Security Management
Mobile Device Manager Plus can be used to remotely secure data in the mobile devices even in the event of the device being lost or missing. The following operations can be done using the security commands in MDM.
To perform actions like sending commands (e.g., Remote Lock) or wiping a device, go to Inventory, select the device, open the Actions menu, choose the desired command (e.g., Remote Lock, Deprovision (Wipe), or Corporate/Complete Wipe), confirm the action, and monitor the status in the Inventory tab.
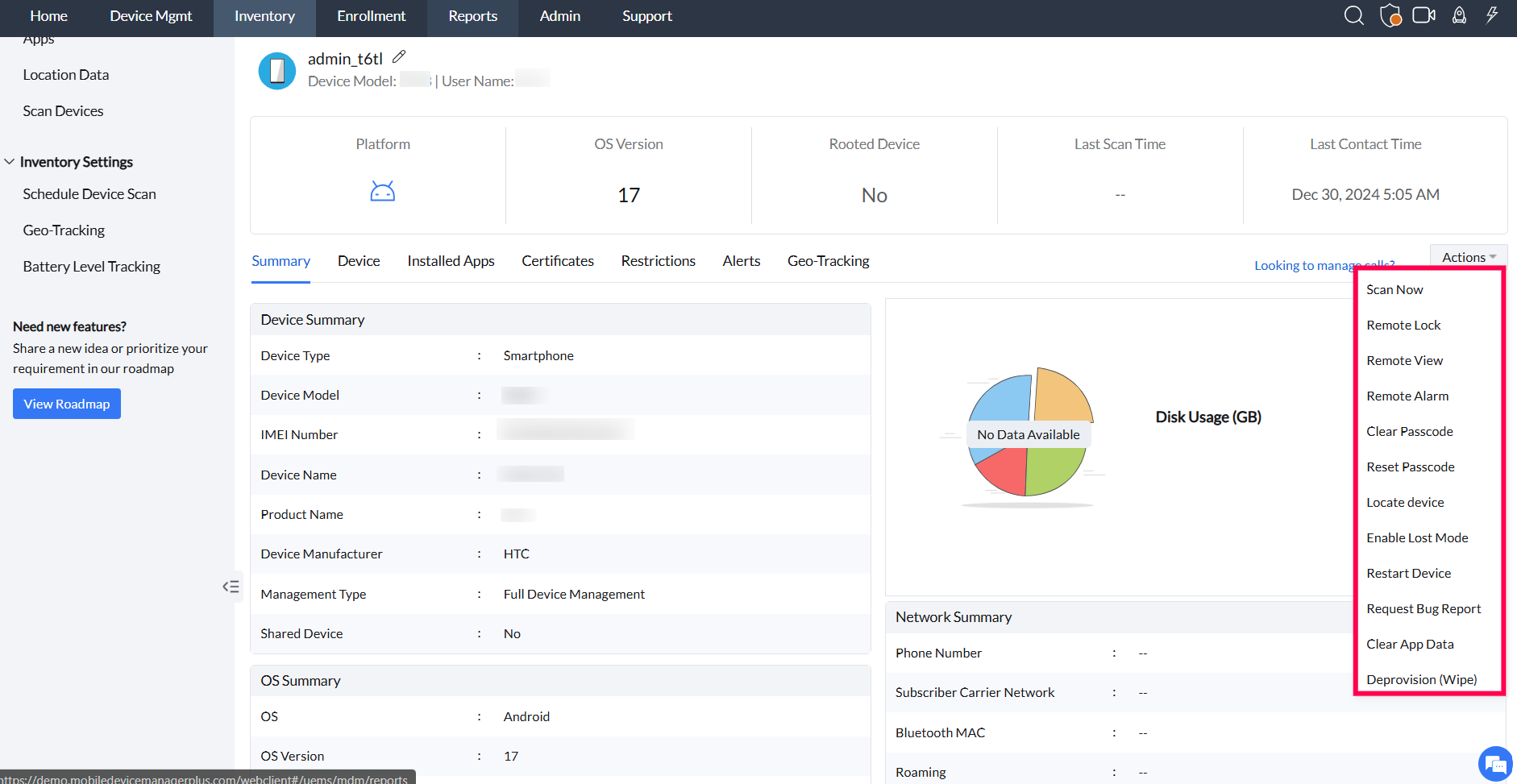
Remote Lock:
You can remotely lock the managed mobile device. After a remote lock is performed, the user is prompted to enter the passcode of the mobile device only if you have set a passcode for the device. This feature is supported for Android, iOS, macOS. In devices running iOS 7 or later versions, you can also specify a message and a contact number while locking the device. The device can be unlocked using the existing passcode. However, for macOS devices, you can only specify a message to be displayed, while locking the device. The existing passcode will be rendered invalid, and the device can be unlocked only using the pin set by the admin.This feature is not supported on Windows devices.
