- Home
- Logging guide
- AWS S3 logging
Logging AWS S3
In this page
- S3 server access logging
- Object-level logging (AWS CloudTrail events)
- Pros and cons of AWS S3 logging
Amazon Simple Storage Service (S3) from Amazon Web Services allows you to store and retrieve any amount of data, at any time, from anywhere on the web. AWS S3 offers a scalable, high-speed, web-based cloud storage service. Logs generated by AWS S3 record events and actions occurring within your S3 buckets, making them essential for monitoring, auditing, and troubleshooting.
Types of logging in AWS S3
There are two main types of AWS S3 logging. They are:
- S3 server access logging
- Object-level logging (AWS CloudTrail events)
S3 Server access logging:
S3 access logging is a feature in Amazon S3 that captures detailed information about all requests made to an AWS S3 bucket. This includes actions such as uploading ( PUT ), downloading (GET), and deleting (DELETE) files.
Each log entry provides details such as:
- Object key (name of the S3 object involved)
- Request method (e.g., GET, PUT, DELETE)
- User identity (if authenticated)
- Date and time of the request
- Source IP address from which the request was originated
- Specific resource in the bucket that was accessed
- HTTP status code indicating whether the request was successful or failed
Unlike CloudTrail, which tracks API calls across AWS, S3 access logs focus specifically on S3 interactions.You need to specify a target bucket to store the logs. This can be the same bucket where the logging is enabled or a different bucket. This includes information about the requester, the request type, and the resources involved. Logs are written to a separate S3 bucket you designate, called the target bucket. This target bucket needs to be in the same region and account as the source bucket. Choose S3 Server Access Logging if you need to track access at the bucket level.
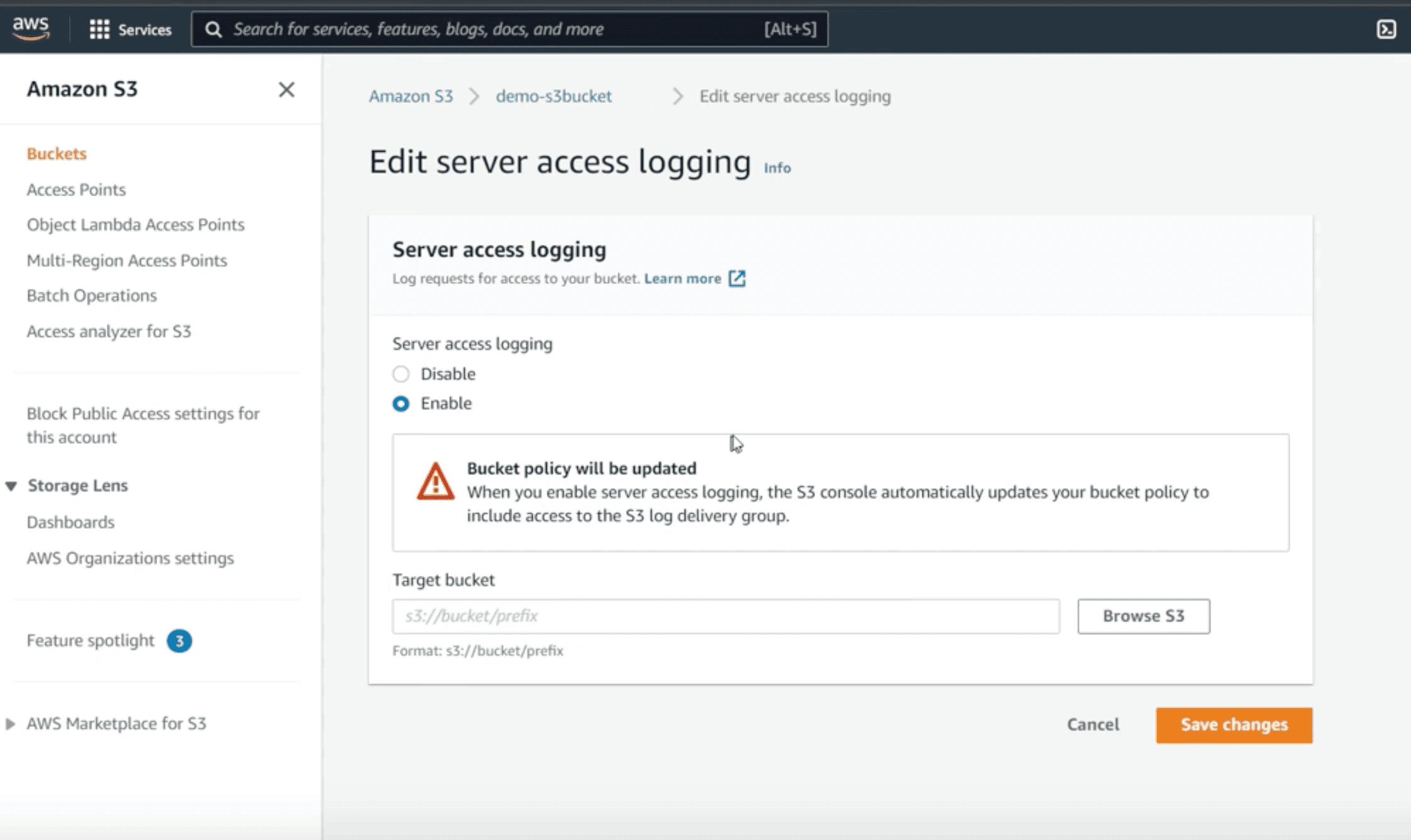
How to enable S3 server access logging?
