An unsecured VPC might be subject to cyberthreats. Monitoring Amazon VPC (Virtual Private Cloud) allows you to proactively identify and resolve issues, optimize resource use, and ensure compliance with security and regulatory standards.
ManageEngine Log360 collects and analyzes log data from a variety of sources inside your VPC environment—including VPC Flow Logs, CloudTrail logs, and system logs from your EC2 instances—to provide you a complete picture of your VPC activities.
With ManageEngine Log360, you can monitor VPC Flow logs, audit security group changes, perform forensic analysis with CloudTrial logs, track the AWS S3 bucket changes, keep track of AWS EC2 instances, and more.
Monitor VPC Flow logs
The VPC activity reports allow you to automatically examine VPC flow logs to monitor significant changes to VPCs, network gateways, VPC endpoints, VPC route tables, subnets, and VPC routes. Also, you'll be able to set up custom alerts to receive information about any questionable changes to VPCs and gain insight into who made the change, when, and from where (as shown in Figure 1).
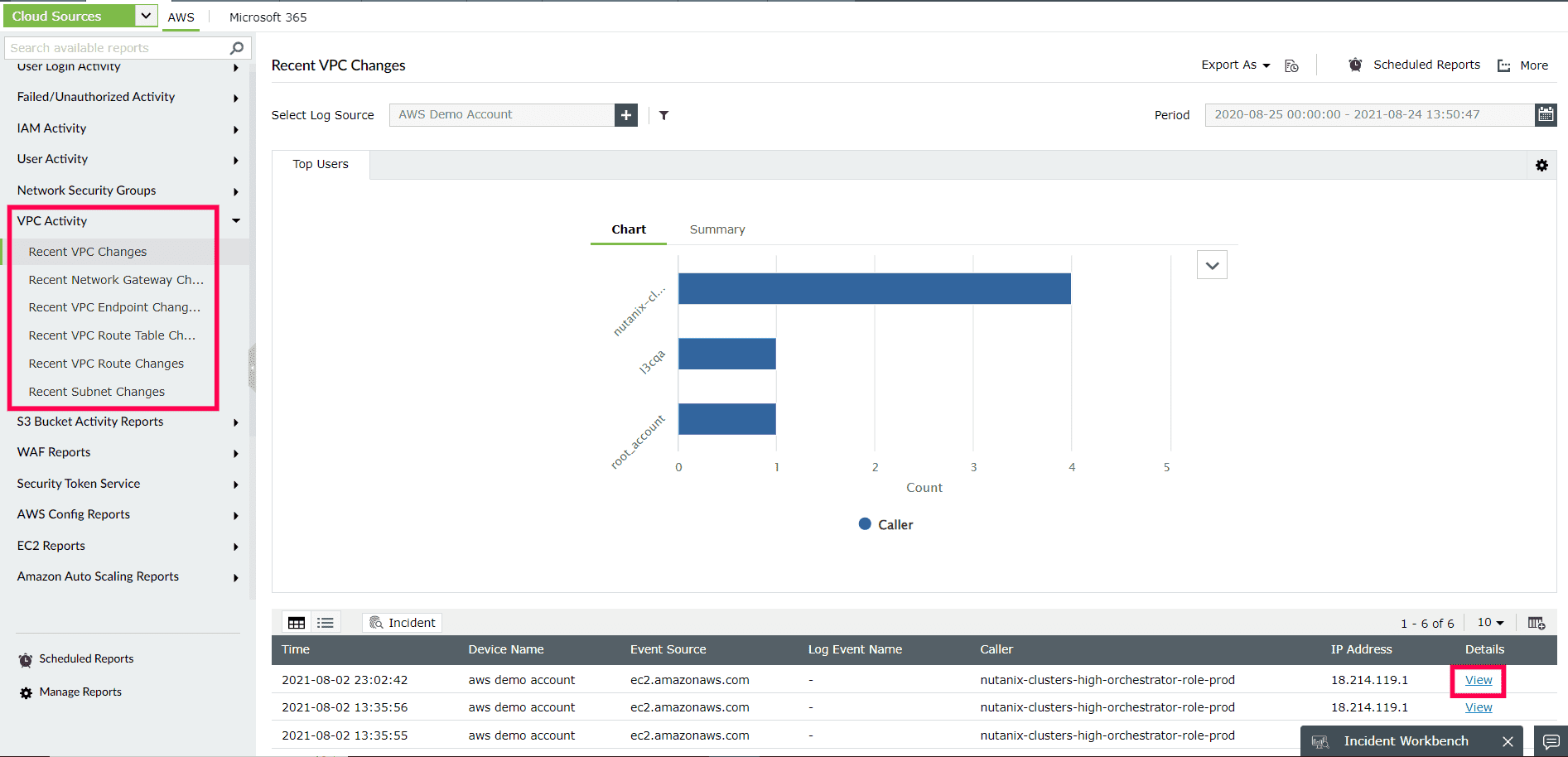
Figure 1: ManageEngine Log360's VPC activity report
Audit security group changes
Gain visibility into recent configuration changes, such as adding IP addresses to security groups or approving inbound traffic using security group rules. Log360's reports provide insights into created and deleted security groups, configuration changes, permitted and revoked security group ingress and egress, network gateway changes, and network access control list (ACL) changes (as shown in Figure 2). With this detailed information, you can detect potential security issues and malicious activities targeting your cloud instances.
