Splunk Integration
When Endpoint Central is integrated with Splunk, both vulnerability data and audit logs are forwarded to Splunk. This provides administrators with a consolidated view of all detected vulnerabilities along with records of actions performed through the console, such as configuration changes, deployments, and administrative activities. Splunk’s analytics can then be used to monitor these events, identify patterns or anomalies, and generate reports and dashboards for auditing, compliance, and security monitoring purposes.
Note:
- Currently, only Vulnerability data and Action Log Viewer data from Endpoint Central are posted to Splunk.
- Vulnerability data is applicable only for the Endpoint Central server with Security edition or Vulnerability Add-On purchased and version starting from 11.3.2430.01 and above.
- Action Log Viewer data is applicable for Endpoint Central version starting from 11.4.2533.01 and above.
Installing the ManageEngine Endpoint Central add-on in Splunk
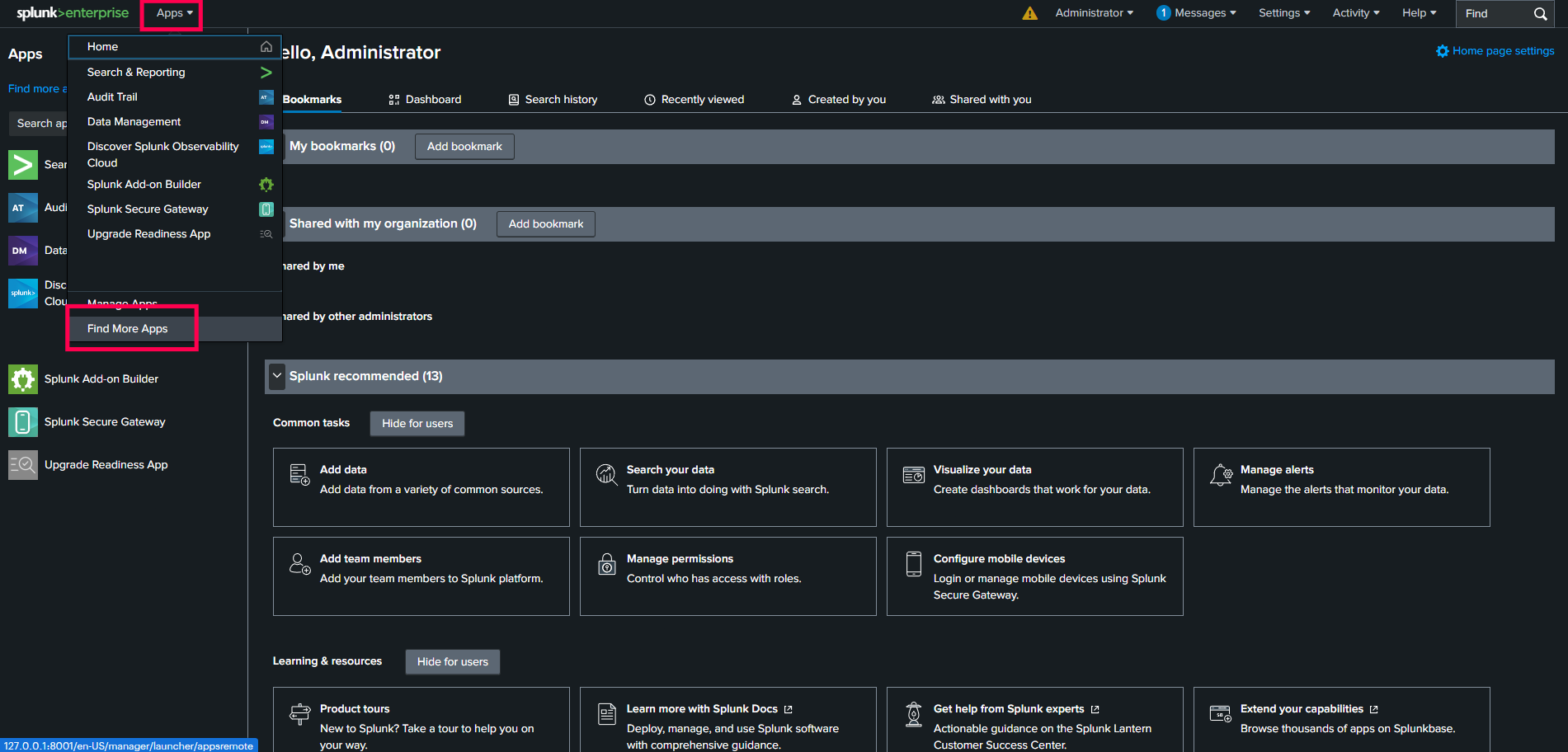
- Navigate to the Splunk Home page.
- In the Header menu, click on Apps.
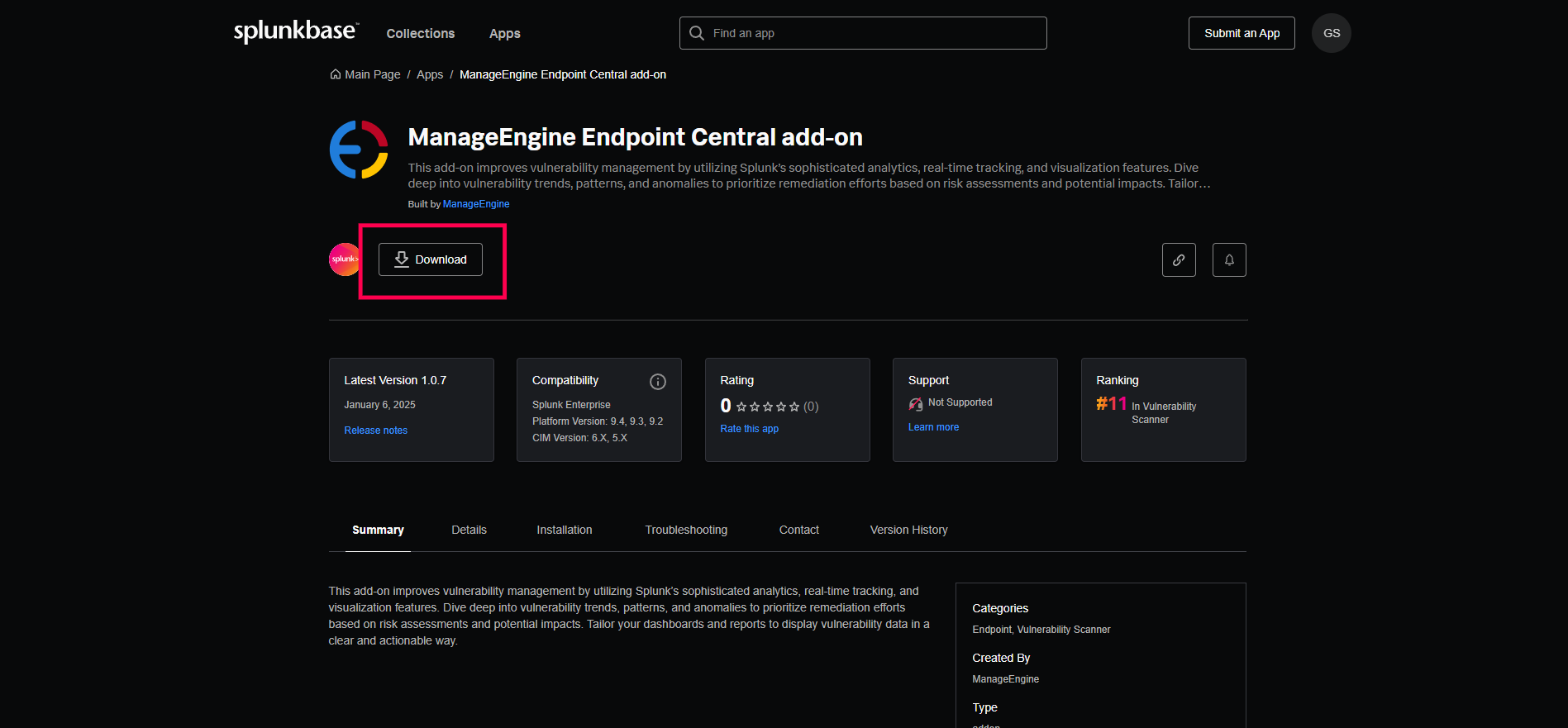
- Select Find More Apps to be redirected to Splunk's Marketplace.
