How to audit and monitor security events in Microsoft Entra ID
It can get difficult monitoring the ever-increasing number of users and the activities they perform across the multiple applications they use. Microsoft Entra ID (formerly Azure Active Directory), a cloud-based IAM solution, offers multiple ways to manage users and track their activities in your Microsoft 365 environment. It also enables you to monitor security events, including sign-in anomalies, app permissions, and service health.
ManageEngine M365 Manager Plus—an extensive tool used for reporting, managing, monitoring, auditing, and creating alerts for critical activities in your Microsoft 365 environments—can also be used for the same purpose, in a more comprehensive, user-friendly way, all under a single console.
In this article, we will see how to audit and monitor security events in Microsoft Entra ID using multiple tools and comprehensively using M365 Manager Plus.
Auditing security events in Microsoft Entra ID
You can audit the activities of your users in Microsoft Entra ID using the Identity logs and Workbooks available under Monitoring & Health. The following table is a list of the reports available there, and what they help you get insights on:
| Settings | Description | Use cases |
|---|---|---|
| Sign-in Logs | Records the details of all sign-in activities by users, applications, and service accounts. |
|
| Audit Logs | Tracks all activities performed on users and resources in your tenant |
|
| Provisioning logs | Tracks user provisioning activities like creation, modification, and deletion across Microsoft Entra ID and integrated applications |
|
| Workbooks | Customizable dashboards that can represent complex logs graphically |
|
| Usage & Insights | A collection of reports on the activity of applications in your tenant. |
|
| Bulk Operations | Records activities performed in bulk, like creation, modification, and deletion. |
|
Monitoring security events in Microsoft Entra ID
You can monitor the security events in Microsoft Entra ID by utilizing the Security logs and Workbooks available under Monitoring & Health. The following table outlines the tools to monitor security events in Microsoft Entra ID and what use cases they serve
| Diagnostic Settings | A setting that you can configure to export logs to tools like Azure Monitor or just store them |
|
| Log Analytics | A data storage solution that can also analyze the logs generated from solutions like Microsoft Entra ID |
|
| Microsoft Sentinel (requires a subscription) | A SIEM solution that can analyze logs, send out event alerts, and automate tasks |
