| Cyber Essentials requirements |
Requirement description |
EventLog Analyzer reports |
| D.1 Boundary firewalls and internet gateways |
Organizations should protect every device in scope with a correctly configured firewall (or network device with firewall functionality). |
- Windows Firewall Threats
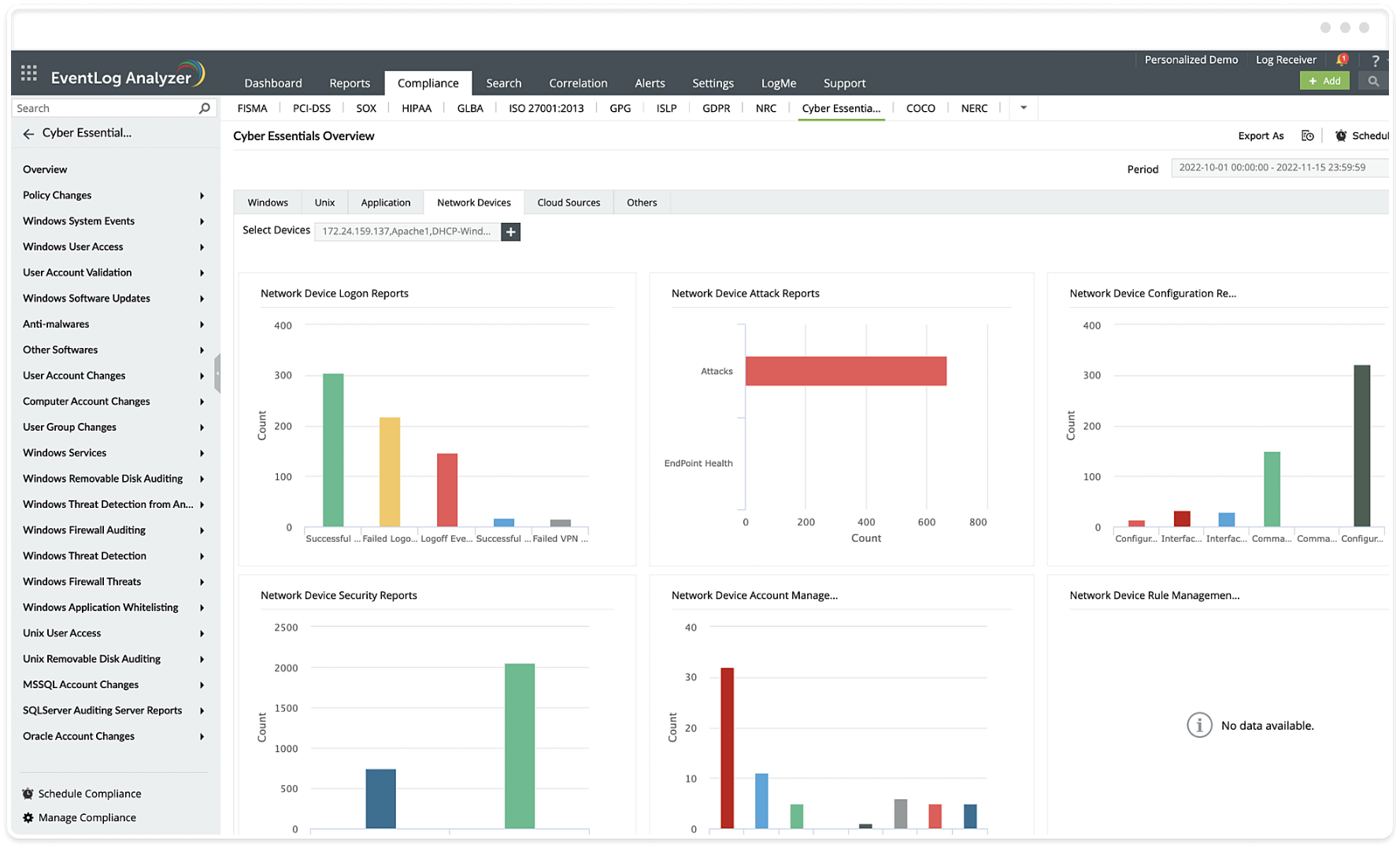
- Network Device Logon Reports
- Network Device Attack Reports
- Network Device Configuration Reports
- Network Device Security Reports
- Network Device Rule Management Reports
- VPC Activity
- WAF Reports
|
| D.2 Secure Configuration |
Proper configuration of computers and network devices should be carried out to minimize inherent vulnerabilities and ensure that only the services needed to carry out their designated tasks are available. |
- Policy Changes
- Windows User Access
- User Account Validation
- User Account Changes
- Computer Account Changes
- User Group Changes
- Unix User Access
- Network Device Account Management Reports
|
| D.3 Patch Managaement |
Maintain the latest security patches and updates on the software utilized on computers and network devices. |
