Keep track of incidents, correlate them across a time period, and reconstruct
An incident timeline provides the complete history of major incidents with real-time updates. This helps administrators understand the sequence in which an incident unfolds.
With this insight, administrators can strategize defense mechanisms to mitigate similar threats in the future.
Furthermore, incident timelines also help them discern attack patterns and construct correlation rules based on the sequence of events.
Log360 provides a complete overview of the various incidents that happen in your network.
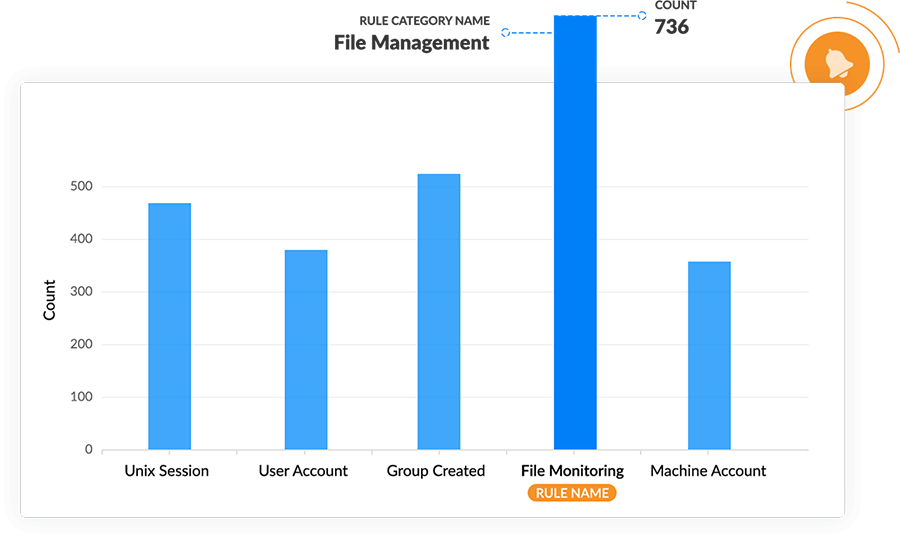
Administrators can get details such as the time, source, and activity for each detected incident.
Log360 generates real-time alerts as soon as an incident is detected. Administrators can make decisions to mitigate the impact of the incident based on its severity.
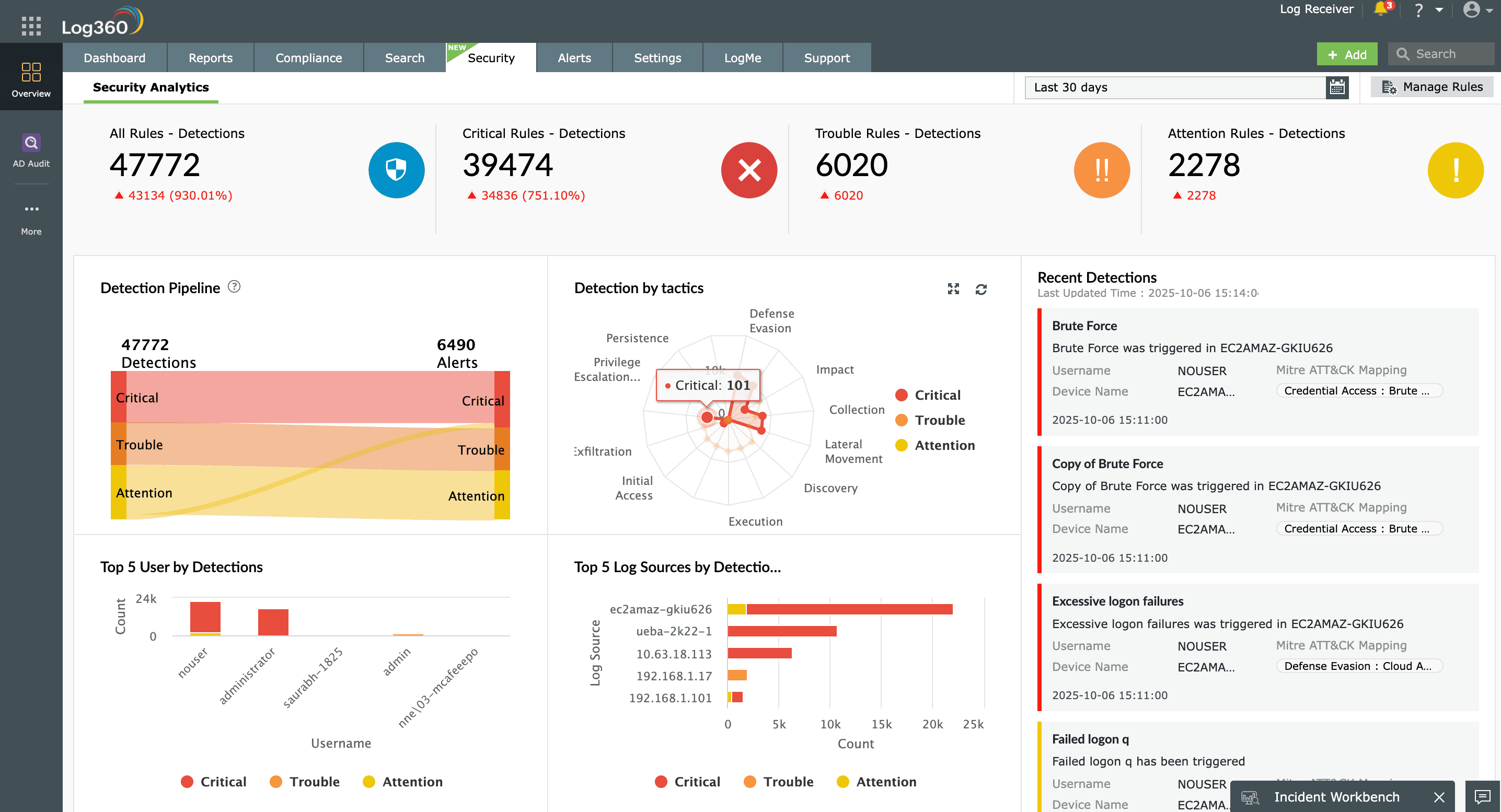
Log360's redesigned detection engine combines behavioral analytics and contextual intelligence to spot evolving threats early. It delivers precise, high-fidelity alerts and helps automate response workflows to contain incidents quickly.
Administrators can link predefined workflows to security alerts and automate standard incident response measures. Log360 uses incident workflows to perform automated incident response, deciding what steps to follow after a security incident..
Log360's security analytics use over 1,200 predefined report and alert profiles and over 30 predefined correlation rules to provide insights into network events.
Log360 identifies malicious entities interacting with networks based on the latest threat intelligence from various threat feeds.