|
All of these tools require you to set up a Log Analytics workspace to use them. Here are the steps to create one.
- Log in to the Azure portal, and search for Log Analytics workspaces in the search box.
- Select Create. You will be redirected to the Create Log Analytics workspace page.
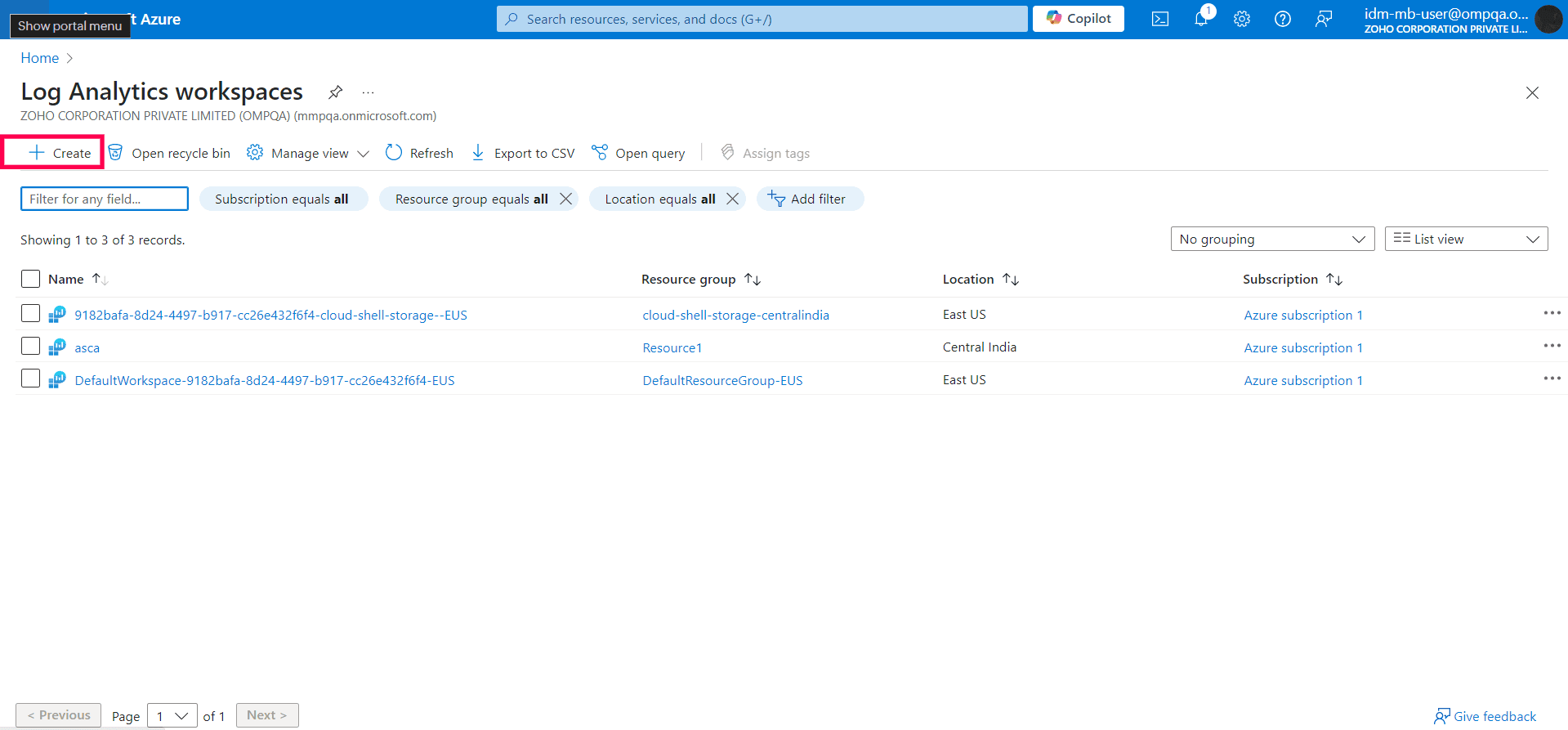
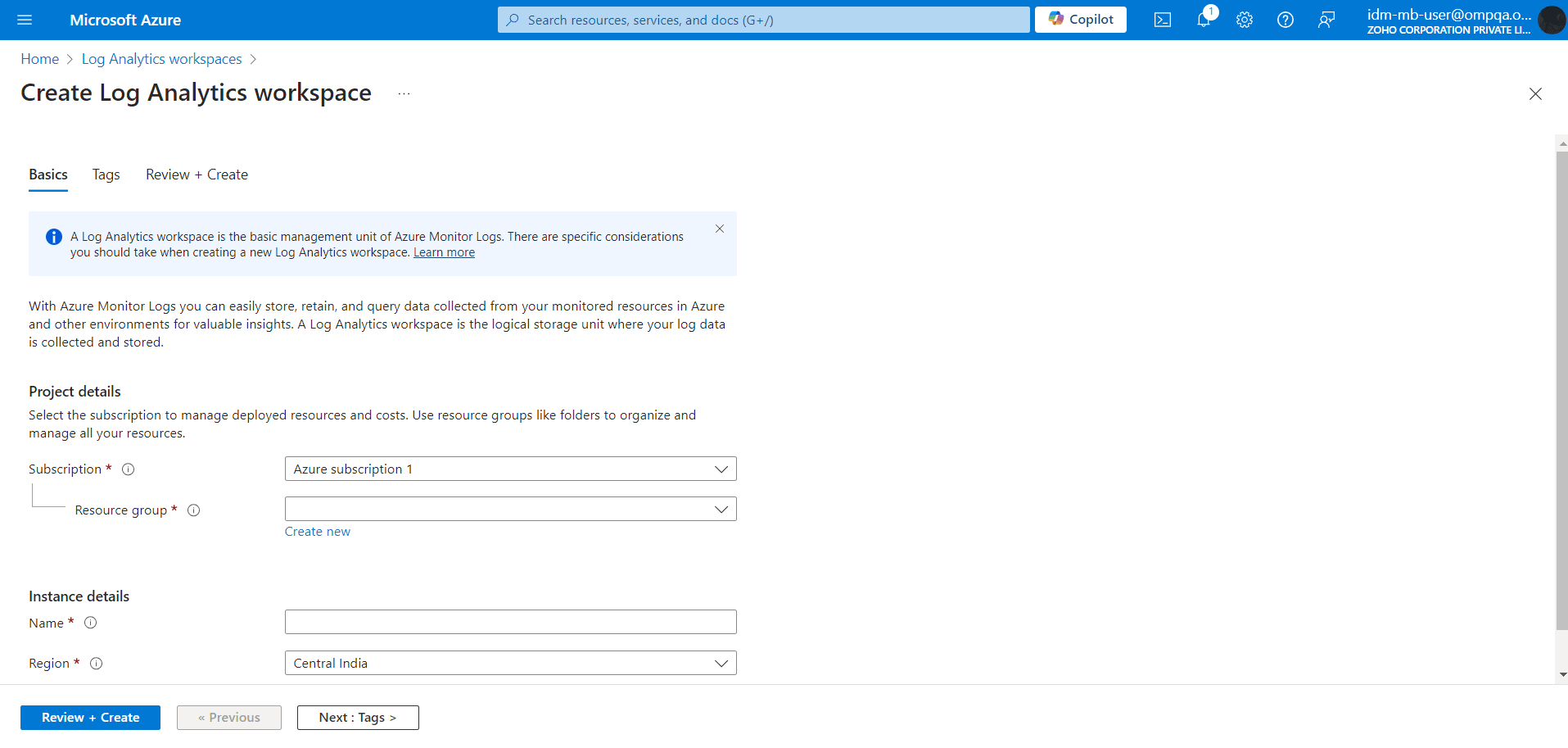
- Select a Subscription from the dropdown.
- You can select an existing Resource Group or create a new one by clicking Create New.
- Fill in the Name and select the Region from the dropdown.
- Click on Next: Tags to assign tags to your workspace. These will help you organize your workspaces based on the data you need. For example, Activity: Add user can be a tag to identify the workspace that you use to analyze user creation.
- Select Review + Create to check your configuration. Then, click Create to create your Log Analytics workspace.
Tracking security events in Microsoft Entra ID using M365 Manager Plus
Although Microsoft Entra ID's native solutions provide a good way to audit and monitor events in your environment, the best part of it is locked behind separate subscriptions and complex configurations. Generating alerts for actions requires the use of Azure Monitor, which needs an