OS credential dumping:
DCSync attack
Content in this page
- What is credential dumping?
- About the attack
- Attack flow
- Detection Mechanism
- Detect and mitigate OS credential dumping using Log360
What is credential dumping?
Isn't it wonderful how every time you visit a website that you've previously visited, your browser conveniently remembers your password? It feels good to be remembered, right? But, have you ever thought of the possibilities of someone snooping around and getting their hands on your password?
Credential dumping refers to the act of obtaining user credentials (username and password) from an operating system or software. These are normally obtained in the form of a hash or clear text, which is then used to perform lateral movement, gain access to restricted information, or to install malware. Once this is done, the attacker can log in to the system at will and access the sensitive information available in it.
About the attack:
Once inside the network, the attacker continuously changes important settings until an affected user contacts their administrator. When the administrator logs on to the user's system, the attacker compromises the administrator's credentials, which can then be used to manipulate other systems in the network.
So, where do these passwords get stored and how does the attacker get them?
1. Security Accounts Manager (SAM)
In Windows, the SAM is a database file that contains local accounts for the host, typically those found with the net user command. To enumerate the SAM database, system-level access is required.
The file can be retrieved through in-memory techniques such as:
- Mimikatz
- gsecdump
- pwdumpx.exe
- secretsdump.py
Apart from these, the SAM can be extracted from the registry with the reg command.
- reg save HKLM\sam sam
- reg save HKLM\system system
The Creddump7 tool can then be used to process the SAM database locally to retrieve hashes.
2. WDigest
This is a heritage protocol used to authenticate users in Windows. The Local Security Authority Subsystem Service (LSASS) keeps a plaintext copy of the password of the current user in the memory when WDigest is enabled. Though this service is disabled by default, it still exists even in the latest versions of Windows. Attackers often enable it to steal user credentials.
3. Kerberos
The Kerberos protocol uses the ticketing system to grant various permissions to users and services. However, this authentication protocol, considered strong and secure, can also be used to gain access. This can be done by forging or injecting stolen tickets into the system.
4. LSA secrets
The Local Security Authority (LSA) manages authentication and the logging of users on a Windows system. It also manages the local security policy for a computer, and the data that this subsystem uses is stored in a protected area called LSA secrets. Attackers can obtain sensitive data if they gain access to this storage area.
5. Proc file system
In Linux, the proc file system stores information about the state of the OS. If an attacker manages to run a process with root privileges, live memory can be scrapped from other applications. Any credentials stored as password hashes or plaintext can be extracted.
Further, if an attacker manages to gain access to the domain controller (the network server that handles managing authentication on a domain), they can find additional places where the credentials get stored such as:
1. NTDS
Active Directory stores information here about the members of the domain to verify the users and credentials.
2. Group Policy Preference files
These Windows files enable the creation of domain policies with embedded credentials and administrative privileges. These policies are stored in a share called the SYSVOL which can be viewed, and potentially be decrypted by any domain user.
3. DCSync
DCSync is a technique in which the attacker mimics the behavior of a domain controller through API calls and gets the domain controller to send the credential hashes to the attacker's system by simulating replication process. With this technique, the attacker takes advantage of the way the domain controller handles the available API calls.
Attack flow:
Attack flow:
- 1 Conduct reconnaissance to identify the target system and potential vulnerabilities.
- 2 Exploit a vulnerability or weakness to gain initial access to the target system using a phishing attack, a software vulnerability, or other social engineering techniques.
- 3 Identify the target account whose credentials are to be stolen.
- 4 Escalate privileges to gain higher levels of access to the system by exploiting additional vulnerabilities, social engineering tactics, or other methods.
- 5 Extract password hashes using tools such as ProcDump, Mimikatz, or others from memory, the registry, configuration files, or other locations on the system.
- 6 Crack the password hashes by using tools such as Hashcat or John the Ripper, and employ methods such as brute-force or dictionary attacks.
- 7 Obtain the plaintext passwords.
- 8 Use the stolen credentials to gain further access to the network and sensitive data, log in to other systems, steal additional credentials, or escalate privileges on the current system.
Detection mechanism:
There are several ways by which the network can be protected from a credential dumping attack. Some of them are:
Detection mechanism:
- 1 Monitor access to services like LSASS and databases like SAM regularly.
- 2 Manage domain controller replication permissions.
- 3 Disable or restrict the NT LAN Manager (NTLM).
- 4 Monitor the logs for unscheduled activities on a domain controller.
- 5 Watch out for the command line arguments used in credential dumping attacks.
- 6 Do not blend the administrator domain accounts with the local administrator groups.
- 7 Use a log management solution to help prevent credential dumping.
Enhance your security posture by leveraging the capabilities of Log360
Let our experts evaluate your security requirements and demonstrate how Log360 can help satisfy them.
Learn how Log360 can combat OS credential dumping and such stealthy attacks with a suite of security features like:
- Real time AD monitoring
- Machine learning based anomaly detection and
- Correlation of network events
Detect and mitigate OS credential dumping using Log360
Learn how to set up correlation rules, alerts, and incident workflows and customize them to detect and remediate credential dumping and DCSync attacks.
- Detection through correlation
- Real-time alerts
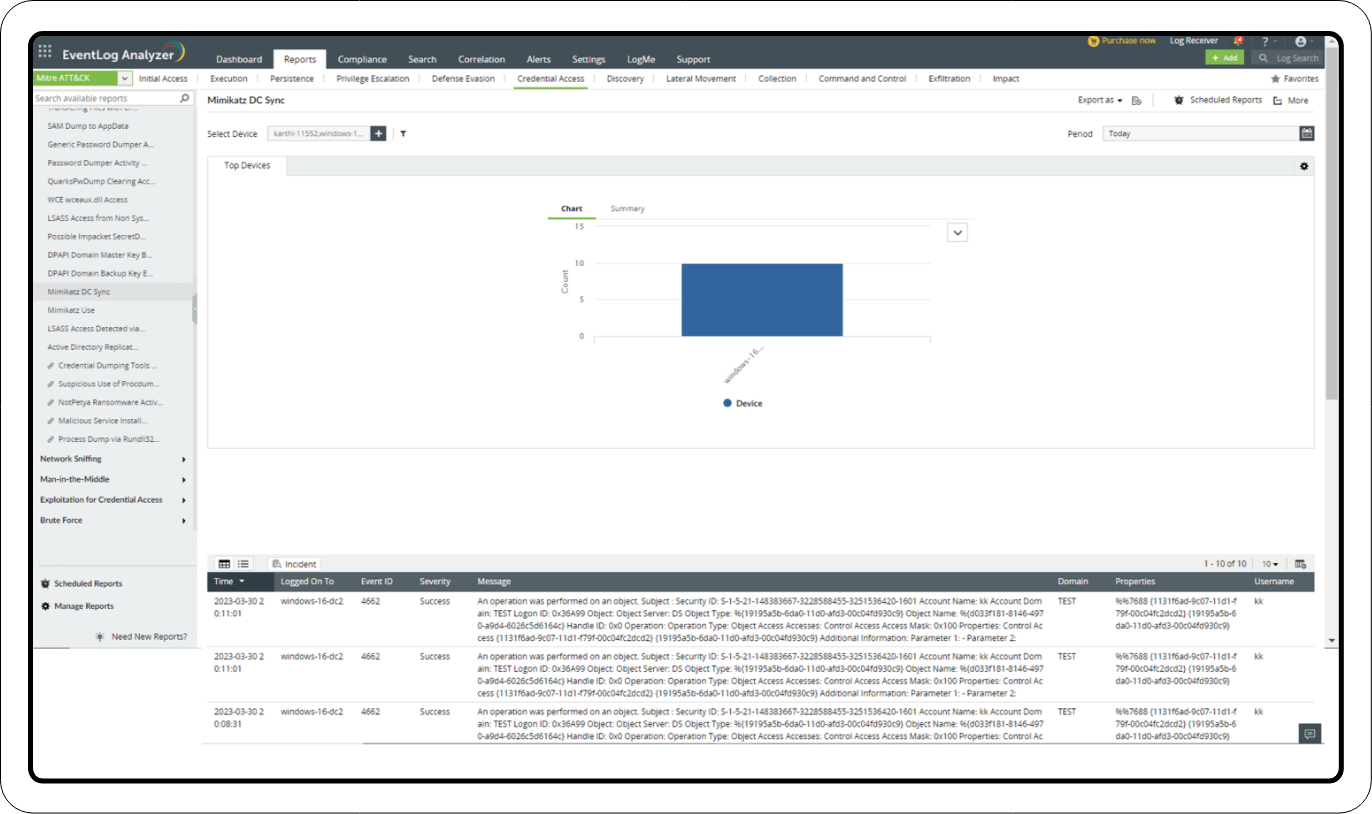
- Investigation through reports
Detection through correlation
For OS credential dumping and a DCSync attack, the action sequence and associated event IDs are as follows:
1. An operation was performed on an object. Event ID: 4662
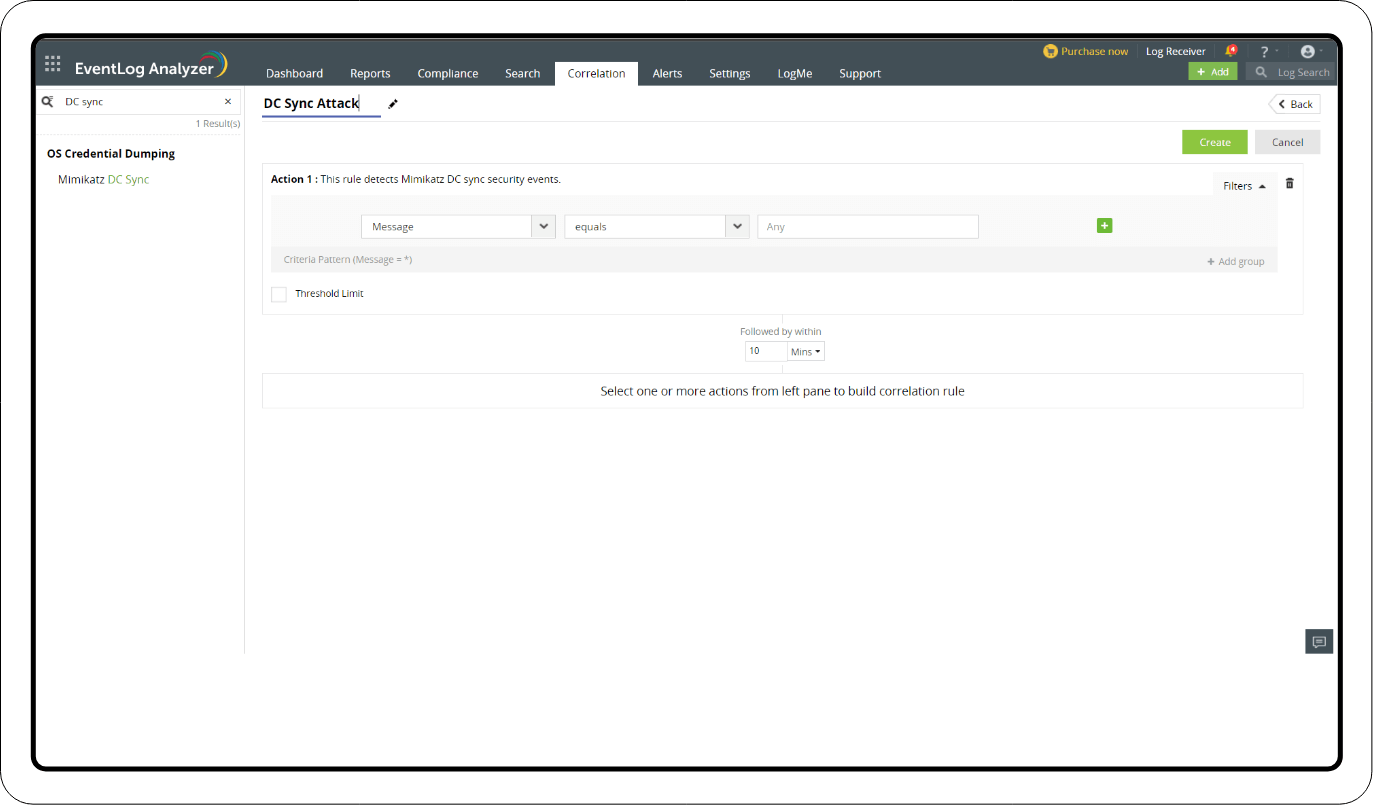
Go to the Log360 console > SIEM > Correlation > Manage Rule > Create Correlation Rule > Mitre ATT&CK TTP(S).
