ManageEngine® PAM360 FAQ
General
Web Interface and Authentication
Security
Password Synchronization
Backup and Disaster Recovery
Licensing
SSH Key Management
SSL Certificate Management
General
1. Do I need to install any prerequisite software before using PAM360?
Apart from the standard system requirements (both hardware and software), the following elements are essential for the proper functioning of the PAM360 server.
These are especially required if you are planning to make use of PAM360's account discovery and password reset provisions.
- An external mail server (SMTP server)for the functioning of PAM360 server and to send various notifications to users.
- A service account [OR] a gMSA that has either domain admin rights or local admin rights in the PAM360 server and in the target systems that you would like to manage.
- Visual C++ Redistributable for Visual Studio 2015 and above (for PAM360's Account Discovery and Password Reset features.)
- Microsoft .NET framework 4.5.2 or above must be installed in the server where PAM360 is installed.
To check if these software requirements are configured:
Go to Support » Software Requirements and click Check Configuration.
In the pop-up box that opens, the configuration status will be displayed.
2. What are the operating systems supported by PAM360?
PAM360 supports the following flavors of Windows and Linux operating systems:
| Windows | Linux |
|---|---|
| Windows Server 2019 | Ubuntu 9.x and above |
| Windows Server 2016 | CentOS 4.4 and above |
| Windows Server 2012 R2 | Red Hat Linux 9.0 |
| Windows Server 2012 | Red Hat Enterprise Linux 7.x |
| Windows 10 | Red Hat Enterprise Linux 6.x |
| Windows 8 | Red Hat Enterprise Linux 5.x |
3. Can others see the resources added by me?
Except for super administrators (if configured in your PAM360 set up), no one including admin users, will be able to see the resources added by you. However, if you share your resources with other administrators, they will be able to see them.
4. Can I add my own attributes to PAM360 resources?
Yes, you can extend the attributes of the PAM360 resource and user account to include details that are specific to your needs. Refer this document for more details.
5. What happens if a user leaves the organization without sharing their sensitive passwords with anyone?
If an administrative user leaves the organization, they can transfer the resources they own to other administrators. By doing so, they'll have no access to those resources themselves, unless they transfer the resources to themselves. Refer this document for more details.
6. How to add a new Active Directory (AD) domain in PAM360?
Administrators can add new domains for both resource discovery and user discovery operations. Follow the below steps for resource discovery:
- Go to the Resource tab and click Discover Resources.
- Here you can click New Domain beside the Enter Domain Name field and add a new domain name.
Refer to this help section for detailed instructions.
To add a new domain for user discovery:
- Go to the Admin tab and click Authentication >> Active Directory.
- Here you can click New Domain beside the Enter Domain Name field and add a new domain name.
Refer to this help section for detailed instructions.
7. How to remove a domain from PAM360?
To remove a domain from PAM360, you first need to remove the users that belong to this domain. Once the users are removed, follow the below steps to remove the domain information:
- Go to the Admin tab and click Authentication >> Active Directory.
- Here, click the View Synchronization Schedules option.
- Delete the required domain from the Domains pane on the left.
8. How to fix the errors “The list of Groups is too large to display ” and "The list of OUs is too large to display" while importing from AD?
To fix these errors, you need to increase the number of OUs and groups allowed during the AD import. Follow the below steps:
- Stop the PAM360 service.
- Take a backup of the system_properties.conf file present inside
\conf directory. - Now, open the system_properties.conf in the Word Pad with admin permission and edit the following values:
- Search for domain.ou.limit=2500 and change the value to 25000.
- Search for domain.group.limit=2500 and change the value to 25000.
- Save the file and restart the PAM360 service.
9. How can I edit the properties of an existing scheduled task, such as changing the time or the frequency?
You can modify the time interval for AD synchronization by following the below steps. To create a new task or edit the existing scheduled tasks, follow the below steps:
- Log in as an administrator and go to the Groups tab.
- Click the Actions icon available beside the resource group and select Periodic Account Discovery from the drop down.
- In the pop-up that comes up, schedule or modify the time interval for AD synchronization.
10. Can an AD sync job be set to occur multiple times a day, such as once every 4 hours?
Configuring a schedule to run every 4 hours must be done when you import the OU/Group from AD.
To import, go to Resources >> Discover Resources >> Import. Here, specify the synchronization interval as per your requirement and import.
11. How to fix the “PAM360 detected harmful content in the data entered by the user and aborted the operation" error occurred while importing resources through a csv/tsv file?
As a security measure, PAM360 to restricts certain characters such HTML tags (< , >), "URL: HTTPS://" or "URL: HTTP://", security mark (?), end line and multiple spaces in the notes or any other field in PAM360 to avoid causing security violations in the product.
If any of these characters are used in any other fields except the password field, then it causes a violation and the import fails.
To avoid this, verify your CSV/TSV file to ensure these characters are removed for a successful import.
12. How do I troubleshoot if importing users/resources from AD fails?
Verify the following:
- Check if the user credentials are correct.
- If you are trying with an admin user and it fails, try entering the credentials of a non-admin user. This is just to verify if connection could be established properly.
If the above verifications fail, please contact pam360-support@manageengine.com.
13. Can I run custom queries to generate results for integration with other reporting systems?
Yes, you can. Please contact our support with your specific request and we will help you with the relevant SQL query to generate XML output.
14. Does domain SSO work across firewalls / VPNs?
The domain Single Sign On (Windows-integrated authentication) is achieved in the Windows environment by setting non-standard parameters in the HTTP header, which are usually stripped off by devices like firewalls / VPNs. PAM360 is designed for use within the network. So, if you have users connecting from outside the network, you cannot have SSO enabled.
15. Can I rebrand PAM360 with my own logo and organizational information?
Yes. PAM360 provides you with the following options for customization and rebranding:
- Using your own logo for web interface the mobile app. (Recommended image size is 210*50 pixels)
- Setting a login page description for the product.
- Changing the default color of the user interface.
- Displaying a banner with customized legal content.
- Customizing a privacy policy content and display an acceptance button for the same.
To carry out the above functionalities:
- Navigate to Admin >> Customization >> Rebrand.
- Under the Logo and Theme section, set up a customized logo and a login page description, and change the default skin tone.
- Under Login Page Text, add policies and/or legal conditions to be displayed in the login page.
Note that at any point, this configuration can be disabled. Know how.
16. Does PAM360 record Password viewing attempts and retrievals by users?
Yes, PAM360 records all operations that can be possibly performed by an user- including password viewing and copying operations. From audit trails, you can get a comprehensive list of all the actions and attempts by the users with password retrieval. Know more
17. Why does the size of PostgreSQL wal_archive file increase at a rapid pace?
This issue occurs when the backup location specified in PAM360 is no longer accessible to save the backup file. In simple terms, whenever the PostgreSQL database backup fails, wal_archive folder size will start increasing.
Solution:
- Check if there is enough disk space available on the PAM360 drive.
- If not, remove the logs directory and a few files present inside directory.
- You need to have only one or two backups to be present here.
- Login to PAM360 and navigate to Admin >> Configuration >> Database Backup.
- Click on the 'Backup Now' button.
This will trigger an instant backup and automatically purge the wal_archive directory.
18. Does PAM360 support High Availability?
Yes, refer the High Availability document for more details.
19. What are the various Syslog formats followed by PAM360?
The following are three different types of syslog formats that PAM360 uses to send syslog messages to your syslog collector host:
i. Resource Audit
ii. User Audit
iii. Key Audits
SSH: <190> Key_Name:172.21.147.130_test123_id Days_Exceeded:0 Modified_On:2016-02-16 17:41:24.008
20. Does PAM360 alter the number of Windows CAL licenses?
Generally, RDP sessions are invoked from the PAM360 server and relayed to the end user's browser through a third-party component called Spark Gateway. This component comes bundled with PAM360 and does not have any relation to Windows CAL licenses. Hence, PAM360 does not affect the number of Windows CAL licenses in any way. Users need to purchase as many CAL licenses, as suggested by Microsoft.
21. How do I run the PAM360 service using a group Managed Service Account (gMSA)?
To know in detail about running the PAM360 service using a group Managed Service Account, click here.
22. How do I fix the PostgreSQL server start-up failure?
Error Scenarios:
During Upgrade:
'Trying to start PostgresSQL server failed' error in the command prompt after choosing the PPM file.
While setting up HA:
'Trying to start PostgresSQL server failed' error in the command prompt after executing the HASetup.bat command.
During Service Start up:
- PAM360 service start failure after the upgrade.
- PAM360 service start failure after updating the PAM360 service account in Services console.
For the above two cases, do the following:
Open the <PAM360-HOME>\logs\wrapper file with notepad/Notepad++ and move to the very bottom of the file (i.e. most recent time frame) and check if we get the 'Trying to start PostgresSQL server failed' error.
Possible Causes:
The following causes are explained with respect to the above error scenarios:
The 'Trying to start PostgresSQL server failed' error occurs when,
- PAM360 is unable to access few sub-folders inside PAM360 (i.e appropriate permission not given).
- The PostgreSQL DB fails to start because of a background process that was not terminated properly.
- The instant DB port might be occupied by a different process.
Solution:
The solution given below applies to all the above error scenarios. To fix this issue, follow the below steps to provide permission,
- Start the Task Manager and kill all Postgres process (make sure "show process from all users" is selected - For PAM360).
