Customize ME MDM app
iOS - Security Settings
On Identifying Jailbroken devices
Jailbroken devices give users additional capabilities which render the devices unsafe for enterprise use. To prevent the misuse of critical information, corporate data must be removed from such devices. MDM identifies Jailbroken devices during enrollment and during every scan. Upon detecting a Jailbroken device, the enrollment fails or the device is removed from management if it was previously managed.
Distributing ManageEngine MDM app to managed iOS devices
ManageEngine MDM app is required to detect jail-broken devices, distribute documents, remotely view device screens and track the location of managed devices. The option "Distribute ME MDM app to managed iOS devices" is enabled by default and ensures the ManageEngine MDM app is installed on all managed iOS devices. You can also configure the mail template for distributing the app, if needed. Also, the ManageEngine MDM app can be used for securing E-mail attachments as explained here.
Note: If users have not logged into their iTunes accounts on the devices, the ManageEngine MDM app will be available in the App Catalog. Users should enter their iTunes credentials to complete app installation. Once the ManageEngine MDM app is installed, the App Catalog will be removed from the devices.
Android
To manage Android devices, you need to configure ME MDM app settings. The app is installed in all the managed Android devices.
Note: After enrollment, ME MDM app will be auto approved in Play Store and updated automatically if the default conditions are met.
You can customize the following:
Security Settings
Remove devices when
Admins can use the following settings to ensure that corporate data is removed from devices if the device is compromised by any threat. The devices are checked during enrollment and during every scan. If the devices are found to be non-compliant with the option selected below, the device will be deprovisioned and data will be wiped from the device. If the device is checked during enrollment, the device enrollment will fail.
Rooted
Rooted devices gives users additional controls like removing profiles distributed by MDM or removing the device from MDM management itself. Therefore, organizations must not allow Rooted devices to access the corporate data, as this could lead to a data breach. MDM identifies rooted devices and upon selecting this option removes these devices from management. Removing the device from management also removes the corporate data from the devices.
Basic Integrity Check fails
Android's Basic Integrity Check monitors if the device is Rooted, virtual device or contains a virtual ROM. If any of the above conditions are true, the device fails the Basic Integrity Check. During enrollment, if the device fails Basic Integrity Check, the device will not be enrolled. If an enrolled device fails Basic Integrity Check, the device will be removed from management and the data will be removed from the device.
Google Certification fails
Google certifies devices based on it's Compatibility Testing Suite, which contains basic requirements for Google to certify devices for enterprises. If this option is selected, the devices will be enrolled only if they are certified by Google. Here is an exhaustive list of Google certified devices.
NOTE: Google Certification also checks for the device's Basic Integrity. But when Basic Integrity Check is selected, it is possible for devices to pass the Basic Integrity Check but not be Google certified.
Profile Settings
Every time you distribute a profile with policies and restrictions to some devices, the end user is notified to accept the Policy. This can be customized by specifying a time limit for the end user to accept the policy. If the policy is not installed within the specified time, then the policy is moved to Violated Policies. If the user accepts the policy, then it is moved to Imposed Polices. If Passcode policy has been distributed to the devices and passcode has not been set according to the configured policy by the time specified, then all the apps except the ME MDM app, Settings and the Launcher app are disabled in the device. After the user sets the passcode, the disabled apps would be enabled. This is to protect corporate data when a corporate policy has been violated.
Managing ME MDM app
You can customize the ME MDM app settings by allowing users to remove app, hiding the app from managed devices, etc.
Allowing users to remove ME MDM app
If the user removes ME MDM app from the device, the device becomes unmanaged. This means that the IT Admin can no longer manage the user's device since ME MDM App is mandatory for device management. In case you still want to allow users to remove the ME MDM App, you can also configure a warning, which is displayed whenever the user attempts to remove the ME MDM App. This is not applicable for devices provisioned as Profile Owner(Work Profile).
You can restrict users from removing the ME MDM app. This is supported for Android devices running 5.0 or later versions and the device should be provisioned as Device Owner. For devices enrolled via DEP, users can be restricted from removing ME MDM app as explained here.
Hiding ME MDM app on device
You can choose to hide the ME MDM app on the managed device. In this case, users cannot open ME MDM app to access the App Catalog on the app. Hence, they will not be able to download apps distributed to the App Catalog.
