Note: In case CrowdStrike Falcon Spotlight integration isn't available in your Endpoint Central server, kindly contact support.
Seamlessly deploy patches for the vulnerabilities detected by CrowdStrike Falcon Spotlight
By seamlessly integrating CrowdStrike Falcon Spotlight into the Endpoint Central console, IT administrators can now efficiently address identified vulnerabilities with the deployment of corresponding patches. Bid farewell to the hassle of navigating to multiple dashboards and manually mapping vulnerabilities with the appropriate patches. The CrowdStrike Falcon Spotlight integration handles it all for you, simplifying the entire process and saving all the valuable time and efforts.
Steps to integrate Spotlight with Endpoint Central
Generate API client in Spotlight
- To generate Spotlight API client, you need to have Falcon Administrator role to view, create or modify API clients or keys.
- If you have Administrator privileges, you can generate the required API clients by following this user-guide by Spotlight.
- When generating the API client, ensure you select the following permissions under the API Scopes section:
- Detections (Read)
- Hosts (Read)
- Vulnerabilities (Read)
- Once you click Save, Spotlight generates Client ID and Client Secret.
- Store these clients in a secure location.
Configure API Settings in Endpoint Central
- Navigate to Admin > Integration > Threat scanner settings. Only users with Administrator privileges can configure the API Settings.
- Enter the Spotlight base URL, Client ID and Client Secret.
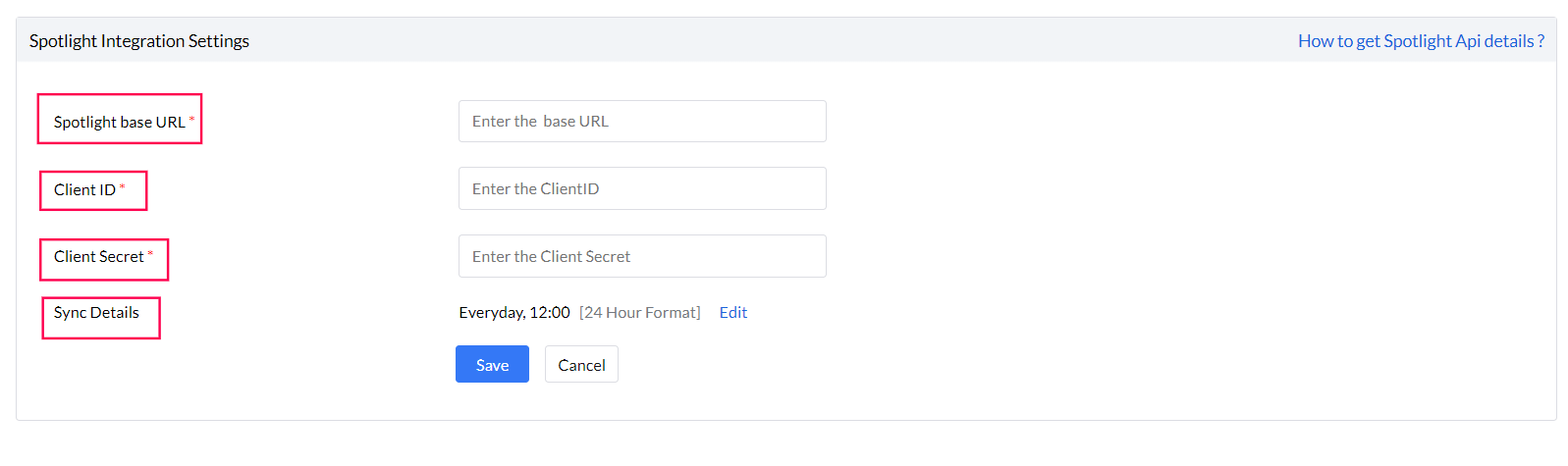
- Configure the frequency at which you want the data sync to happen.
- Click on Save to enable the Integration.
Workflow
- After enabling the Integration, Endpoint Central will import the vulnerability details and the affected machine details from Spotlight.
- Identify the corresponding patch/fix for the respective vulnerabilities and remediate those vulnerabilities by installing the appropriate patch.
- Threats detected by Spotlight, with the patch availability, will be listed under Threats & Patches > Spotlight Threats. Users can also deploy patches for vulnerabilities from this view.
If you have any further questions, please refer to our Frequently Asked Questions section for more information.