additional license. Creating custom dashboards and audit profiles require you to use Kusto Query Language (KQL) in workbooks. Moreover, you will have to jump between multiple admin centers to get all of these working seamlessly.
M365 Manager Plus offers alerts for crucial security events like user creation, group membership changes, and more along with the capability to audit and monitor your Microsoft 365 environment. You can view the generalized steps to create a profile in M365 Manager Plus below.
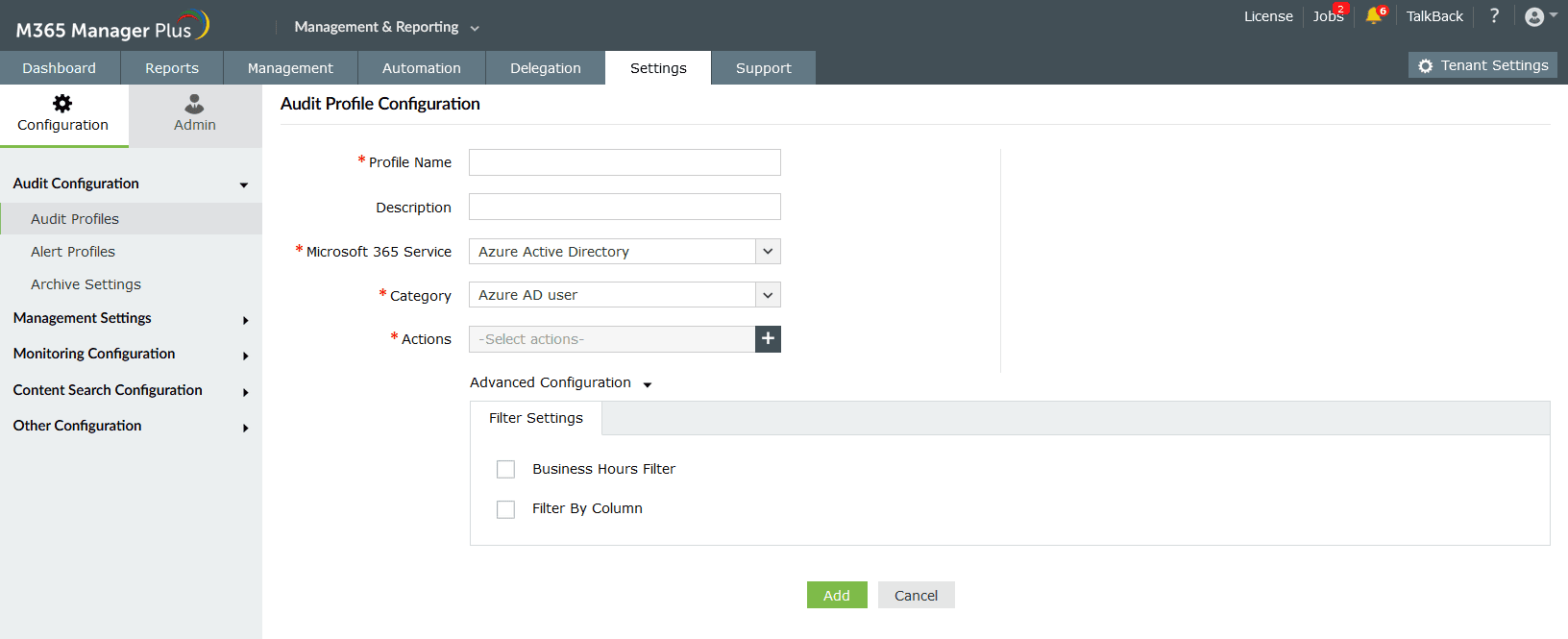
- Log in to M365 Manager Plus, navigate to Settings > Audit Configuration and click Audit Profiles or Alert Profiles. Then, click Add Profile.
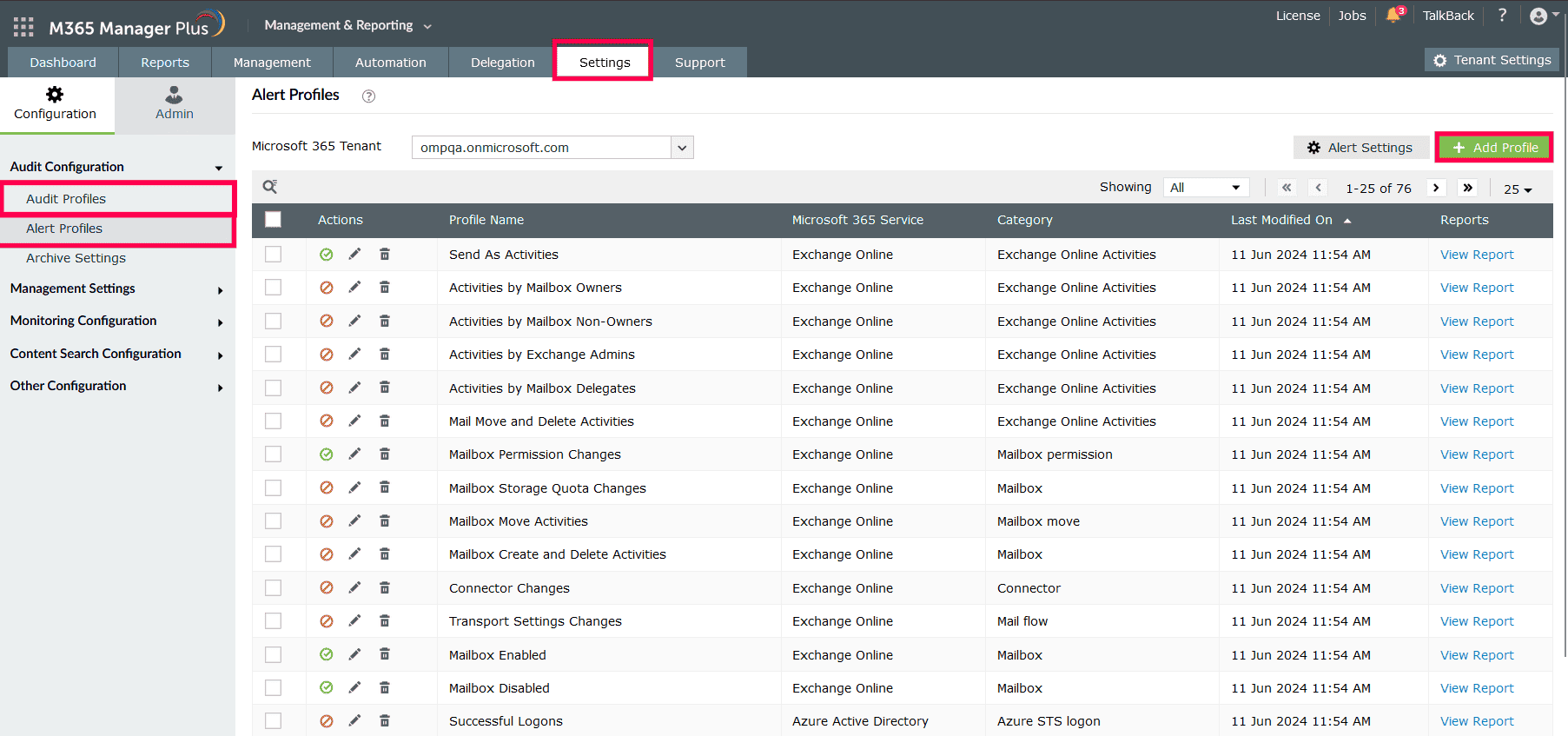
- Type in a Profile Name and Description for your profile.
- Select a Microsoft 365 Service to track, the Category of actions, and select the events you want under Actions:
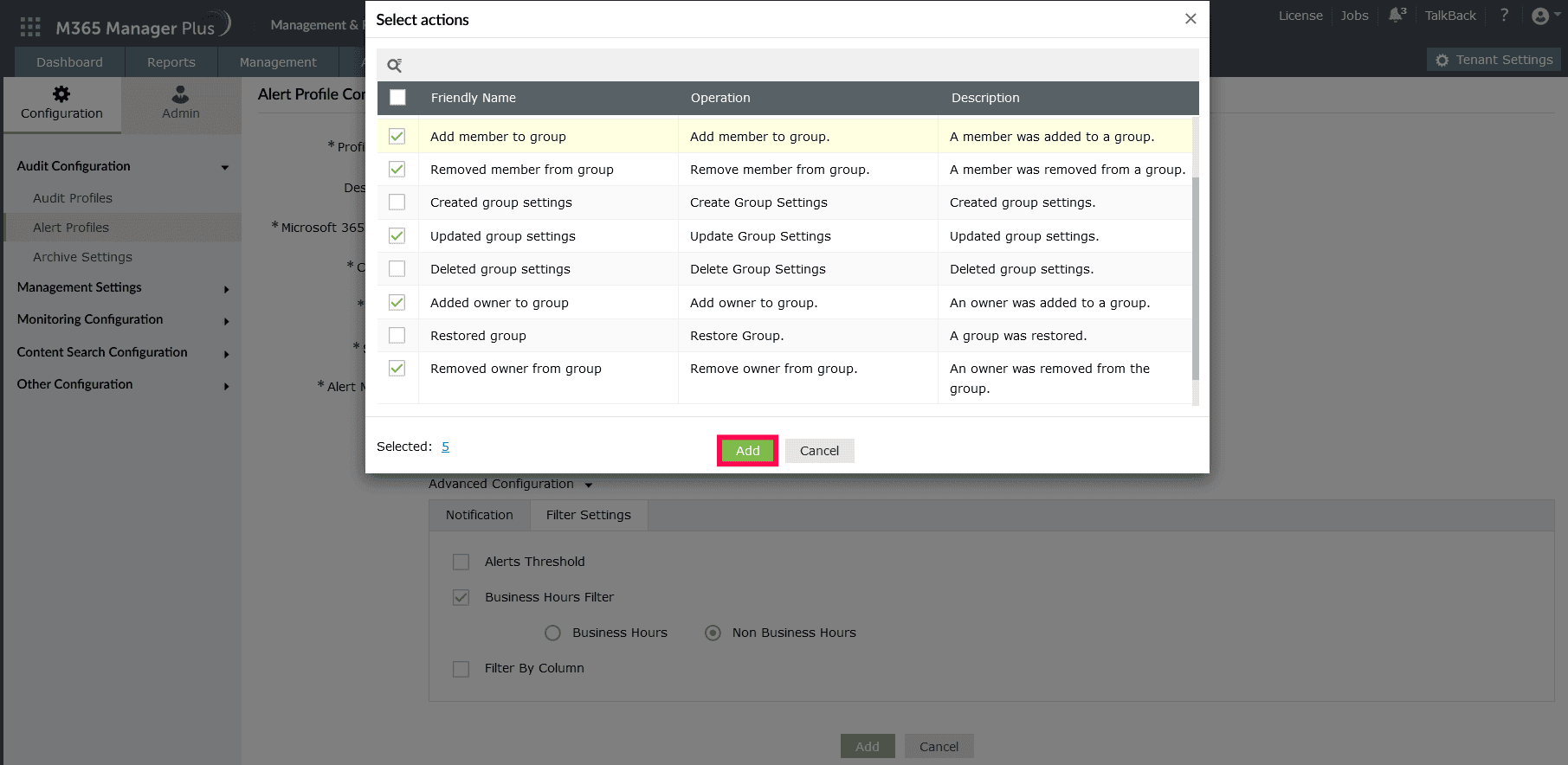
Note:
- For alerts, assign a Severity level based on how crucial this alert is. In the example screenshot below, we've selected Attention.
- Configure a message using Macros to use specific variables in your alert message. For this example, we've used the following message: %OBJECT_ID% modified by %ACTOR%. Activity is %OPERATION%.
