

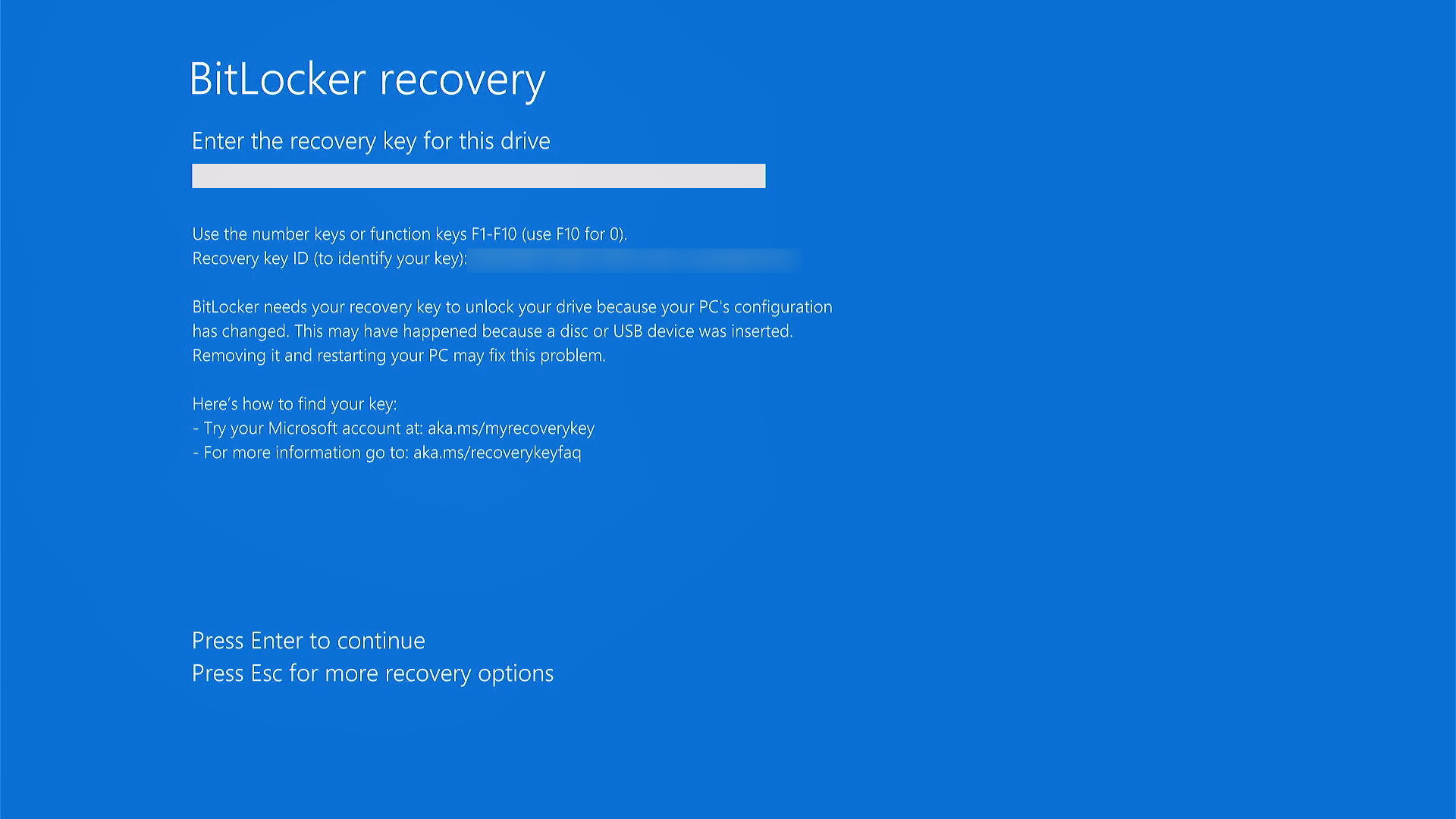
A recovery key is a 48-bit string used to unlock an encrypted hard drive when the password is forgotten. Even if the hardware is severely damaged, the drive's contents can still be recovered by installing it in another computer and providing the correct recovery key. It is also useful when the user forgets their password.