- Update the PAM360 service with a privileged account in the services console.
- Open command prompt using administrator and execute the below query:
- icacls "installation path" /q /c /t /grant Users:F
- installation path - Provide the Manage_Engine folder location.
- Users - Provide the PAM360 service account in the following format: <DomainName\user name> or <username@domainname>.
- Example: icacls "C:\ProgramFiles\ManageEngine\PAM360" /q /c /t /grant ManageEngine\svcpam360:F
- If the key is placed outside the PAM360 folder, kindly provide permission for the key's locations using icacls command.
- In the same way, provide full control permission for <PAM360>\pgsql\data folder.
- Check the <PAM360_Installation_Directory>/pgsql/data folder and ensure if it has inherited that permission.
- icacls "installation path" /q /c /t /grant Users:F
- Navigate to <PAM360_Installation_Directory>/pgsql/data and open pg_hba.conf and search NULL. If you find any, remove the entire line that contains NULL.
- Rename the logs folder present inside the <PAM360_Installation_Directory> as logs.old and create a new folder as logs.
- Rename the Patch folder present inside the <PAM360_Installation_Directory> as Patch.old and create a new folder as Patch.
- Navigate to <PAM360_Installation_Directory>/bin directory and look for files named .lock or lockfile. If present, move both these files to any other directory.
- Go to <PAM360_Installation_Directory>/pgsql/data directory and look for files named recovery.conf and postmaster.pid. If present, move this file to any other directory.
- Now, try to apply the PPM or configure HA or try starting the service.
If the issue still persists, zip and send us the logs from the <PAM360_HOME> and also the <PAM360-HOME>\pgsql\data\pg_log folder along with the above screen shots to pam360-support@manageengine.com.
23. How to handle the following exceptions that occur while upgrading PAM360 version?
Exception #1: Caused by: java.lang.OutOfMemoryError: GC overhead limit exceeded
- Stop the PAM360 service.
- Take a backup of the <PAM360_Installation_Directory> or a VM snapshot.
- Navigate to <PAM360 installation directory>\bin and open the file UpdateManager.bat (UpdateManager.sh for Linux)
- Open this file using any editor and search for the entry: $JAVA -Xmx100m $JAVA_OPTS -Dtier-type=BE -Djava.library.path=./lib/native -Dtier-id=BE1 -cp $CLASSPATH com.adventnet.tools.update.installer.UpdateManager -u conf $*
- Change the value to $JAVA -Xmx2048m $JAVA_OPTS -Dtier-type=BE -Djava.library.path=./lib/native -Dtier-id=BE1 -cp $CLASSPATH com.adventnet.tools.update.installer.UpdateManager -u conf $*
- Save the file. Start the PAM360 service and try the upgrade once again.
If the issue still persists, please send your logs to pam360-support@manageengine.com for further investigation.
Exception #2: Trying to start the PostgreSQL server failed
- Stop PAM360 service.
- Kill any Postgres or PAM360.exe process using task manager.
- Exit the PAM360 tray icon.
- Run PAM360 service account using a privileged account. And give this account <PAM360_Installation_Directory> full and manage folder permission.
- Open command prompt using the privileged account.
- Proceed with the upgrade.
24. How to perform version upgrade using the CLI mode?
Windows
- Stop the PAM360 service.
- Open command prompt with administrator privileges.
- Navigate to<PAM360_Installation_Directory>/bin and execute - UpdateManager.bat -u conf -c -option i Mention the .ppm file location in the next line.
- Enter to proceed with the upgrade.
Linux
- Stop the PAM360 service.
- Open command prompt with administrator privileges.
- Navigate to
/bin and execute - UpdateManager.sh -u conf -c -option i -ppmPath Eg: UpdateManager.sh -u conf -c -option i -ppmPath c:\pam360.ppm.
- Enter to proceed with the upgrade.
Click here for detailed upgrade pack instructions.
25. Logs, Reports, and CAPTCHA are unreadable after a version upgrade. How to fix this issue?
Check for the following:
- Open logs and check if you could find the following error:
javax.servlet.ServletException: javax.servlet.ServletException: java.lang.Error: Probable fatal error:No fonts found. - Check if you have installed dejavu fonts.
Use the following commands to install the dejavu fonts.
1. For RHEL / Centos:
sudo yum install fontconfig dejavu-sans-fonts dejavu-serif-fonts
2. Ubuntu / Debian:
sudo apt install fonts-dejavu fontconfig
3. SLES:
sudo zypper install dejavu-fonts fontconfig
Now, you have successfully installed the dejavu font in your machine.
After installing, follow the below steps:
- Navigate to <PAM360 Installation Directory>/conf folder.
- Open wrapper_lin.conf file and add following property:
wrapper.java.additional.27=-Dsun.java2d.fontpath=<Font Dir Path>
[or] - Copy all the ttf files and paste it under <PAM360 Installation Directory>/jre/lib/fonts folder.
- Restart the PAM360 service.
Web Interface and Authentication
1. Can I change the default port 8282 where PAM360 is listening?
Yes, you can change the default port as explained below:
- Login to PAM360 as an Administrator. Navigate to Admin >> Configuration >> PAM360 Server.
- Enter the required port beside the Server Port field, and click Save.
- Restart PAM360 for this configuration to take effect.
2. How do I change the PAM360 web portal access URL?
- Login as an administrator. Navigate to Admin >> Settings and click Mail Server Settings.
- Fill in the required URL in the Access URL field and save the settings.
This will serve as your custom web URL for PAM360 from now on.
3. PAM360 is a web-based application that can be accessed via a web browser. Does that mean I can access it from anywhere?
PAM360 is an on-premise tool installed in a physical server or virtual machines (VM). You can access PAM360's web interface from any machine on the network connected to the same LAN network using the web browsers.
4. Can I change the IP address in which PAM360 application is binding when I have multiple NIC cards and IP's available in the server?
PAM360 comes bundled with a tailored version of TomCat webserver which allows users to access the webpage and also the JVM which performs the product operations. You can use the below steps to configure the Bind IP address for both these components.
Steps for changing webserver bind IP
- Stop the PAM360 service.
- Navigate to <PAM360 installation folder>/conf directory and take a backup of the file named server.xml.
- Open Wordpad as an administrator and open server.xml under <PAM360 installation folder>/conf directory.
- Look for the port="8282" and add the entry address="<IP addresses of the application server>" next to it.
- Save the file.
- Start the PAM360 service. This time the Tomcat webserver will start using the bind IP that you have specified.
Steps for changing JVM bind IP
- Stop the PAM360 service.
- Navigate to <PAM360 installation folder>/conf directory and take a backup of the file named wrapper.conf.
- Open Wordpad as an administrator and open wrapper.conf under <PAM360 installation folder>/conf directory.
- Now, rename <PAM360 installation folder>/logs folder to logs_older and start the PAM360 service.
- Connect to the login page and try using the product features such as Password reset. The source IP for these operations will be the IP Address that you have configured.
5. What if my users are not notified of their PAM360 accounts?
In general, users are notified of their PAM360 accounts only through emails. If a user does not get the notification emails, verify:
- if you have configured the mail server settings properly, with the details of the SMTP server in your environment.
- if you have provided valid credentials as a part of mail server settings, as some mail servers require the same for mails to be received.
- if the 'Sender E-Mail ID' is properly configured, as some mail servers reject emails sent without the From address or mails originating from unknown domains.
6. What are the authentication schemes available in PAM360?
You can use one of the following three authentication mechanisms out of PAM360:
- Active Directory: When enabled, the authentication request is forwarded to the configured domain controller and based on the result, the user is allowed or denied access into PAM360. The user name, password and the domain are supplied in the PAM360 login screen. This scheme works only for users whose details have been imported previously from AD, and is available only when the PAM360 server is installed on a Windows system.
- LDAP Directory: When enabled, the authentication request is forwarded to the configured LDAP directory server and based on the result, the user is allowed or denied access into PAM360. The username, password and the option to use LDAP authentication are supplied in the PAM360 login screen. This scheme works only for users whose details have been imported previously from the LDAP directory.
- PAM360 Local Authentication: The authentication is done locally by the PAM360 server. Irrespective of AD or LDAP authentication being enabled, this scheme is always available for the users to choose in the login page. This scheme has a separate password for users and the AD or LDAP passwords are never stored in the PAM360 database. However, for security reasons, we recommend that you disable the local authentication for users after enabling AD/LDAP authentication.
- Azure AD: Once you integrate PAM360 with Azure Active Directory (Azure AD) in your environment, you can allow users to use their Azure AD credentials to log in to PAM360 in both Windows and Linux platforms. To use this authentication, PAM360 should first be added as a native client application in your Azure AD portal .
- Smartcard Authentication: Enabling this feature will mandate users to possess a smartcard, and also know their Personal Identification Number (PIN). Note that smartcard authentication will bypass other first factor authentication methods like AD, LDAP or Local Authentication.
- RADIUS Authentication: You can integrate PAM360 with RADIUS server in your environment and use RADIUS authentication to replace the local authentication provided by PAM360. The users who will be accessing PAM360 using their RADIUS server credentials will have to be added as users in PAM360 first. When you do so, you need to ensure that the "username" in PAM360 is the same as the username used for accessing the RADIUS server.
