Collect, analyze, and spot suspicious threats throughout your network logs based on indicators of compromise. Log360's out-of-the-box correlation rules, which are tied to the ATT&CK database, help in tracing attackers' movements, like repeated login attempts, unusual account activities, scheduled tasks, changes to registry keys, and data exfiltration patterns. Log360 detects security threats and provides a detailed timeline of incidents with the source, time of the event, device type, severity, and much more.
Advanced threat analytical capabilities help you detect signs of compromise, including unexpected network traffic, unusual system activity, unauthorized user accounts, and malicious activities in your network. Log360 provides you with a complete view of what happened during an event and how it happened. Additionally, the solution has access to international threat feeds like STIX/TAXII and malicious, blacklisted IPs, URLs, and domains. If a malicious IP address tries to establish a remote communication with your network, Log360 quickly spots and stops it, safeguarding your network's sensitive data by comparing it to historical patterns of network activity.
Leverage ML-based UEBA techniques to analyze user behavior within your organization's network. Log360 maps disparate user accounts and related identifiers to build a comprehensive baseline of a user’s behavior. When a user conducts any activity that deviates from the baseline, the solution considers it an anomaly and assigns a risk score based on the severity. One of the key features of Log360 is behavior analytics, which helps you identify patterns that are indicative of malicious activity. Log360 identifies this anomalous user behavior based on time, count, and abnormal patterns, and helps spot insider threats, data exfiltration attempts, privilege escalation, and account compromise.
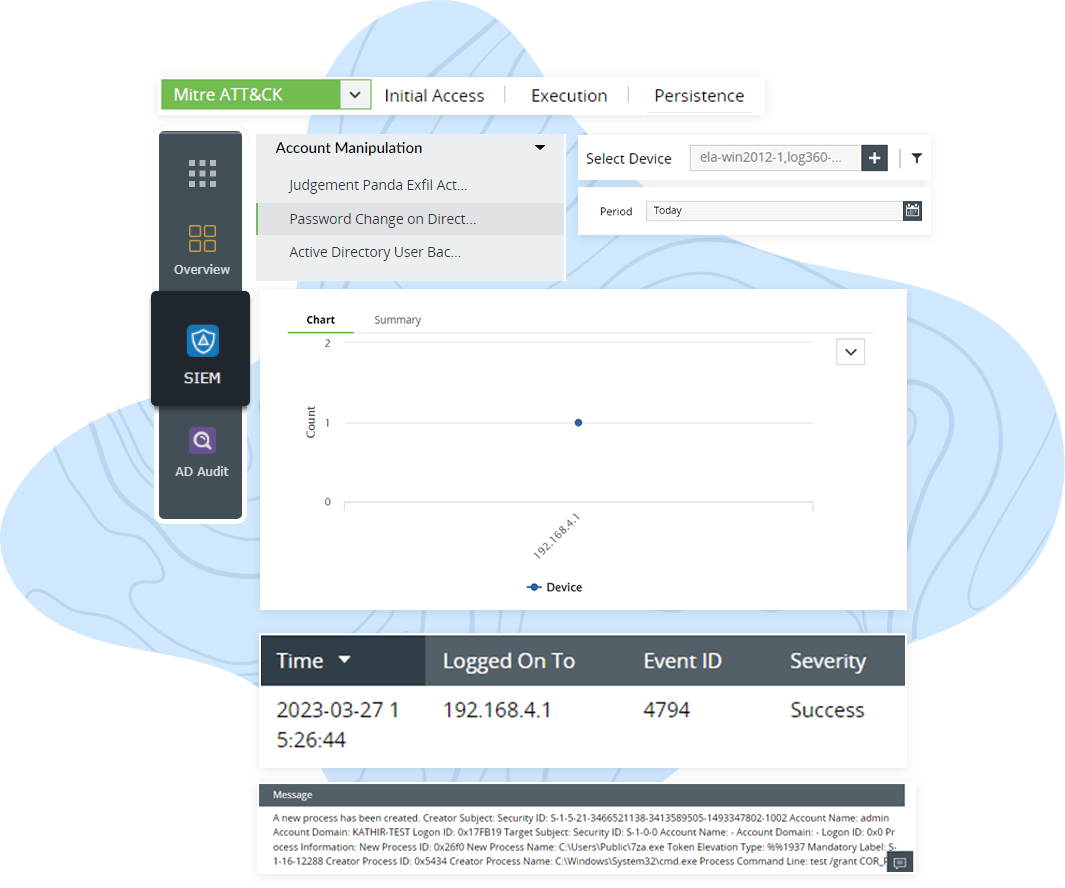
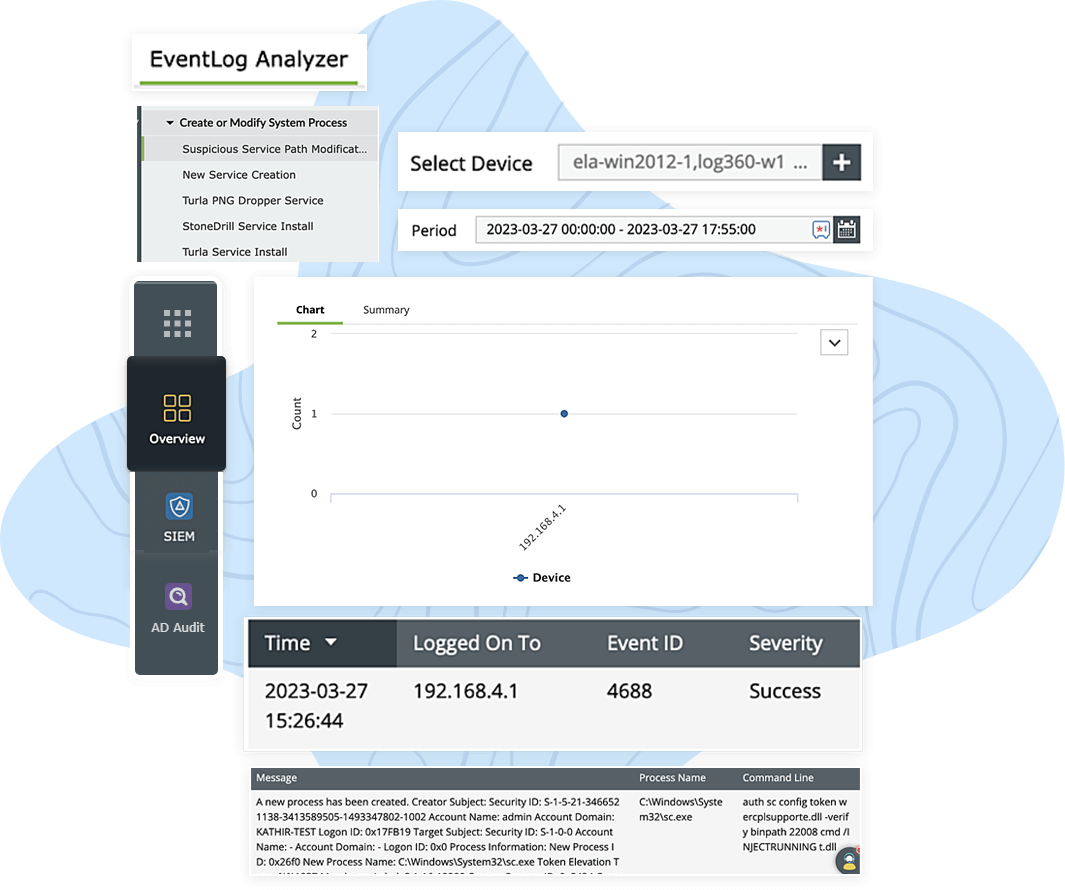