Once a BitLocker encryption policy is deployed, the configuration process begins during the PC boot, generating a recovery key automatically. Admins can create or modify BitLocker policies to ensure the recovery key is updated in the domain controller.
Here's the view of the recovery key being asked on bootup:
NOTE: Both Windows AD and Azure AD support recovery keys backup.
To simplify recovery key retrieval, it is recommended to back up the key in the domain controller. Follow these steps:
NOTE: Enabling this option ensures that every newly generated key is automatically updated in Active Directory.
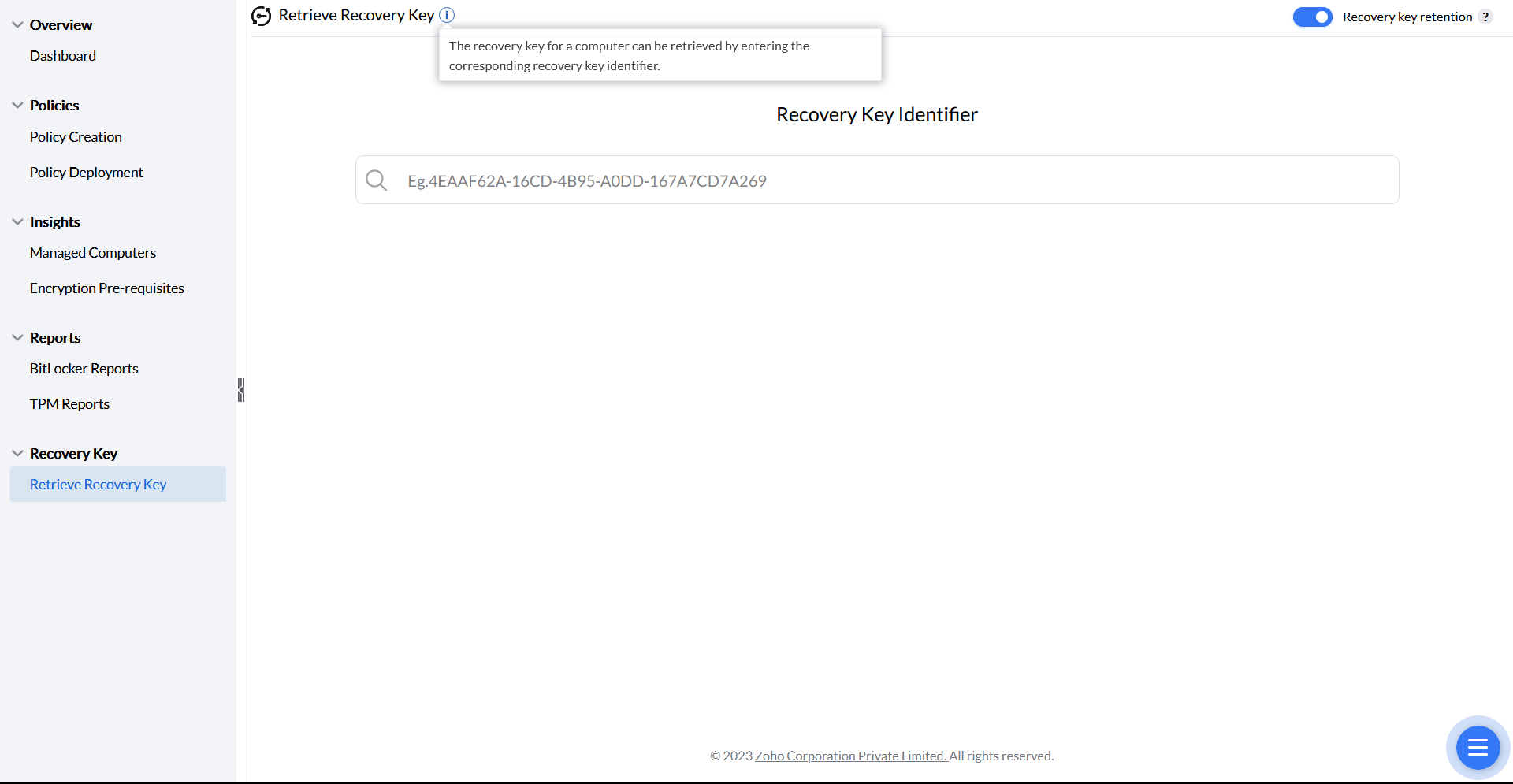
The recovery key is automatically generated during BitLocker configuration and can be backed up in AD for domain users. If the end user forgets their PIN or passphrase, the admin can retrieve the recovery key using these steps:
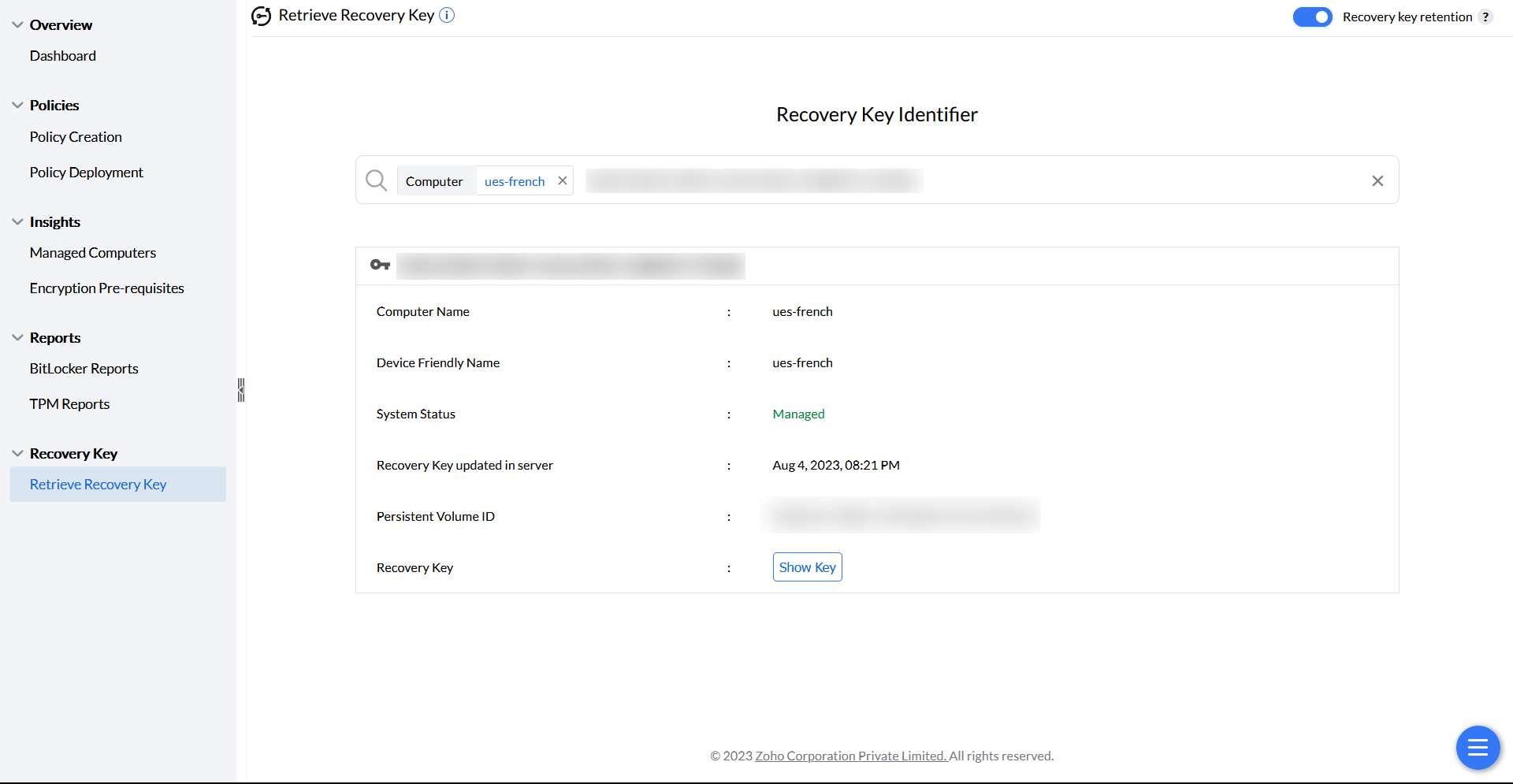
Note: A new recovery key is automatically generated upon the next system reboot if the existing key is accessed via Endpoint Central after deploying a BitLocker policy.