- Search for the ManageEngine Endpoint Central Add-On app.
- Click Download and enter your username and password.
- Click Agree and Install. Now you can access the application from the Splunk home page or the Apps menu.
Creating a CA-Bundle (Certificate Authority bundle) for SSL validation
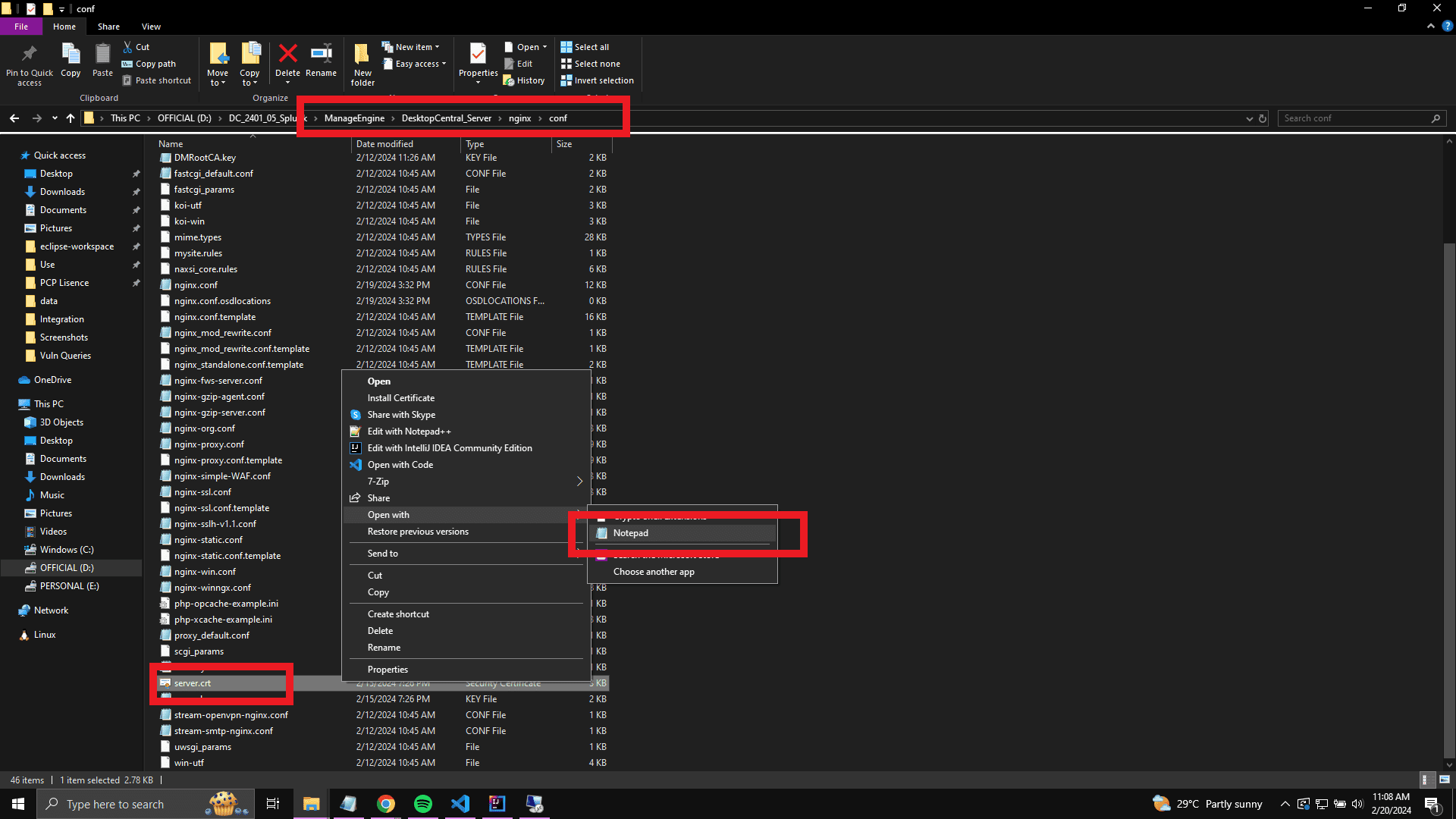
- Navigate to the Endpoint Central server installation directory on your system. Then, go to the %EC Home Dir% → nginx → conf folder.
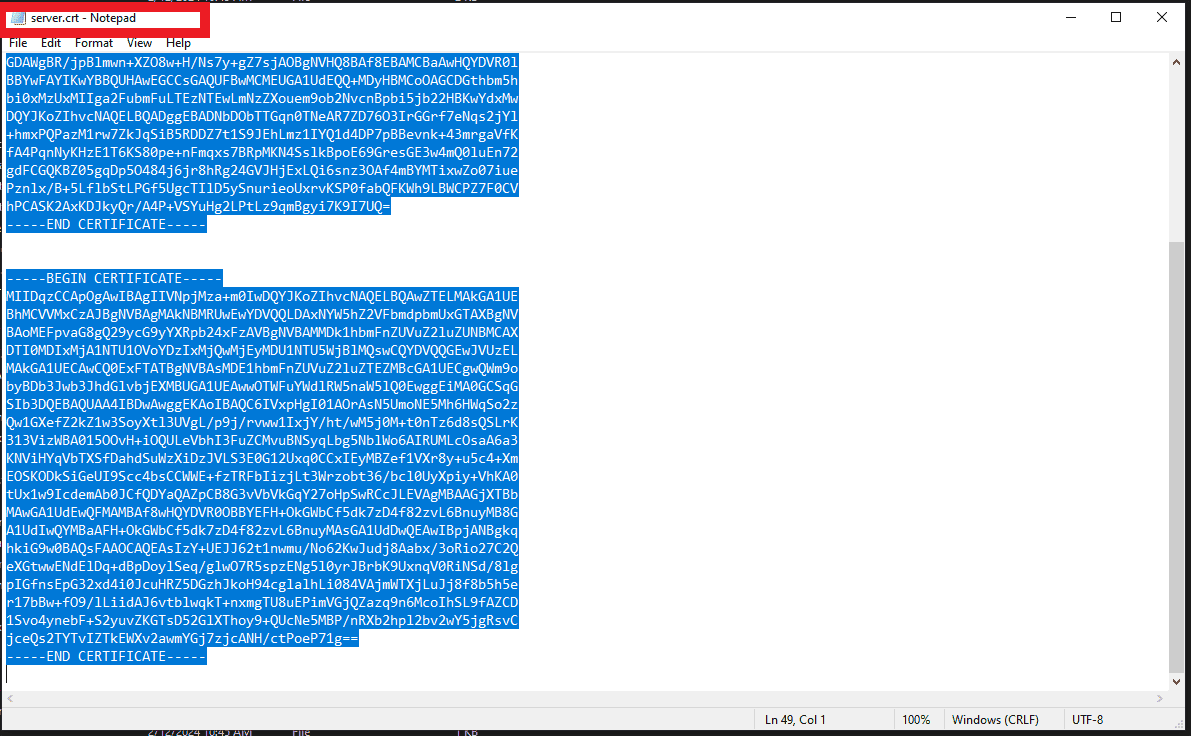
- Open the server.crt file with a text editor and copy the contents of the certificate file.
- Now go to the Splunk installation directory on your system.
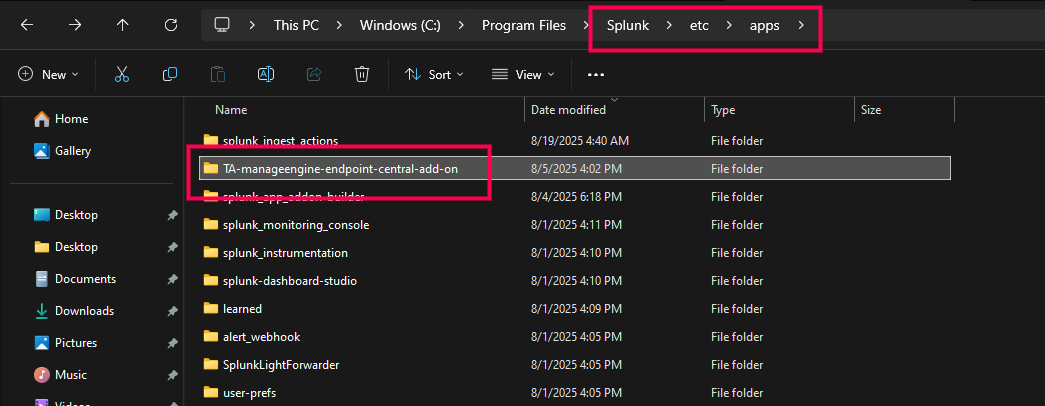
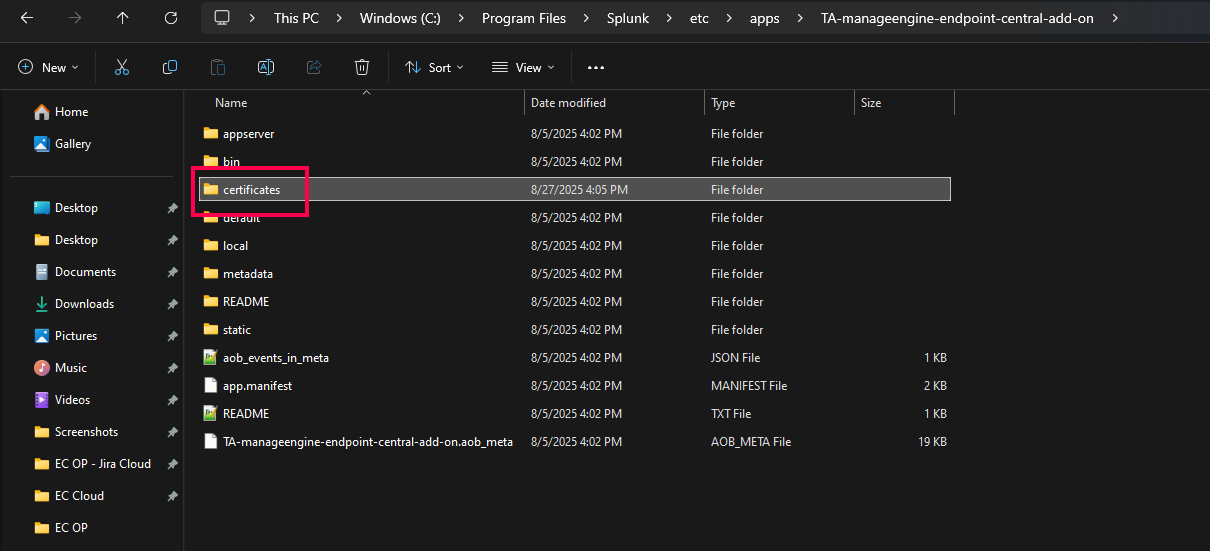
- Navigate to %Splunk Home Dir% → etc → apps → TA-manageengine-endpoint-central-add-on.
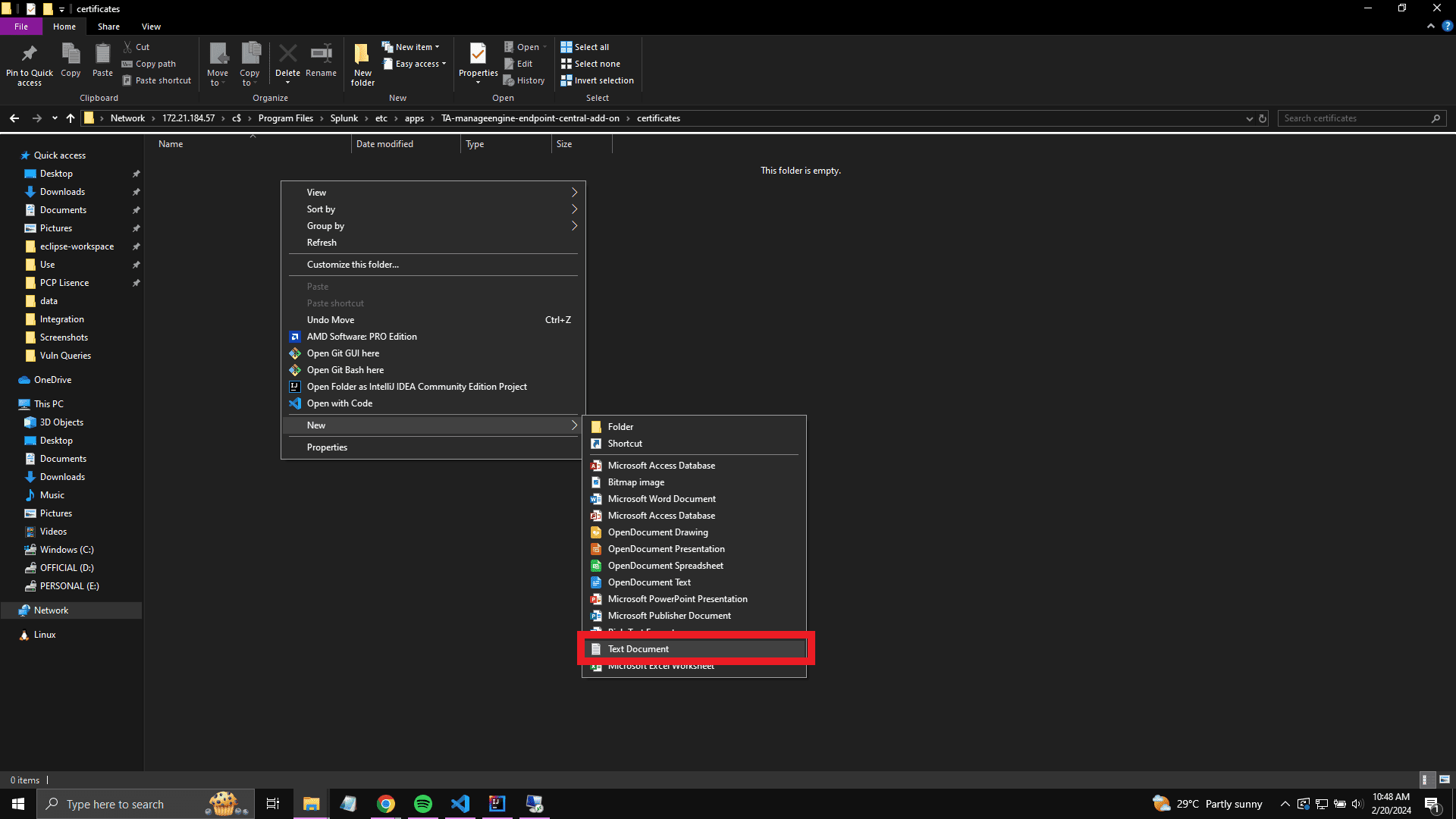
- Within the TA-manageengine-endpoint-central-add-on folder, create a new folder named certificates.
