What is a command and control (C2/C&C) attack?
Command and control (C2 or C&C) is an attack tactic where adversaries maintain control over compromised systems or networks. With this attack tactic, threat actors use a C2 server to communicate with the compromised devices or systems, which are often referred to as bots or zombies. Attackers utilize these communication channels to install additional malware, form botnets, or exfiltrate sensitive information.
Key characteristics of C2 attack
- Remote control: With the established C2 channel, attackers execute commands on a compromised system.
- Persistence: C2 attacks often involve the installation of persistent malware that allows threat actors to maintain control over the compromised system or network
- Botnets: C2 attacks often leverage large botnets—networks of compromised devices—that can be used to launch distributed attacks.
- Stealth mode: Attackers often use different techniques to hide their C2 infrastructure and avoid detection.
How command and control attack occurs
According to the MITRE ATT&CK® framework, C2 attack tactics prioritize stealth by blending into normal network traffic to avoid detection. It details 18 techniques and sub-techniques used by attackers to create covert C2 channels, tailored to the target's network environment and defenses.
This attack includes five stages: Initial compromise, malware installation, C2 communication, command execution, and persistence.
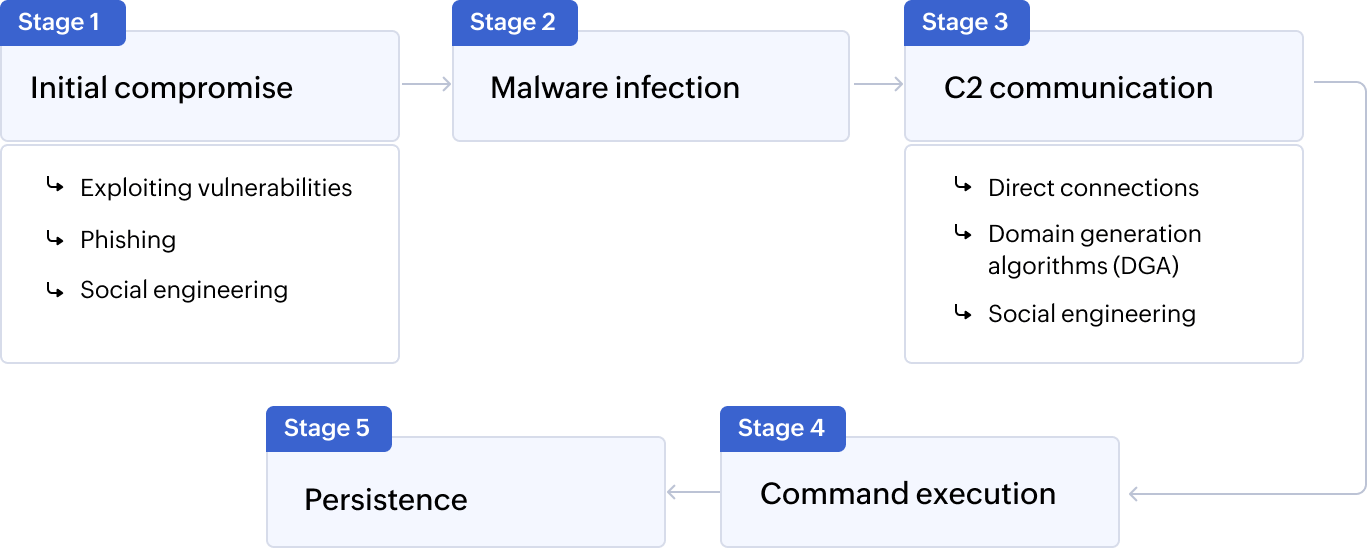
Stage 1
Initial compromise
At this stage of this attack, adversaries gain initial access to a system through various methods, including:
Phishing
Sending deceptive emails designed to trick users into clicking on malicious links or downloading attachments.
Exploiting vulnerabilities
Leveraging the known vulnerabilities in software or operating systems.
Social engineering
Manipulating users to reveal sensitive information or grant unauthorized access.