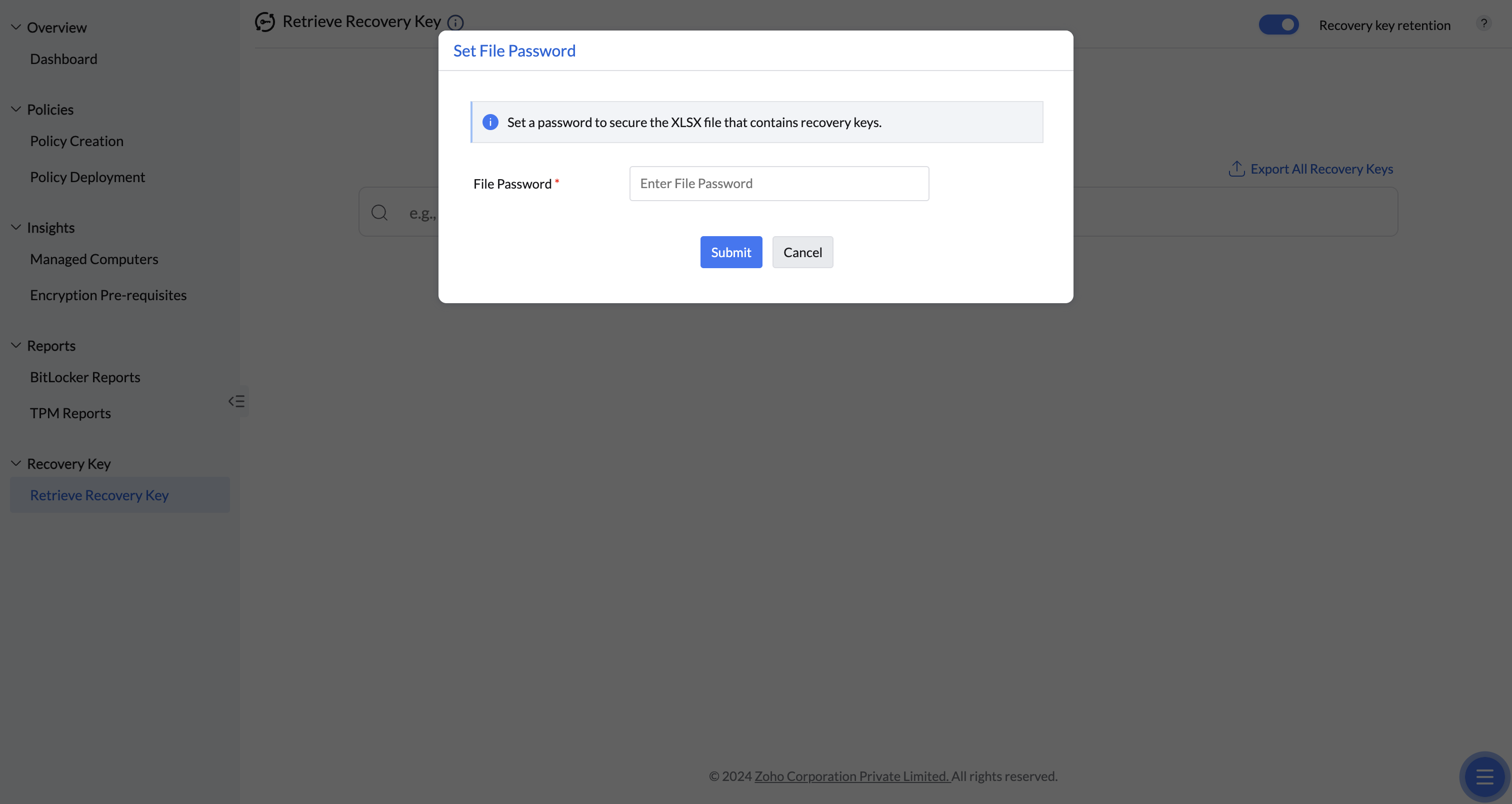
The Export Recovery Keys functionality allows you to create a secure backup of all machine recovery keys in a password-protected XLSX file. This streamlines the recovery keys retrieval process, saving time and effort.