Follow the steps mentioned below to specify a contact number and the message to be displayed on the lock screen of devices running iOS 7 or later:
- On the web console, navigate to Devices.
- Select the device to be locked.
- Under Actions, click on Remote Lock. Enter the contact number and the message to be displayed on the locked screen of the mobile device. You can see the message displayed on the device as shown below.
Scan now:
You can scan the enrolled mobile device to view details about the installed apps, blacklisted apps and restrictions imposed on the device, along with other device details. You can also view the installed apps and the restrictions imposed on the device. The scanning can be performed only when the device is connected to the internet. This feature is supported for Android, iOS, Windows and ChromeOS. If Periodic communication mode is chosen, the scanning operation has a 60-minute communication interval with the server. So, scanning takes place only the next time, when the device interacts with the server.
Remote Alarm:
You can trigger an alarm on the mobile device if it is lost or stolen. It sounds an alarm even if the device is in silent mode. The alarm stops ringing only when the device is unlocked. This feature is applicable for Android, iOS (Supervised) and Windows phones, with iOS requiring Lost Mode to be enabled for Remote Alarm to work.
Note: After enabling Lost Mode on your device, the option to trigger a Remote Alarm will be available under the Inventory Actions of the device.
Complete Wipe:
All the data in the device can be completely wiped, using this command. The device becomes as good as new. You can also wipe all the data from the device's SD card, for Knox devices. This feature is supported for Android, iOS, macOS, ChromeOS and Windows.
Corporate or Selective Wipe:
All the profiles and apps previously installed using MDM are wiped in iOS, macOS and Android devices. In case of Windows devices, only profiles are removed and not the apps. The personal data on the device, is not be affected. Also, the device is no longer managed by MDM.
Note : In EC Inventory, MDM remote actions Corporate Wipe and Complete Wipe will be shown only for Modern Management Devices (MacOS and Windows) but in both standalone and integrated (EC MDM) MDM Inventory, Deprovison action is shown instead of Wipe actions.
Logout User:
This command lets the admin logout the current users on Shared iPads. With this option, the admin can logout users even when they are currently logged in or when iCloud data sync is in progress.
Delete User:
This command lets the admin select the list of users on Shared iPads or Mac and then delete the session for all device users on the devices. With the force deletion option, the admin can delete users even when they are currently logged in or when iCloud data sync is in progress. This feature is applicable for Shared iPads and Mac machines running macOS 10.13 and above.
Note: For Mac machines, the administrator user with a secure token cannot be deleted from the device.
Clearing the passcode:
This command clears the passcode completely. However, the user is prompted to enter a new passcode if a passcode policy was previously associated with the device. Clearing the passcode also clears the biometric-based passcodes in all iOS and Android devices (provisioned as Device Owner) except for Samsung devices running Android 5.0. This feature is not supported for Windows devices.
Reset Passcode:
You can reset the passcode on the managed devices, using this command. If the new passcode does not meet the complexity criteria set for the device or if no passcode was set on the device (using device settings), the user is prompted to set a passcode as per the associated passcode policy. So, it is better to set a password which adheres to the associated passcode policy. This is applicable only for Android devices. Admin can specify the new passcode to be set on the device and choose to send a notification mail to the user.
Note:
- Passcode set by users can not be removed or reset from Samsung devices running Android 9.0 or above, enrolled via invite. OS-specific details on Clear and Reset passcode commands are provided in the table below.
- For devices running Android 14.0 and above, the minimum passcode length should be 6.