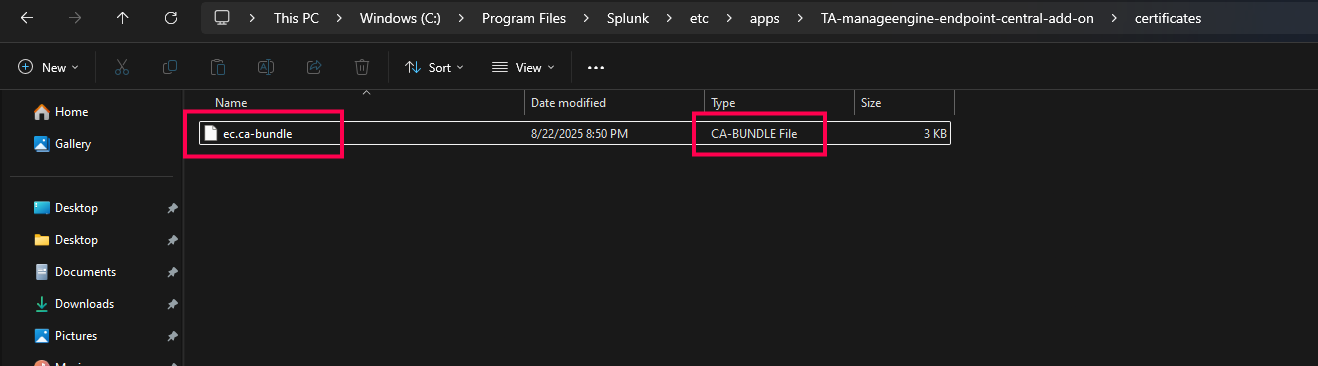
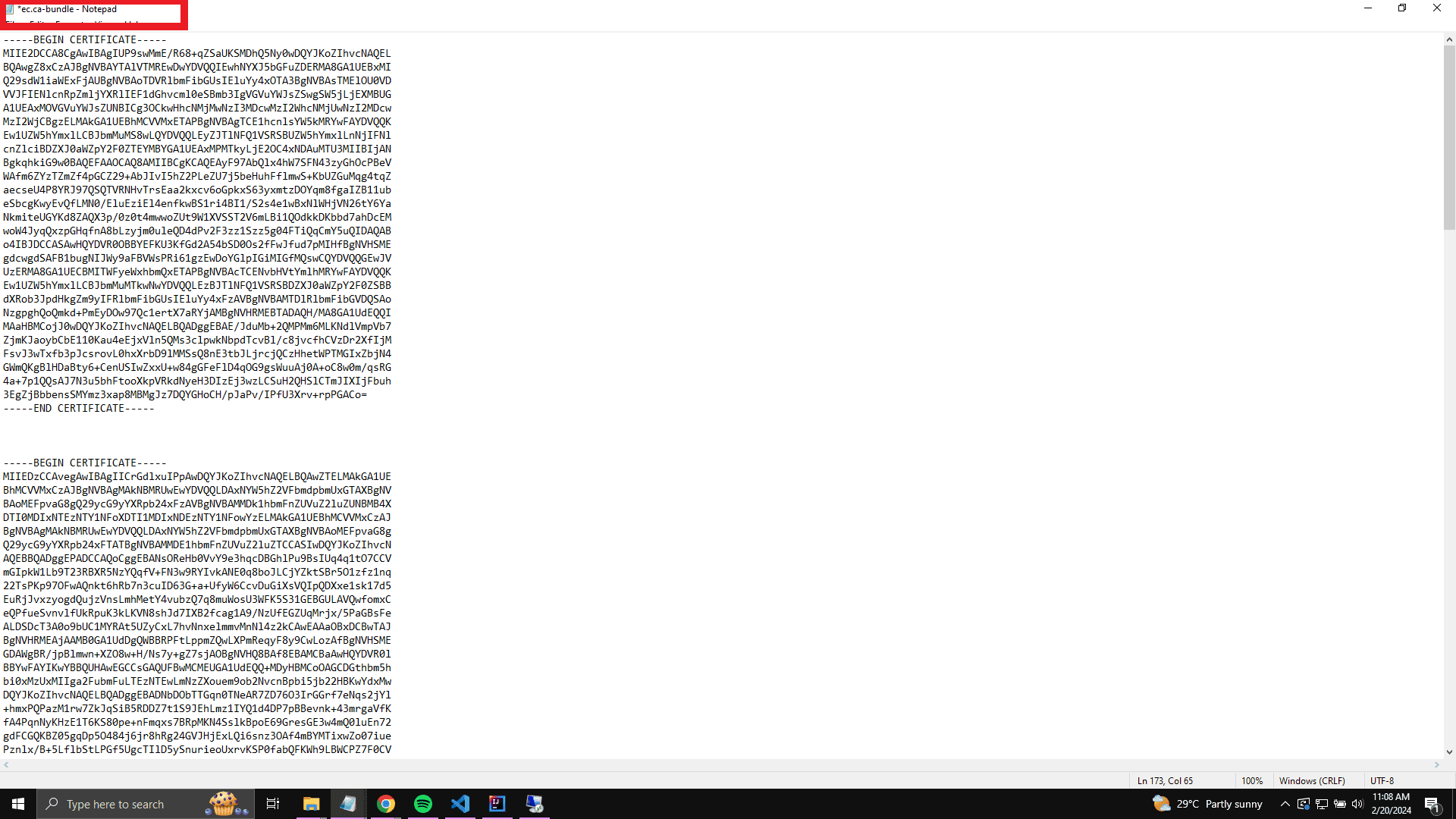
- Inside the certificates folder, create a new text file and rename it to ec.ca-bundle.
- Open the ec.ca-bundle file with a text editor and paste the contents of the server.crt file copied from the Endpoint Central.
- Save and close the ec.ca-bundle file. Please ensure that the file is saved with the file type CA-BUNDLE.
Generating an API key in Endpoint Central
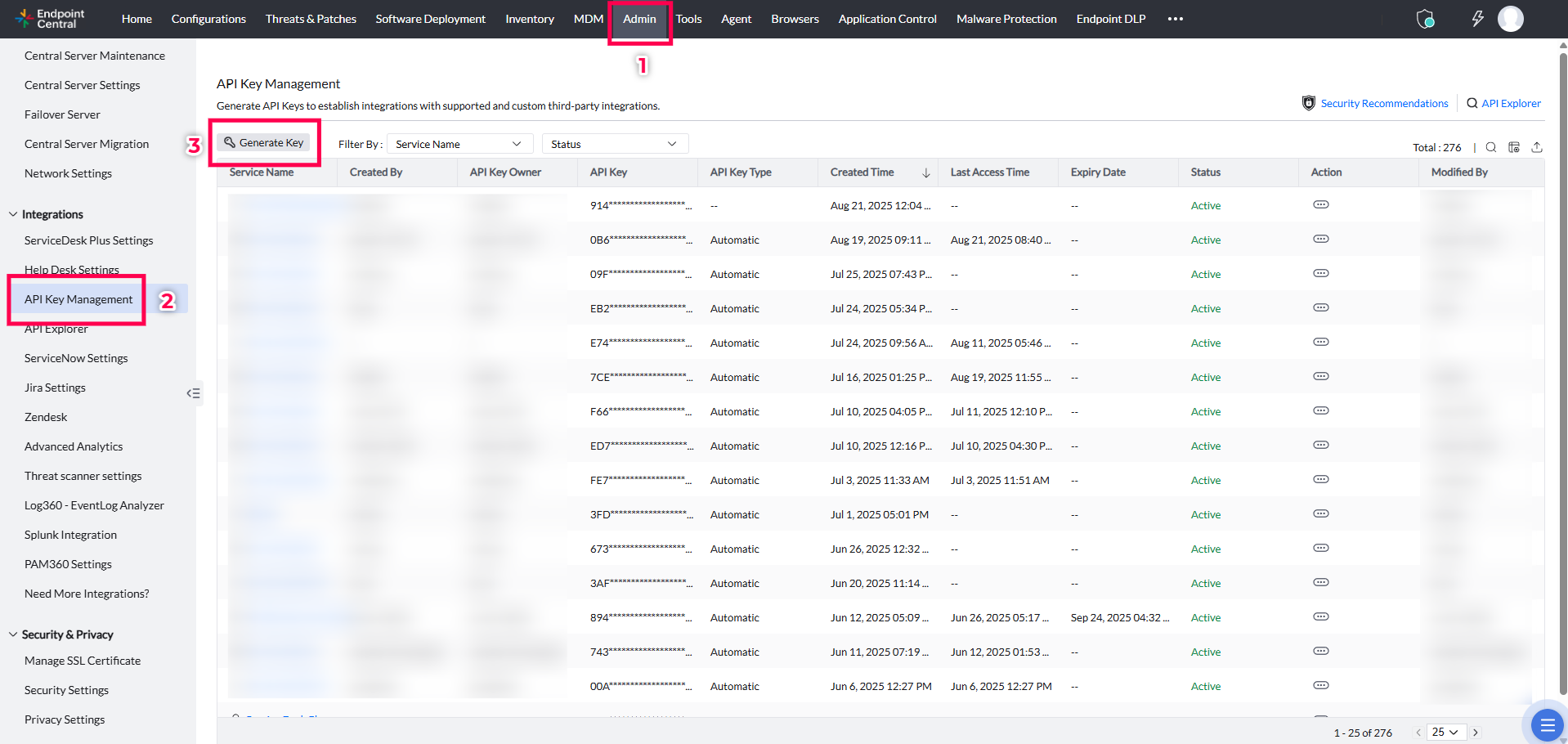
- In the Endpoint Central console, navigate to the Admin tab → API Key Management and click on Generate Key.
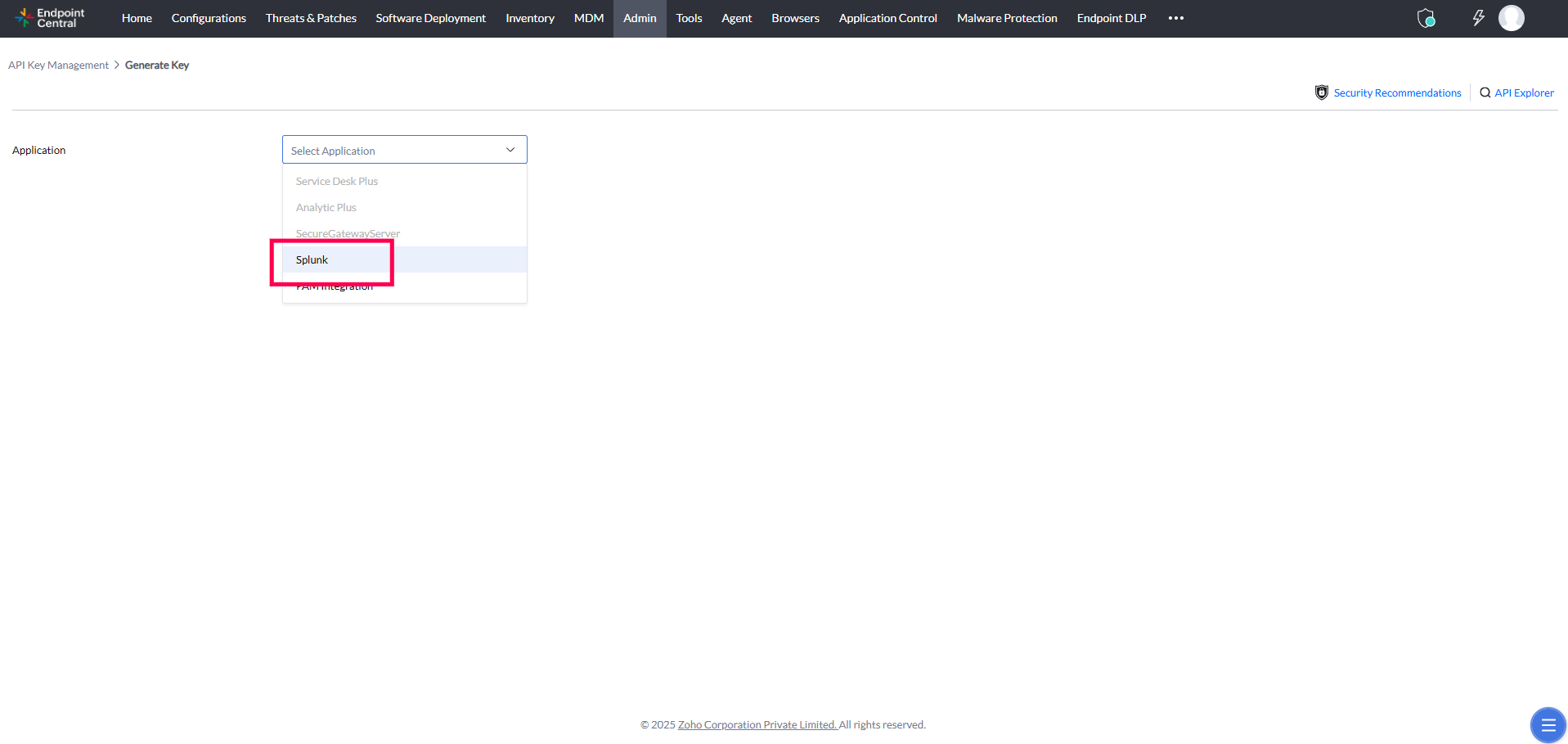
- Select Splunk from the Application menu and click on Generate Key to generate your API key.
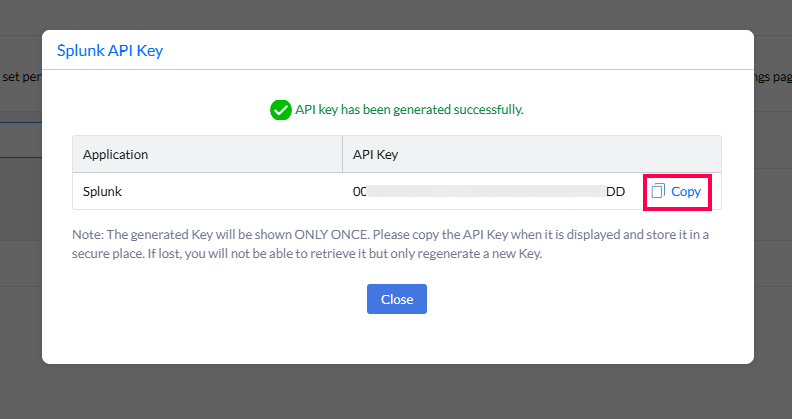
- Then you can copy your API key.
Note
The generated Key will be shown Only once. Please copy the API Key when it is displayed and store it in a secure place. If lost you will not be able to retrieve it but only regenerate a new Key.
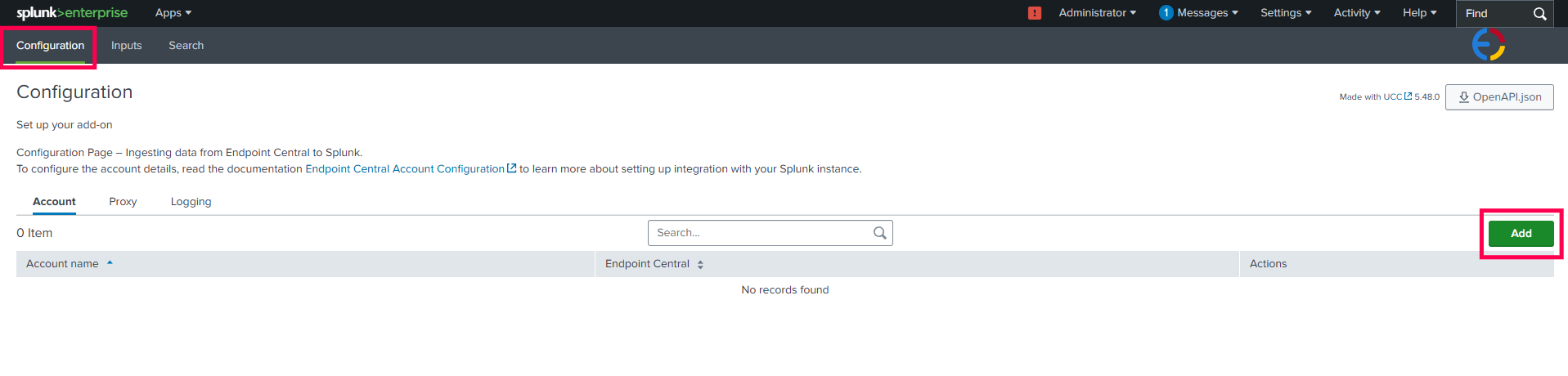
Configuring the app in Splunk for the Endpoint Central
- Navigate to the Splunk home page and access the header menu and click on Apps.
- Select the ManageEngine Endpoint Central Add-On App.
- Within the App, navigate to the Configurations page and Click the Add button.