- SAML SSO: PAM360 acts as the Service Provider (SP) and it integrates with Identity Providers (IdP) using SAML 2.0. The integration basically involves supplying details about SP to IdP and vice-versa. Once you integrate PAM360 with an IdP, the users have to just login to the IdP and then, they can automatically login to PAM360 from the respective IdP's GUI without having to provide the credentials again. PAM360 supports integration with Okta, AD FS, and Azure AD SSO.
Note:
For SAML SSO authentication, the Assertion Consumer URL is the hostname of the server, by default. To update the Assertion URL, follow the below steps:
- Go to Admin >> Settings >> Mail Server Settings.
- Under Access URL, update the required URL and click Save.
Now, the Assertion Consumer URL under Service Provider Details will be updated.
7. What are the user roles available in PAM360? What are their access levels?
PAM360 comes with five pre-defined roles:
- Privileged Administrator
- Administrators
- Password Administrator
- Password Auditor
- Password User
Apart from these default roles, any administrator can be promoted as a Super Administrator with the privilege to view and manage all the resources. Click here for details on the access levels of the default roles.
8. What if I forget my PAM360 login password?
If you were already given a valid PAM360 account, you can use the 'Forgot Password?' link available in the login page to reset your password. The username/email ID pair supplied should match the one already configured for the user. The password will be reset for that user and the new password will be sent to the respective email address. However, you wouldn't need this option if AD/LDAP authentication is enabled.
9. Why do I sometimes see a security warning while accessing the PAM360 console via the browser?
The PAM360 web console always uses the HTTPS protocol to communicate with the PAM360 server. The PAM360 server comes with a default self-signed SSL certificate, which the standard web browsers will not recognize, thereby issuing a warning. You can ignore this warning while you're testing or evaluating the product. However, if you're rolling it out in production, we recommend that you install an SSL certificate bought from an authorized Certificate Authority(CA) that is recognized by all standard web browsers. Know More
Security
1. How secure are my passwords in PAM360?
Ensuring secure storage of passwords and offering solid defense against intrusion are the top priorities of PAM360. The following measures ensure high level security for your passwords:
- Passwords are encrypted using Advanced Encryption Standard (AES), and stored in the database. AES is currently the strongest encryption algorithm known, and has been adopted as an encryption standard by the U.S. Government.
- The database which stores all the passwords accepts connections only from the host that it is running on, and is not visible externally.
- Role-based, fine-grained user access control mechanism ensures that users can view and access passwords only based on the permissions granted to them.
- All transactions between the PAM360 console and the server take place through HTTPS.
- PAM360's in-built password generator helps you generate strong passwords.
2. How secure are Application-to-Application and Application-to-Database password management done through Password Management APIs?
PAM360 offers RESTful APIs and SSH-based CLI APIs that can be used for Application-to-Application/Database password management. The applications connect and interact with PAM360 through HTTPS. An application's identity is verified first by verifying the validity of its SSL certificate, and then by verifying the source IP/hostname in which it resides. Each application/database must be registered as an API User in PAM360. During this registration, the hostname/IP of the application server has to be supplied and a unique authentication token that uses the REST API will be generated. This token needs to be sent along with the API requests for authentication. In addition to these security checks, each application/database can only access the information that are explicitly delegated to them by an administrative user. Refer to this document to know more about sharing/delegating passwords.
3. Can we install our own SSL certificates?
Yes, you can install your own SSL certificates. Follow the steps below:
- Navigate to "Admin >> Configuration >> PAM360 Server".
- Choose the Keystore Type as JKS, PKCS12 or PKCS11 whichever you chose while generating the CSR.
- Browse and upload the Keystore File.
- Enter the same Keystore Password, you entered while generating the CSR.
- Modify the Server Port, if required.
- Hit Save. Restart the PAM360 service once, for the certificate change to take effect.
4. How to generate signed SSL certificates?
PAM360 runs as a HTTPS service. It requires a valid CA-signed SSL certificate with the principal name as the name of the host on which it runs. By default, on first time startup, it creates a self-signed certificate, which will not be trusted by the user browsers. Thus, while connecting to PAM360, you need to manually verify the certificate information and the host name of PAM360 server carefully and should force the browser to accept the certificate.
To make the PAM360 server trusted by web browsers and users:
- Obtain a new signed certificate from a CA for the PAM360 host. [OR]
- Configure an existing certificate obtained from a CA with wild-card principal support for the PAM360 host.
There are different ways to generate the signed SSL certificates:
- By using the "Certificate Management" module of PAM360.
- By using the OpenSSL or Keytool (bundled with Java) to create your certificates, get them signed by a CA and use them with PAM360.
- By installing a wild card certificate.
You can decide the mode of generating the signed SSL certificates based on what your security administrators recommend. The detailed steps for using each of the above methods are provided under the links below.
Note: If you already have a certificate signed by a CA, then we recommend using OpenSSL to create the keystore and configure it in PAM360 (steps 4 and 5 in the instructions below).
- Generating Signed SSL certificates using the Certificate Management module of PAM360
- Generating Signed SSL certificates using OpenSSL
- Generating Signed SSL certificates using Keytool
- Generating Signed SSL certificates by installing a wild card certificate
1. Generating Signed SSL certificates using the Certificate Management module of PAM360
You can generate signed SSL certificates through the Certificate Management module of PAM360 and also apply the certificate changes (Certificate Keystore) directly from the PAM360 console. This involves three processes:
1.1 Generating a Certificate Signing Request (CSR):
To request and acquire certificates from a Local CA through PAM360, you need to first generate a Certificate Signing Request (CSR). Here are the steps for the same:
- Navigate to the "Certificates >> Create CSR".
- Click the Create button. The Create CSR page is displayed.
- Select either of the options Create CSR or Create CSR From KeyStore, based on whether you want to create a new CSR or create a CSR from an already existing private key, respectively.
- If you have selected Create CSR, fill in the details, such as Common Name, SAN, Organization Unit, Organization Location, State, Country, Key Algorithm and Key Size. Select the Key Algorithm and Keystore Type. Enter the Validity and Store Password.
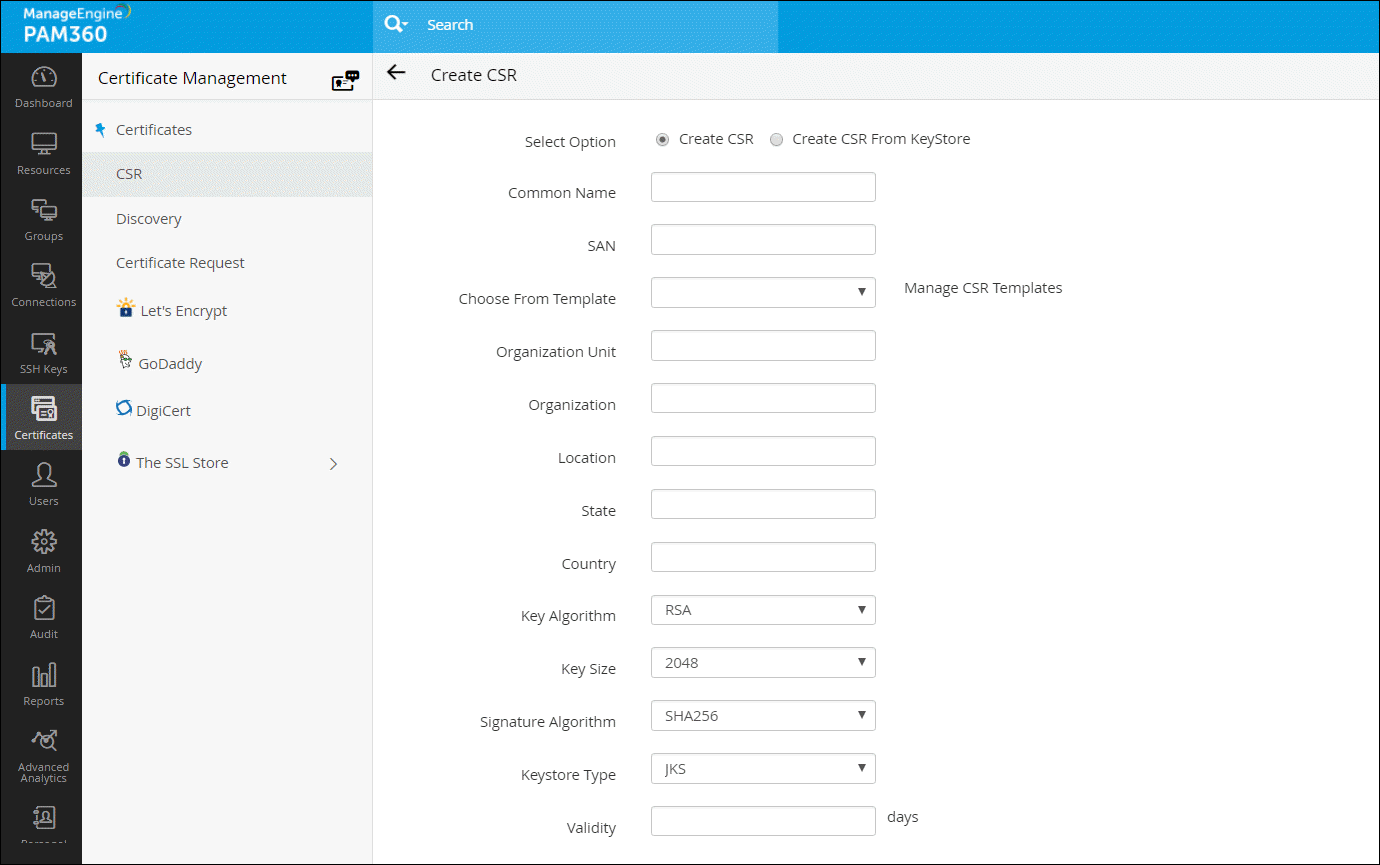
- If you have selected Create CSR From KeyStore, browse and attach the required private key file along with the Private Key Password.