Log360's security analytics dashboard provides holistic visibility into 12 ATT&CK tactics and their corresponding techniques. The analytics-driven security approach keeps you well-informed about high security threats that need your immediate attention to conduct an in-depth investigation. Log360 simplifies the collection and analysis of log data from diverse network devices, endpoints, and security events, all within a single console. Through intuitive graphs and extensive reports, you can effortlessly identify suspicious activities such as account manipulation, BITSAdmin downloads, boot or auto start logon executions, event-triggered executions, suspicious server path modifications, hijacked execution flows, or potential ransomware.
The SOAR capabilities of Log360 send an instant alert to notify the security admin when the system identifies correlation matches or anomalies related to persistence attacks. For instance, Log360 sends an instant alert when a user suddenly starts accessing unusual files or making changes to system settings. These alerts provide actionable information, including details about suspicious activities, affected systems, and recommended response actions.You can also group different technique and tactic alerts into a single, logical incident for an organized investigation.
Log360's intrusion detection system prevents adversaries from evading your security controls. If the solution detects any suspicious activity, it promptly takes actions such as blocking the attacker, isolating the affected system, and notifying the security admin. You can further streamline incident management with automated incident response workflows and assign tickets to security admins for faster incident resolution. You can also define a set of actions to be triggered based on the type of security incidents to proactively mitigate critical threats.
Monitor system logs, events, and network traffic to detect persistence attacks and other cyberattacks as soon as they occur.
Learn MoreDetect rule-based attacks that adversaries often use to enter and control your network.
Learn MoreLeverage Log360's threat intelligence capability to proactively detect and prevent security threats.
Learn MoreSend real-time alerts to the SOC team to expedite effective threat resolution.
Learn MoreMeet stringent compliance requirements with more than 150 ready-to-use audit reports.
Learn MoreMITRE ATT&CK provides an extensive list of persistence techniques used by attackers. Some of these techniques include:
Some best practices to mitigate persistence attacks include: