

The successful deployment of BitLocker encryption depends on meeting specific system requirements and configurations. These conditions ensure that BitLocker can function optimally and provide the desired level of protection. BitLocker pre-requisites are criteria a computer must adhere to before deploying a BitLocker policy to initiate encryption. This article will delve into the essential criteria a computer must fulfill before implementing a BitLocker policy. Below are the various criteria:
BitLocker encryption might not be available in all Windows versions used in your organization. Here's a list of Windows operating systems that support BitLocker:
BitLocker is not automatically enabled on servers; however, you can manually enable it to start encryption. Below are common issues you might encounter when enabling BitLocker on a Windows Server machine.
BitLocker is disabled in Server OS computers by default. It can be enabled through the Server Manager and Command Prompt.
Perform these steps to enable the BitLocker feature through Server Manager and utilize the BitLocker Recovery Key storing feature:
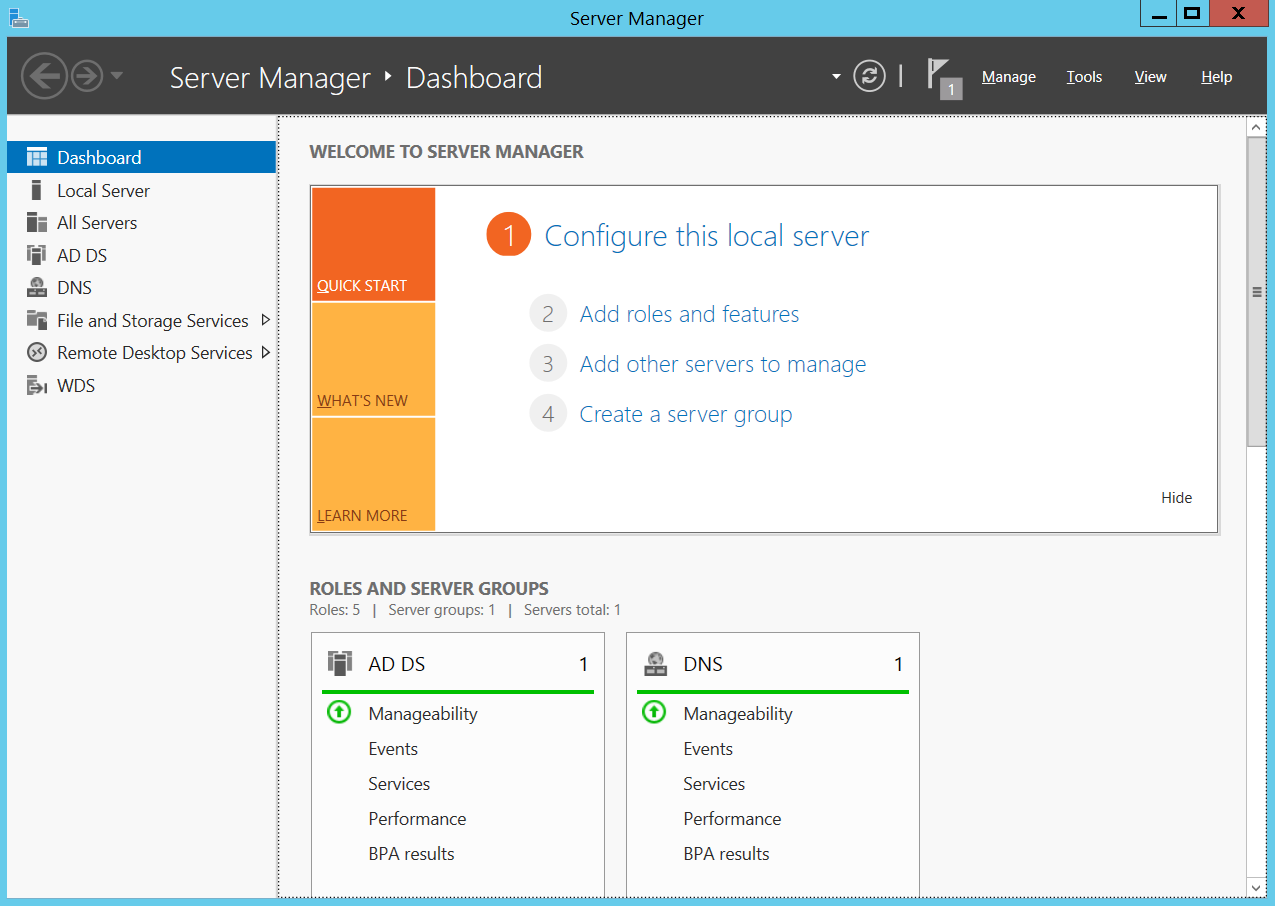
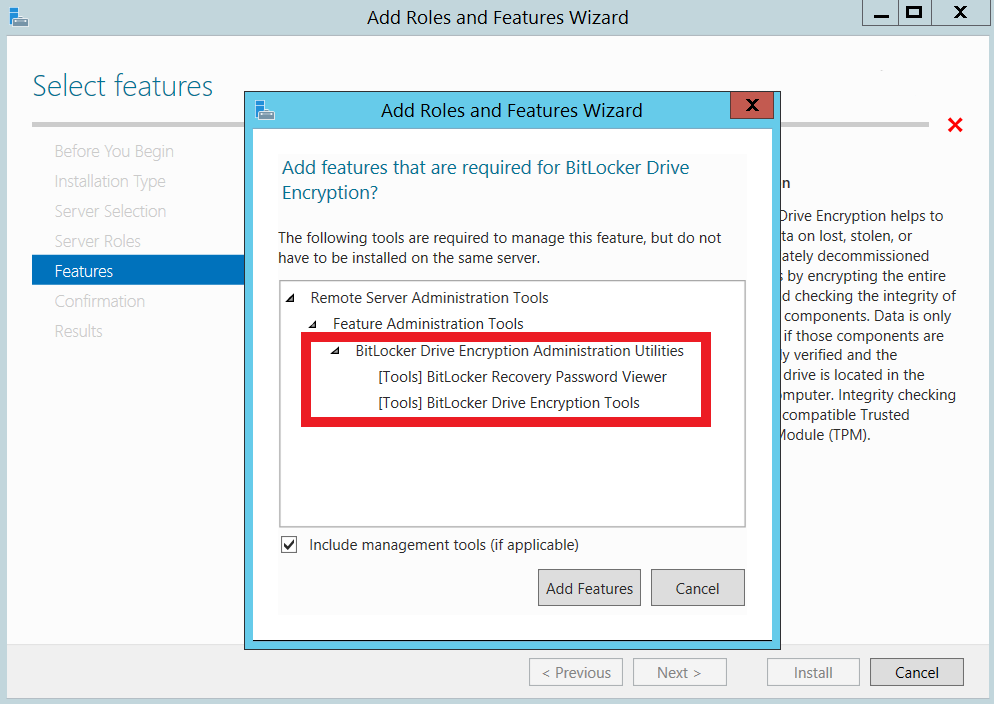
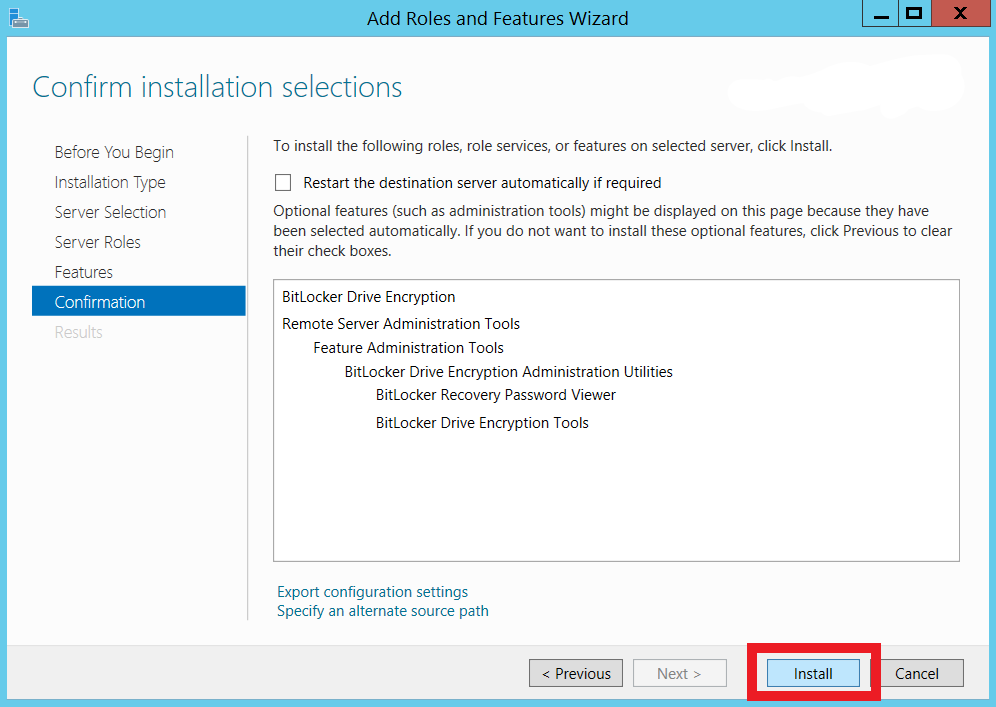
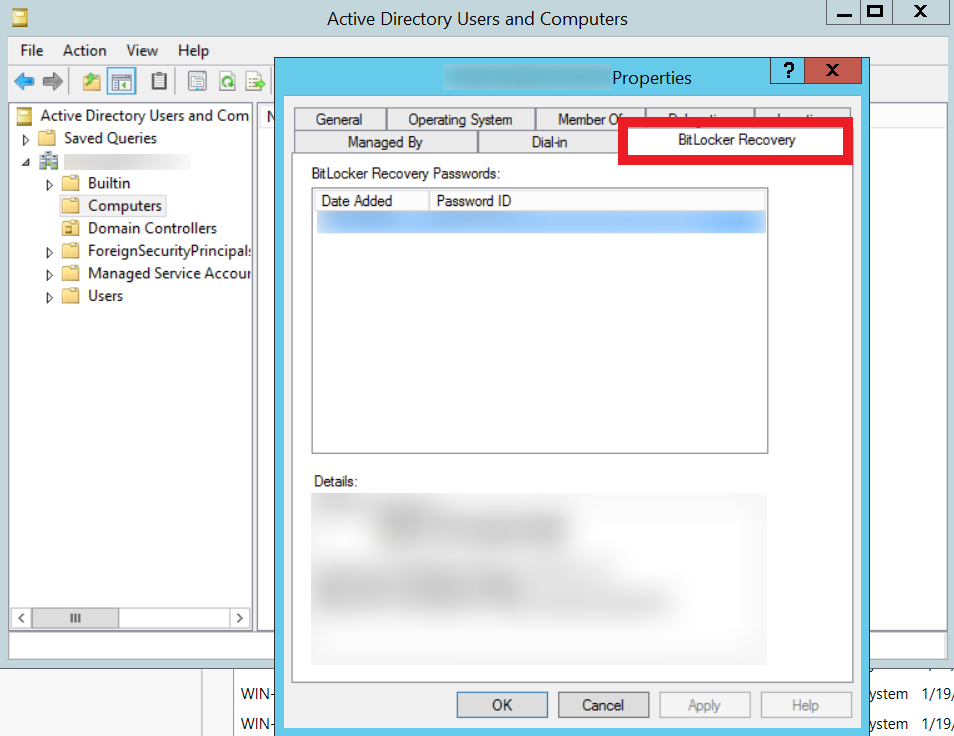
Perform these steps to enable the BitLocker feature through the Command prompt:
Windows Management Instrumentation (WMI) is Microsoft's remote protocol for management tasks and information retrieval. To troubleshoot common errors while enabling BitLocker, perform the following steps:
The Trusted Platform Module (TPM) is a microchip that encrypts drives using cryptographic keys to mitigate dictionary attacks. If you have partial ownership of the TPM, BitLocker cannot use cryptographic keys; full ownership is required for TPM-based encryption.
To gain full ownership, clear the TPM as explained here. Clearing TPM will trigger the OS to automatically reinitialize and acquire full ownership.
NOTE - Clearing TPM can cause loss of stored cryptographic keys. Refer to this link for precautions before clearing TPM to safeguard your data.
TPM-aided BitLocker encryption is supported only in Unified Extensible Firmware Interface (UEFI) mode. If you are using Legacy or Compatibility Support Mode (CSM), switch to UEFI mode to facilitate TPM-based encryption, as explained here.
Group Policy (GPO) settings can control Microsoft BitLocker's preliminary actions. Sometimes, the existing GPO settings of your computer can counteract
Details of BitLocker Group Policy Settings for your reference.
Now you can configure a BitLocker policy for successful encryption. Refer to this document for a detailed guide on creating and configuring BitLocker policies.
If you have any further questions, please refer to our Frequently Asked Questions section for more information.