- Search for DC Sync under the Correlation tab.
- Select OS Credential Dumping.
- Name the action, and click Create.
Real-time alerts
Creating an Alert Profile:
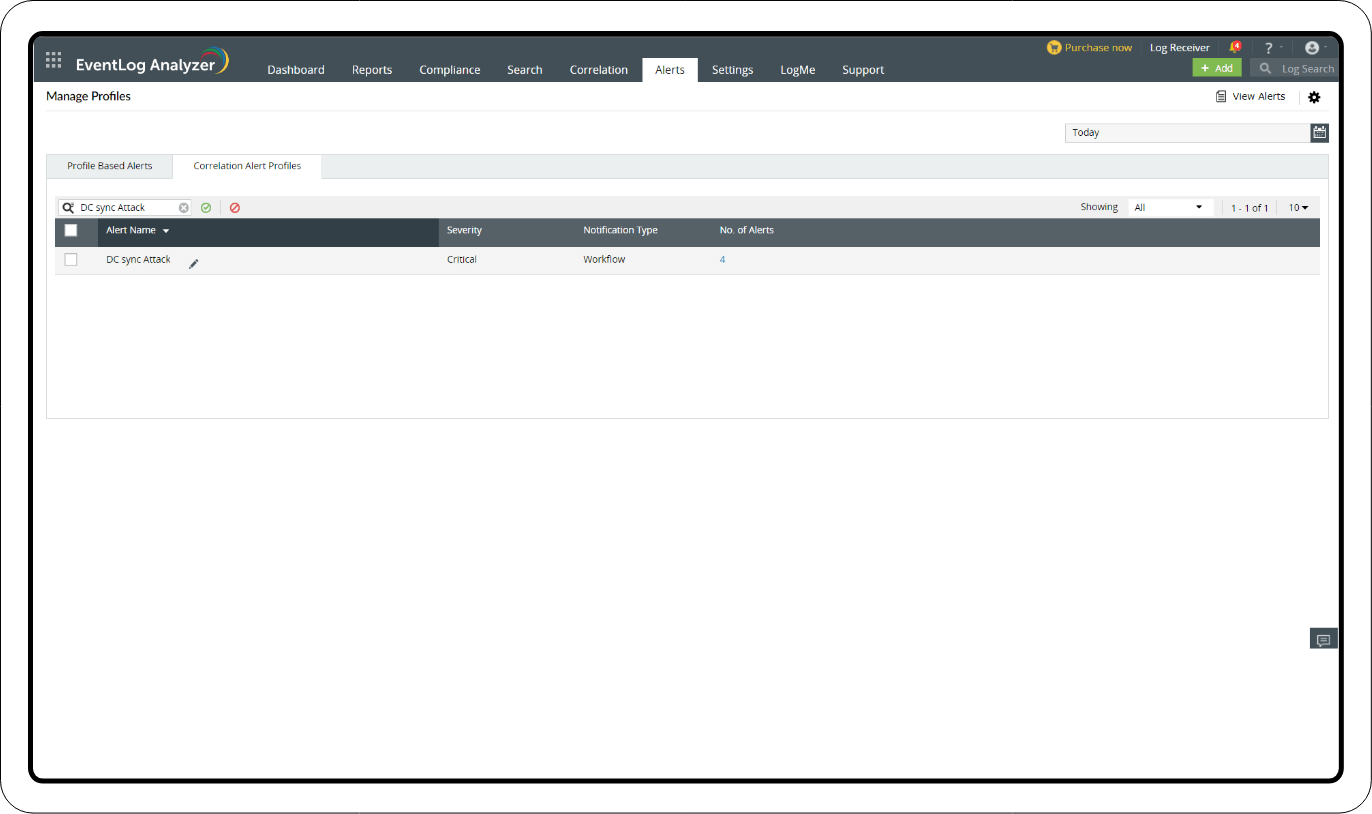
Go to the Log360 console > SIEM > Alerts > click the settings icon in the top-right corner > Manage Profiles > Correlation Alert Profiles > click the search icon and select the DC Sync Attack that was created > click Configure.