MITRE ATT&CK framework association
The techniques and sub-techniques used at this stage of the C&C attack include:
- T1132 Data encoding (2): Used to obfuscate or encrypt communication to avoid detection.
- T1001 Data obfuscation (3): Similar to T1132, but used to hide or disguise data.
- T1586 Dynamic resolution: Used to create unpredictable domain names or IP addresses to avoid detection.
- T1090 Proxy (4): Used to mask the attacker's IP address and hide their location.
Stage 2
Malware infection
Once the system is compromised using any of the techniques above, attackers then install malicious software that establishes connection to the C2 server.
MITRE ATT&CK framework association
The techniques and sub-techniques used at this stage of the C2 attack include:
- T1105 Ingress tool transfer: Used to transfer malicious tools onto the compromised system.
- T1092 Communication through removable media: Used to transfer data or malware via physical media.
- T1659 Content injection: Used to inject malicious code into legitimate content.
- T1104 Multi-stage channels: Used to establish multiple layers of communication to avoid detection.
Stage 3
C2 communication
At this stage, the bot communicates with the C2 server using various techniques, including:
Direct connections
The bot connects directly to the C2 server using the known IP address or domain name.
Domain generation algorithms (DGA)
The bot generates unique domain names to avoid detection.
Encrypted communication
Attackers often use encrypted channels to obfuscate C2 communication.
MITRE ATT&CK framework association
The techniques and sub-techniques used at this stage of the C2 attack include:
- T1104 Multi-stage channels: Used to establish multiple layers of communication to avoid detection.
- T1250 Traffic signaling (2): Used to coordinate communication between the attacker and the compromised system.
Stage 4
Command execution
The attacker sends commands to the bots using the C2 channel as established in the previous stage. Then, they instruct the bots to performs malicious actions such as spreading additional malware, data exfiltration, and launching DDoS.
MITRE ATT&CK framework association
The techniques and sub-techniques used at this stage of the C2 attack include:
- T1090 Proxy (4) - Can be used to gain unauthorized access to privileged accounts.
- T1219 Remote access software: Can be used to gain remote access to privileged systems.
- T1071 Application layer protocol (4) - Used to transfer data over network protocols.
- T1573 Encrypted channel: Used to protect data in transit from interception.
Stage 5
Persistence
At this stage, attackers often use techniques to ensure that the bot remains undetected and can continue receiving communications from the C2 server, even after system reboots and security updates. They also blend their communication with legitimate traffic like HTTP/HTTPS or DNS to avoid detection.
MITRE ATT&CK framework association
The techniques and sub-techniques used at this stage of the C2 attack include:
- T1008 Fallback channels (2): Used to maintain communication even if the primary C2 channel is disrupted.
- T1665 Hide infrastructure: Used to conceal the C2 server or infrastructure from detection.
- T1095 Non-application layer protocol: Used to avoid detection by using protocols that are not typically associated with legitimate network traffic.
- T1571 Non-standard protocol: Used to avoid detection by using custom or proprietary protocols.
- T1572 Protocol tunneling: Used to hide C2 communication within other protocols.
C2C attack: Devices targeted
C2 attacks can be tailored to specific targets or indiscriminate, depending on the attacker's objectives. Devices with known vulnerabilities, valuable data, or the ability to launch further attacks are often prioritized. This includes laptops, desktops, servers, mobile phones, IoT devices, and industrial control systems.
Want to protect your systems and network from C2 attacks?
The impact of C2 attacks
C2 attacks pose a serious threat to organizations of all sizes, ranging from minor inconveniences to major financial losses and reputational harm. Often occurring late in the cyberattack life cycle, detecting and stopping C2 attacks is crucial to prevent significant damage.
Potential consequences of C2 attacks include:
- Data loss and theft: Stealing of sensitive data such as credit card information, PIIs, PHIs, or intellectual property and data breaches leading to financial losses, regulatory fines, and reputational damage.
- Service disruption: C2 attacks can be used to launch DDoS and compromise critical systems, leading to service outage and operational disruptions.
- Spam campaigns: Using the compromised bots or zombies to send spam or phishing campaigns, leading to multiple attacks at once.