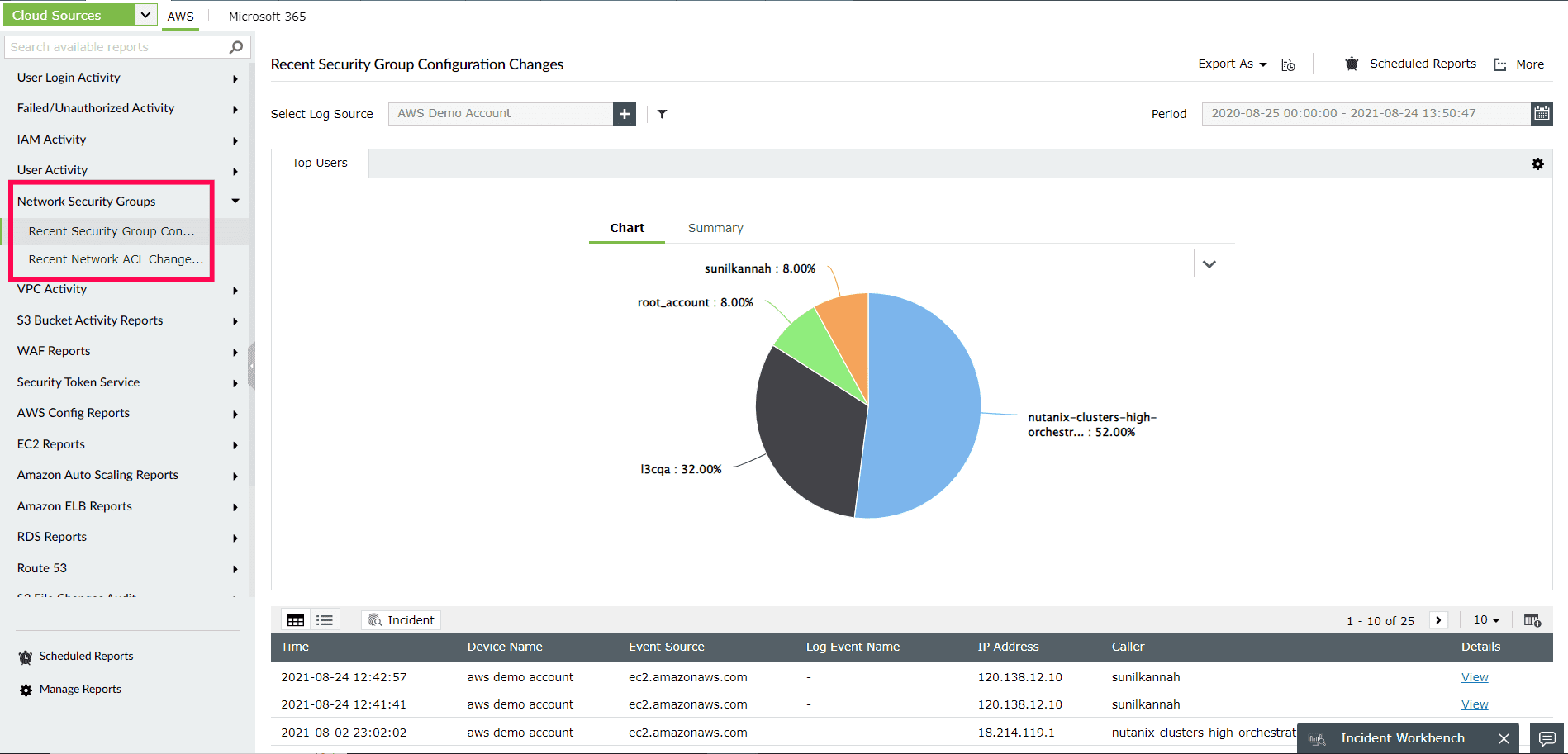
Figure 2: ManageEngine Log360's Network Security Groups report
Perform forensic analysis with CloudTrial logs
Log360 receives and analyzes your AWS CloudTrail logs and S3 server access logs to deliver valuable insights into your AWS environment. An auto-configuration feature simplifies the time-consuming configuration process required to begin obtaining CloudTrail logs. Also, providing flexible log storage and an effective search mechanism simplifies manual forensic analysis (refer to Figure 3).
