Often, detecting lateral movements is arduous because lateral movement events may look legitimate. This section lists out some of the most common yet impactful lateral movement techniques and how Log360 can detect and remediate them.
Log360 provides a complete picture of all privileged user sessions in the form of an intuitive security analytics dashboard so as to quickly spot privilege escalations. The solution helps you to accurately spot indicators of lateral movements such as process injection, access token manipulation, hijack execution flow, and more. The solution also helps monitor unauthorized logon and access attempts and tracks all user activity in real time.
Pass-the-hash attack is one of the most commonly used lateral movement techniques. Detecting pass-the-hash attacks is difficult, but Log360 uses log analysis and Sysmon analysis to accurately spot successful authentications that happen without passwords. The solution also provides insights such as logon type, remote device from which the pass-the-hash attack happened, and more critical differentiators of this technique.
Spotting a unusual resource access is very difficult if you're only using a rule-based threat detection system. You'll require an AL/ML-based threat detection system to spot lateral movement tactics from legitimate events. Log360 combines both a signature-based threat detection framework that depends on the MITRE ATT&CK® threat model and a machine-learning based anomaly module to detect various lateral movement techniques. Combining the two threat detection frameworks makes Log360 a reliable and accurate tool to detect lateral movement techniques.
Adversaries will try to exploit the remote services or facilitators such as RDP to cause an impactful attack. Since most endpoints support a remote connection, exploiting these remote services will drastically increase the attack surface, allowing intruders to move swiftly across different resources undetected. Log360 captures and alerts you in real time about indicators that could cause potential remote services exploitation. The solution can alert you to potential RDP exploits, RDP logins from local hosts, denied access to remote desktops, and more to help you instantly spot lateral movements.
Log360's powerful machine-learning based user and entity behavior analytics (UEBA) module and signature-based attack detection system helps you to quickly hunt lateral movement techniques.
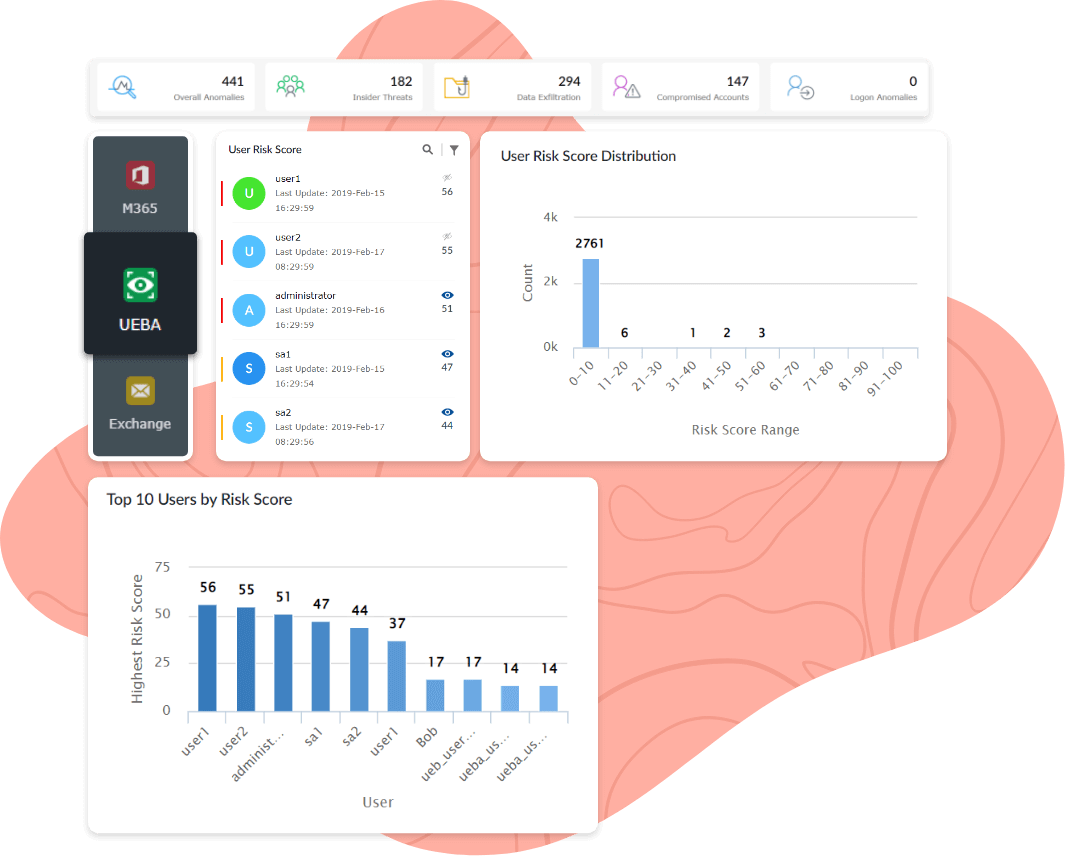
Log360's user entity and behavior analytics (UEBA) employs AI and ML algorithms to identify abnormal patterns in the user and entity behaviors and correspondingly increase the user or system's risk score. The integrated risk management system of this module helps detect slow and sophisticated threats that often go undetected. Spot red flags such as a user accessing a resource or remote desktop for the first time, suspicious permission changes, a remote login from an unusual location or time, and more. These are some of the subtle events that are starting points for lateral movement attacks.
To effectively contain and mitigate lateral movement techniques, Log360 offers you real-time and automated workflow executions. You can associate alerts or correlation rules specific to lateral movement detection with a workflow profile. The solution automatically triggers an alert to help you instantly remediate the threat condition. Further, the solution comes with a case management system to effectively manage security incidents.
Log360's MITRE ATT&CK framework helps detect the various techniques adversaries use to penetrate into the network and move laterally, escalating privileges to evade your defenses. Get a complete picture of all user activities on your network with an intuitive security analytics dashboard and reports to easily spot insider threats, account compromises, and data exfiltration attempts.
Analyze log data by leveraging contextual insights to detect security incidents in your network with advanced threat analytics capability. Log360 allows you to discover malicious IPs, domains, and URLs that try to intrude into your network and helps you take preemptive action against lateral movement attacks.
Log360's SIEM capability helps gain complete visibility into what's happening on your network to quickly alleviate various cyber attacks including lateral movement.
Learn MoreLog360's extensive threat hunting capability helps identify and investigate who did what, when, and from where to trace lateral movement cyber attacks with ease.
Learn MoreThe solution's log forensic capability helps identify the vulnerabilities or loopholes present in the network and helps thwart future attacks.
Learn MoreSOAR helps reduce the load on your IT security team. Replace performing mundane tasks with automated incident response workflows.
Learn MoreLog360 simplifies the auditing process with 150 out-of-the-box, audit-ready compliance reports for PCI DSS, HIPAA, FISMA, SOX, the GDPR, CCPA, and more.
Learn MoreThere are three main stages of a lateral movement attack.
Log360 allows you to correlate logs from various devices with built-in global threat intelligence feeds with over over 600 blacklisted IPs to detect malicious IP addresses, URLs, or domain interactions. Log360's threat intelligence solution allows you to effectively mitigate lateral movement attacks. Integrating UEBA with Zero Trust helps alleviate the harm done by hackers.