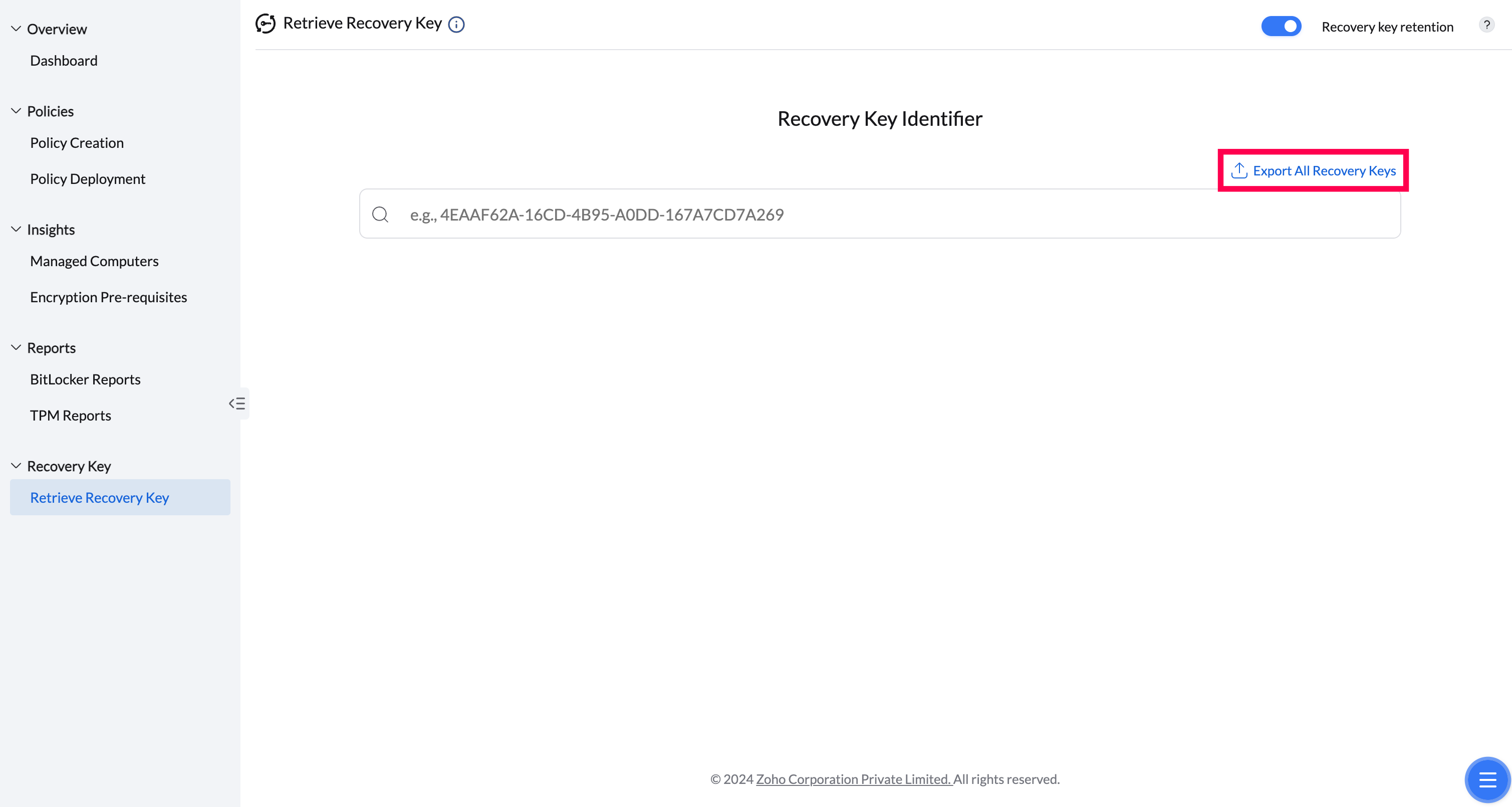
You can also define the file password to secure the file.