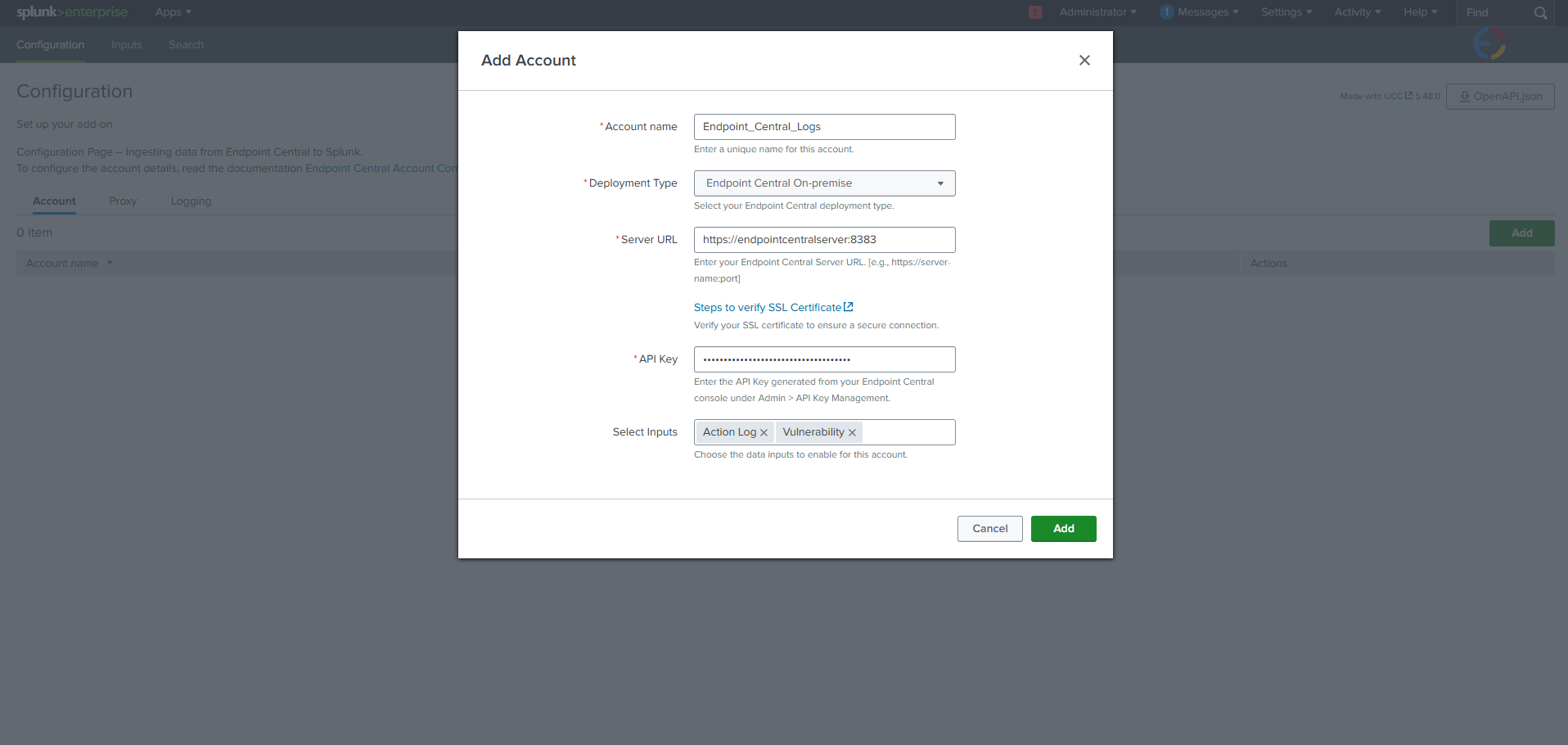
- In the pop-up, choose Endpoint Central On-premise from the Deployment Type and complete all necessary fields.
- Paste the API key copied from Endpoint Central Server.
- Click Add. If all the information is correct, it will be validated successfully.
Valid inputs:
- Account Name: Should be unique and without spaces.
- Deployment Type: Must be Endpoint Central On-premise.
- Server URL: URL with the scheme (https://). This URL must be accessible from the machine hosting Splunk. If using a proxy, configure proxy settings before adding configuration details.
- API Key: Use the API Key generated from Endpoint Central without any modifications.
- Select inputs: Select the required log inputs based on your needs. You can also configure or modify these inputs later from the Inputs Configuration section.
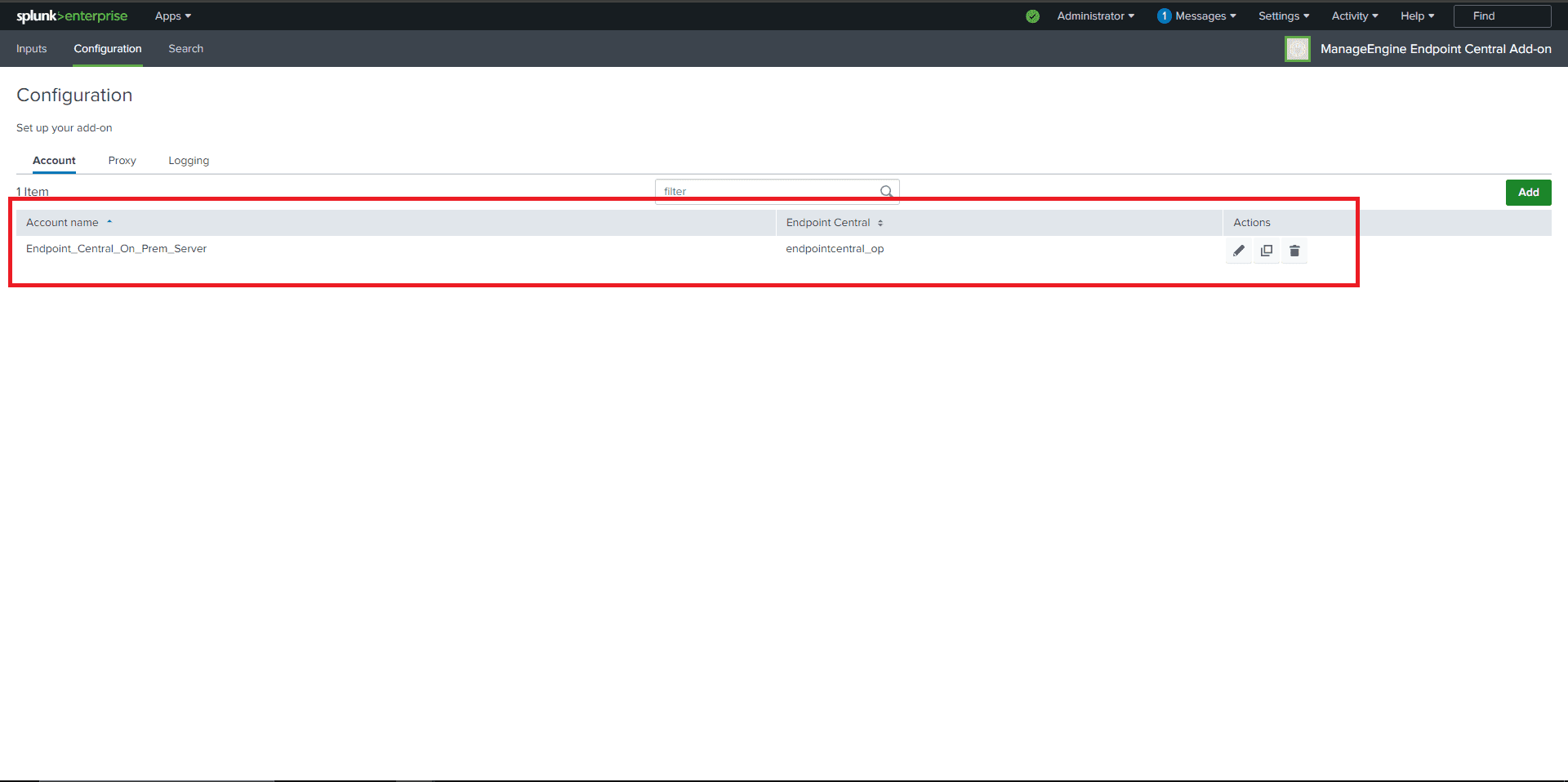
- The added configuration will appear in the Accounts section.