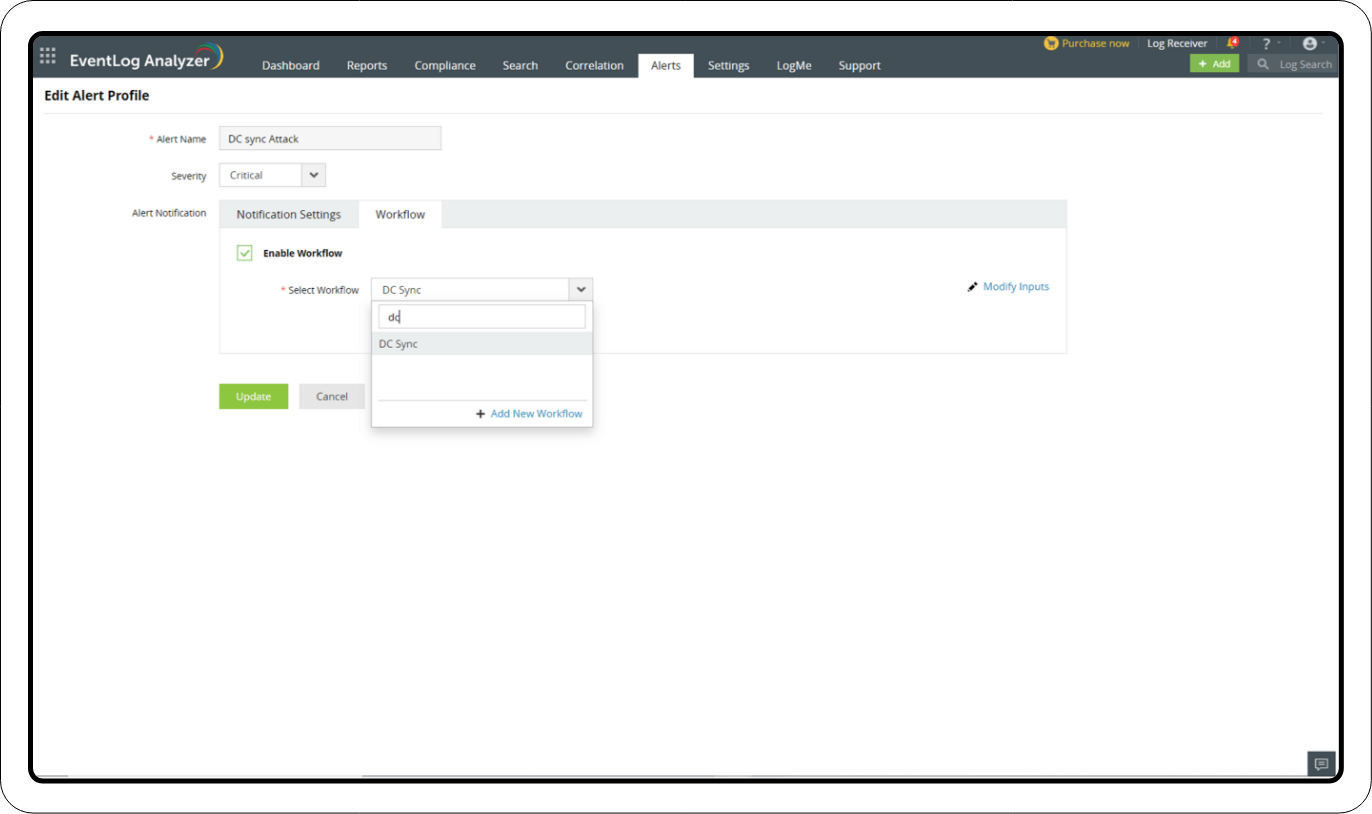
Adding a Workflow
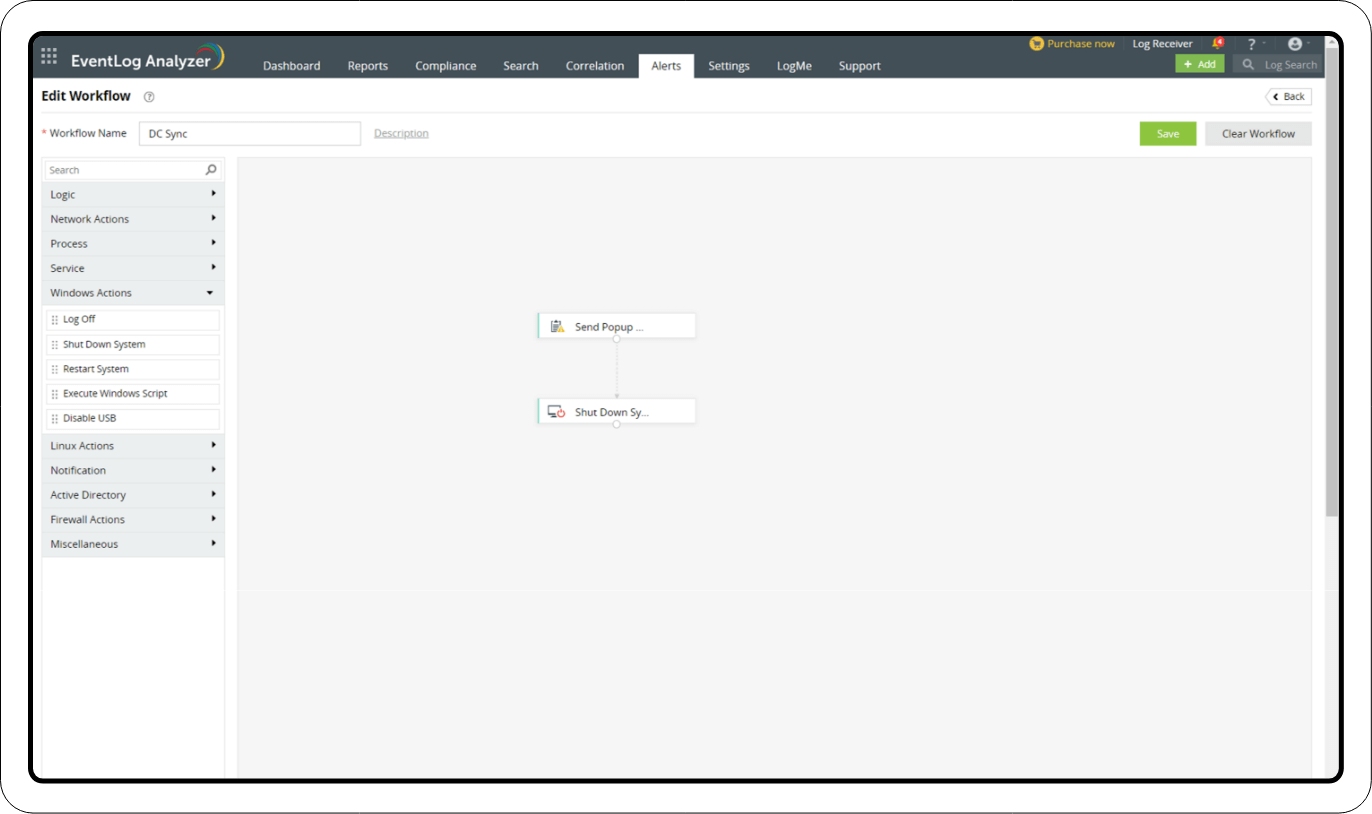
1. Create Workflow
- In the Alerts tab, click the settings icon in the top-right corner of the page.
- Select Workflow.
- Click Create Workflow in the top-right corner to create a new Workflow.
For example:
- Drag the Send Popup Message under the Notifications tab to the Workflow area to start the Workflow.
- Drag and drop Shut Down System under Windows Actions to create a Workflow that immediately shuts down the system, thus preventing the user from further exploiting that access once the alert has been triggered.