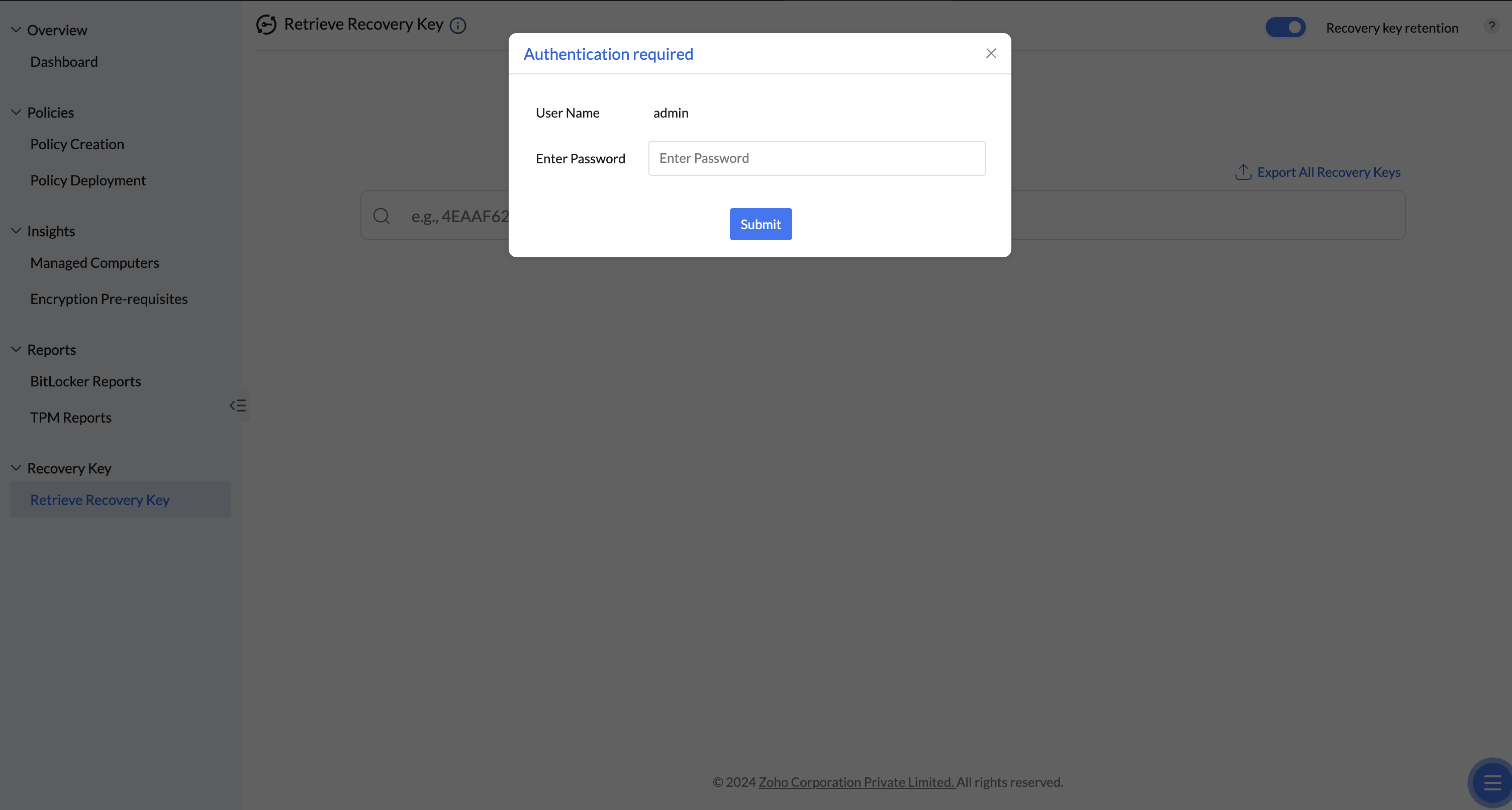
To ensure the security of sensitive recovery information, user authentication is required to download the file.