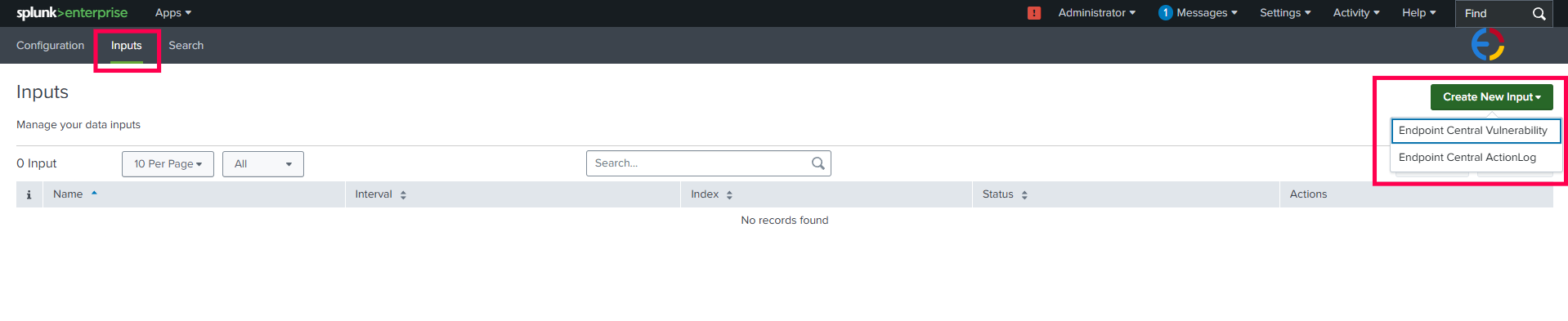
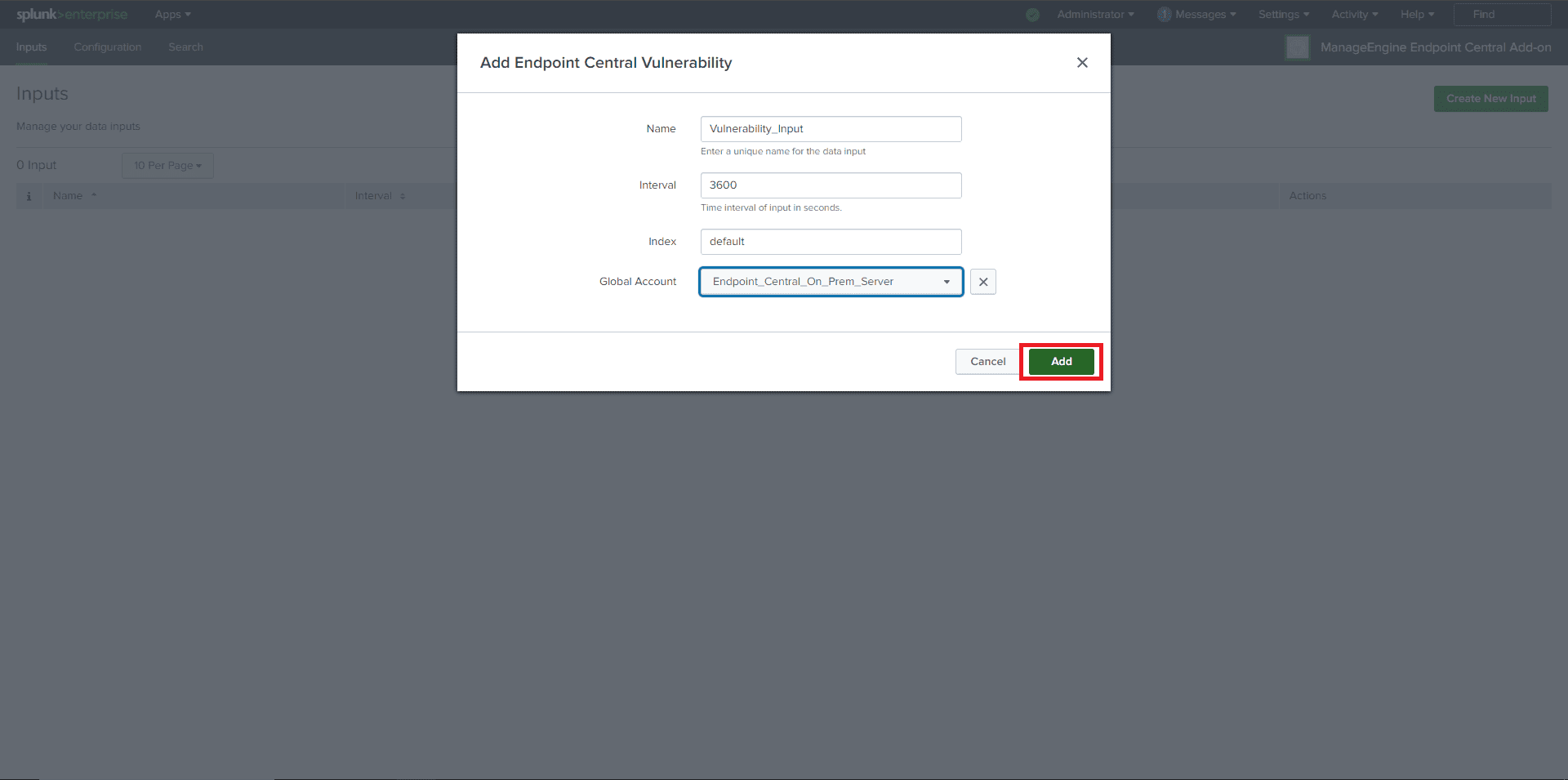
- Navigate to the Inputs tab in Splunk, click on the Create New Input, and select the log data that you need from Endpoint Central.
- In the pop-up window, enter all the required information. From the Global Account dropdown, select the Account configured for Endpoint Central.
- Then, click the Add button. If all inputs are valid, the input will be added successfully.
Valid Inputs:
- Name: Unique name without any white spaces.
- Interval: Must be in seconds.
- For Vulnerability data: Between 3600 seconds (1 hour) and 86400 seconds (24 hours).
- For Action log viewer data: Between 300 seconds (5 minutes) and 86400 seconds (24 hours).
- Index: Default.
- Global Account: Account created for Endpoint Central in the configuration section.
- The added input will then get displayed.
Viewing data in Splunk
- Once an input is configured, synchronization with the Endpoint Central server will begin.
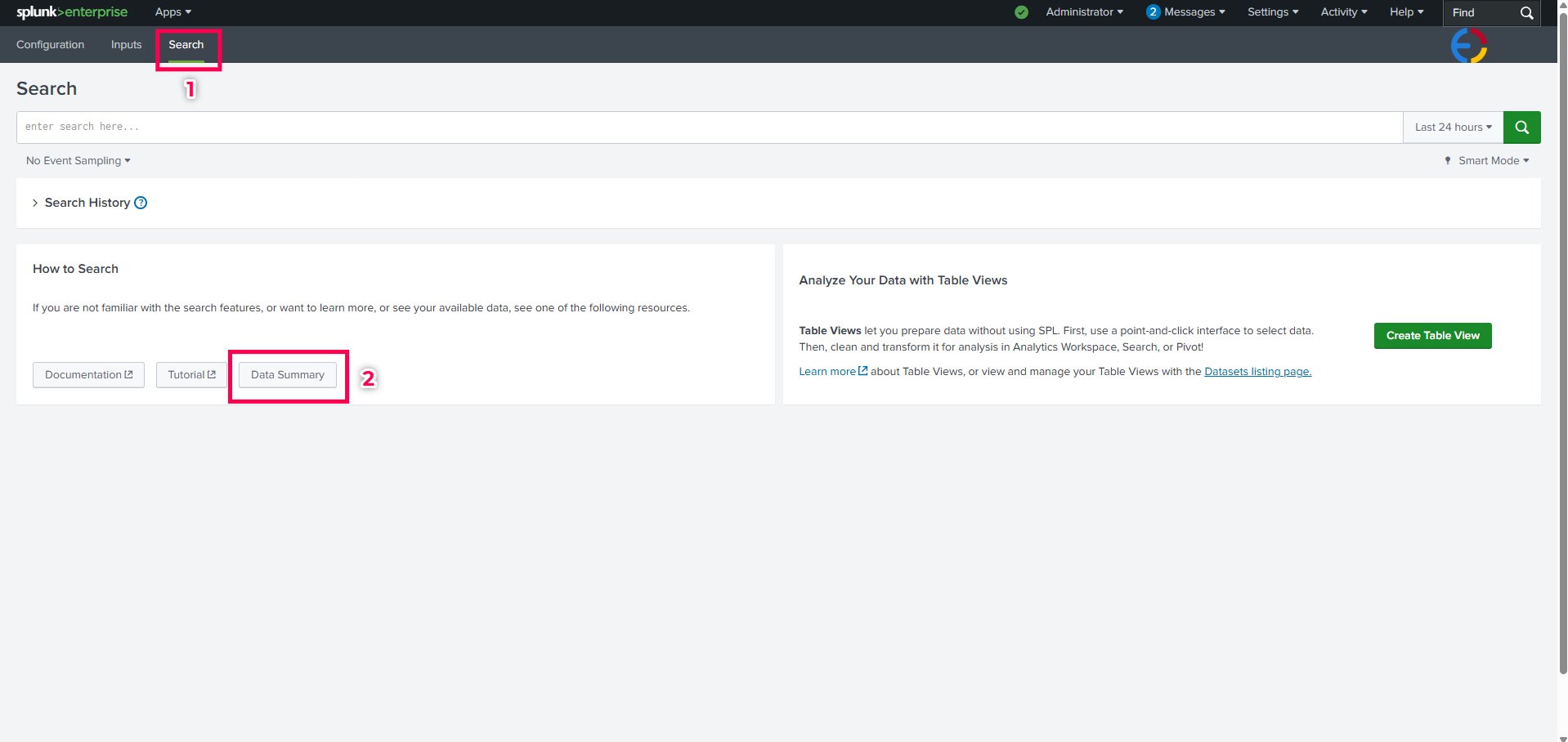
- Navigate to the Searchtab in the app.