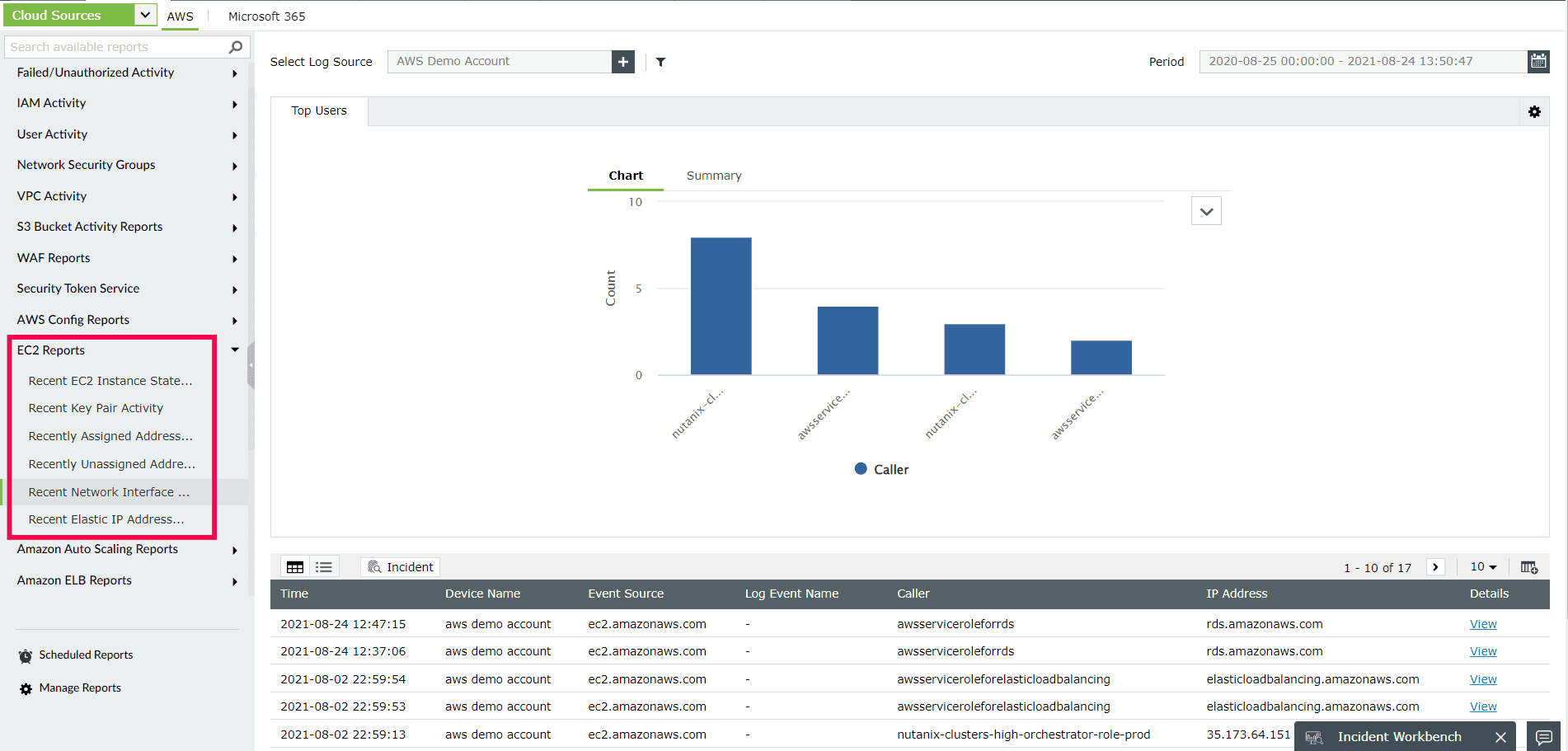
Figure 3: ManageEngine Log360's EC2 reports
Track the AWS S3 bucket changes
Monitor the S3 bucket changes in your AWS VPC environment by running reports on crucial actions like bucket creation and deletion (as shown in Figure 4). These provide critical information such as who did the action, the originating IP address, the time of the event, and any errors that occurred. Log360 aggregates the failure events in the S3 service and provides the details about the problem that caused the activity to fail, such as the error number and message. The deletion events—such as DELETE Bucket lifecycle, DELETE Bucket policy, and DeleteMultipleObjects—are also recorded at both the bucket and object levels.