- Cryptojacking: C2 attacks also use the compromised system to mine cryptocurrency.

Detecting C2 attacks
Detecting C2 attacks requires multi-faceted approach that combines network monitoring, endpoint security, threat intelligence, and behavioral analytics. Therefore,a SIEM is a valuable asset in the fight against C2 attacks by providing a centralized platform for collecting, analyzing, and responding to threats. SIEM tools integrate various solutions and technologies, acting as a comprehensive solution for detecting and mitigating C2 attacks. Let's discuss some critical strategies for detecting this C2 attack.
Network monitoring:
- Unusual network traffic: Monitor for unusual network traffic patterns, such as excessive outbound connections, unusual protocols, or encrypted traffic.
- DNS queries: Monitor for unusual DNS queries, especially for domains that are not associated with legitimate services.
- Port scanning: Monitor for unauthorized port scanning activity, which can indicate reconnaissance or C2 communication.
- Network flow analysis: Use network flow analysis tools to identify suspicious patterns in network traffic.
Talk to our experts to know how ManageEngine SIEM, Log360, can ingest network data from IT operations suite to provide complete security visibility
Indicator of attack detection:
- Anomaly detection: Use endpoint security solutions to detect anomalous behavior on endpoints, such as unusual process activity, file access patterns, or network connections.
- Malware detection: Regularly scan endpoints for malware and other malicious software.
- Behavior-based detection: Monitor user behavior for anomalies that might indicate a C2 attack, such as unusual login times, access to sensitive data, or unusual network activity. Analyze the behavior of entities such as devices, applications, and accounts to identify suspicious activity.
Threat Intelligence:
- Indicators of compromise (IoCs): Use threat intelligence feeds from trusted sources to identify IoCs associated with known C2 attacks. Check out how ManageEngine Log360's threat intelligence system function in detecting these IoCs.
- Threat actor tracking: Monitor the activities of known threat actors to identify potential C2 attacks targeting your organization.
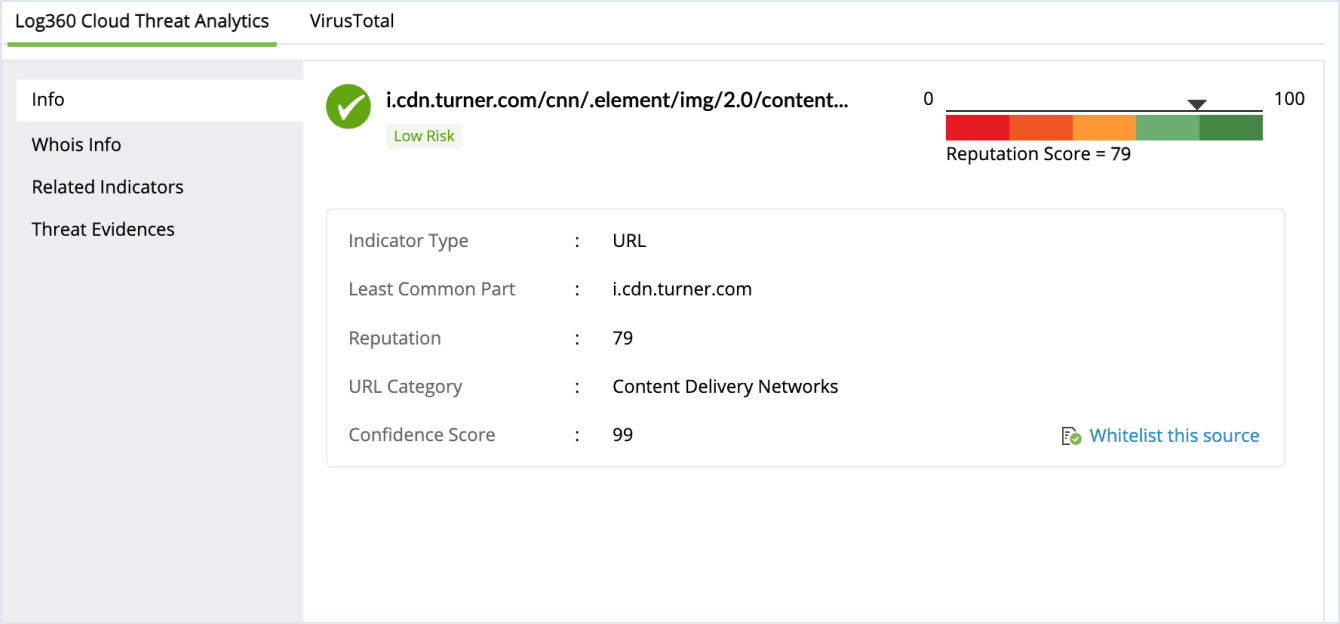
Additional Tips:
- Honey pots: Deploy honeypots to attract attackers and gain insights into their tactics and techniques.