Usually, when a device is unmanaged, the ME MDM app present in the device can be easily removed by the users manually. The data including all profiles and apps is removed automatically. But in some cases, if you remove a device from management when ME MDM app is hidden on a device, the app may not be removed from the device, due to certain server connectivity problems. To avoid such issues, you can consider the following:
NOTE: Hide ME MDM app is not applicable for Samsung devices running 10.0 or later. For these OS versions, it is recommended to enroll via Full Device Management (Device Owner) and Workspace Management (Profile Owner).
Now, use Device Access Recovery Key to disable Device Administrator rights for ME MDM App and then remove it.
Device Access Recovery Key
Revoke Administration Password has been enhanced as Device Access Recovery Key. MDM provides a recovery key to regain access and revoke management on devices that are offline or unresponsive. This key acts as a secure backup when standard authentication methods fail. Follow the steps mentioned below to create a Recovery Key:
- On the MDM console, navigate to Inventory->Devices->Click on the Device Name to open the device details->On the Summary Page->Device Access recovery Key. Click on the Generate Now option to Generate the Recovery key.
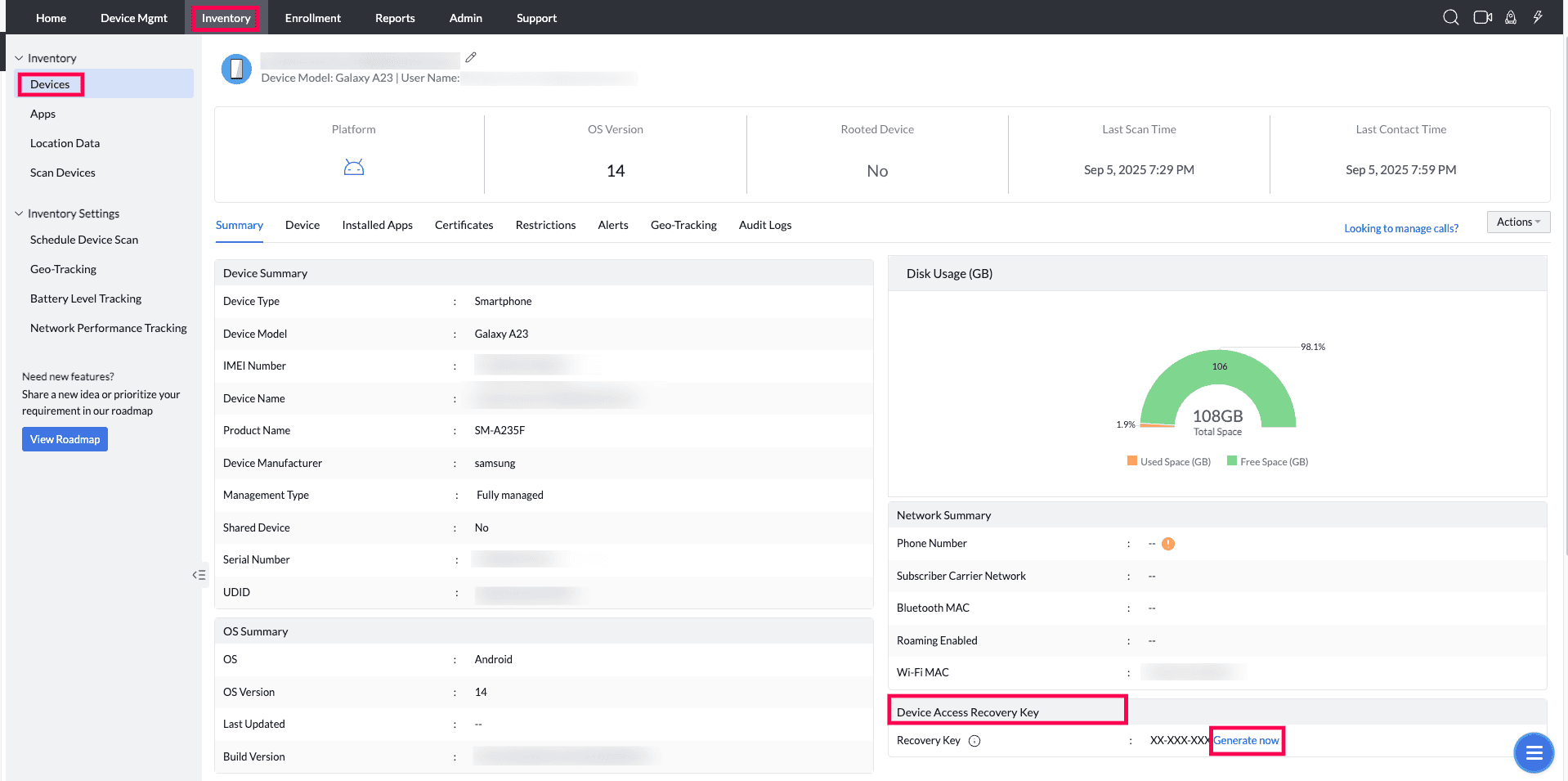
- Select the Recovery Key type and provide the additional details alick "OK" to generate the key.