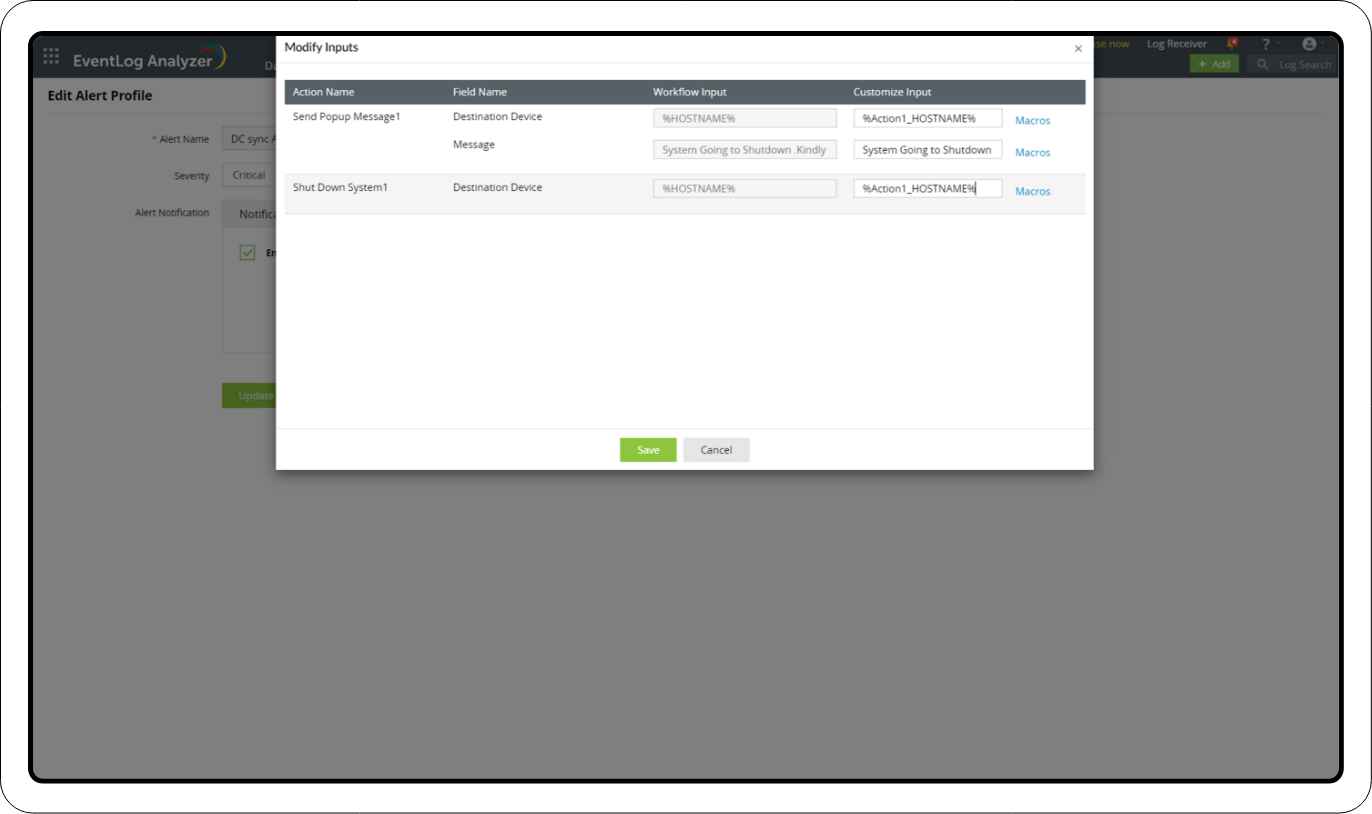
2. Add the Workflow with an Alert Profile
- In the Alerts tab, click the settings icon in the top-right corner of the page.
- Select Manage Profiles.
- Click Correlation Alert Profiles.
- In the newly created DCSync attack Alert Profile, click Configure.
- Navigate to the Workflow tab under Alert Notification.
- Click Enable Workflow and select the relevant Workflow from the drop-down menu.