- Sandboxing: Isolate suspicious files or code in a sandbox environment to analyze their behavior without risking damage to the production environment.
- Dark web monitoring: Monitor the dark web for mentions of your organization or its data, which could indicate a C2 attack.
Command and control attack response plan
A well-developed C2 attack response plan, as illustrated here, should help security operations minimize the damage caused by the attack and reduce the time to recovery.
Key components of a C2 attack response plan:
When you suspect or receive an alert for C2 attack in your network, use a SIEM solution to conduct a thorough investigation for analyzing the impact, assessing the infection rate, and follow the below steps based on the inputs from the solution:
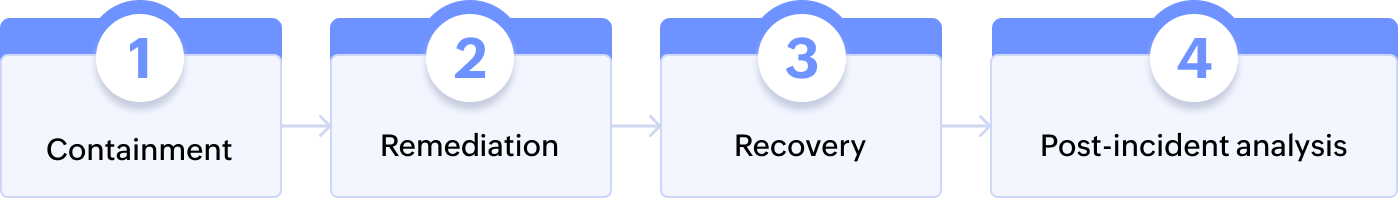
1.Containment:
- Isolate the infected system: Get the list of infected system(s) from the investigation and disconnect them from the network to prevent further spread of the attack.
- Disable compromised accounts: Disable compromised accounts to limit the attacker's access.
- Block malicious traffic: Use firewalls or other security measures to block malicious traffic.
2. Remediation:
- Remove malware: Remove any malicious software from the compromised systems.
- Patch vulnerabilities: Apply security patches to address vulnerabilities that may have been exploited.
- Restore systems: Restore systems from backups if necessary.
- Strengthen security measures: Implement additional security measures to prevent future attacks.
3. Recovery:
- Restore services: Restore critical services and systems to full functionality.
- Communicate with stakeholders: Communicate with affected stakeholders, such as customers and employees.
- Review incident response plan: Review and update the incident response plan based on the lessons learned from the attack.
4. Post-incident analysis:
- Conduct a review: Conduct a thorough review of the incident to identify weaknesses in the organization's security posture.
- Implement improvements: Implement improvements to prevent future attacks.
- Document lessons learned: Document the lessons learned from the incident for future reference.
A C2 attack response plan should regularly be tested and updated to ensure its effectiveness. It is also important to involve relevant stakeholders, such as IT staff, security professionals, and senior management, in the development and implementation of the plan.
Interested to explore how ManageEngine helped enterprises across the world to tackle C2 and other cyberattacks? Get in touch with our solution experts
- What is a command and control attack?
- How C2 attack happens
- C2C attack: Devices targeted
- The impact of C2C attack
- Detecting C&C attacks
- Command and control attack response plan


