Data breach at the US Army's Cyber Protection Brigade — here's all you need to know.
An image recently leaked online—on 4chan's Business and Finance forum—seems to suggest that the US Army worked with the NSA to unmask users who access anonymous networks via Tor, Invisible Internet Project (I2P), or VPNs. The memo, from the US Army's Cyber Protection Team (CPT), also shows that they're finding it difficult to identify users of several digital currencies, including Monero (XMR) and Karbo (KRB). Data leaks are on the rise, and this leak is just another example that whether it be photos,electronic documents, emails, or memos, we need to implement security measures to prevent these leaks from continuing. Organizations should take notice that the damage of a leak or breach isn't just the public access of private information, but the tarnished perception of that organization.
How did people react to the leak?
Response to this leak has been of two varieties. Some people believe that the intelligence community is looking into anonymous services and cryptocurrencies for law enforcement purposes. Others think it's fake and aimed at creating fear, uncertainty, and doubt (FUD) surrounding cryptocurrencies in an effort to reduce their prices and provide cheaper investment opportunities. The lack of classification markings and the presence of BLUF (Bottom Line Up Front) at the end of the memo, instead of the beginning, has led people to believe that it's not real.
The memo reads:
SUBJECT: Additional resource request for ACC project
- 2nd Battalion’s joint NSA/CPT [Cyber Protection Team] anonymous cryptocurrency project needs additional support in the form of new hires and additional funding to meet GWOT [Global War On Terror] and drug interdiction objectives outlined in July’s Command update brief.
- Requesting authorization to add additional civilian consultants to the ACC project and to initiate their SCI investigations.
- Requesting additional funds for class 7 and 9, amounts indicated in attached cost analysis worksheet.
- The success we have had with Tor, I2P, and VPN cannot be replicated with those currencies that do not rely on nodes. There is a growing trend in the employment of Stealth address and ring signatures that will require additional R&D. Please reference the weekly SITREP [SITuation REPort] on SIPR for more details regarding the TTPs involved.
- BLUF [Bottom Line, Up Front]: In order to put the CPT back on track, we need to identify and employ additional personnel who are familiar with the CryptoNote code available for use in anonymous currencies.
- BLUF [Bottom Line, Up Front]: In order to put the CPT back on track, we need to identify and employ additional personnel who are familiar with the CryptoNote code available for use in anonymous currencies.
- Include this request for discussion at the next training meeting.
- Point of contact for this memorandum is CW4 Henry, James P. at DSN (312)-780-2222.
JAMES,HENRY
.P1363921716
JAMES P.HENRY
CW4,USASPB
A closer look
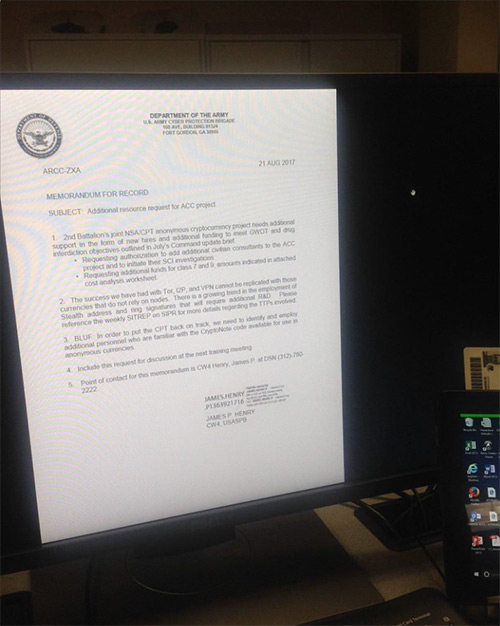
If you take a close look at the photo, you can see a Common Access Card on top of the tablet on the right side. These access cards are used by Department of Defense officials. It remains to be seen if this inclusion was a simple mistake or the kind of easter egg that usually comes with deliberate leaks. If this memo is real, some serious data protection violations have been made.
What can other organizations learn from this incident?
Here's how you can avoid such a leak happening in your organization:
- Limit the number of users who have access to sensitive data.
- Require access cards to be flashed for entry to zones where confidential information is discussed. This will also help identify the individuals responsible for a leak if one does occur.
- Educate employees about locking workstations when they're away from their desks.
- Secure your endpoints to prevent confidential information from leaving your organization.
It should be noted that breaches such as this one are quite rare, but can definitely be avoided by following the above-mentioned practices. However, there are several other instances of data leaks that a third-party tool can help investigate or curb.
How does ManageEngine help with forensics?
Data breaches and other security attacks are only on the rise, and you need to ensure your enterprise has measures in place to detect them. Here's how ManageEngine can help:
- Audit data transfers through removable media devices using our real-time Active Directory auditing tool, ADAudit Plus.
- Locate emails that contain confidential data as attachments by filtering based on file name and type using Exchange Reporter Plus.
Latest Ransomware attacks
Latest Data breach attacks
Latest Email Phishing attacks
Latest DoS and DDoS attacks
Latest Brute force attack
Latest Advanced persistent threat (APT)