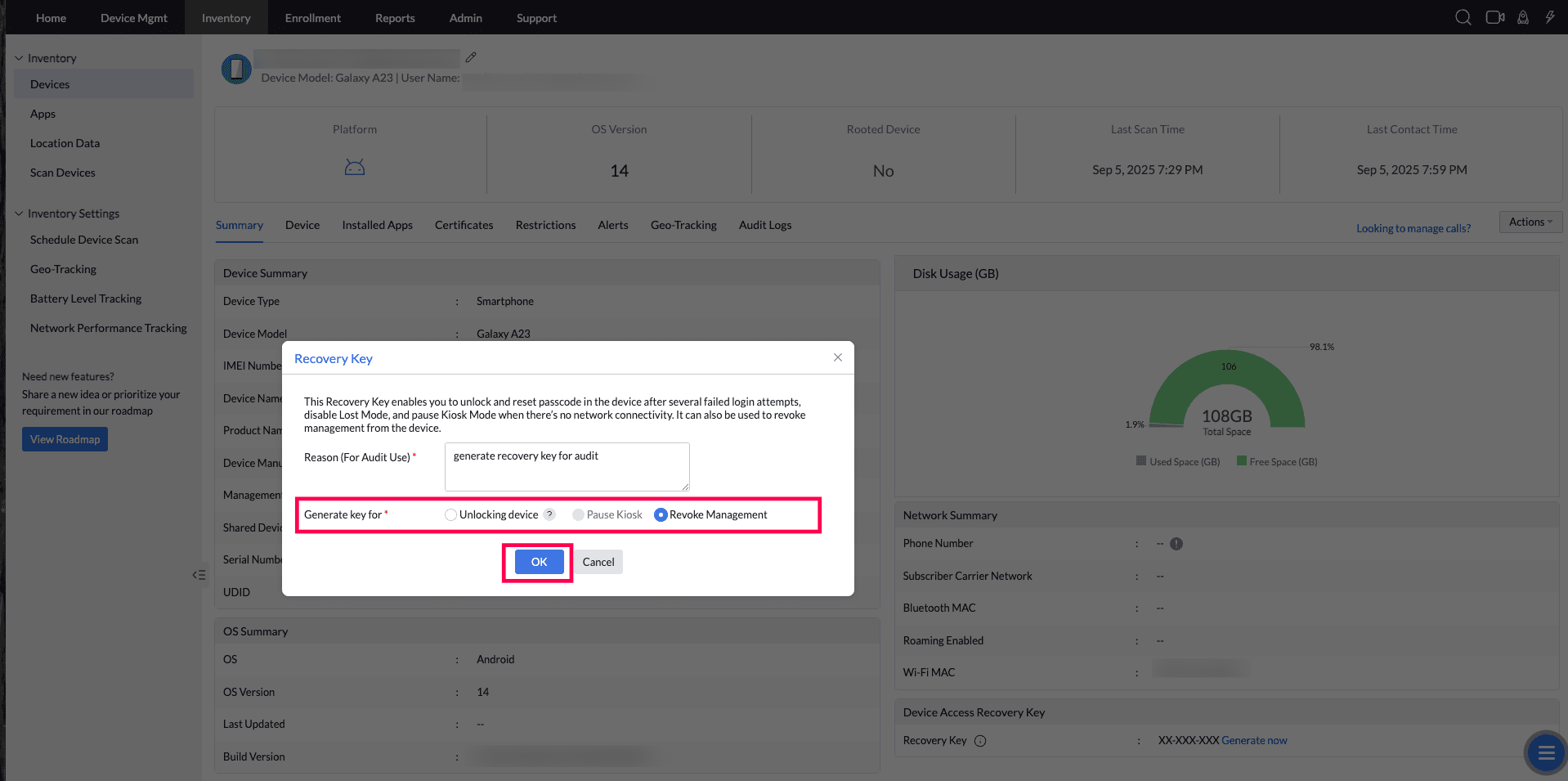
- A Recovery Key will be generated. The generated recovery key remains time-bound and secure. Each key is unique to the device and expires after this period.
