How to configure external authentication methods in Microsoft Entra ID
With Microsoft Entra ID being one of the major cloud-based IAM solutions used across organizations, logging in to it securely is a major concern. This is addressed by Microsoft Entra MFA, which offers eight different MFA factors for logging in to Microsoft 365. However, organizations prefer to use MFA solutions they are familiar with to keep their workflows simple and efficient. This is now possible with the introduction of external authentication methods in Microsoft Entra ID.
What are external authentication methods in Microsoft Entra ID?
External authentication methods in Microsoft Entra ID refer to third-party solutions that can authenticate users with their MFA verification flow, without having to rely on an external identity provider to manage the accounts.
Previously, this use case was achieved with the custom controls feature, which redirects you to the external authenticator. However, this uses an external identity provider, which requires the user to create an account with the external authenticator. With the new external authentication flow in Microsoft Entra ID, solely Microsoft Entra ID accounts will be used for the process, eliminating the need for separate accounts to be created in the authenticator.
What can external authentication methods be used for in Microsoft Entra ID?
External authentication methods can be used for the same purposes the native methods in Microsoft Entra MFA are. These include:
- Logging in to Microsoft 365, admin centers, and applications
- Satisfying conditional access policy requirements
- Device registrations
Which external methods are currently supported in Microsoft Entra ID?
The following authentication providers are currently integrated with Microsoft Entra ID and can be used as external authentication methods:
- Cisco Duo
- Entrust Identity
- HYPR Authenticate
- Ping Identity
- RSA
- Silverfort advanced MFA
- Symantec VIP
- Thales STA
- TrustBuilder MFA
What do you need to set up external authentication methods in Microsoft Entra ID?
You will need some values from your external authentication provider to set them up in Microsoft Entra ID. This includes:
- Application ID: A unique ID assigned to your application by your authentication provider. You will need an admin's consent to use this in your organization.
- Client ID: This ID is used to identify your specific application when it requests authentication from Microsoft Entra ID.
- Discovery URL: This is the URL used by the application you log in to that discovers information about the authentication provider’s configuration, like OpenID Connect details.
How to configure external authentication methods in Microsoft Entra ID
Follow the steps given below to integrate an external authentication provider as an authentication factor for Microsoft Entra ID.
- Log in to Microsoft Entra ID with an account that has at least a Privileged Role Administrator role assigned to it.
- Navigate to Identity > Protection > Authentication methods, and select Add external method (Preview).
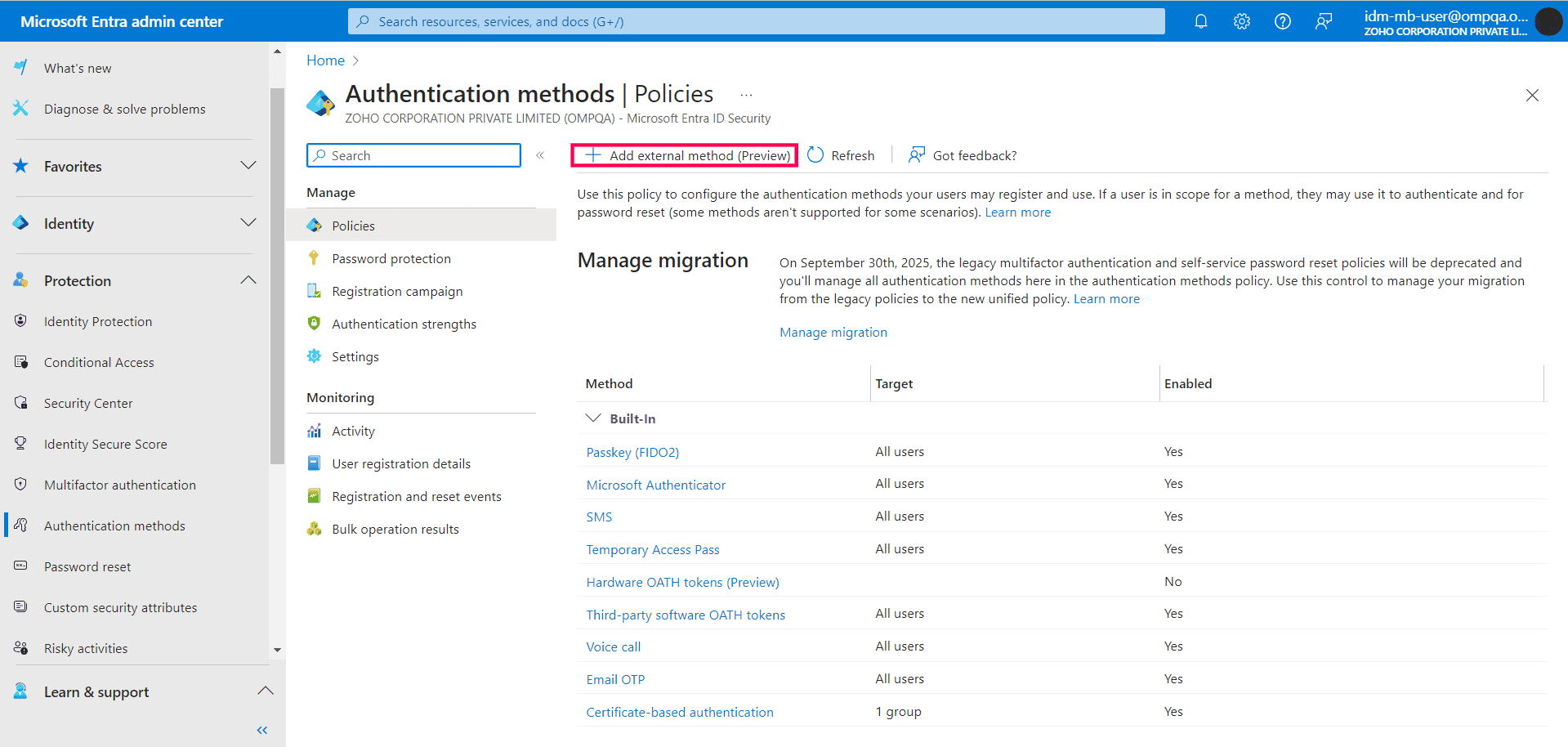
- Enter the Name, Client ID, Discovery Endpoint, and App ID of the authentication method.
- Click Request permission to request an admin's consent to add this authentication method.
- Once admin consent is granted, toggle the Enable field.
- You can add all users or the groups that you want to use the authentication method by adding them using Add Target under the Include tab. You can also exclude users from this method similarly under the Exclude tab.
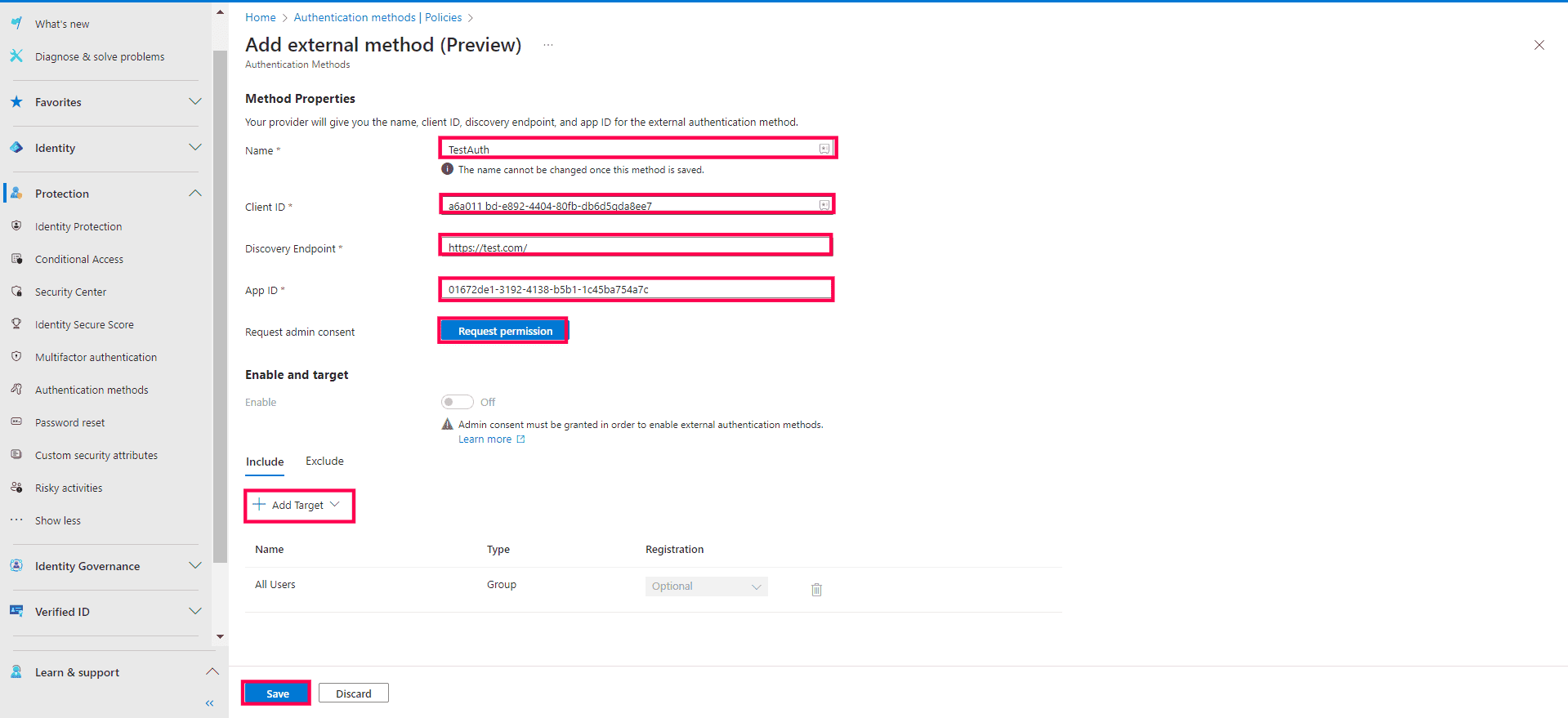