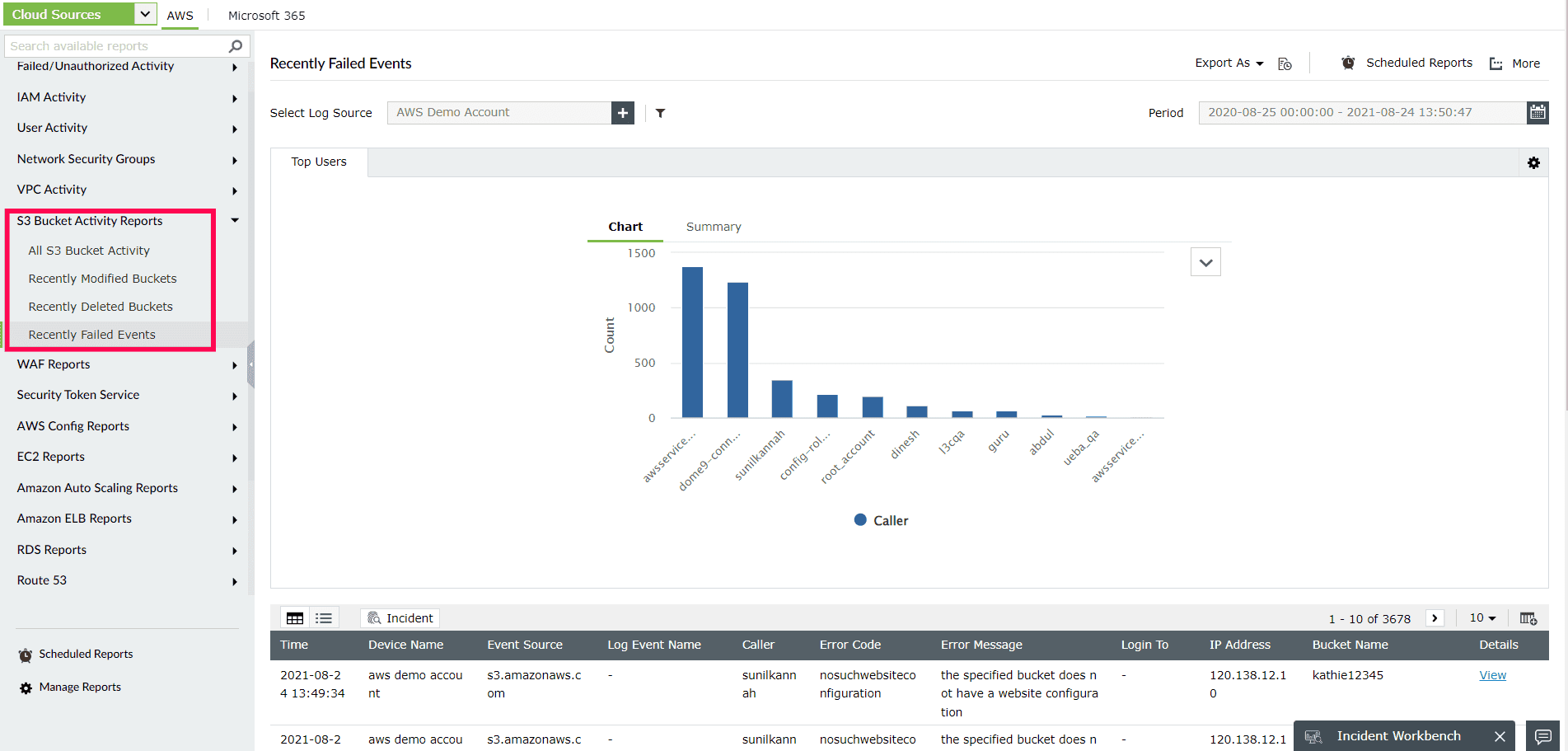
Figure 4: ManageEngine Log360's S3 Bucket Activity reports
Keep track of AWS EC2 instances
Closely monitor the changes to AWS EC2 instances to guarantee the security of sensitive enterprise data hosted in the cloud, detect potential security concerns, and satisfy compliance requirements. With its EC2 reports, Log360 helps you keep track of EC2 state changes—such as instances starting, rebooting, and halting—and provides information on who executed the event, when, and where it occurred (as shown in Figure 5).