- If you have selected Create CSR, fill in the details, such as Common Name, SAN, Organization Unit, Organization Location, State, Country, Key Algorithm and Key Size. Select the Key Algorithm and Keystore Type. Enter the Validity and Store Password.
- Click the Create button. You will be redirected to a window where the CSR content is displayed. You can copy the CSR content or export it to a mailbox.
- Email - Select this option to send the certificate file via email to the specified mail id.
- Export CSR / Private Key - Select this option to export the CSR or the corresponding private key alone based on your requirement.
- View the saved CSRs under "Certificates >> Create CSR".
Note: The 'show passphrase' eye icon corresponding to each CSR allows the administrators to view the KeyStore passwords of the CSR files.
1.2 Signing the Certificate:
PAM360 provides the option to sign and issue certificates to all clients in your network either from your Microsoft Certificate Authority or using a custom root CA certificate that is trusted within your environment.
Note: Remember, you should have generated a valid Certificate Signing Request (CSR) before getting your certificate signed from the local CA.
Follow the below steps to sign the certificate:
- Navigate to "Certificates >> Create CSR".
- Select the required CSR from the table and click Sign from the top menu.
- In the pop-up window displayed, provide the name of the server that runs the internal certificate authority, CA Name and choose the certificate template based on your requirement. Click Sign Certificate. The CSR is signed now and the issued certificate can be viewed under "Certificates >> Certificates".
1.3 Applying the Certificate Keystore for PAM360 web server:
To apply the certificate Keystore, first you need to create it.
- Navigate to "Certificates >> Certificates". Click the signed certificate link under the heading Common Name. In the certificate details page displayed, click the Export icon present at the top right corner of the screen. The certificate file will be downloaded to your local machine.
- Now, navigate to "Certificates >> Create CSR".
- Click the Import Certificate icon corresponding to the CSR of the signed certificate. Browse and choose the certificate file downloaded in your local machine and click Import. Now, the certificate will be bonded with the private key to form a Keystore.
- Now navigate back to "Certificates >> Certificates" and click the certificate link under the heading Common Name. In the certificate details page displayed, scroll down and click the Export link. This will download the certificate Keystore to your local machine.
- The final step is to navigate to "Admin >> Configuration >> PAM360 Server" and do the following:
- Choose the Keystore Type as JKS, PKCS12 or PKCS11, whichever you chose while generating the CSR.
- Browse and upload the Keystore File.
- Enter the same Keystore Password, you entered while generating the CSR.
- Modify the Server Port, if required.
- Hit Save. Restart the PAM360 service once, for the certificate change to take effect.
2. Generating Signed SSL certificates using OpenSSL
OpenSSL mostly comes bundled with the Linux distributions. If you are using the Windows server and do not have OpenSSL installed, download it from http://www.slproweb.com/products/Win32OpenSSL.html. Make sure the 'bin' folder under the OpenSSL installation is included in the 'PATH' environment variable.
2.1 Create the public-private key pair that will be used for the SSL handshake
- Open the command prompt.
- Execute 'openssl genrsa -des3 -out <privatekey_filename>.key 1024'
- You will be prompted to enter a pass-phrase for the private key. Enter 'passtrix' or a pass-phrase of your choice. (Though it is not documented, Tomcat has issues with passwords containing special characters, so use a password that has only alpha characters)
- A file will be created in the name <privatekey_filename>.key in the same folder.
<privatekey_filename> is the filename you specify to store the private key.
2.2 Create a Certificate Signing Request (CSR) for submission to a certificate authority to create a signed certificate with the public key generated in the previous step
- Execute 'openssl req -new -key <privatekey_filename>.key -out <certreq_filename>.csr'
- <privatekey_filename>.key is the one used in the previous step.
- <certreq_filename>.csr is the filename you specify to carry the certificate creation request to the CA (certificate authority).
- You will be prompted to enter a series of values that are part of the distinguished name (DN) of the server hosting PAM360.
- Enter values as required. Importantly, for the 'Common Name' supply the fully qualified name of the server hosting PAM360 (with which it will be accessed through the browsers).
- A file will be created in the name <certreq_filename>.csr in the same folder.
2.3 Submit the CSR to a Certificate Authority (CA) to obtain a CA signed certificate
Some of the prominent CAs are Verisign, Thawte, RapidSSL. Check their documentation / website for details on submitting CSRs and this will involve a cost to be paid to the CA. This process usually takes a few days time and you will be returned your signed SSL certificate and the CA's root certificate as .cer files. Save them both in the same working folder where files from steps 1 and 2 are stored
2.4 Import the CA-signed certificate to a keystore
- Open command prompt and navigate to the same working folder.
- Execute 'openssl pkcs12 -export -in <cert_file>.cer -inkey <privatekey_filename>.key -out <keystore_filename>.p12 -name PAM360 -CAfile <root_cert_file>.cer -caname PAM360 -chain'
where,
- cert_file.cer is the signed SSL certificate with the .cer extension.
- privatekey_filename.key is the private key file with a .key extension.
- keystore_filename.p12 name is the keystore that will be generated with a .p12 extension.
- root_cert_file.cer is the CA's root certificate with a .cer extension.
- When prompted for a password, enter the same password, you used in step 1 for the private key. This requirement is due to an inherent limitation in tomcat, which requires the two passwords to match.
- Now, a keystore file in the name <keystore_filename>.p12 will be generated in the same folder.
2.5 Configure the PAM360 server to use the keystore with your SSL certificate
This is the final step in generating Signed SSL certificates using OpenSSL.
- Copy the <keystore_filename>.p12 generated in step 4 to the <PAM360_Install_Folder>\conf folder.
- Open command prompt and navigate to the <PAM360_Install_Folder>\conf folder.
- Open the file server.xml and do the following changes:
- Search for the entry 'keystoreFile', which will have the default value set to 'conf/server.keystore'. Change the value to 'conf/<keystore_filename>.p12'.
- Starting from version 9700, the keystore password is encrypted and cannot be updated directly in the server.xml file.In order to manuallyupdate the keystore password in the .xml file, disable the encryption first,bychanging the value'keystorePassEncrypted=true'to 'keystorePassEncrypted=false'.
- Now, set the value of 'keystorePass' to "passtrix" or the password you specified in the previous step while creating the keystore.
- Add a new entry keystoreType= PKCS12 or PKCS11 next to the keystorePass entry.
- Save the server.xml file.
- Restart the PAM360 server and connect through the web browser. If you are able to view the PAM360 login console without any warning from the browser, you have successfully installed your SSL certificate in PAM360.
3. Generating Signed SSL certificates using Keytool
3.1 Create the public-private key pair that will be used for the SSL handshake
- Go to the <PAM360_Home>/jre/bin folder.
- Execute the command:
"./keytool -genkey -alias PAM360 -keyalg RSA -sigalg SHA256withRSA -keypass <privatekey_password> -storepass <keystore_password> -validity <no_of days> -keystore <keystore_filename>where,
<keystore_password> is the password to access the keystore, <privatekey_password> is the password to protect your private key. Note that due to an inherent limitation in tomcat, these two passwords have to be the same. (Though it is not documented, Tomcat has issues with passwords containing special characters, so use a password that has only alpha characters)
<no_of_days> is the validity of the key pair in number of days, from the day it was created - The above command will prompt you to enter details about you and your organization.
- For the 'first and the last name', enter the FQDN of the server where PAM360 is running.
- For other fields, enter the relevant details.
- A keystore file will be created in the name <keystore_filename> in the same folder, with the generated key pair.
3.2 Create a Certificate Signing Request (CSR) for submission to a certificate authority to create a signed certificate with the public key generated in the previous step
- Go to the <PAM360_Home>/jre/bin folder.
- Execute the command: "keytool -certreq -keyalg RSA -alias PAM360 -keypass <privatekey_password> -storepass <keystore_password> -file <csr_filename> -keystore <keystore_filename>".
Note: The <csr_filename> that you choose should have the .csr extension.
- A CSR file in the name <csr_filename> will be created in the same folder.
3.3 Submit the CSR to a Certificate Authority (CA) to obtain a signed certificate
Some of the prominent CAs are Verisign, Thawte, RapidSSL. Check their documentation / website for details on submitting the CSRs. Please note that this is a paid service. This process usually takes a few days of time. You will receive your signed SSL certificate and the CA's certificate as .cer files. Save both the files in the <PAM360_Home>/jre/bin folder.
3.4 Import the CA-signed certificate to the PAM360 server
- Go to the <PAM360_Home>/jre/bin folder using command prompt.