Admins can manage Active Directory objects using the Active Directory Users and Computers (ADUC) console, which can also be used as a Remote Server Administration tool (RSAT) to to retrieve the recovery key from a Windows machine. Follow these steps:
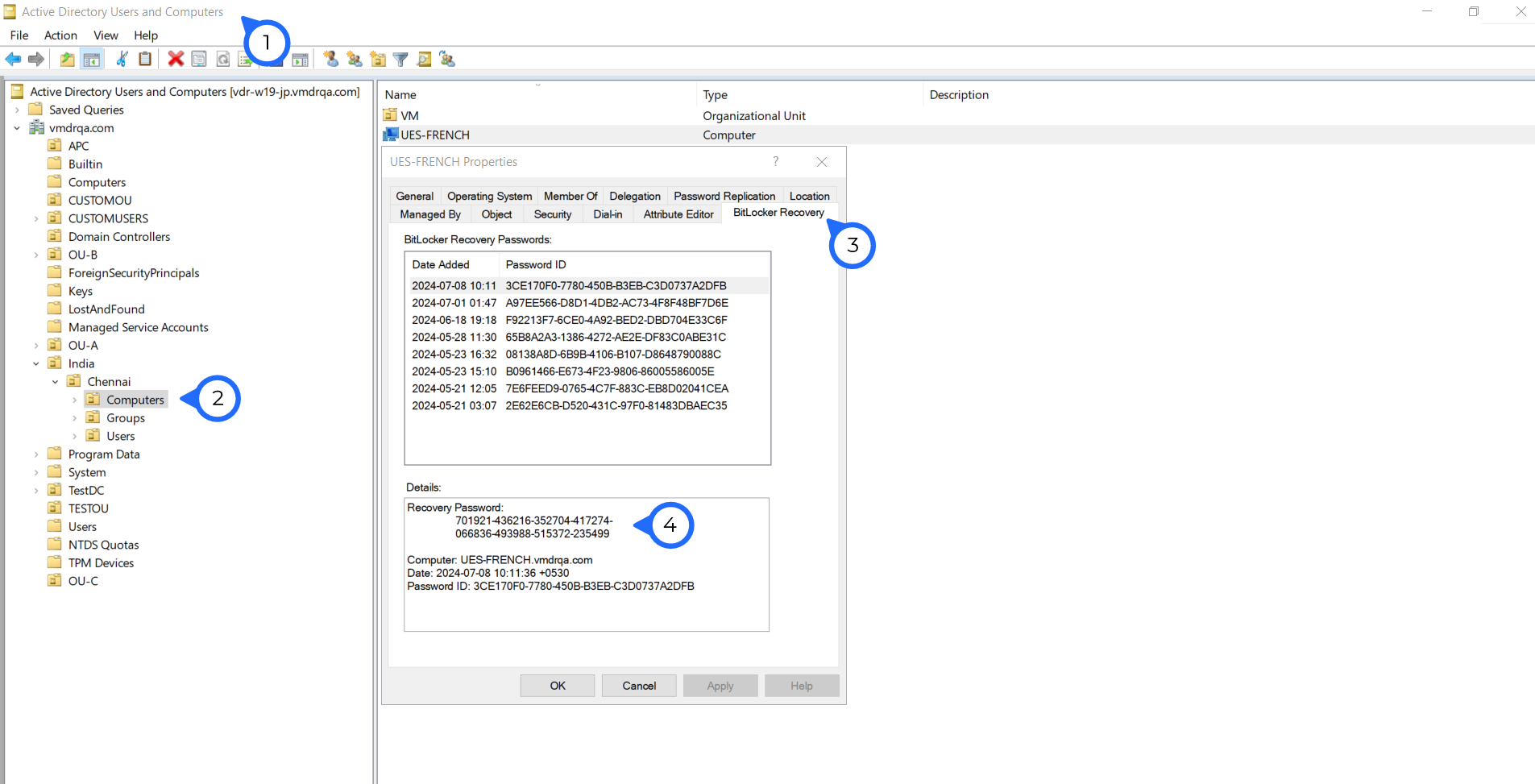
You have found the Recovery key of a Windows machine using ADUC successfully.