- Expand Advanced Configuration and check the email every alert corresponding to this profile box to receive email alerts
- In the Filter Settings tab that appears after expanding Advanced Configuration, use the Business Hours Filter to monitor for any events outside of working hours and the Filter By Column option to format the report data you will receive.
- Click Add to finalize your changes and create a custom profile to monitor your preferred security event in Microsoft Entra ID.
Limitations of using Microsoft 365 native tools to monitor and audit security events in Microsoft Entra ID
- Microsoft Entra ID Premium P2 license and subscriptions to Azure Monitor and Microsoft Sentinel is required to perform some of these actions.
- Administrators must be assigned the required role to access individual native admin centers and carry out tasks in them.
- Reports generated using Microsoft Entra ID can only be exported in CSV and JSON formats.
- Audit logs will have to be filtered every time they are generated, and the filters cannot be saved, which can get exhausting if a filter is required to generate data that you require frequently.
- Assigning granular permissions to execute individual tasks in a broad category is not possible.
Benefits of using M365 Manager Plus to monitor and audit security events in Microsoft Entra ID
- Keep tabs on even the most granular user activities in your Microsoft 365 environment.
- Configure alert profiles in M365 Manager Plus to notify you of specific activities that take place outside of business hours or occur at unusual frequencies.
- Gain a thorough understanding of your environment in Exchange Online, Microsoft Entra ID, SharePoint Online, OneDrive for Business, and other Microsoft 365 services with detailed reports from a single console.
- Filter your reports just once and save them as custom reports that you can access in just a few clicks.
- Export reports generated in M365 Manager Plus in not just CSV, but also in other presentable formats such as HTML, PDF, and XLSX.
- Delegate granular permissions to technicians without elevating their Microsoft 365 privileges and create custom roles with any combination of reporting, management, and auditing tasks.
- Easily manage users, groups, contacts, mailboxes, teams, and sites in bulk without PowerShell scripting.
- Monitor the health and performance of Microsoft 365 features and endpoints around the clock.
Effortlessly schedule and export reports on your Microsoft 365 environment.
Try now for freeStreamline your Microsoft 365 governance and administration with M365 Manager Plus
Get Your Free Trial