- If you have a single file as the certificate bundle(p7b), then run the below command:
"keytool -import -alias PAM360 -keypass <privatekey_password> -storepass <keystore_password> -keystore <keystore_filename> -trustcacerts -file <your_ssl_bundle.p7b>"
where,
- <boundlessness> is the certificate bundle obtained from the CA, a .p7b file saved in the previous step. The <privatekey_password>,<keystore_password> and <keystore_filename> are the ones used in the previous steps.
- If you have 3 files, the root, the intermediate and the actual certificates in .cer format, then you need to import each one of them using the below commands.
- "keytool -import -alias root -keypass <privatekey_password> -storepass <keystore_password> -keystore <keystore_filename> -trustcacerts -file <rooter>"
- "keytool -import -alias inter -keypass <privatekey_password> -storepass <keystore_password> -keystore <keystore_filename> -trustcacerts -file <inter.cer>"
- "keytool -import -alias PAM360 -keypass <privatekey_password> -storepass <keystore_password> -keystore <keystore_filename> -trustcacerts -file <your_ssl_cert.cer>"
- Now, copy the <keystore_filename> to the <PAM360_Home>/conf folder.
3.5 Configure the PAM360 server to use the keystore with your SSL certificate
This is the final step in generating Signed SSL certificates using Keytool.
- Go tothe <PAM360_Home>/conf folder.
- Open the fileserver.xml.
- Search for the entry 'keystoreFile', which will have the default value set to "conf/server.keystore". Change the value to "conf/<keystore_filename>", where <keystore_filename> is the one used in the previous steps.
- Starting from version 9700, the keystore password is encrypted and cannot be updated directly in the server.xml file.In order to manually update the keystore password in the.xml file, disable the encryption first, bychanging the value 'keystorePassEncrypted=true' to 'keystorePassEncrypted=false.
Note: This step is applicable only if you're using the version 9700 or above.
- Set the value of 'keystorePass' to "passtrix" or the password you specified in the previous step while creating the keystore.
- Restart the PAM360 server and connect through the web browser. If youare able to view the PAM360 login console without any warning from the browser, you have successfully installed your SSL certificate in PAM360.
Note: Tomcat, by default, accepts only the JKS (Java Key Store) and PKCS #12 format keystores. In case, the keystore is of PKCS #12 format, include the following option in the server.xml file along with the keystore name, keystoreType="PKCS12? This notifies tomcat that the format is PKCS12. Restart the server after this change.
4. Generating Signed SSL certificates by installing an existing wild card supported SSL certificate:
- Go to the <PAM360_Home>/conf folder.
- Open the file server.xml.
- Search for the entry 'keystoreFile', which will have the default value set to "conf/server.keystore". Change the value to "conf/<keystore_filename>" where <keystore_filename> belongs to the existing wild-card certificate.
- Also search for the entry 'keystorePass' (found next to the keystoreFile), which will have the default value set to "passtrix". Change the value to "<keystore_password>", where <keystore_password> protects the existing wild-card certificate keystore.
- Restart the PAM360 server and connect through the web browser console. If you are able to view the PAM360 login console without any warning from the browser, you have successfully installed your SSL certificate in PAM360.
Note: Please refer your CA's documentation for more details and troubleshooting.
5. How to make the PAM360 server trusted by web browsers and users?
PAM360 runs as a HTTPS service. It requires a valid CA-signed SSL certificate with the principal name as the name of the host on which it runs. By default, on first time startup, it creates a self-signed certificate, which will not be trusted by the user browsers. Thus, while connecting to PAM360, you need to manually verify the certificate information and the host name of PAM360 server carefully and should force the browser to accept the certificate.
To make the PAM360 server trusted by web browsers and users:
- Obtain a new signed certificate from a CA for the PAM360 host. [OR]
- Configure an existing certificate obtained from a CA with wild-card principal support for the PAM360 host.
There are different ways to generate the signed SSL certificates:
- By using the "Certificate Management" module of PAM360.
- By using the OpenSSL or Keytool (bundled with Java) to create your certificates, get them signed by a CA and use them with PAM360.
- By installing a wild card certificate.
You can decide the mode of generating the signed SSL certificates based on what your security administrators recommend. The detailed steps for using each of the above methods are provided under the links below.
Note: If you already have a certificate signed by a CA, then we recommend using OpenSSL to create the keystore and configure it in PAM360 (steps 4 and 5 in the instructions below).
- Generating Signed SSL certificates using the Certificate Management module of PAM360
- Generating Signed SSL certificates using OpenSSL
- Generating Signed SSL certificates using Keytool
- Generating Signed SSL certificates by installing a wild card certificate
1. Generating Signed SSL certificates using the Certificate Management module of PAM360
You can generate signed SSL certificates through the Certificate Management module of PAM360 and also apply the certificate changes (Certificate Keystore) directly from the PAM360 console. This involves three processes:
1.1 Generating a Certificate Signing Request (CSR):
To request and acquire certificates from a Local CA through PAM360, you need to first generate a Certificate Signing Request (CSR). Here are the steps for the same:
- Navigate to the "Certificates >> Create CSR".
- Click the Create button. The Create CSR page is displayed.
- Select either of the options Create CSR or Create CSR From KeyStore, based on whether you want to create a new CSR or create a CSR from an already existing private key, respectively.
- If you have selected Create CSR, fill in the details, such as Common Name, SAN, Organization Unit, Organization Location, State, Country, Key Algorithm and Key Size. Select the Key Algorithm and Keystore Type. Enter the Validity and Store Password.

- If you have selected Create CSR From KeyStore, browse and attach the required private key file along with the Private Key Password.
- If you have selected Create CSR, fill in the details, such as Common Name, SAN, Organization Unit, Organization Location, State, Country, Key Algorithm and Key Size. Select the Key Algorithm and Keystore Type. Enter the Validity and Store Password.
- Click the Create button. You will be redirected to a window where the CSR content is displayed. You can copy the CSR content or export it to a mailbox.
- Email - Select this option to send the certificate file via email to the specified mail id.
- Export CSR / Private Key - Select this option to export the CSR or the corresponding private key alone based on your requirement.
- View the saved CSRs under "Certificates >> Create CSR".
Note: The 'show passphrase' eye icon corresponding to each CSR allows the administrators to view the KeyStore passwords of the CSR files.
1.2 Signing the Certificate:
PAM360 provides the option to sign and issue certificates to all clients in your network either from your Microsoft Certificate Authority or using a custom root CA certificate that is trusted within your environment.
Note: Remember, you should have generated a valid Certificate Signing Request (CSR) before getting your certificate signed from the local CA.
Follow the below steps to sign the certificate:
- Navigate to "Certificates >> Create CSR".
- Select the required CSR from the table and click Sign from the top menu.
- In the pop-up window displayed, provide the name of the server that runs the internal certificate authority, CA Name and choose the certificate template based on your requirement. Click Sign Certificate. The CSR is signed now and the issued certificate can be viewed under "Certificates >> Certificates".
1.3 Applying the Certificate Keystore for PAM360 web server:
To apply the certificate Keystore, first you need to create it.
- Navigate to "Certificates >> Certificates". Click the signed certificate link under the heading Common Name. In the certificate details page displayed, click the Export icon present at the top right corner of the screen. The certificate file will be downloaded to your local machine.
- Now, navigate to "Certificates >> Create CSR".
- Click the Import Certificate icon corresponding to the CSR of the signed certificate. Browse and choose the certificate file downloaded in your local machine and click Import. Now, the certificate will be bonded with the private key to form a Keystore.
- Now navigate back to "Certificates >> Certificates" and click the certificate link under the heading Common Name. In the certificate details page displayed, scroll down and click the Export link. This will download the certificate Keystore to your local machine.
- The final step is to navigate to "Admin >> Configuration >> PAM360 Server" and do the following:
- Choose the Keystore Type as JKS, PKCS12 or PKCS11, whichever you chose while generating the CSR.
- Browse and upload the Keystore File.
- Enter the same Keystore Password, you entered while generating the CSR.
- Modify the Server Port, if required.
- Hit Save. Restart the PAM360 service once, for the certificate change to take effect.
2. Generating Signed SSL certificates using OpenSSL
OpenSSL mostly comes bundled with the Linux distributions. If you are using the Windows server and do not have OpenSSL installed, download it from http://www.slproweb.com/products/Win32OpenSSL.html. Make sure the 'bin' folder under the OpenSSL installation is included in the 'PATH' environment variable.
2.1 Create the public-private key pair that will be used for the SSL handshake
- Open the command prompt.
- Execute 'openssl genrsa -des3 -out <privatekey_filename>.key 1024'
- You will be prompted to enter a pass-phrase for the private key. Enter 'passtrix' or a pass-phrase of your choice. (Though it is not documented, Tomcat has issues with passwords containing special characters, so use a password that has only alpha characters)
- A file will be created in the name <privatekey_filename>.key in the same folder.
<privatekey_filename> is the filename you specify to store the private key.
2.2 Create a Certificate Signing Request (CSR) for submission to a certificate authority to create a signed certificate with the public key generated in the previous step
- Execute 'openssl req -new -key <privatekey_filename>.key -out <certreq_filename>.csr'
- <privatekey_filename>.key is the one used in the previous step.