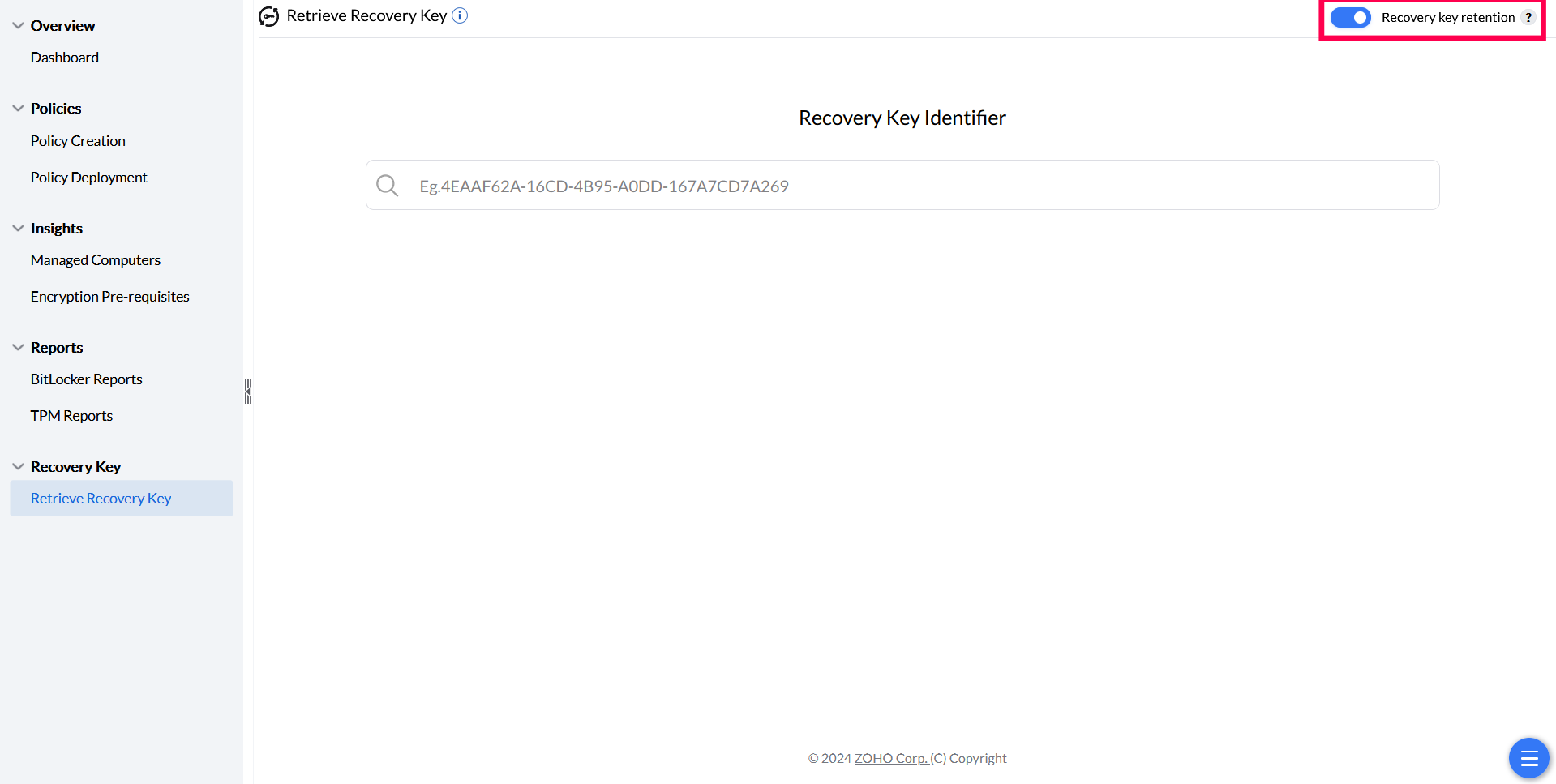
The recovery key is critical for data security. Even after retaining the key in the Endpoint Central server, it can be backed up in the customer’s Active Directory (both Azure AD and on-premise AD). If a computer is removed from SoM, the recovery key is retained in the server for up to one year and can be retrieved using the recovery key identifier. To enable recovery key retention, toggle the option on the Retrieve Recovery Key page. Encryption will not start until the recovery key is successfully stored in the server.
If you have any further questions, please refer to our Frequently Asked Questions section for more information.
d