Clear Screentime Passcode
In some cases, admins need to remotely clear the screen time passcode for troubleshooting purposes. This is applicable only for Supervised iOS devices.
- In 11.0 and earlier version, this action will remove screen time passcode restrictions and other constraints it holds.
- From iOS 12.0 and above, if the Screen Time passcode and Share Across Devices setting is enabled, then this command clears the Screen Time passcode and its restrictions. If the user is a child in the iCloud family, then this command fails. Otherwise, if the Share Across Devices setting is disabled, then this command will clear only the Screen Time Passcode and not the other restrictions with it.
With MDM, you can enable/disable users from configuring screen time restrictions on the device.
Device Access Recovery Key:
If a managed device is locked due to incorrect passwords, you can either perform Clear Passcode or generate a Device Access Recovery Key to unlock the device. Incase of no network connectivity, you can generate a Recovery Key and unlock your device. It is supported for Android devices enrolled as Device Owner. Once you have exhausted half the maximum number of failed attempts (in passcode policy), you will be redirected to the recovery key page. For example, a value of 6 specifies that the device will be locked after 3 failed login attempts and users can unlock the device using the recovery key. After 6 failed login attempts the data in device will be completely wiped. To know more about how to generate Device Access Recovery Key, click here.
Pause Kiosk:
The Pause command lets you pause Kiosk on devices which have been previously provisioned with Kiosk. This command is usually used on devices facing issues and the IT admin needs to troubleshoot the same. You can choose to have the Kiosk automatically resumed after some time by specifying the same. This can be done using the Resume Kiosk command. You can also pause Kiosk using other methods as listed here. This is currently supported only for Android devices.
Resume Kiosk:
If a device provisioned as Kiosk is paused, the Resume command can be executed to restore the device to Kiosk. Similar to Pause Kiosk, you can choose to resume Kiosk using other methods as listed here. This is currently supported only for Android devices.
MDM supports pausing Kiosk and resuming Kiosk using different methods. For example, you can pause Kiosk using remote chat commands and resume it using security commands.
Enable Lost Mode:
This command is used to mark devices as lost and initiate Lost Mode on the devices.
Before enabling Lost Mode on certain devices, it is crucial to be aware of the potential failures which may occur in rare cases in the process of disabling it. As outlined in Apple's Protocol document, attempts to deactivate Lost Mode may encounter failures for unspecified reasons. This warning highlights the importance of considering that unsuccessful attempts to execute the disable Lost Mode command could lead to the device being persistently stuck in Lost Mode.
Note: But in the case of devices with no sim cards such as iPads when the device is in lost mode and is restarted then the Wi-Fi connectivity is lost and the device is locked. To avoid this, it is suggested to clear the passcode on the devices after successfully enabling lost mode on the device but before restarting the device.
Restart:
Remote Restart is applicable only for the following devices.
- Supervised iOS devices running on iOS 10.3 or above
- Samsung or non-Samsung devices running 7.0 or later, provisioned as Device Owner
- macOS devices
- Windows devices
- Chrome OS devices provisioned in Kiosk Mode.
NOTE:
- Remote Restart and Remote Shutdown can also be scheduled on devices. You can choose a date and time and which these actions should take place on the devices. Especially for environments with kiosk or unattended devices, scheduling these actions simplifies device maintenance for IT admins. Watch this video to learn how to schedule device actions.
- On Windows devices, the command is implemented only after 5 minutes from the time the command was acknowledged by the device.
- On Chrome devices, the command will expire if the device does not contact the MDM server within 10 minutes of initiating the command on the device.
- In case of Apple devices (iOS and macOS), a password-protected device must be unlocked after successfully executing a Remote Restart command to ensure the device can connect to a Wi-Fi network. This is essential to ensure continued management of the device upon restarting it.
- macOS devices also provide an option to notify the user to restart the device.
- For detailed steps on on how to configure a schedule for Remote Restart and Remote Shutdown, refer to this document.
Wipe Users
This command is used to wipe out all the users and user profiles from the device. Applicable only for Chrome devices.
Take Screenshot
You can execute 'Take Screenshot' command to take a screenshot on Chrome devices provisioned in Kiosk mode. This command will expire if the device didn't contact the MDM server within 10 minutes. All the screenshots will be recorded under Device Files (Inventory > Devices > System Activity). To view these screenshot file, you have to sign in to the Google Admin Console.