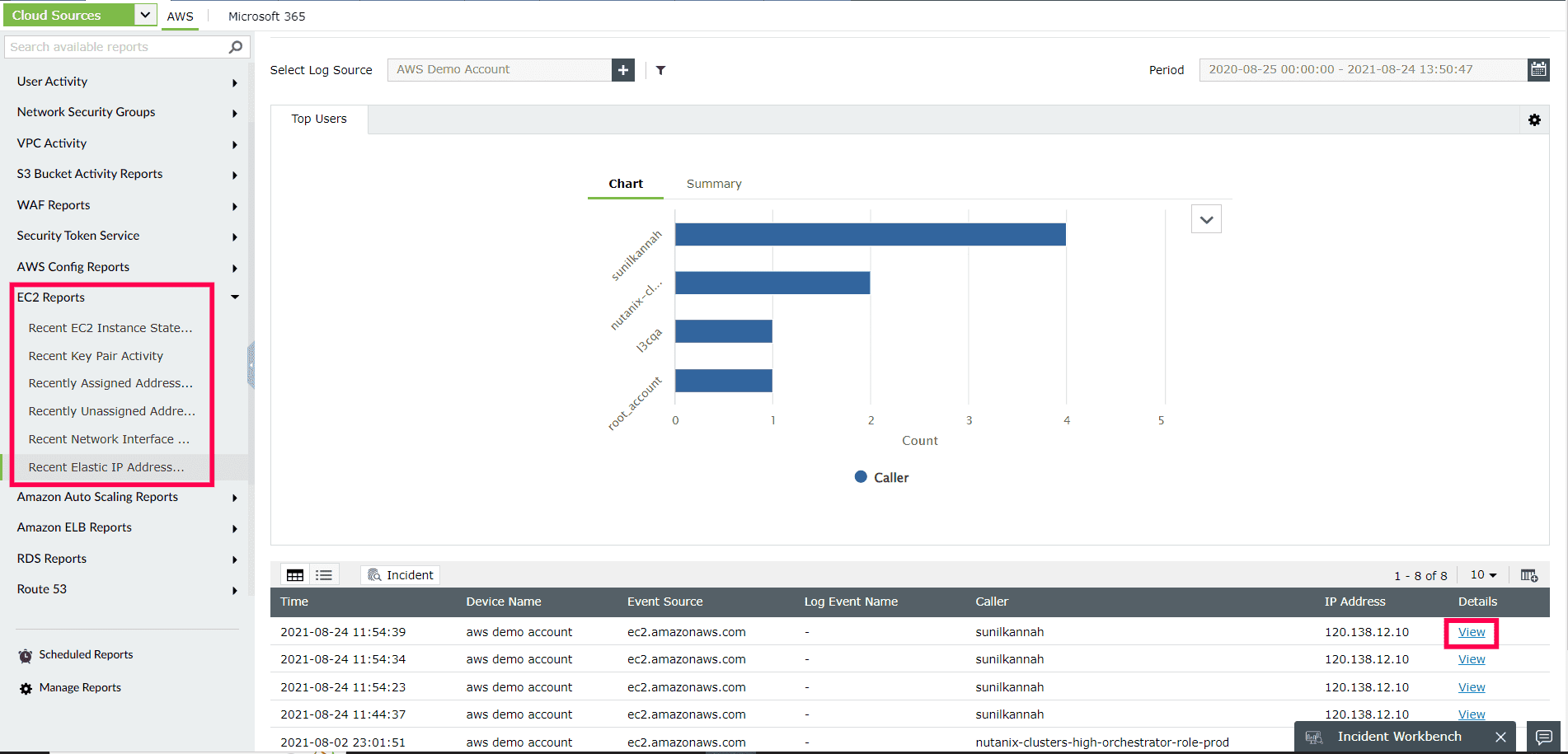
Figure 5: ManageEngine Log360's EC2 reports
Get an overview of your environment
EventLog Analyzer has a near real-time dashboard that presents an overview of the activities that occur within your AWS environment. The dashboard helps you discern anomalies quickly, investigate threats and attack patterns, and get insights from log trends (as shown in Figure 6).
