Log360 is a comprehensive security information and event management (SIEM) solution that helps you proactively thwart both insider and external attacks; spot, resolve, and contain security threats; and prove your adherence to compliance mandates. It does these by seamlessly integrating components and modules such as log management, Active Directory (AD) auditing, Exchange Server monitoring, cloud infrastructure reporting, and much more.
With Log360, you can gain complete control over your network, and audit AD changes, network device logs, Microsoft Exchange Servers, Microsoft Exchange Online, Azure Active Directory, and your public cloud infrastructure, all from a single console.
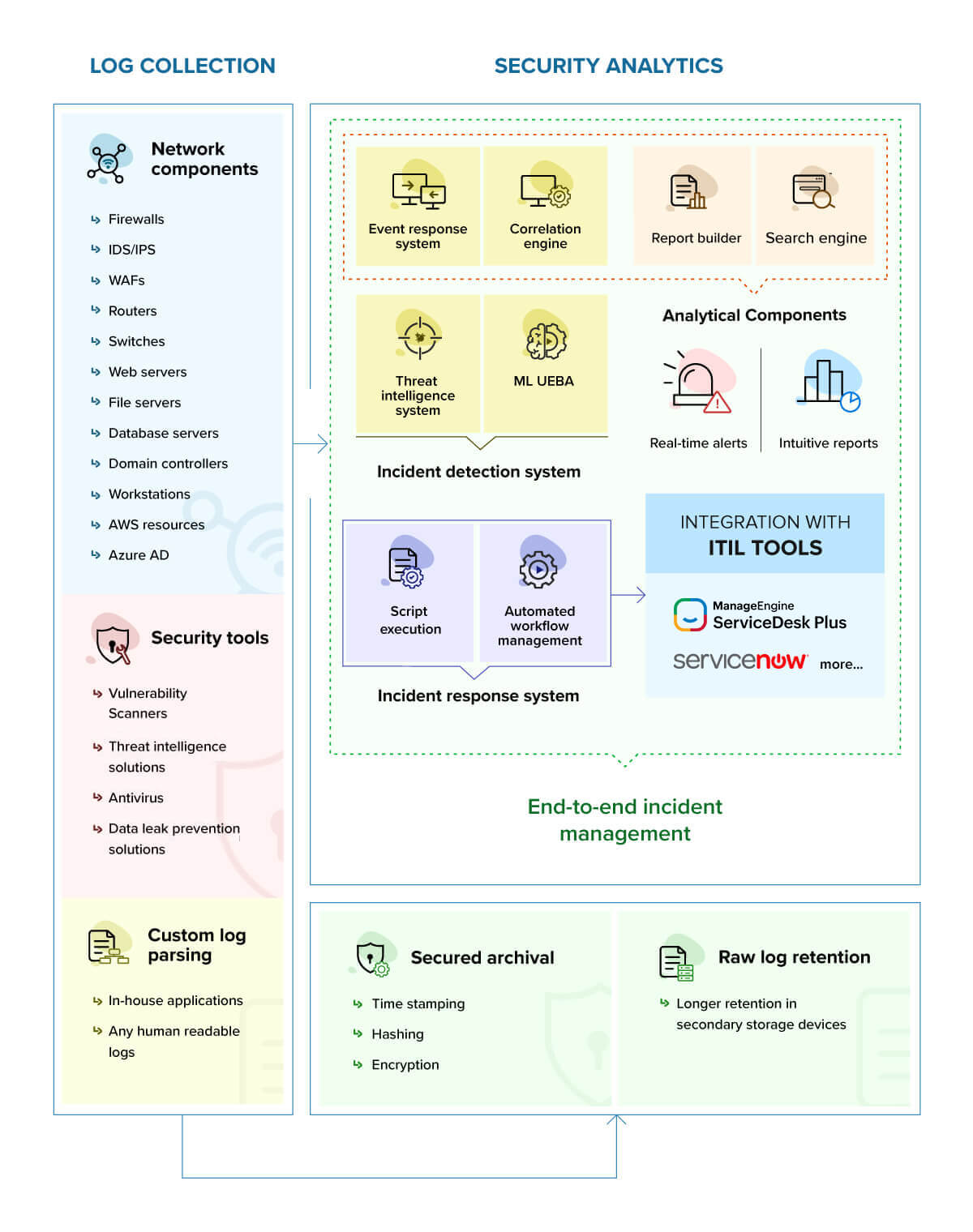
Collects logs from multiple log sources such as firewalls, Windows systems, Unix/Linux systems, applications, databases, routers, switches, and intrusion detection systems (IDS)/intrusion prevention systems (IPS). The solution supports over 700 log sources for analysis right out-of-the-box. Furthermore, it also has a custom log parser to parse and analyze log data from unsupported devices.