- <certreq_filename>.csr is the filename you specify to carry the certificate creation request to the CA (certificate authority).
- You will be prompted to enter a series of values that are part of the distinguished name (DN) of the server hosting PAM360.
- Enter values as required. Importantly, for the 'Common Name' supply the fully qualified name of the server hosting PAM360 (with which it will be accessed through the browsers).
- A file will be created in the name <certreq_filename>.csr in the same folder.
2.3 Submit the CSR to a Certificate Authority (CA) to obtain a CA signed certificate
Some of the prominent CAs are Verisign, Thawte, RapidSSL. Check their documentation / website for details on submitting CSRs and this will involve a cost to be paid to the CA. This process usually takes a few days time and you will be returned your signed SSL certificate and the CA's root certificate as .cer files. Save them both in the same working folder where files from steps 1 and 2 are stored
2.4 Import the CA-signed certificate to a keystore
- Open command prompt and navigate to the same working folder.
- Execute 'openssl pkcs12 -export -in <cert_file>.cer -inkey <privatekey_filename>.key -out <keystore_filename>.p12 -name PAM360 -CAfile <root_cert_file>.cer -caname PAM360 -chain'
where,
- cert_file.cer is the signed SSL certificate with the .cer extension.
- privatekey_filename.key is the private key file with a .key extension.
- keystore_filename.p12 name is the keystore that will be generated with a .p12 extension.
- root_cert_file.cer is the CA's root certificate with a .cer extension.
- When prompted for a password, enter the same password, you used in step 1 for the private key. This requirement is due to an inherent limitation in tomcat, which requires the two passwords to match.
- Now, a keystore file in the name <keystore_filename>.p12 will be generated in the same folder.
2.5 Configure the PAM360 server to use the keystore with your SSL certificate
This is the final step in generating Signed SSL certificates using OpenSSL.
- Copy the <keystore_filename>.p12 generated in step 4 to the <PAM360_Install_Folder>\conf folder.
- Open command prompt and navigate to the <PAM360_Install_Folder>\conf folder.
- Open the file server.xml and do the following changes:
- Search for the entry 'keystoreFile', which will have the default value set to 'conf/server.keystore'. Change the value to 'conf/<keystore_filename>.p12'.
- Starting from version 9700, the keystore password is encrypted and cannot be updated directly in the server.xml file.In order to manuallyupdate the keystore password in the .xml file, disable the encryption first,bychanging the value'keystorePassEncrypted=true'to 'keystorePassEncrypted=false'.
- Now, set the value of 'keystorePass' to "passtrix" or the password you specified in the previous step while creating the keystore.
- Add a new entry keystoreType= PKCS12 or PKCS11 next to the keystorePass entry.
- Save the server.xml file.
- Restart the PAM360 server and connect through the web browser. If you are able to view the PAM360 login console without any warning from the browser, you have successfully installed your SSL certificate in PAM360.
3. Generating Signed SSL certificates using Keytool
3.1 Create the public-private key pair that will be used for the SSL handshake
- Go to the <PAM360_Home>/jre/bin folder.
- Execute the command:
"./keytool -genkey -alias PAM360 -keyalg RSA -sigalg SHA256withRSA -keypass <privatekey_password> -storepass <keystore_password> -validity <no_of days> -keystore <keystore_filename>where,
<keystore_password> is the password to access the keystore, <privatekey_password> is the password to protect your private key. Note that due to an inherent limitation in tomcat, these two passwords have to be the same. (Though it is not documented, Tomcat has issues with passwords containing special characters, so use a password that has only alpha characters)
<no_of_days> is the validity of the key pair in number of days, from the day it was created - The above command will prompt you to enter details about you and your organization.
- For the 'first and the last name', enter the FQDN of the server where PAM360 is running.
- For other fields, enter the relevant details.
- A keystore file will be created in the name <keystore_filename> in the same folder, with the generated key pair.
3.2 Create a Certificate Signing Request (CSR) for submission to a certificate authority to create a signed certificate with the public key generated in the previous step
- Go to the <PAM360_Home>/jre/bin folder.
- Execute the command: "keytool -certreq -keyalg RSA -alias PAM360 -keypass <privatekey_password> -storepass <keystore_password> -file <csr_filename> -keystore <keystore_filename>".
Note: The <csr_filename> that you choose should have the .csr extension.
- A CSR file in the name <csr_filename> will be created in the same folder.
3.3 Submit the CSR to a Certificate Authority (CA) to obtain a signed certificate
Some of the prominent CAs are Verisign, Thawte, RapidSSL. Check their documentation / website for details on submitting the CSRs. Please note that this is a paid service. This process usually takes a few days of time. You will receive your signed SSL certificate and the CA's certificate as .cer files. Save both the files in the <PAM360_Home>/jre/bin folder.
3.4 Import the CA-signed certificate to the PAM360 server
- Go to the <PAM360_Home>/jre/bin folder using command prompt.
- If you have a single file as the certificate bundle(p7b), then run the below command:
"keytool -import -alias PAM360 -keypass <privatekey_password> -storepass <keystore_password> -keystore <keystore_filename> -trustcacerts -file <your_ssl_bundle.p7b>"
where,
- <boundlessness> is the certificate bundle obtained from the CA, a .p7b file saved in the previous step. The <privatekey_password>,<keystore_password> and <keystore_filename> are the ones used in the previous steps.
- If you have 3 files, the root, the intermediate and the actual certificates in .cer format, then you need to import each one of them using the below commands.
- "keytool -import -alias root -keypass <privatekey_password> -storepass <keystore_password> -keystore <keystore_filename> -trustcacerts -file <rooter>"
- "keytool -import -alias inter -keypass <privatekey_password> -storepass <keystore_password> -keystore <keystore_filename> -trustcacerts -file <inter.cer>"
- "keytool -import -alias PAM360 -keypass <privatekey_password> -storepass <keystore_password> -keystore <keystore_filename> -trustcacerts -file <your_ssl_cert.cer>"
- Now, copy the <keystore_filename> to the <PAM360_Home>/conf folder.
3.5 Configure the PAM360 server to use the keystore with your SSL certificate
This is the final step in generating Signed SSL certificates using Keytool.
- Go tothe <PAM360_Home>/conf folder.
- Open the fileserver.xml.
- Search for the entry 'keystoreFile', which will have the default value set to "conf/server.keystore". Change the value to "conf/<keystore_filename>", where <keystore_filename> is the one used in the previous steps.
- Starting from version 9700, the keystore password is encrypted and cannot be updated directly in the server.xml file.In order to manually update the keystore password in the.xml file, disable the encryption first, bychanging the value 'keystorePassEncrypted=true' to 'keystorePassEncrypted=false.
Note: This step is applicable only if you're using the version 9700 or above.
- Set the value of 'keystorePass' to "passtrix" or the password you specified in the previous step while creating the keystore.
- Restart the PAM360 server and connect through the web browser. If youare able to view the PAM360 login console without any warning from the browser, you have successfully installed your SSL certificate in PAM360.
Note: Tomcat, by default, accepts only the JKS (Java Key Store) and PKCS #12 format keystores. In case, the keystore is of PKCS #12 format, include the following option in the server.xml file along with the keystore name, keystoreType="PKCS12? This notifies tomcat that the format is PKCS12. Restart the server after this change.
4. Generating Signed SSL certificates by installing an existing wild card supported SSL certificate:
- Go to the <PAM360_Home>/conf folder.
- Open the file server.xml.
- Search for the entry 'keystoreFile', which will have the default value set to "conf/server.keystore". Change the value to "conf/<keystore_filename>" where <keystore_filename> belongs to the existing wild-card certificate.
- Also search for the entry 'keystorePass' (found next to the keystoreFile), which will have the default value set to "passtrix". Change the value to "<keystore_password>", where <keystore_password> protects the existing wild-card certificate keystore.
- Restart the PAM360 server and connect through the web browser console. If you are able to view the PAM360 login console without any warning from the browser, you have successfully installed your SSL certificate in PAM360.
Note: Please refer your CA's documentation for more details and troubleshooting.
6. Can we create server certificates with SubjectAlternativeName (SAN)?
Yes, you can create a certificate using SAN with an alias name and apply it in PAM360. Follow the below steps:
1. Creating a CSR using PAM360's SSL certificate management module, and submitting it to any CA for signing
1.1 Create a Certificate Signing Request (CSR)
- Login to PAM360 as an administrator.
- Navigate to Certificates >> Create CSR.
- Click on the 'Create' button.
- Here, provide a name for your certificate.
- The Subject Alternative Name (SAN) will be auto-filled when you click on it after providing the common name. You can include additional SANs in the text field.
- Provide the other details including your organization details, location, validity, and a password.
- Click on 'Create'.
- Once done, you will find the option to export the certificate and the private key, or send the CSR to an email address that you specify.
1.2 Submit the CSR to a Certificate Authority (CA) to obtain a CA signed certificate
After creating the CSR, the next step is get the CSR verified and signed by a CA. There are two options to do this:
- You can export the CSR file and manually send it to a third party CA to get it signed.
- You sign and issue certificates to all clients in your network either from your Microsoft Certificate Authority or using a custom root CA certificate that is trusted within your environment. To do this, navigate to Certificates >> Create CSR, select a certificate, and click on 'Sign'. Refer to this document for more details on certificate signing.