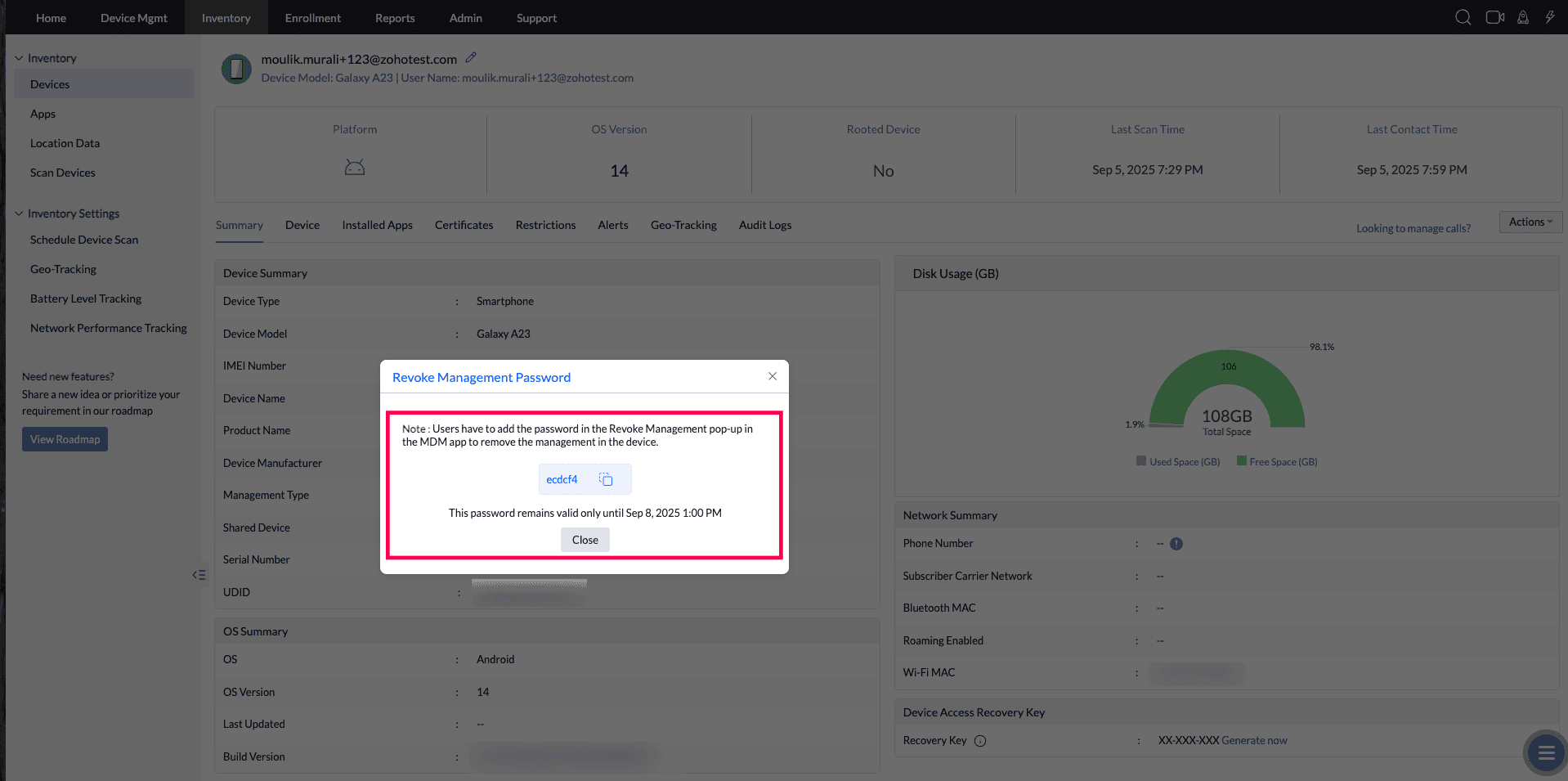
To enter the "Device Recovery Key" on the device, first click on the ME MDM app icon and click four times on the top pane where the app name is visible. A Password Prompt dialog box appears where the password can be entered. For detailed information, visit our Device Access Recovery Key guide. If the ME MDM app is hidden, refer to these steps, to know how to Recovery Key.