Offers predefined security report templates, alert profiles, correlation rules, and workflow profiles to effectively detect, analyze, and mitigate attacks and incidents.
Includes a built-in reports library with over with over 1,000 predefined reports. Reports are generated instantly whenever logs are collected, reducing organizations' auditing overhead by presenting only the most important information. These reports help organizations analyze their networks, and meet various security and compliance requirements.
Enables you to respond to critical security events promptly. It sends out email and SMS notifications based on configured alert profiles; assigns incidents to designated technicians, and stores the statuses and related information for every incident.
Helps you identify the defined attack patterns within your logs efficiently. It also provides real-time alerts and intuitive reports that help you take timely actions to mitigate the impact of the attacks. Log360 is also integrated with ITIL® tools ServiceNow and ManageEngine ServiceDesk Plus to align the IT services to efficiently resolve incidents. Its powerful search engine helps you search through logs seamlessly, irrespective of the volume of data.
Automatically archives all event logs and syslogs collected from Windows and UNIX devices, routers, switches, and other syslog devices. The event log archive is invaluable in forensic analysis and determining performance and usage statistics for a device. The archived log data is encrypted and time stamped to ensure that the archive data files are tamper-proof. The default log compression period is seven days, and can be customized according to the needs of the organization. Archiving can also be disabled entirely, though this isn't recommended.
The incident management console collates events, reports, log searches, and alerts that are manually added as incidents or captured through predefined rules. As security incidents get detected through Log360's correlation engine and machine-learning-based behavior analytics module, the incident console helps create tickets, manage and track the status of the incidents, automate assigning technicians or administrators, activate workflows, and observe SOC metrics such as mean time to detect (MTTD) and mean time to respond (MTTR). Users can also design customized workflows to mitigate the impact of the attack.
Analyzes logs from different sources including firewalls, routers, workstations, databases, and file servers. Any deviation from normal behavior is classified as a time, count, or pattern anomaly. It then gives an actionable insight to the IT administrator with the use of risk scores, anomaly trends, and intuitive reports.
Helps detect any communications with various known external malicious sources. Its built-in integration with Webroot and its BrightCloud Threat Intelligence service provides in-depth insights into the threats that have been flagged; security teams can analyze the reputation scores of IPs and URLs, and take appropriate remedial actions.
Offers over 200 event-specific reports and real-time email alerts, Log360 provides in-depth knowledge about changes made to both the content and configuration of Active Directory, Azure AD, and Windows servers.
Log360 can report on and audit Microsoft Exchange Servers with over 100 different reports for every aspect of an Exchange Server environment. With these reports, you can perform Exchange traffic analysis, get detailed reports on ActiveSync usage, and more.
A singular console that allows you to monitor, audit, and create alerts for critical activities related to M365 services such as Exchange Online, Azure Active Directory, Skype for Business, OneDrive for Business, Microsoft Teams, and others.
Combats security concerns and protects your cloud. It gives complete visibility into both your Amazon Web Services (AWS) and Azure cloud infrastructures. The comprehensive reports, easy search mechanism, and customizable alert profiles enable you to track, analyze, and react to events happening in your cloud environments, ensuring your business runs smoothly in a secure and protected cloud.