Once signed, you can view the certificate under 'Certificates'.
1.3 Import the CA-signed certificate to the PAM360 server
To import the certificates in your network:
- Navigate to the Certificates.
- Click on 'Add'.
- Choose the required option:
- File Based Certificate“ Browse and import the required certificate file directly from your system.
- Content Based Certificate “ Copy the content of the required certificate file and paste it in the text box.
- Keystore Based “ Import all individual certificates available in keystore simultaneously. Upload the required keystore file and enter its corresponding password (if any).
- Click on the 'Add' button.
2. Creating a certificate with SAN using Microsoft internal CA
Make sure you follow the below mentioned steps to create server certificate with SubjectAlternativeName using Microsoft Internal CA. Also, in Additional Attributes, specify the 'san:dns=<The URL which you use to access PAM360>', and then try creating the certificate.
- Connect to the server where Microsoft Certificate Service is running.
- Open a command prompt and execute certutil -setreg policy\EditFlags +EDITF_ATTRIBUTESUBJECTALTNAME2
- Then, restart Microsoft Certificate Service(certsvc).
Create the private key using the below command,"./keytool -genkey -alias PAM360 -keyalg RSA -keypass <privatekey_password> -storepass <keystore_password> -validity <no_of days> -sigalg SHA256withRSA -keysize 2048 -keystore <keystore_filename>" - Here, when it prompts for first and last name, specify the name which you use to access PAM360.
- Create the Certificate Signing Request(CSR) using the below command: 'keytool -certreq -keyalg RSA -alias PAM360 -keypass <privatekey_password> -storepass <keystore_password> -file <csr_filename> -keystore PAM360.keystore'
- Submit CSR request to Microsoft Internal CA:
- Open IE and go to your CA's certificate request page.
- Request advanced certificate.
- Submit a certificate request.
- Copy and paste content of <csr_filename>.cer file.
- Certificate template should be Web Server.
- In "Additional Attributes", enter 'san:dns=passwordmanager&dns=passwordmanager.tcu.ad.local' and click on 'Submit'.
- Download the certificate chain in base64 format as PAM360cert.p7b.
- Import the downloaded 'PAM360cert.p7b' file into the PAM360.keystore "keytool -import -alias PAM360 -keypass <privatekey_password> -storepass <keystore_password> -keystore PAM360.keystore -trustcacerts -file PAM360cert.p7b"
Notes:
- If you receive the error message "Failed to establish chain from reply" with the above command, it means the root and intermediate certs of your CA are not available in the trusted store of the PAM360. So, before importing the actual certificate, you have to import the root certificate with a different alias and then import the actual certificate. Also, if you have multiple root certificates, then you have to import them one by one with the different alias names.
For example,
./keytool -import -alias root1 -keypass Password123 -storepass Password123 -keystore PAM360.keystore -trustcacerts -file root1.cer
./keytool -import -alias root2 -keypass Password123 -storepass Password123 -keystore PAM360.keystore -trustcacerts -file root2.cerBased on the number of root or intermediate root certificates, you have to execute the above command with different alias names and then continue with the actual certificate.
- The actual certificate should be in .cer or .crt format.
- If you receive the error message "Failed to establish chain from reply" with the above command, it means the root and intermediate certs of your CA are not available in the trusted store of the PAM360. So, before importing the actual certificate, you have to import the root certificate with a different alias and then import the actual certificate. Also, if you have multiple root certificates, then you have to import them one by one with the different alias names.
- Applying the certificate keystore in PAM360.
- Login to PAM360 as an administrator.
- Navigate to Admin >> Configuration >> PAM360 Server.
- Choose PKCS12 or PKCS11 as the Keystore Type.
- Click on 'Browse' and select your PFX/P12 file.
- Provide the correct keystore password and save the configuration.
- Restart PAM360 service to bring the certificate change into effect.
3. Creating certificate with SAN signed by third party vendor like GoDaddy, Verisign, Commodo, etc.
Make sure you follow the below mentioned steps to get SAN certificate signed from the third party vendors.
- Create the private key using the below command,
'./keytool -genkey -alias PAM360 -keyalg RSA -keypass <privatekey_password> -storepass <keystore_password> -validity <no_of days> -sigalg SHA256withRSA -keysize 2048 -keystore <keystore_filename>"'
Here, when it prompts for first and last name, specify the name which you use to access PAM360.
- Create the Certificate Signing Request(CSR) using the below command:
'keytool -certreq -keyalg RSA -alias PAM360 -keypass <privatekey_password> -storepass <keystore_password> -file <csr_filename> -keystore PAM360.keystore'
- Submit CSR request to third party signing tool and ensure to get the certificate signed using SAN name. Download the certificate chain in base64 format as PAM360cert.p7b
- Import the downloaded 'PAM360cert.p7b' file into the PAM360.keystore keytool -import -alias PAM360 -keypass <privatekey_password> -storepass <keystore_password> -keystore PAM360.keystore -trustcacerts -file PAM360cert.p7b
Note: If you receive the error message "Failed to establish chain from reply" with the above command. Then, the root and intermediate certs of your CA are not available in the trusted store of the PAM360. So, before importing the actual certificate, you have to import the root certificate with a different alias and then the actual certificate. Also, if you have multiple root certificates, then you have to import them one by one with different alias names. For example,
./keytool -import -alias root1 -keypass Password123 -storepass Password123 -keystore PAM360.keystore -trustcacerts -file root1.cer
./keytool -import -alias root2 -keypass Password123 -storepass Password123 -keystore PAM360.keystore -trustcacerts -file root2.cerBased on the number of root or intermediate root certificates, you have to execute the above command with different alias names and then continue with the actual certificate.
- Applying the certificate keystore in PAM360.
- Login to PAM360 as an administrator.
- Navigate to Admin >> Configuration >> PAM360 Server.
- Choose PKCS12 or PKCS11 as the Keystore Type.
- Click on Browse and select your PFX/P12 file.
- Provide the correct keystore password and save the configuration.
- Restart PAM360 service to bring the certificate change into effect.
Password Synchronization
1. Can I change resource passwords from the PAM360 console?
Yes. PAM360 can remotely reset the passwords of various end points. PAM360 supports both agent-based and agent-less modes of changing passwords. Refer this document for more information.
2. When do I use the agent and agent-less modes for password synchronization?
Let us first look at the requisites for both the modes:
The agent mode requires the agent to be installed as a service in each end point and run with administrative privileges to perform password reset operations. The agent uses one-way communication using outbound traffic to reach the PAM360 server.
For the agent less mode, you must supply administrative credentials to perform the password changes. For Linux, you must specify two accounts- one with root privileges and the other with normal user privileges that can be used to login remotely. Telnet or SSH service must be running on the resources. For Windows domain, you must supply the domain administrator's credentials. For Windows and Windows Domain, PAM360 uses remote calls, so relevant ports must be open on the resource.
Based on this, you can choose which mode you want for your environment, indicated by the following tips:
Choose the agent mode when:
- You do not have administrative credentials stored for a particular resource in PAM360,
- You do not have the required services running on the resource (Telnet / SSH for Linux, RPC for Windows),
- You run PAM360 in Linux and want to make password changes to a Windows resource.
Choose agent less mode in all other cases as it is a more convenient and reliable way of doing password changes.
3. Can I enable agent less password reset if I add my own resource type for other distributions of Linux / other versions of Windows?
Yes, you can. As long as your resource type label contains the string 'Linux' or 'Windows', you can still configure agent less password reset for those resources.
Example of valid resource type labels to enable password reset:
Debian Linux, Linux - Cent OS, SuSE Linux, Windows XP Workstation, Windows 2003 Server
4. Is there a way to carry out remote password synchronization for custom resource types that do not come out of the box in PAM360?
PAM360 supports remote password reset for custom resource types through SSH command sets, password reset plugins, and password reset listeners.
- SSH Command Sets: For SSH-based devices, you can build command-based executables directly from PAM360 using a set of default or customized SSH commands. These command sets can then be associated with the respective SSH device accounts that do not come out of the box with PAM360 to perform their password resets without the need for a CLI.
- Password Reset Plugin: You can build your own implementation class and run it via PAM360 to enforce automatic password resets of custom resource types. With the plugin, you can also leverage access control for legacy accounts and automatically reset passwords instantly upon usage. This way, the passwords of these accounts will serve as one-time passwords that are reset after every use via the associated plugin.
- Password Reset Listeners: Listeners are custom scripts or executables that can be invoked for local password changes, as well as to reset the passwords of custom resource types for which remote password reset is not supported out-of-the-box by PAM360. You can configure listener scripts individually for each resource type including the custom ones.
5. How do I troubleshoot when password reset does not happen?
In the agent mode:
- Check if the agent is running by looking at the Windows active process list for the entry 'PAM360Agent.exe' or the presence of a process named 'PAM360Agent' in Linux.
- Check if the account in which the agent is installed has sufficient privileges to make password changes.
In the agent less mode:
- Check if the right set of administrative credentials have been provided and the remote synchronization option is enabled.
- Check if the necessary services are running on the resource (Telnet / SSH for Linux, RPC for Windows).
- Check if the resource is reachable from the PAM360 server using the DNS name provided.
6. How do I reset domain passwords when Windows domain password reset fails with an error message: "The authentication mechanism is unknown"?