Rebranding ME MDM App
If you want to use your enterprise's logo as the icon for ME MDM app or rename the ME MDM app, then you can use this feature. ME MDM app can be re-branded, the display name of the app can be renamed, app icon can be modified and even the startup screen image can be customized. Follow the steps mentioned below to rebrand the ME MDM app:
- On the web console, navigate to the Admin tab and click on Rebranding
- Here you can change the logo displayed on the Server and the website that you need to link.
- To make app-related changes, click on the Enrollment tab and select ME MDM app from Android in the left pane.
- Here you can change the app logo, app name and the app's startup screen.
On Samsung devices, the MDM logo can be customized both on the launcher and within the MDM app. On non-Samsung devices, customization is limited to within the MDM app.
The ME MDM app is now re-branded based on your preferences.
Configuring Mode of Communication
You can choose one of the following modes of communication to enable efficient communication between your MDM server and managed mobile devices.
Immediate Mode
You can choose this mode of communication when you have uninterrupted internet access for server-device communication. All communications between the MDM server and managed mobile devices will occur instantly via Firebase Cloud Messaging(FCM).
On selecting 'Immediate mode', you should choose either Google Play Store or MDM Server to download the ME MDM App which is required during device enrollment.
- It is recommended to download ME MDM app from the Google Play Store.
- You can choose to download ME MDM app directly from MDM Server in circumstances when access to Google Play Store is restricted or when the device is not registered and does not have a Google Account linked to it.
Periodic Mode (Enroll devices within the corporate network/Wi-Fi)
Periodic mode is an alternative to Immediate Mode and is the preferred mode of communication between the MDM server and mobile devices, when there is limited public internet access within your organization, or if there is no access to Google apps and/or services. In this mode the managed mobile devices communicate with MDM Server once every 60 minutes, hence it is not possible to carry out on-demand actions such as remote lock, complete wipe etc. immediately.
On choosing this option, the ME MDM app which is required for device enrollment, can be downloaded by default, only from the MDM Server.
- It is recommended not to switch between Immediate mode and Periodic mode frequently, to avoid problems in communication between the server and managed mobile devices.
- When you switch from Periodic mode to Immediate mode as the preferred mode of communication, it is necessary to check if there is internet access and that the mobile devices are registered with Google i.e., they have a Google Account linked to them.
Download Mode of ME MDM app
As a part of enrollment, every device would have downloaded the ME MDM app. The ME MDM app can be downloaded from the Google Play Store or MDM Server. You can choose to configure the mode by which the download should take place. You can configure this mode by following the steps mentioned below:
- On the web console, click Enrollment
- Under Android click ME MDM app
- Under distribute ME MDM App settings, choose the mode, for the users to download ME MDM App. You can choose to download the App either from the Google Playstore or from MDM Server.
- Click Save Changes
If you choose Periodic mode, you will have to ensure that the server is reachable at port 8020/9020, for the users to initiate download.
You have successfully configured the download mode for ME MDM app.
Windows
Allowing user to delete MDM Workspace account
In case the user no longer requires the device or leaves the organization, it is necessary to remove all your enterprise details from the mobile device. When this option is enabled, users can delete the ME MDM Workspace account on the device.
If you allow users to delete ME MDM Workspace account from the device, the device becomes unmanaged on deleting the account. Hence, it is recommended to disable this option.
Communication Type
You can choose one of the following modes of communication to enable efficient communication between your MDM server and managed mobile devices.
Immediate Mode
You can choose this mode of communication when you have uninterrupted internet access for server-device communication. All communications between MDM server and managed mobile devices will occur instantly via Windows Notification Service (WNS).
Periodic Mode (Enroll devices within the corporate network/Wi-Fi)
Periodic mode is an alternative to Immediate Mode and is the preferred mode of communication between MDM server and mobile devices, when there is limited public internet access within your organization or if the organization has strict security standards. In this mode the managed mobile devices communicate with MDM Server once every 60 minutes, hence it is not possible to carry out on-demand actions such as remote lock, complete wipe etc. immediatelyIn this mode the managed mobile devices communicate with MDM Server once every 60 minutes, hence it is not possible to carry out on-demand actions such as remote lock, complete wipe etc. immediately.
- It is recommended not to switch between Immediate mode and Periodic mode frequently, to avoid problems in communication between the server and managed mobile devices.
- When you switch from Periodic mode to Immediate mode as the preferred mode of communication, it is necessary to check if there is Internet access.
If you allow users to delete ME MDM Workspace account from the device, the device becomes unmanaged on deleting the account. Hence, it is recommended to disable this option.