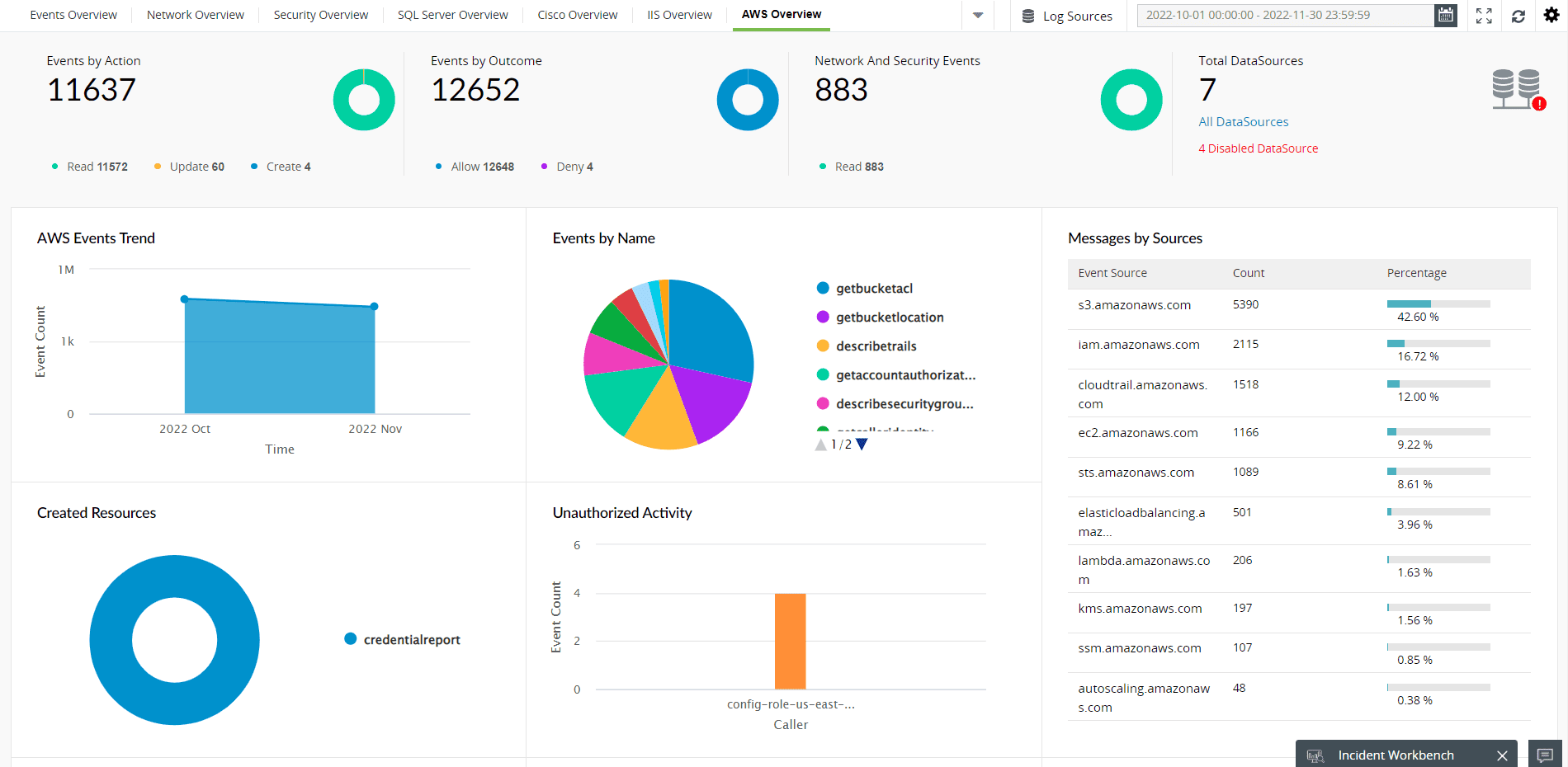
Figure 6: ManageEngine Log360's AWS Overview Dashboards
Ready for the next step?
Explore how you can protect your organization's sensitive information from being misused. Sign up for a personalized demo of ManageEngine Log360, a comprehensive SIEM solution that can help you detect, prioritize, investigate, and respond to security threats.
You can also explore on your own with a free, fully functional 30-day trial of Log360.



