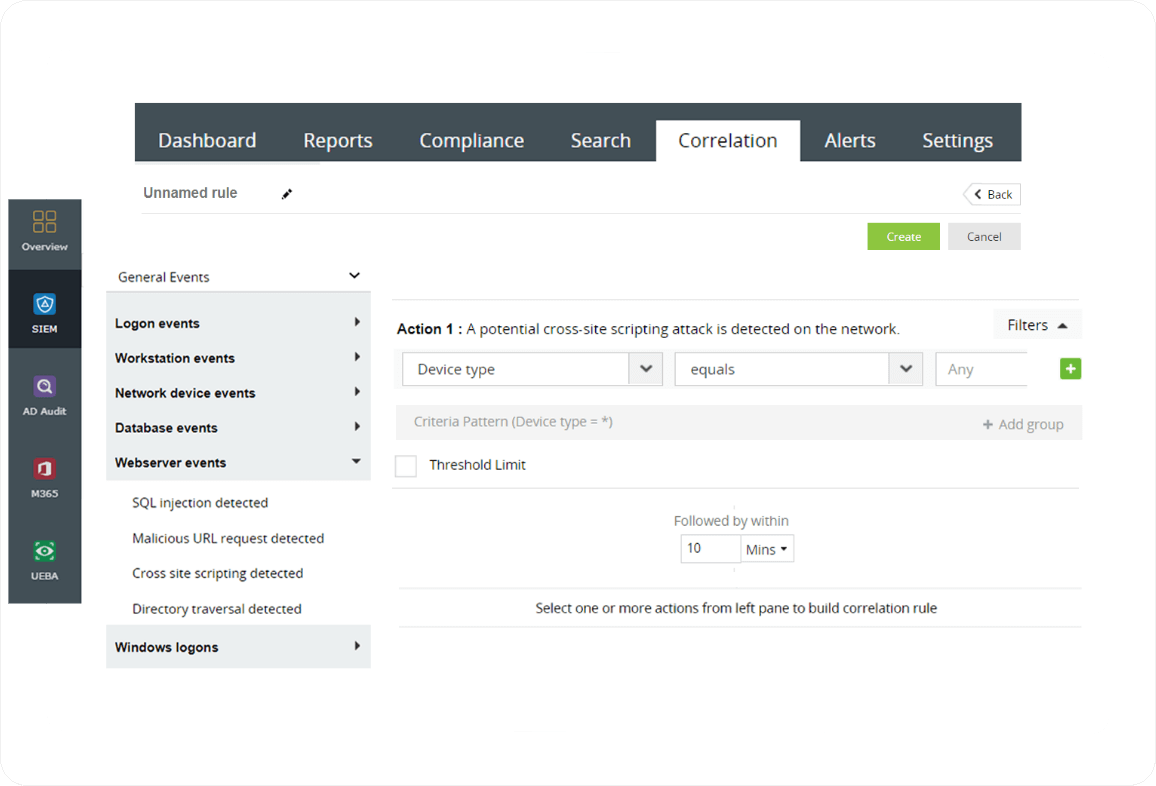
Incident response
Security analysts have the capability to identify real-time security incidents such as XSS attacks within their network promptly with Log360. It also offers automated incident response workflows, which are initiated upon alert activation, delivering immediate responses to security incidents without requiring the direct involvement of a security analyst.