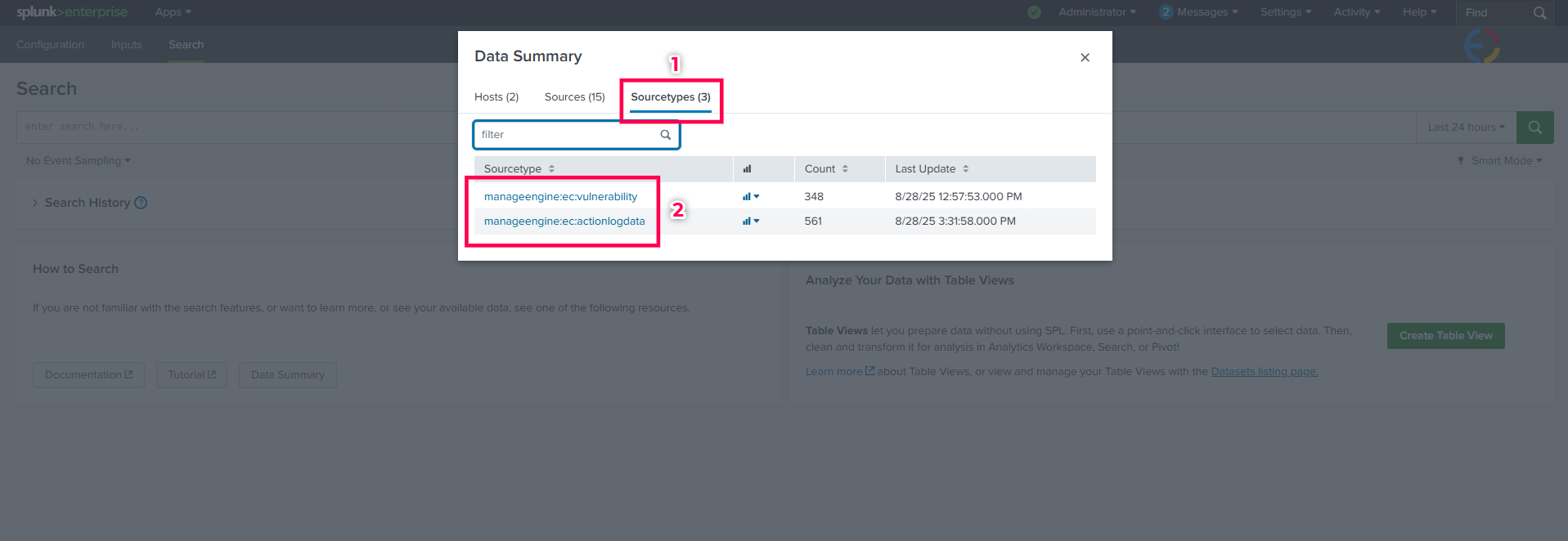
- Click on Data Summary and navigate to the Sourcetypestab.
- Search for the required Sourcetype from below and click on it to view the data.
- Vulnerability data sourcetype:
manageengine:ec:vulnerability
- Action log viewer data sourcetype:
manageengine:ec:actionlogdata
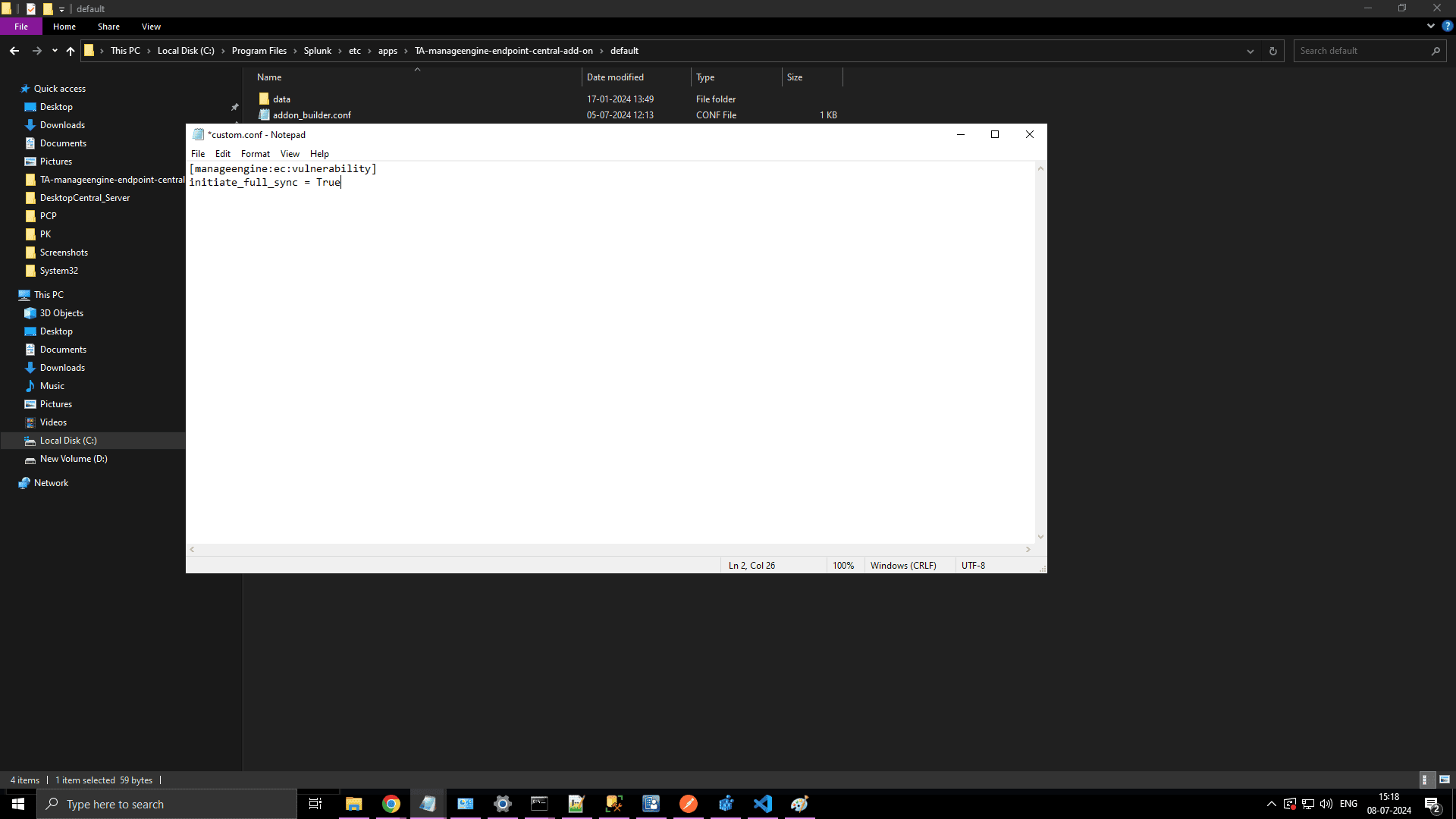
Initiating Full Sync
Configuring Multiple Endpoint Central Servers in Splunk
- Whenever you add a new On-Prem Endpoint Central server in Splunk, include the contents of the server.crt file in the existing ec-ca-bundle file.
- Refer to the steps in Creating a CA-Bundle for SSL Validation to copy the contents of the server.crt file.
- Append the copied contents to the end of the already created ec-ca-bundle file.
- Finally, follow the instructions in Configuring App in Splunk with Endpoint Central server to complete the configuration.