On this page
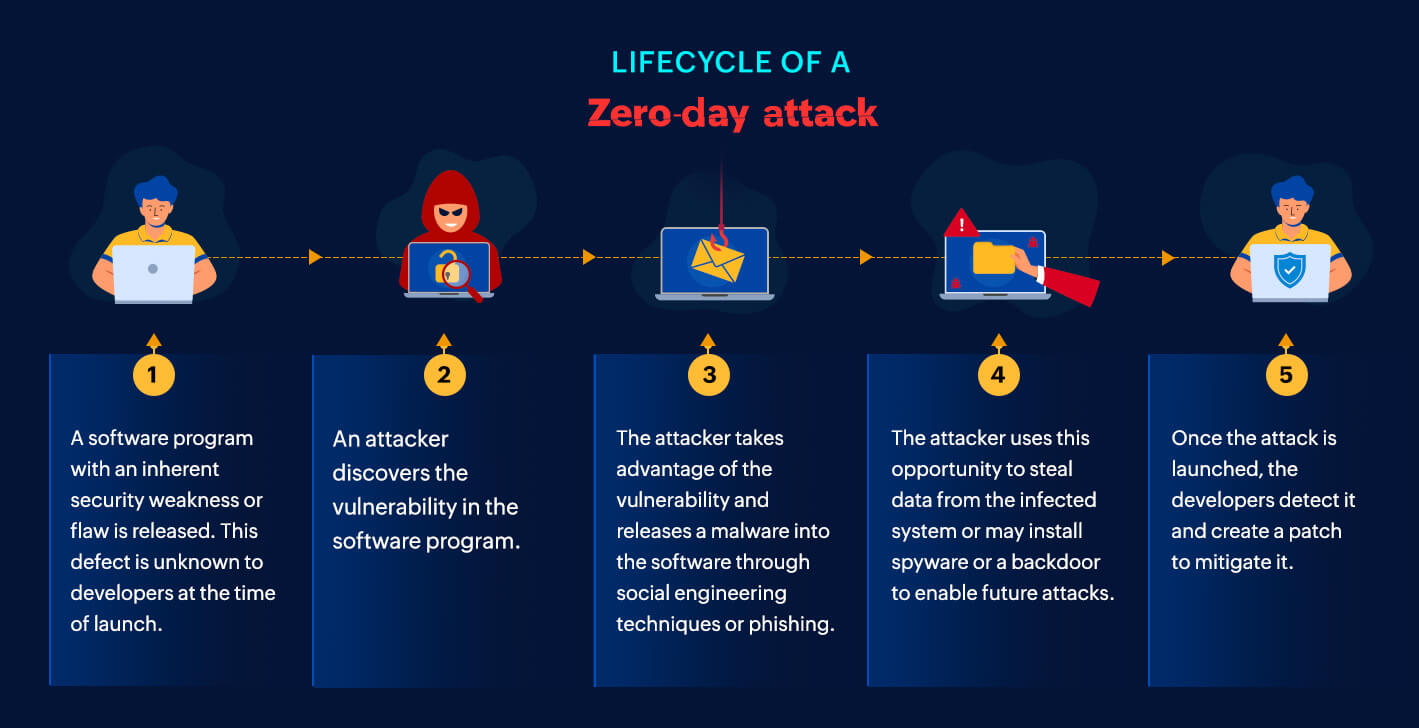
NIST defines vulnerability as a weakness in an information system, system security procedures, internal controls, or implementation of technology that could be exploited or triggered by a threat source. Cybercriminals are always on the hunt to find new vulnerabilities which they can pounce on to further their malicious intentions. Most of the time, these new security flaws in programs are unknown to the developers, so there is no patch available to fix them, and it makes the work of attackers easier.
In the ever-evolving threat landscape, it has become imperative for organizations to revisit their defense strategies and continually prepare for threats, such as a zero-day attack. In a zero-day attack, cybercriminals exploit a vulnerability in software which is unknown to its developers.
What is a zero-day vulnerability, attack, and exploit?
Zero-day vulnerability: This is a vulnerability or a weakness which is unknown to the developers or the vendors, and is first discovered by adversaries. The bad actors might then carry out cyberattacks by leveraging it.
Zero-day attack: This is an attack carried out by exploiting the zero-day vulnerability discovered by the threat actors.
Zero-day exploit: This is a technique used by attackers to gain access into a system or take advantage of a zero-day vulnerability.
Generally, zero-day attacks are target-specific, and the victims can be exploited to gain confidential information. Some of their common targets are government institutions, large scale organizations, financial institutions, and individual users having access to classified information.
Examples of a zero-day attack
The following are two examples of zero-day attacks which received news coverage because of the high impact the hack had on the victim organizations:
- WannaCry Attack: The WannaCry ransomware attack was a global cyberattack in May 2017 that affected more than 150 countries in less than 24 hours and cost billions of dollars. It spread using EternalBlue, an exploit that was discovered by the National Security Agency (NSA) and further stolen and publicly leaked by a group of hackers called the Shadow Brokers. EternalBlue took advantage of a vulnerability in Windows’ Server Message Block (SMB) protocol.
- Sony: Sony Pictures became a target of zero-day exploit in 2014. The attack caused a shutdown of Sony's network and confidential data including personal information of employees, and classified business plans. The bad actors also leaked copies of unreleased movies.
Preventive measure against zero-day attack
It is not possible for organizations to completely protect themselves against zero-day threats. However, they can follow certain best practices and strategize their defensive game plan to defend and mitigate such attacks as much as possible.
Here are some of the measures which organizations can follow to mitigate zero-day threats:
- Use antivirus and antimalware software to protect against different viruses and malwares.
- Ensure all the software and devices are updated and patched.
- Keep a backup of all the critical data and systems.
- Stay on top of news or information on any newly discovered vulnerability.
- Use a web application firewall.
- Detect threats by spotting anomalies.
- Educate and create awareness among users about zero-day attacks.
Zero-day threats are hard to detect as they are generally known to the public only upon their execution. However, organizations and users should continue to take the best preventive measures possible to mitigate and to contain zero-day attack damage.
Related solutions
ManageEngine AD360 is a unified IAM solution that provides SSO, adaptive MFA, UBA-driven analytics, and RBAC. Manage employees' digital identities and implement Zero Trust and the principles of least privilege with AD360.
To learn more,
Sign up for a personalized demoManageEngine Log360 is a unified SIEM solution with UEBA, DLP, CASB, and dark web monitoring capabilities. Detect compromised credentials, reduce breach impact, and lower compliance risk exposure with Log360.
To learn more,
Sign up for a personalized demoThis content has been reviewed and approved by Ram Vaidyanathan, IT security and technology consultant at ManageEngine.