- Windows System Events
- Windows Services
- Network Device Security Reports
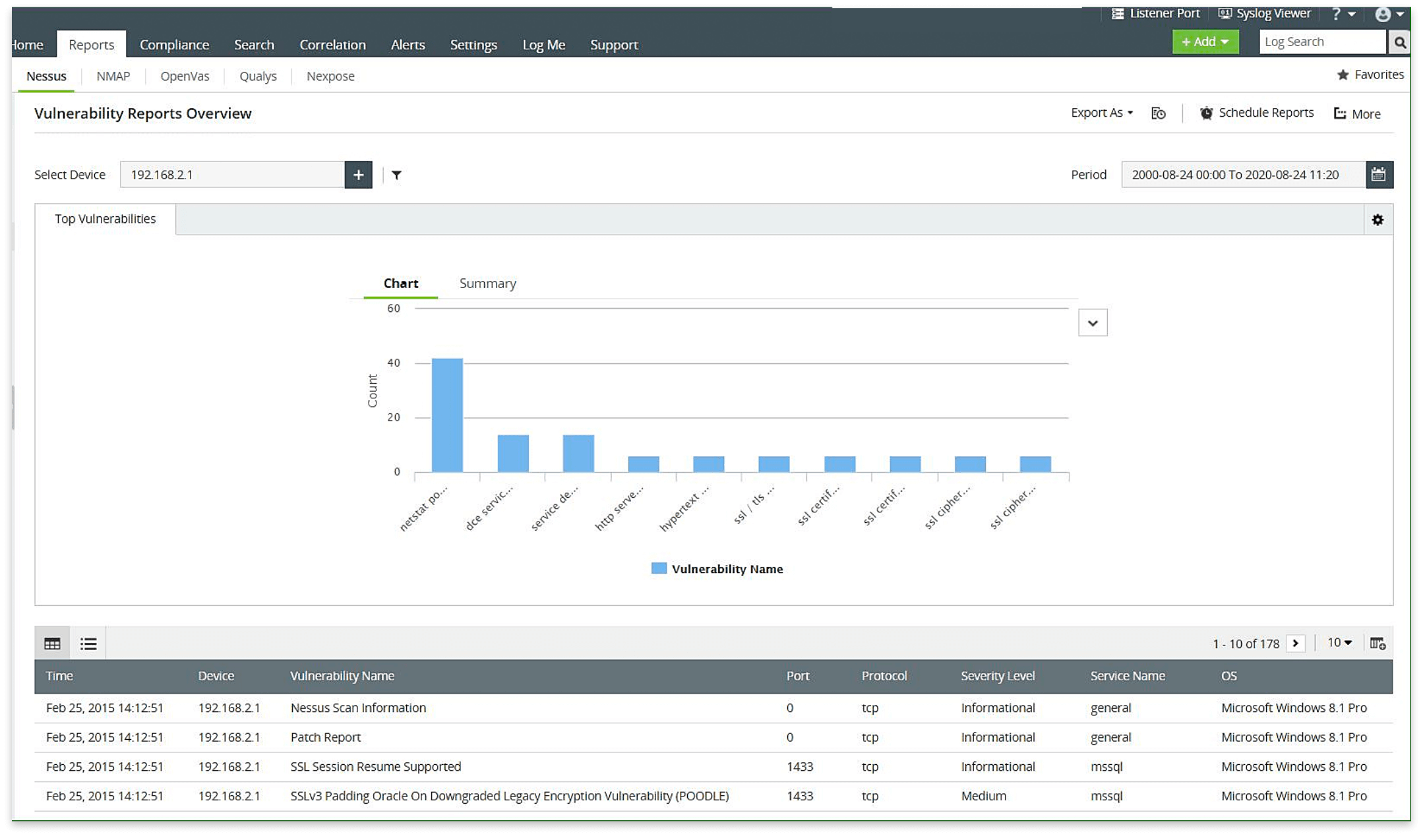
- Nessus Vulnerability Reports
|
| D.4 User access control |
Authorized individuals should be the only ones assigned user accounts, especially those with special access privileges, like administrative accounts, and effective management should be implemented to prevent the misuse of such privileges. |
- Policy Changes
- Windows User Access
- User Account Validation
- Unix User Access
- AWS User Activity
- AWS Failed/Unauthorized Activity
- Oracle Account Changes
- Network Device Logon Reports
|
| D.5 Malware Protection |
The use of malware protection software is necessary to safeguard computers in an organization that are connected to the internet, and it is essential to implement strong malware protection measures on these devices. |
- Windows Software Updates
- Anti-malware
- Other Software
- Windows Removable Disk Auditing
- Windows Threat Detection from Antivirus
- Windows Threat Detection
- Windows Application Whitelisting
|