Why organizations should use PAWs?
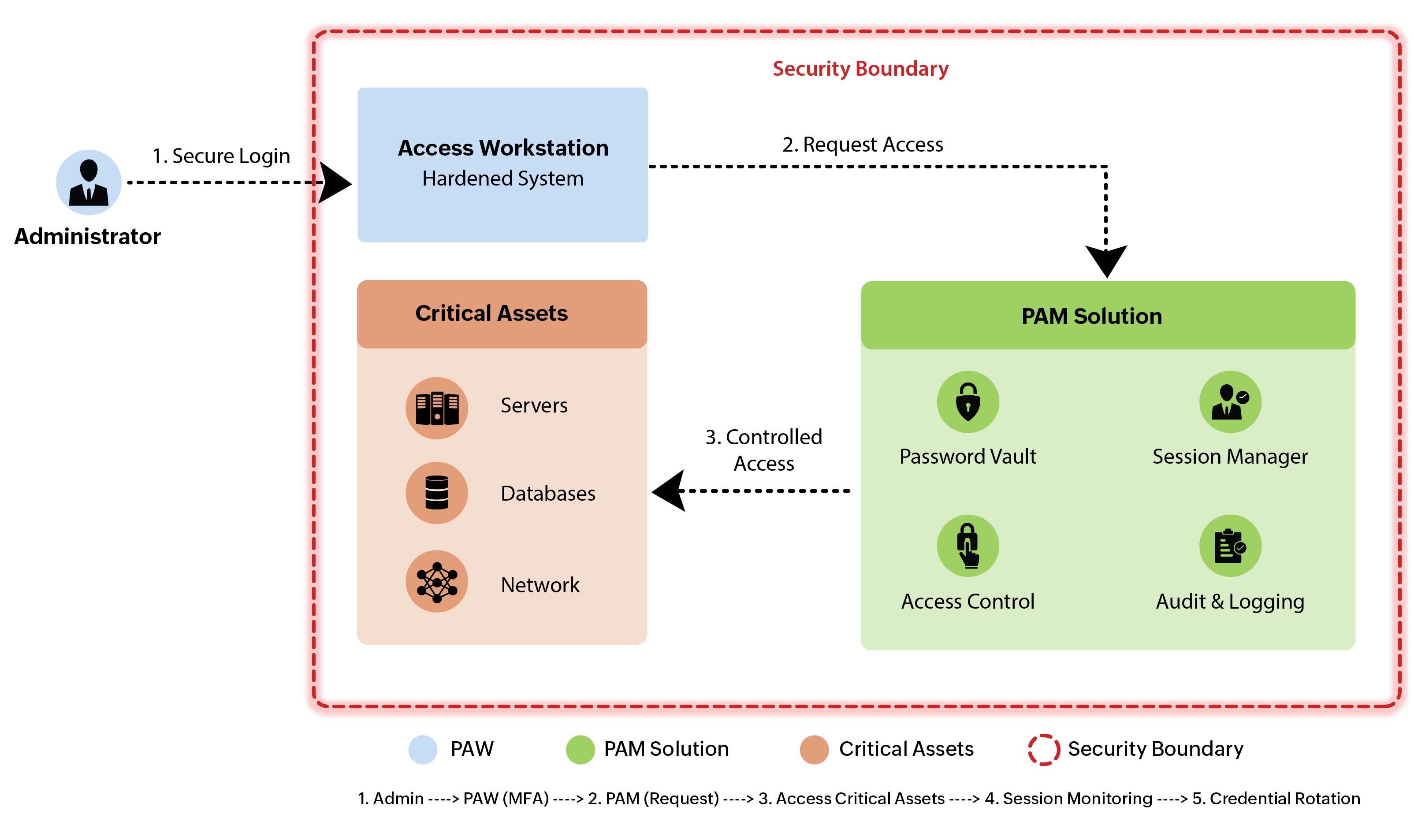
The primary purpose of a PAW is to minimize the risk of security breaches, especially those stemming from credential theft or privilege misuse targeting sensitive accounts. PAWs are often used by IT administrators, security professionals, and other users who need to perform privileged tasks. PAWs can also be used to provide remote access to privileged systems, which can help to reduce the risk of exposure.
Authorized users are allowed to use PAWs to gain administrative access to privileged accounts through a privileged access management tool that manages and governs access to business-critical endpoints.
Configuring a PAW—basic requirements
PAWs are dedicated machines that are hardened using a layered approach to offer the highest security to privileged accounts and resources. They are typically configured with several security controls, including, but not limited to:
- 01
Application and command allow-listing
Only a predefined set of applications and commands are allowed to run on a PAW. This helps to reduce the attack surface by restricting these environments to select users.
- 02
Network isolation
PAWs are typically isolated from the rest of the network, which makes it more difficult for attackers to reach them.
- 03
Multi-factor authentication (MFA)
Users must utilize MFA before gaining access to a PAW.
- 04
System hardening
PAWs are configured with security best practices, such as keeping software up-to-date and disabling unnecessary services.
Since PAWs are specifically used for privileged access activities, these endpoints cannot be used for general user activities, such as internet browsing, emails, team collaborations, and other application usage. Further, PAWs incorporate application allow-listing and other forms of administrative restrictions, which means they will not accept connections from external networks or devices. All these aforementioned controls are offered by PAM solutions.
Differences between a jump server and a privileged access workstation
- TopicPrivileged access workstationJump servers
- What is it?A dedicated workstation used by authorized users to perform administrative tasks that require privileged access. It is designed to be highly secure and isolated from potentially risky activities.A hardened server specifically configured to act as a gateway or intermediary between client and server endpoints.