Set Volume
This command is used to set the volume level on the kiosk devices remotely. This command will expire if the device didn't contact the MDM server in 10 minutes. Applicable only for Chrome devices.
Recover User Account:
When a device is locked after exceeding maximum number of failed attempts in Passcode (varies according to the configuration of associated profile), the user gets locked out of the account. Then, the account can be remotely unlocked by selecting Recover User Account and entering the user account details, so that user can try logging in again. Supported by MDM for macOS 10.13 and above.
Only devices running Android 5.0 or above can be provisioned as Profile Owner or Device Owner.
| ANDROID OS VERSION | DESCRIPTION |
ENROLLED USING INVITES
|
DEVICE OWNER USING ADMIN ENROLLMENT | ||
|---|---|---|---|---|---|
| SAMSUNG | PROFILE OWNER | CORE ANDROID | |||
| Clear Passcode | |||||
| Below Android 5.0 | Passcode applied to the work profile in a Profile Owner provisioned device and the device passcode in a Device Owner provisioned device cannot be cleared. |  |
 |
 |
 |
| Android 5.0 and 6.0 | Passcode applied to the work profile in a Profile Owner provisioned device cannot be cleared. |  |
 |
 |
 |
| Android 7.0 | Passcode applied to a device provisioned as Device Owner and the work profile passcode in a Profile Owner provisioned device can be cleared. |  |
 |
 |
 |
| Android 8.0 and above | Passcode can be cleared in Samsung devices provisioned as Device Owner and the work profile in Profile Owner provisioned devices. |  |
 |
 |
 |
| Reset Passcode | |||||
| Below Android 5.0 | Passcode applied to the work profile in a Profile Owner provisioned device and the device passcode in a Device Owner provisioned device cannot be reset. |  |
 |
 |
 |
| Android 5.0 and 6.0 | Passcode applied to the work profile in a Profile Owner provisioned device cannot be reset. |  |
 |
 |
 |
| Android 7.0 | Passcode applied to a device provisioned as Device Owner and the work profile passcode in a Profile Owner provisioned device can be reset. |  |
 |
 |
 |
| Android 8.0 and above | Passcode can be reset in Samsung devices provisioned as Device Owner and the work profile in Profile Owner provisioned devices. |  |
 |
 |
 |
For Knox, security commands can be executed separately for the device and the container. The container-specific security commands are explained below:
- Create Container:You can select this command to distribute Knox License and create a Knox Container within a Knox supported device for advanced management activities.
- Remove Container:The Knox Container created in the device can be removed by executing this command. This also revokes the Knox license distributed to the device.
- Lock Container:You can lock the Knox Container and restrict the user's entry into the container for security reasons.
- Unlock Container:You can execute this command to unlock the already locked container. This permits users to access the Knox Container.
- Clear Passcode:You can clear the passcode of the Knox Container, using this command. The user is then prompted to set a new passcode, adhering to the complexity criteria set for the container.
Follow the steps mentioned below to use security commands using Mobile Device Manager Plus.
- On the web console, navigate to Devices under the Inventory tab.
- Click on the specific device under Device Name.
- Click on the Action Button which is located on the right side, and select the action to be performed. Due to security reasons, you are prompted to enter your password to authenticate the action to be performed.
- Specified Security command is executed and the status is reported under Device Details.
Troubleshooting Tips
Issue: This Mac is Locked. Try again in 24,284,826 minutes.
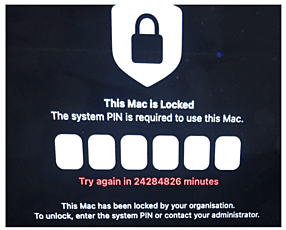
Cause: The Mac was MDM-locked and left powered on. While in storage, its battery drained completely. After the full drain and restart, the Mac’s system clock reset to Epoch time, (00:00:00 UTC, January 1, 1970).
Solution:
- Establish a stable network connection by connecting the device directly to the corporate network via Ethernet.
- Allow the device 30 minutes of uninterrupted uptime while connected.
- Perform a full restart of the macOS device. Verify the device successfully unlocks.