- Select Modify Inputs if there are any fields that need to be modified.
- Once the fields are updated, click Save.
- On the main page, click Update.
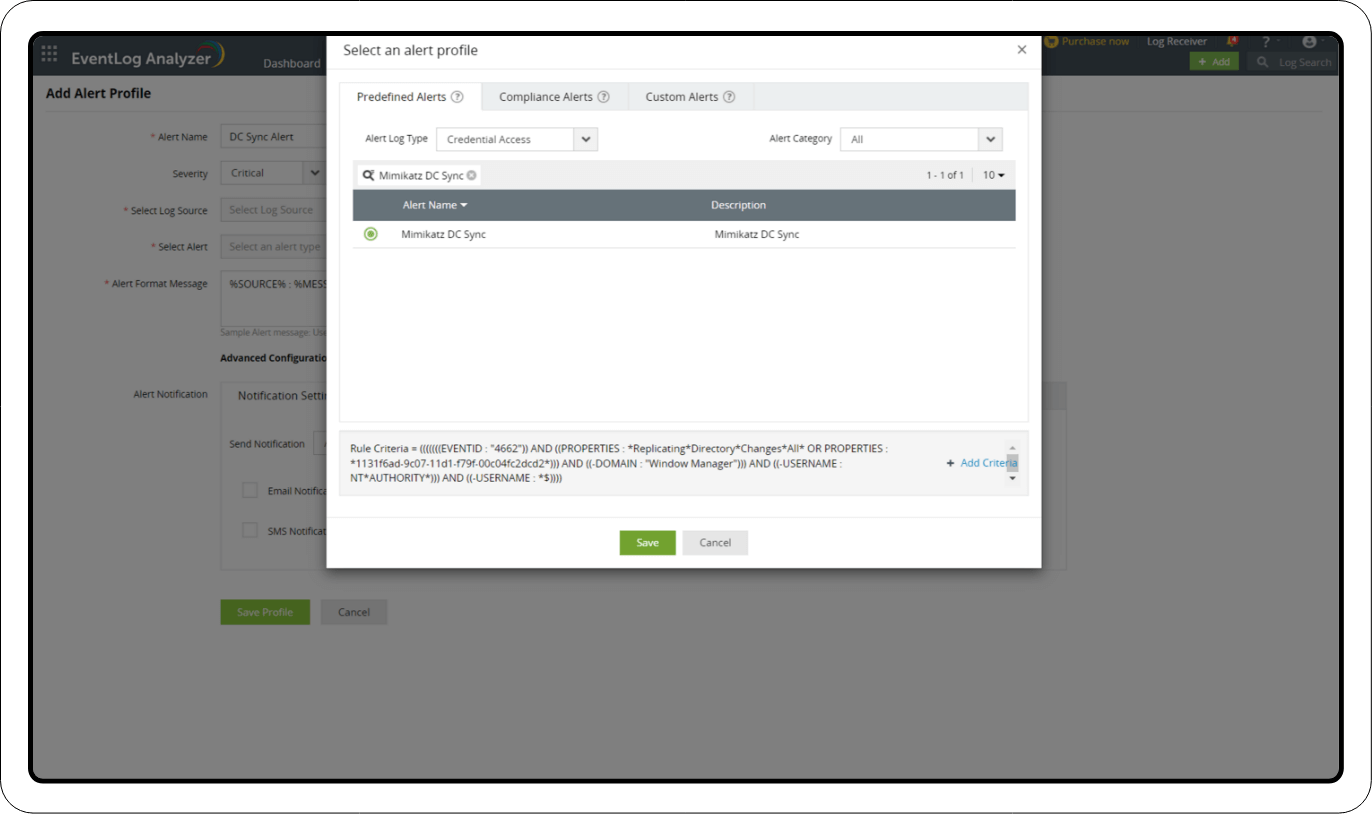
3. Creating an Alert Profile
Go to the Log360 console > SIEM > Alerts > Add Alert Profile > Select Alert.
- Search for Credential Access in the Alert Log Type field.
- Click the search icon to search for the DC Sync alert.
- Check the alert name, and click Save.
- You can assign a Workflow for the alert as well.