- Log in to the AWS Management Console and navigate to the Amazon S3 service.
- Select the source bucket you want to enable logging for.
- Go to the properties tab of the selected bucket.
- Locate and edit the server access logging section:
- Enable logging.
- Specify a target bucket for storing the logs (use a separate bucket to avoid recursive logging).
- If needed, set a target prefix to organize the logs.
- Save changes to apply the logging settings.
Object-level logging:
AWS CloudTrail logs API calls made to S3 and other AWS services. This logging captures detailed information about S3 object-level operations such as:
- API caller identity
- Request parameters
- Source IP address
- Timestamp
- Event name
- Event source
- Response elements
You can configure CloudTrail logging for your entire AWS account in the CloudTrail console and specify an S3 bucket as the log destination. Permissions are required to create a CloudTrail trail and write logs to the specified S3 bucket. CloudTrail charges are based on the number of trails and events recorded, and you may incur storage costs for the logs. Retention can be managed using S3 life cycle policies or CloudTrail’s built-in options.
This CloudTrail logging method is valuable for security auditing, compliance reporting, tracking changes, and investigating operational issues.
Logs can be analyzed using Amazon Athena, AWS CloudWatch, CloudTrail Insights, or third-party tools like Log360 Cloud.
Additionally, you can set up CloudWatch Events to trigger automated responses or notifications for specific API actions. Best practices include regularly reviewing and archiving logs, enabling CloudTrail Insights for anomaly detection, and ensuring logs are encrypted and access-controlled.
Choosing the right AWS S3 logging method:
It's important to consider your needs for detail, security, and compliance when deciding between AWS S3 server access logging and object-level logging via AWS CloudTrail. S3 server access logging provides high-level monitoring by tracking requests made to your S3 buckets. This method logs information such as request type, resource accessed, and time of access, making it suitable for detecting unauthorized access or unusual activity at the bucket level. It is ideal for general auditing, understanding usage patterns, and meeting basic compliance requirements.
On the other hand, object-level logging offers detailed, granular logs of operations on individual objects within your S3 buckets, such as GetObject, PutObject, and DeleteObject actions. It allows for precise tracking of who accessed or modified each object, enabling thorough forensic analysis and enhanced data security. This level of detail is crucial for environments with sensitive data and stringent regulatory requirements.
By understanding these options, you can select the logging method that best fits your needs. This ensures your data remains secure, compliant, and well-monitored.
Pros and cons of AWS S3 logging
Pros:
- Security and compliance: Logging helps in maintaining security by tracking access patterns, identifying unauthorized access attempts, and ensuring compliance with security policies and regulations.
- Auditing and monitoring: Detailed logs enable S3 bucket and object operations auditing, helping organizations track who accessed what data and when.
- Troubleshooting: Logs facilitate troubleshooting by providing visibility into errors, access denials, and other operational issues within S3.
- Operational insights: Analyzing S3 logs can provide operational insights, such as usage patterns, access trends, and performance metrics, which can inform capacity planning and optimization efforts.
- Cost management: Logging can aid in cost management by identifying unused or rarely accessed data, facilitating data life cycle management decisions.
- Incident response: In the event of a security incident or data breach, S3 logs can be invaluable for forensic analysis and understanding the scope and impact of the incident.
- Integration with monitoring systems: S3 logs can be integrated with monitoring and alerting systems like Amazon CloudWatch, enabling proactive detection and response to anomalous activities.
Cons:
- Storage cost: S3 is cost-effective for storage. Logging can incur additional costs, especially when enabling detailed logging or storing logs for extended periods.
- Complexity: Configuring and managing logging settings, especially across multiple buckets or accounts, can be complex and may require careful planning and monitoring.
- Data volume: S3 generates large volumes of logs, particularly in environments with high traffic or frequent access, which can pose challenges for storage, processing, and analysis.
- Performance impact: Enabling extensive logging can potentially impact S3 performance, although AWS manages this impact to a large extent.
- Granularity: Depending on the logging mechanism (e.g., CloudTrail vs. server access logs), the granularity of data and available fields may vary, affecting the depth of analysis and insights.
- Privacy: Set appropriate access controls on the target bucket to restrict who can view logs.
- Retention and compliance: Managing log retention periods and ensuring compliance with data retention policies can require ongoing attention and resources.
- Limited real-time visibility: Some logging mechanisms (e.g., S3 Server access logs) may not provide real-time visibility into activities, with logs being delivered on a delayed basis.
In conclusion, while logging AWS S3 activities offers significant benefits for security, compliance, troubleshooting, and operational insights, organizations should carefully consider the associated costs, complexities, and management aspects to derive maximum value from their logging strategy. Balancing the need for detailed logging with cost-efficiency and operational impact is crucial for effective S3 management in AWS environments.
So, what next?
Try Log360 Cloud for efficient AWS S3 logging and robust security.
Log360 Cloud is ManageEngine's cloud-based SIEM solution that offers comprehensive visibility and security management across on-premises and cloud environments in a single platform. Enhance your security posture with real-time log analysis and threat detection.