The Add external method page with the details of the external authenticator configured.
ManageEngine M365 Manager Plus is a comprehensive administration and security solution for Microsoft 365 used for reporting, managing, monitoring, auditing, and creating alerts for critical activities in your Microsoft 365 environments. You can gain a thorough understanding of not only your Microsoft Entra ID environment but also Exchange Online, SharePoint Online, OneDrive for Business, and other Microsoft 365 services, with detailed reports and intuitive visualizations, all from a single console.
There are also other benefits to using M365 Manager Plus to manage and monitor your Microsoft 365 environment.
- Filter your reports just once and save them as custom Microsoft Entra ID and Microsoft 365 reports that you can access in just a few clicks.
- Export reports generated in M365 Manager Plus in not just CSV but also other presentable formats, such as HTML, PDF, and XLSX.
- Delegate granular permissions to technicians without elevating their Microsoft 365 privileges and create custom roles with any combination of reporting, management, and auditing tasks.
- Easily manage users, groups, contacts, mailboxes, teams, and sites in bulk without PowerShell scripting.
- Keep tabs on even the most granular user activities in your Microsoft 365 environment.
- Configure alert profiles in M365 Manager Plus to notify you of specific activities that take place outside of business hours or occur at unusual frequencies.
- Monitor the health and performance of Microsoft 365 features and endpoints around the clock.
Effortlessly generate reports and customize dashboards for your Microsoft 365 environment.
Streamline your Microsoft 365 governance and administration with M365 Manager Plus
Get Your Free Trial