This happens when PAM360 is run as a Windows service and the 'Log on as" property of the service is set to the local system account. Change it to any domain user account to be able to reset domain passwords. Follow the instructions below to effect that setting:
- Go to the Windows Services Applet (from Control Panel --> Administrative Tools --> Services).
- Select the 'ManageEngine PAM360' service, right-click --> choose 'Properties'.
- Click the 'Log On' tab and choose 'This Account' radio button and provide the username and password of any domain user - in the format <domainname>\<username>.
- Save the configuration and restart the server.
7. What are the prerequisites for enabling Windows Service Account Reset?
Before enabling windows service account reset, ensure if the following services are enabled in the servers where the dependent services are running:
- Windows RPC service should have been enabled.
- Windows Management Instrumentation (WMI) service should have been enabled.
8. Does domain SSO work across firewalls / VPNs?
The domain Single Sign On (windows integrated authentication) is achieved in the Windows environment by setting non-standard parameters in the HTTP header, which are usually stripped off by devices like firewalls / VPNs. PAM360 is designed for use within the network. So, if you have users connecting from outside the network, you cannot have SSO this enabled.
Backup and Disaster Recovery
1. Can I move PAM360 from one server to another?
Yes. you can migrate PAM360 to another server by following the below steps:
- Stop PAM360 service, exit tray icon.
- Make sure that the Postgres process is not running in Task Manager.
- Copy and move entire PAM360 directory to the new server.
- Open command prompt with admin rights and navigate to <PAM360 HOME>\bin directory. Execute the command PAM360.bat install. (This will install PAM360 service.)
- Move the encryption key(PAM360_key.key) to the new server and specify the correct location of it in PAM360/conf/manage_key.conf file. Click here for more information about the encryption key.
- Go to services console, provide a service account and start PAM360 service.
- If you want the tray icon, Go to the <PAM360 HOME>, right click on PAM360.exe and select "Run as Administrator".
Now you should be able to access the PAM360 web page using the new server name in the URL.
2. Can I setup disaster recovery for the PAM360 database?
Yes, you can. PAM360 can periodically backup the entire contents of the database, which can be configured through the PAM360 console. Refer this document for more details.
3. Where does the backup data get stored? Is it encrypted?
All sensitive data in the backup file are encrypted using the 7-Zip utility, which has options to encrypt and compress data by the AES256 algorithm. The encrypted data is stored under the '<PAM360_Install_Directory/backUp>' directory as a .zip file. We recommended you to store the backup in secure, secondary storage for disaster recovery.
Licensing
1. What is the Licensing Policy for PAM360?
There are three license types:
- Evaluation download / Trial Version - You can straightaway download and install this trial version. It is fully functional, capable of supporting a maximum of 5 administrators and you can evaluate all the features for 30 days.
- Free Edition - Licensed software that allows you to have 1 administrator and manage up to 10 resources. Valid forever.
- Registered Version - You get the Enterprise edition, and Licensing is based on the Number of Administrators. This is useful if you require more enterprise-class features such as auto discovery of privileged accounts, integration with ticketing systems and SIEM solutions, jump server configuration, application-to-application password management, out-of-the-box compliance reports, SQL server / cluster as backend database, etc.
Note: PAM360 comes with five user roles - Administrator, Password Administrator, Privileged Administrator, Password Auditor and Password User. The term 'administrator' denotes Administrators, Password Administrators and Privileged Administrators. So, licensing restricts the number of administrators as a whole, which includes Administrators, Password Administrators and Privileged Administrators. There is no restriction on the number of Password Users and Password Auditors. To get more details on the five user roles, refer this section of our help documentation.
2. Can I buy a permanent license for PAM360? What are the options available?
Though PAM360 follows an annual subscription model for pricing, we also provide perpetual licensing option. The perpetual license will cost three times the annual subscription price, with 20% AMS from the second year. Contact sales@manageengine.com for more details.
3. How can I apply my license file?
- Login as an administrator in the PAM360 web interface. Click the 'My Account' icon at the top right corner and select License from the drop down.
- Browse to add the license file and click on Upgrade. Your new license file is added.
- Now, restart the PAM360 service for the license to take effect. You can check to see if the license is applied and other details under the same section.
4. I want to have a High Availability setup with multiple servers. Will a single license suffice for this?
Yes, if you buy a single license, you are entitled to have the High Availability setup. You can apply the same license on the Primary as well as the Secondary servers. Follow the below steps:
5. Can PAM360 support more than 1000 administrators?
Yes, very much. If you want a license with more than 1000 administrator users, please contact sales@manageengine.com for more details.
6. Can I extend my evaluation to include more administrator users or for more number of days?
Yes. Fill in the required details in the website and we will send you the license keys.
7. How many resources and accounts can I manage from the PAM360 application?
In PAM360 licensing, there are no limitations on managing resources and accounts. You have the flexibility to add or import any number of resources, depending on the supported resource types, and you can manage accounts according to your needs without any restrictions.
SSH Key Management
1. Are there any differences in the way SSH user accounts and SSH service accounts are managed using PAM360?
No. PAM360 adopts the same approach for managing SSH user accounts and SSH service accounts. The only difference is that during resource discovery, if service / root account credentials are provided to establish connection with the resource, you acquire extended privileges to import and manage keys from all user accounts in the resource.
Whereas, when connection to the resource is established using user account credentials, you get key management privileges only for SSH keys present in that particular account.
2. Is there any way to view SSH keys that were not rotated?
Yes. We have a dashboard that displays the number of keys that were not rotated for the predefined time period as specified in the notification policy.
3. Does PAM360 support management of digital keys other than SSH keys and SSL certificates?
PAM360 houses a key vault called "Key Store" which facilitates the storage and management of any type of digital key. However, the option to discover and import is limited to SSH keys and SSL certificates only, and isn't available for other types of digital keys.
SSL Certificate Management
1. Is there any certificate type that PAM360 is incompatible with?
No. PAM360 supports all X.509 certificate types.
2. Is it possible to automatically identify and update the latest version of certificates in PAM360' certificate repository?
Yes. You can create scheduled tasks to perform automatic certificate discovery through which you can import and replace old certificates from target systems with their updated versions in PAM360' certificate repository. Click here for a detailed explanation on creating schedules.
3. Does the Linux version of PAM360 support certificate discovery from Active Directory and MS Certificate Store?
No, it doesn't. The AD User Certificate and MS Certificate Store tabs appear only in the Windows version of PAM360.
4. Is it possible to track the expiry of certificates with the same common name in PAM360' certificate repository?
PAM360 differentiates certificates by their common names and records certificates with same common names as a single entry in its certificate repository. We've designed it this way because PAM360 licensing is based on the number of certificates and we don't want customers to spend many license keys for the same certificate.
However, if there's a need to manage both the certificates separately, you can do so by listing them as separate entries in PAM360' certificate repository. Once listed, the newly added certificate will be counted for licensing.
To add a certificate with the same common name as a separate entry in certificate repository,
- Navigate to the Certificates tab and click Certificates, and click the Certificate History icon beside the certificate.
- Click the 'Certificate Settings' icon beside the required version of the certificate and click on 'Manage Certificate'.
- The selected version is listed as a separate certificate in the certificate repository.
- In case you want to manage only one version of the certificate, click 'Certificate Settings' icon beside the required version and choose 'Set as current certificate' option.
5. How do I import private key for a certificate?
Follow the steps below to import a certificate's private key into PAM360.
- Navigate to the Certificates tab and click Certificates.
- Select the certificate for which you need to import the private key.
- Click the Import Keys option from the More drop down menu at the top.
Browse for the file that contains the private key, enter the keystore password, and click on 'Import'. The private key will be imported and attached to the selected certificate.
6. How do I deploy a certificate to Certificate Store and map it to the application that uses the certificate?
PAM360 facilitates certificate deployment through which you can deploy certificates from its repository to target server's Microsoft Certificate Store.
Click here for step-by-step explanation on certificate deployment.
To map the certificate to its corresponding application, you've to manually restart the server on which the application is running for the change to take effect.
7. Does PAM360 support subnet based certificate discovery?
No. PAM360 currently doesn't support subnet based SSL certificate discovery.
8. Does PAM360 support automatic scheduling for certificate discovery from MS Certificate Store?
No. Currently, PAM360 doesn't support automatic scheduling for certificate discovery from MS Certificate Store.
9. Are certificate related alert emails generated for all versions of a certificate (the ones that show in "Certificate History" also) or only for those certificates listed in PAM360's certificate repository?
Email notifications are generated ONLY for certificates listed in PAM360's certificate repository and NOT for different versions of a certificate displayed in "Certificate History" section.
10. Are the certificates issued by the company's internal Certification Authority (CA) counted for licensing?
Yes. All types of SSL certificates, SSH keys and any other digital key being managed using PAM360 are taken into account for licensing. There's a dashboard widget "License Details" that provides insights on the type and number of digital identities being managed using PAM360 that will be taken into account for licensing.
11. How do I import a root certificate into PAM360?
To import a root certificate, open the Command Prompt and navigate to the <pam360_server_home>\bin directory and execute the following command:
For Windows:
importCert.bat <Absolute Path of certificate>
For Linux:
importCert.sh <Absolute Path of certificate>