- What is it used for?Solely used to perform to privileged tasks and not used for general web browsing, email, or other potentially risky activities.Users connect to the jump server first, typically via SSH or RDP, before accessing other endpoints in the network.
- How are they connected?They are not connected to external Wi-Fi networks or external USB devices to minimize potential attack vectors. PAWs are designed to only accept connections from privileged operating systems.Typically used to allow administrators to securely access internal network resources from external locations.
- What are some of the use cases it is utilized for?Used for tasks that require the highest level of security, such as managing Active Directory, or to install software on a server.Used to access a production server to troubleshoot an issue.
Key features that a PAM software should offer to meet the security needs of PAW users
Following are top controls that a PAM software should provide to enable PAW users.
- 01
MFA
Add an extra layer of security by mandating multiple levels and modes of authentication.
- 02
Privileged account governance
Automatically discover, onboard, manage, and share privileged accounts and credentials pertaining to different types of endpoints, such as operating systems, databases, applications, network devices, hypervisors, and more. Enforce granular access controls, allowing only authorized users to log in and perform specific privileged tasks.
- 03
Privileged session management
Monitor, record, and archive privileged sessions. Audit these sessions in real-time to aid in forensic audits, and terminate sessions automatically as or when users are found to be engaging in malicious activities.
- 04
Role-based access control
Employ the principle of least privilege, where users are granted access to mission-sensitive resources and accounts based on their roles and requirements.
- 05
Just-in-time (JIT) access
Provide users with time-limited, elevated access to privileged endpoints based on their requirements. This a critical module in PAM software, which includes revoking privileges and rotating the passwords of sensitive endpoints after every use.
- 06
Secure remote access
Enable secure, one-click access from PAWs to remote endpoints, thereby ensuring that administrative users can access business-critical systems from external locations without compromising security.
- 07
Policy enforcement and compliance reporting
Enforce password policies based on internal security requirements, and provide reporting capabilities to demonstrate compliance with industry regulations and internal policies.
- 08
Application allow-listing and command control
Enable users to run allow-listed applications and commands with varying levels of privileges to reduce the risk of malicious software execution.
- 09
Dynamic risk assessment and anomaly detection
Continuously monitor users and devices based on numerous security parameters to derive trust scores. Use these scores to automatically generate access policies based on their security posture. Leverage behavioral analytics and ML to identify unusual patterns of behavior, and proactively isolate threat actors.
Security benefits of privileged access workstations
- 01
Enhanced protection against cyber threats
Privileged access workstations are designed with advanced security measures, such as isolation from less secure networks and robust access controls, which significantly reduce the risk of cyber attacks. By limiting access to sensitive systems and data, PAWs help prevent unauthorized access and potential breaches.
- 02
Reduced attack surface
PAWs minimize the attack surface by removing unnecessary software and services, and by applying stringent security configurations. This hardening process ensures that only essential functions are enabled, thereby reducing vulnerabilities that could be exploited by attackers.
- 03
Improved monitoring and auditing
PAWs often come with comprehensive monitoring and auditing capabilities. These features allow for real-time tracking of user activities and system changes, enabling quick detection and response to suspicious behavior. Regular audits ensure compliance with security policies and help maintain the integrity of the system.
- 04
Secure access management
With features like multi-factor authentication (MFA) and privileged access management, PAWs ensure that access to critical systems is tightly controlled and monitored. These measures add layers of security, making it significantly harder for unauthorized users to gain access, even if they manage to compromise one form of identification.
Privileged access workstation (PAW) best practices
Considering that the security of privileged access workstations is essential for safeguarding critical data and systems against cyber threats, following are comprehensive best practices for securing PAWs:
- 01
Isolation and segmentation
PAWs should be kept separate from the general network and other less secure systems. This separation can be achieved through network segmentation, which involves creating smaller, isolated network segments. Each segment can have its own security measures, thereby limiting the potential spread of breaches. PAWs should be placed in the most secure segment.
- 02
OS hardening
The operating system of a PAW should be hardened to minimize its exposure to attacks. This includes removing unnecessary software, disabling non-essential services, and applying the latest security patches. The system should be configured to require complex passwords and to lock out users after several failed login attempts.
- 03
Multi-factor authentication (MFA)
MFA strengthens security by necessitating that users supply two or more types of identification to access the PAW. These identification types can encompass passphrases, OTP, biometrics, and so on. If a credential is breached, the attacker would still need the second form of identification to gain entry.
- 04
Privileged access management
PAM solutions help manage and monitor privileged access. They can enforce policies, such as requiring approval for access to certain systems, and provide detailed logs of all privileged activities. Some PAM solutions also offer session recording, which is useful for auditing and forensic investigations.
- 05
Regular auditing and monitoring
Conducting regular audits ensures that security policies are followed and that there are no unauthorized changes to the PAW. Monitoring tools can provide real-time alerts for suspicious activities, such as multiple failed login attempts or access attempts outside of normal working hours.
- 06
Workforce training and awareness
Users of PAWs should receive training on security best practices, such as creating strong passwords, recognizing phishing attempts, and knowing what to do if they suspect their account has been compromised. Regular security awareness training helps keeps security atop business operations.
- 07
Data encryption
All data stored on the PAW, as well as data transmitted to and from the PAW, should be encrypted. This protects the data even if the PAW is compromised. Full disk encryption can protect data at rest, while protocols like TLS can protect data in transit.
- 08
Periodic backups
Regular backups ensure that data can be recovered in the event of a ransomware attack or other data loss incidents. Backups should be stored securely and tested regularly to ensure they can be restored quickly and accurately.
- 09
Incident response plan
This ensures a quick and effective response in the event of a security incident. The plan should outline the steps to be taken, such as isolating the affected system, notifying the appropriate personnel, and preserving evidence for forensic investigation.

